
Trezor Fails Lessons Learned from Past Failures

In the world of digital finance, security is paramount. For users of cryptocurrency, protecting their assets from hackers and malicious actors is of the utmost importance. One popular solution that has emerged to address this need is the Trezor hardware wallet. However, even with its strong reputation, Trezor has had its fair share of failures in the past.
One of the most notable Trezor failures occurred in 2018 when a group of researchers discovered a vulnerability that allowed them to extract the private keys from the device. This revelation sent shockwaves through the cryptocurrency community and highlighted the need for constant vigilance when it comes to security in the digital world.
The lessons learned from Trezor’s past failures are invaluable. Firstly, they remind us that no system is completely immune to vulnerabilities. As technology advances, so do the techniques used by hackers. It is crucial for companies like Trezor to constantly update their security measures to stay one step ahead of those with malicious intentions.
Secondly, Trezor’s failures remind us of the importance of transparency and honesty when dealing with security issues. After the vulnerability was discovered, Trezor promptly acknowledged and addressed the issue, providing a software update that fixed the problem. This open and transparent approach helped to restore confidence in the company and showed their commitment to the safety of their users.
In conclusion, Trezor’s past failures have provided valuable lessons for both the company and its users. They serve as a reminder of the ever-present threat of security breaches in the digital world and the need for constant vigilance. By learning from these mistakes and continually improving their security measures, Trezor and other companies can ensure the safety and protection of their customers’ digital assets.
Trezor Fails: Lessons Learned from Past Failures
In the world of cryptocurrency, security is of utmost importance. One of the leading companies in providing secure hardware wallets is Trezor. However, even with their expertise, there have been instances where Trezor has faced failures. These failures have not only taught Trezor valuable lessons but also provided valuable lessons for others in the industry.
The Importance of Regular Updates
One of the key lessons learned from Trezor’s past failures is the importance of regular updates. Security threats in the crypto world are ever-evolving, and it’s crucial for hardware wallet manufacturers to stay ahead of these threats. Trezor has acknowledged this and has implemented a robust system of regular updates to ensure that their wallets are always equipped with the latest security features.
Lesson Learned: Regular updates are crucial to stay ahead of evolving security threats.
User Education and Communication
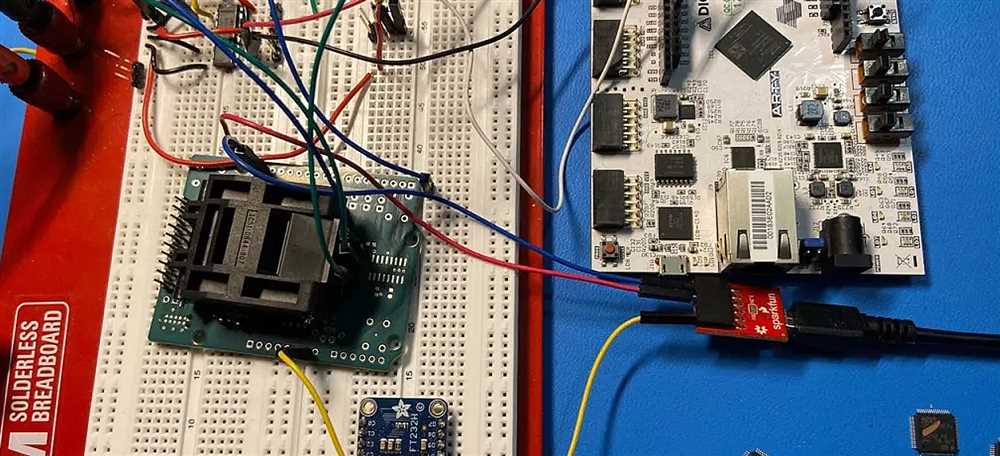
Trezor’s failures also highlighted the importance of user education and communication. In the face of a security breach or vulnerability, it’s essential for a company to communicate openly and transparently with its users. Trezor has learned this lesson and now actively engages with its community, providing detailed information about any vulnerabilities and steps users can take to mitigate risks.
Lesson Learned: Open and transparent communication with users is crucial during times of failures and vulnerabilities.
In conclusion, Trezor’s past failures have taught valuable lessons to both the company itself and the cryptocurrency industry as a whole. Regular updates and open communication are critical components in ensuring the security of hardware wallets. It is through these failures that Trezor has strengthened its products and the overall security of the crypto community.
