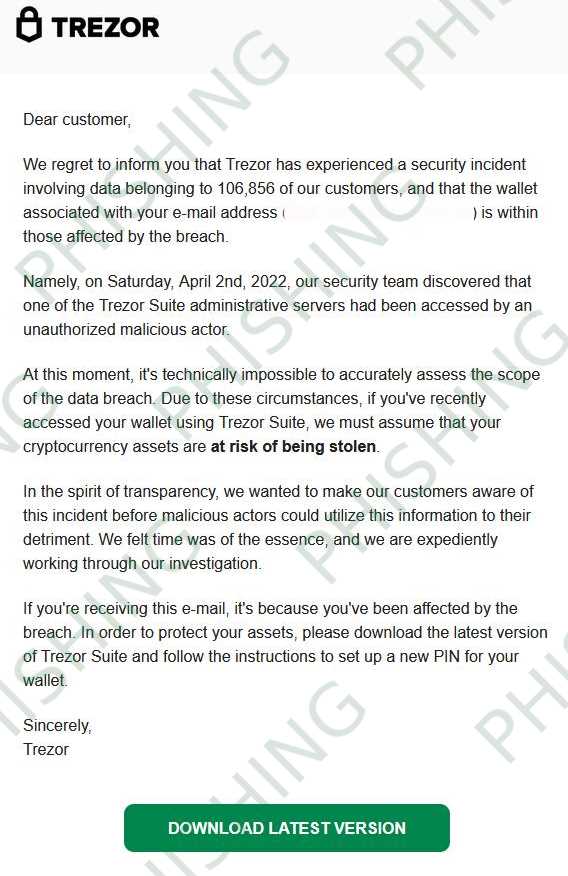
Trezor Security Breach: Critical Details You Must Know

Last week, Trezor, one of the leading cryptocurrency hardware wallet manufacturers, experienced a major security breach that potentially puts user funds at risk. A thorough investigation is currently underway to determine the full extent of the attack and the potential impact on Trezor users.
This security breach serves as a reminder of the constant threats faced by users in the digital asset space. While hardware wallets are generally considered a secure way to store cryptocurrencies, incidents like these highlight the importance of staying vigilant and taking necessary precautions.
According to reports, a malicious actor was able to infiltrate Trezor’s infrastructure, gaining unauthorized access to certain systems and potentially compromising sensitive user information. This includes email addresses, encrypted login credentials, and device serial numbers. Trezor has assured users that their private keys, which are stored securely on the hardware wallets, remain uncompromised.
As a precautionary measure, Trezor is advising all users to change their account passwords and enable two-factor authentication if they haven’t already done so. Additionally, users are encouraged to monitor their accounts closely for any suspicious activity and report it immediately.
Trezor has taken immediate steps to address the vulnerability and enhance the security of its systems. The company is working closely with cybersecurity experts to investigate the incident and minimize the potential impact on its users.
It is crucial for Trezor users to stay informed about the latest developments regarding the security breach. Regularly checking for updates from Trezor and following their recommendations will help ensure the safety of your digital assets.
While this unfortunate incident highlights the evolving nature of cybersecurity threats, it also emphasizes the need for individuals to take responsibility for their own security. Staying informed and practicing good security hygiene by using strong and unique passwords, enabling two-factor authentication, and keeping software and firmware up to date are important steps to safeguard your cryptocurrencies.
Trezor’s commitment to transparency and user security is evident in their prompt response to the breach. By staying informed and taking appropriate actions, users can continue to confidently use their Trezor hardware wallets, knowing that the company is actively addressing the situation and working towards a resolution.
Trezor Security Breach Explained
In recent news, Trezor, a popular hardware wallet for storing cryptocurrencies, has experienced a security breach. This incident has raised concerns among users about the safety of their digital assets and the overall security measures implemented by Trezor.
The breach occurred on [insert date], when hackers gained unauthorized access to Trezor’s servers. Upon investigation, it was discovered that the attackers were able to exploit a vulnerability in the system, allowing them to gain control of certain user accounts and potentially steal their funds.
Trezor has taken immediate action to address the breach and mitigate any potential damage. They have disabled the compromised accounts and implemented additional security measures to prevent similar incidents in the future. Furthermore, they have notified all affected users and encouraged them to update their passwords and enable two-factor authentication.
It is important for Trezor users to stay informed about the breach and follow the recommended security measures to protect their funds. By updating passwords, enabling two-factor authentication, and regularly monitoring their accounts, users can enhance the security of their cryptocurrencies stored in Trezor wallets.
While this security breach is certainly concerning, it is also an opportunity for Trezor to reassess and strengthen their security measures. As the popularity of cryptocurrencies continues to grow, the need for robust security solutions becomes increasingly important. Trezor will likely learn from this incident and continue to improve their security protocols to safeguard user funds.
As a user of Trezor, it is crucial to remain vigilant and informed about any developments related to this breach. By staying informed and taking appropriate security precautions, users can protect their cryptocurrencies and maintain peace of mind in an increasingly digital world.
Understanding the Recent Attack on Trezor