Security Breaches: Understanding the Consequences

In today’s interconnected and digital world, security breaches have become a growing concern for individuals, businesses, and organizations alike. These breaches, often caused by vulnerabilities in systems or human error, can have severe consequences that can cripple both personal and financial well-being.
One of the most alarming consequences of security breaches is identity theft. When hackers gain unauthorized access to personal information such as social security numbers, credit card details, or passwords, they can use this information to commit fraudulent activities in the victim’s name. This can lead to devastating financial losses, ruined credit scores, and a significant amount of time and resources spent trying to regain control over one’s identity.
Another consequence of security breaches is the loss of sensitive corporate data. Businesses and organizations that handle large amounts of sensitive information, such as customer data, trade secrets, or intellectual property, are at risk of losing valuable assets if their security measures are not robust enough. The consequences of such data breaches can range from reputational damage and loss of client trust to legal implications and financial penalties.
Moreover, security breaches can have a significant impact on individuals’ privacy. In an era where personal information is collected and stored by numerous online services, any breach can result in sensitive data being exposed to the public or sold on the dark web. This invasion of privacy can have long-lasting effects on individuals, causing feelings of vulnerability and mistrust towards technology.
Finally, security breaches can disrupt services and systems, affecting businesses and individuals reliant on those systems. Whether it’s a bank’s online banking service being compromised or a transportation company’s systems being hacked, these breaches can lead to significant downtime, financial losses, and inconvenience for users. This can have ripple effects on various aspects of society, from the economy to public trust in technology.
In conclusion, the consequences of security breaches are far-reaching and impactful. They can result in identity theft, loss of sensitive data, invasion of privacy, and disruption of services. It is crucial for individuals, businesses, and organizations to invest in robust security measures and regularly update them to mitigate the risks of these breaches and protect themselves from the severe consequences that can arise.
User Experience Matters: Avoiding Common Pitfalls
When it comes to developing a successful hardware wallet, user experience is of utmost importance. This is because a user-friendly interface can greatly enhance the overall security of the device by minimizing the chances of user error. In this section, we will discuss some of the common pitfalls that can negatively impact the user experience and how to avoid them.
1. Complicated Setup Process
The setup process of a hardware wallet should be as simple as possible. Users should not require technical know-how or spend an excessive amount of time to get their device up and running. Clear, concise instructions with visual aids can go a long way in making the setup process intuitive and hassle-free.
2. Lack of Intuitive Navigation
Navigating through the wallet’s interface should be straightforward and intuitive. Users should be able to access the necessary features and functions easily without confusion. A well-organized menu and clear labels can help users find what they need quickly and efficiently.
3. Poorly Designed User Interface
The user interface should be visually appealing and easy to understand. Cluttered screens, small font sizes, and complex layouts can overwhelm users and lead to mistakes. A clean and minimalistic design, with clear icons and buttons, can greatly improve the user experience and make the wallet more user-friendly.
4. Lack of Clear Transaction Confirmation
One of the critical aspects of a hardware wallet is confirming transactions accurately. Users should be provided with clear and detailed information about the transaction they are about to sign. This includes the recipient address, the amount being transferred, and any associated fees. Clear confirmation prompts and comprehensive transaction summaries can help users verify the details before finalizing the transaction.
5. Inadequate Error Handling
Error messages should be informative and provide users with guidance on how to resolve the issue. Vague error messages or cryptic error codes can leave users frustrated and confused. Clear and concise error messages that suggest specific actions can greatly enhance the user experience and reduce the chances of user errors.
Avoiding these common pitfalls can significantly improve the user experience of a hardware wallet. By prioritizing usability and making the device more intuitive and user-friendly, hardware wallet manufacturers can provide a secure and enjoyable experience for their users.
Transparent Communication: Building Trust with Customers
Trust is at the core of any successful business relationship, especially when it comes to financial services. As a company that deals with people’s money and sensitive information, it is essential to prioritize transparent communication to build and maintain trust with customers.
Transparency means being open and honest about your company’s practices, policies, and intentions. It involves sharing information proactively, even when it may not portray the company in the best light. By doing so, you show your commitment to being accountable and responsible for your actions.
Building trust starts with clear and straightforward communication. Customers should have a clear understanding of how their data is collected, stored, and used. Providing this information in a transparent manner fosters trust and reassures customers that their privacy is a priority.