The recent attack on Trezor, a popular hardware wallet for storing cryptocurrencies, has caused concern among its users and the wider crypto community. In this article, we aim to provide a clear explanation of the attack and its implications.
What happened?

On [date], Trezor’s security team detected an unauthorized access attempt on their servers. The attackers tried to exploit a vulnerability in the system to gain access to users’ wallets and funds. Trezor promptly responded by taking their servers offline and launching an investigation into the incident.
Impact on users
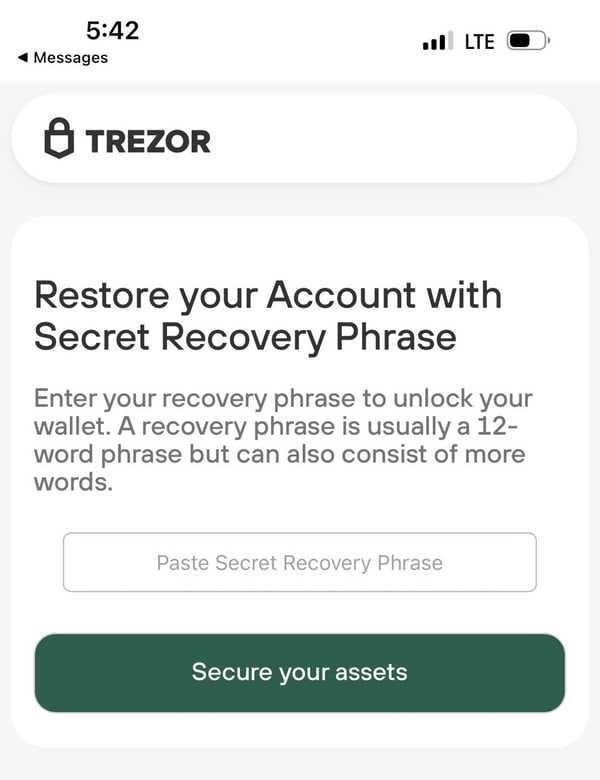
While the attack was thwarted before any harm was done, it serves as a reminder of the importance of maintaining strong security practices when it comes to storing and managing cryptocurrencies. Users are advised to update their Trezor firmware to the latest version and ensure they have a secure PIN to minimize the risk of unauthorized access.
It is worth noting that Trezor wallets are known for their robust security measures, including offline storage of private keys and encrypted communication. However, no system is completely immune to attacks, and it is essential to stay vigilant and informed about potential vulnerabilities.
Trezor has taken steps to enhance its security measures in response to the incident. This includes implementing additional security protocols and conducting regular security audits to identify and mitigate any potential weaknesses.
Key takeaways:
- Stay informed: Keep up to date with the latest information about the attack from reliable sources, such as Trezor’s official announcements.
- Update firmware: Ensure your Trezor device is running the latest firmware version, which includes security patches and enhancements.
- Use strong authentication: Set a secure PIN for your device and enable two-factor authentication whenever possible.
- Stay cautious: Be aware of phishing attempts and suspicious emails or websites claiming to be associated with Trezor. Always verify the authenticity of any communication before sharing sensitive information.
In conclusion, understanding the recent attack on Trezor is crucial for maintaining the security of your cryptocurrency assets. By staying informed and implementing the recommended security measures, you can better protect your funds and minimize the risk of unauthorized access.
Steps to Keep Yourself Informed and Protected

It is important to stay informed about the recent attack on Trezor to ensure the security of your assets. Here are some steps you can take to keep yourself informed and protected:
1. Stay Updated