Regularly updating customers about any changes, updates, or issues is vital. Providing timely and accurate information can prevent misunderstandings, rumors, or speculations. Customer communication should be transparent, concise, and easily understandable, avoiding technical jargon or confusing language.
Another essential aspect of transparent communication is taking responsibility for mistakes or failures. No company is perfect, and mistakes can happen. However, what sets businesses apart is how they handle those mistakes. Admitting to errors, being transparent about the impact, and outlining steps taken to prevent similar incidents in the future demonstrates integrity and builds trust.
Through open and transparent communication, businesses can involve customers in decision-making processes. Seeking feedback, conducting surveys, or providing channels for customer input ensures that their opinions are acknowledged and valued. This involvement fosters a sense of ownership and trust in the company’s operations.
Ultimately, transparent communication builds trust, loyalty, and a positive reputation. It establishes a solid foundation for successful customer relationships and sets the stage for long-term business growth. By prioritizing transparent communication, companies like Trezor can demonstrate their commitment to their customers’ well-being and security.
Continuous Improvement: Evolving to Stay Ahead
In the fast-paced world of technology, it is crucial for companies to constantly evolve and improve their products to stay ahead of the competition. This is especially true in the cryptocurrency realm where security and reliability are paramount. Trezor, a leading hardware wallet provider, understands the importance of continuous improvement and has learned valuable lessons from past failures.
Learning from Mistakes
Trezor has faced its fair share of challenges and failures in the past. However, rather than being deterred by these setbacks, they have embraced them as learning opportunities. Each failure has provided valuable insights into how they can improve their products and better serve their customers.
By analyzing the causes of past failures, Trezor has been able to identify weaknesses and vulnerabilities in their hardware wallets. They have then taken proactive steps to address these issues and enhance the security and functionality of their products. This iterative process of learning from mistakes and making continuous improvements has been instrumental in ensuring that Trezor stays ahead of the competition.
Striving for Perfection
Trezor understands that in order to remain at the forefront of the industry, they must strive for perfection. They know that even small vulnerabilities or weaknesses can have significant implications for their users, and they refuse to compromise on security. This commitment to excellence drives their continuous improvement efforts.
Through rigorous testing and quality control measures, Trezor ensures that every aspect of their hardware wallets is thoroughly scrutinized and optimized. They work closely with independent security auditors to identify any potential issues, and they actively seek feedback from their user community. This feedback loop allows them to constantly refine and enhance their products, making them more secure and user-friendly.
Evolving to Stay Ahead
With each new iteration of their hardware wallets, Trezor demonstrates their commitment to evolving and staying ahead. They understand that the world of cryptocurrency is constantly evolving and that they must adapt to meet the changing needs of their users.
By continuously improving their products, Trezor not only enhances the security and functionality of their hardware wallets but also instills confidence in their users. They have shown that they are proactive in addressing weaknesses, and that they prioritize the safety and satisfaction of their customers.
In conclusion, continuous improvement is crucial for companies like Trezor to stay ahead in the fast-paced cryptocurrency industry. By learning from past failures, striving for perfection, and constantly evolving their products, Trezor has positioned itself as a leader in the hardware wallet market.
Question-answer:,
What is Trezor?
Trezor is a hardware wallet for securely storing and managing cryptocurrencies.
What are some of the past failures of Trezor?
Some of the past failures of Trezor include a vulnerability that allowed an attacker to take control of the device and steal the user’s funds and a firmware update that caused some devices to become unresponsive.
What lessons have been learned from Trezor’s past failures?
One of the lessons learned is the importance of regularly updating the firmware to ensure the device’s security. Additionally, it highlighted the need for Trezor to have a strong communication strategy with its users to quickly address any security issues that may arise.
How has Trezor improved its security measures after past failures?
Trezor has improved its security measures by introducing a security-hardened design, implementing a multi-step authentication process, and offering additional features such as passphrase protection. They have also increased the transparency of their security practices by conducting regular security audits.
Is Trezor considered a reliable hardware wallet despite its past failures?
Yes, despite its past failures, Trezor is still considered a reliable hardware wallet. The company has taken steps to address the vulnerabilities and has a strong track record of providing secure storage for cryptocurrencies. However, it is always recommended to stay informed about the latest security updates and best practices in using hardware wallets.