Regularly visit the official Trezor website and subscribe to their newsletter to stay updated on the latest news and security measures. This will help you stay informed about any potential security risks and vulnerabilities.
2. Follow Security Best Practices
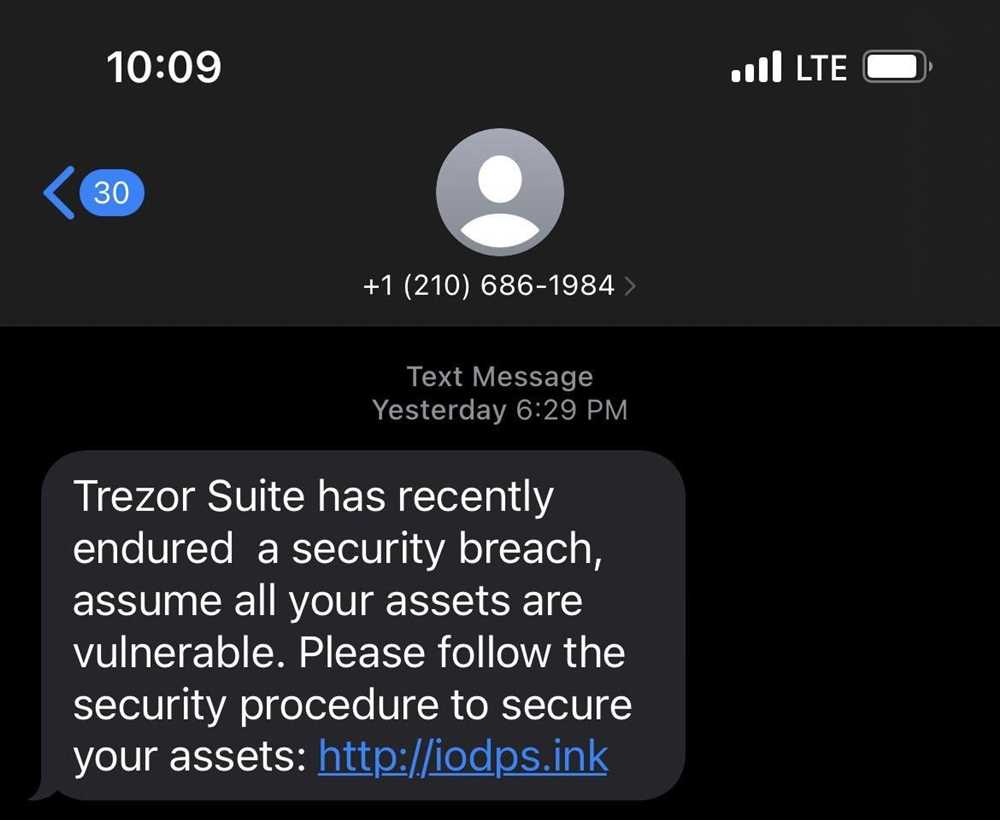
Make sure to follow security best practices when using your Trezor device, such as setting up a strong password, enabling two-factor authentication, and keeping your firmware up to date. These simple steps can greatly enhance the security of your assets.
3. Be Aware of Phishing Attempts

Be cautious of phishing attempts that may try to trick you into revealing your personal information or seed phrase. Always double-check the URL of the websites you visit and never enter sensitive information on suspicious or untrusted sites.
4. Join Community Forums

Joining community forums and discussion groups can help you stay informed about the latest security issues and share experiences with other Trezor users. This can provide valuable insights and support in keeping your assets safe.
5. Report Suspicious Activity
If you notice any suspicious activity or have encountered a security breach, report it immediately to Trezor and any relevant authorities. This will help ensure that appropriate actions are taken to address the issue and protect other users.
By following these steps, you can stay informed about the recent attack on Trezor and take necessary precautions to protect your assets and personal information.
Q&A:
What is Trezor Security Breach?
Trezor Security Breach refers to the recent attack on Trezor, a popular hardware wallet used for storing cryptocurrencies. During the breach, hackers gained unauthorized access to certain features and data of Trezor users.
What type of data could have been compromised during the attack?
During the attack, certain users’ personal information, such as email addresses and encrypted passwords, could have been compromised. Additionally, the hackers may have gained access to users’ transaction history and cryptocurrency balances.
How did the hackers manage to breach Trezor’s security?
The exact method used by the hackers to breach Trezor’s security has not been disclosed. However, it is suspected that they may have exploited vulnerabilities in the software or used phishing techniques to trick users into revealing their login credentials.
What steps is Trezor taking to address the security breach?
Trezor has taken immediate steps to address the security breach. They have notified all potentially affected users and advised them to change their passwords. They are also conducting a thorough investigation to identify the root cause of the breach and strengthen their security measures to prevent future attacks.
What should Trezor users do to protect their accounts?
Trezor users should take several steps to protect their accounts. Firstly, they should change their passwords immediately and ensure that the new password is strong and unique. Secondly, they should enable two-factor authentication for an additional layer of security. Finally, users should remain vigilant for any suspicious activity and report it to Trezor immediately.


