
Uncovering the Hackers Behind the Trezor Data Breach

The Trezor data breach has sent shockwaves throughout the digital community as security experts scramble to identify the culprits behind this devastating event. Trezor, a popular hardware wallet used for storing cryptocurrencies, was known for its robust security features. However, hackers managed to exploit a vulnerability, leading to the breach of sensitive user information.
The hunt for the perpetrators is underway, with cybersecurity firms and law enforcement agencies combining their efforts to trace the origins of the attack. The magnitude of the breach has raised concerns about the overall safety of digital assets and the effectiveness of existing security measures.
Security analysts believe that the data breach was not the work of a lone individual but rather a sophisticated and well-coordinated operation. The nature of the attack suggests the involvement of a highly skilled group with extensive knowledge of both cryptography and hacking techniques. The ultimate goal of these cybercriminals remains unclear, with speculation ranging from financial gain to political motives.
As the investigation unfolds, the digital community is urged to remain vigilant and take necessary precautions to safeguard their assets. It serves as a stark reminder of the ever-present threat of cyber attacks and the importance of continuously evolving security strategies. The identification and prosecution of the culprits responsible for the Trezor data breach will be a critical step towards restoring faith in the security of cryptocurrencies and ensuring the safety of users’ digital wealth.
Trezor Data Breach: Uncovering the Culprits

The Trezor data breach is a serious incident that has put the security of users’ digital assets at risk. In this article, we will delve into the investigation process and explore the clues that led to the identification of the culprits behind the breach.
1. Gathering Evidence:
- Forensic experts analyzed the compromised system and collected digital evidence.
- Logs and network traffic data were carefully examined to trace the origin of the breach.
- Security cameras and access logs were reviewed to identify any suspicious activities within the premises.
2. Tracing the Attack:
- The timeline of the breach was established by analyzing timestamps and correlating events.
- Unusual network traffic patterns and connections were identified, indicating the presence of an external attacker.
- Intrusion detection systems and firewalls were analyzed to determine the entry point of the attacker.
3. Identifying the Culprits:
- Using advanced threat intelligence tools and techniques, the investigators uncovered a trail of clues.
- Anomalous activity patterns were linked to specific IP addresses and geographical locations.
- Analysis of malware used in the breach led to known hacking groups and their previous activities.
- The investigators cross-referenced suspect information with law enforcement databases to identify potential culprits.
4. Legal Action:
- The authorities were alerted and provided with evidence to support the identification of the culprits.
- Law enforcement agencies initiated investigations and coordinated efforts with international counterparts if necessary.
- Arrests were made, and legal proceedings commenced to hold the responsible parties accountable.
In conclusion, the Trezor data breach was meticulously investigated to uncover the culprits responsible for compromising the security of users’ digital assets. This incident serves as a reminder of the importance of robust security measures and continuous monitoring to protect sensitive information.
The Cybersecurity Investigation

The Trezor data breach raised concerns about the overall cybersecurity of the company. In response, a thorough investigation was launched to identify the culprits responsible for the breach and to understand the extent of the damage done.
The investigation commenced by first analyzing the patterns and nature of the breach. This included examining the affected systems, the type of data that was compromised, and the specific vulnerabilities that were exploited. Forensic experts and cybersecurity analysts were brought in to assess the situation and gather evidence.
One aspect of the investigation focused on identifying any potential insider threats or internal vulnerabilities. This involved scrutinizing employee access privileges, reviewing security protocols, and conducting interviews with relevant personnel. By understanding the internal workings of the company, investigators could determine if any employees played a role in the breach or if there were systemic weaknesses that were exploited.
Another key area of investigation was to trace the origin of the breach. This meant examining the IP addresses used to launch the attack, tracing the network pathways, and analyzing any malware or other malicious tools that were discovered. By piecing together this information, investigators hoped to uncover the identity of the attackers and potentially uncover any patterns or motives behind the breach.
The investigation also involved reaching out to external parties for potential leads or clues. This included collaborating with law enforcement agencies, sharing information with other affected companies, and leveraging the expertise of third-party cybersecurity firms. By expanding the network of resources, investigators aimed to gather as much intelligence as possible and enhance the chances of identifying the culprits.
Conclusion
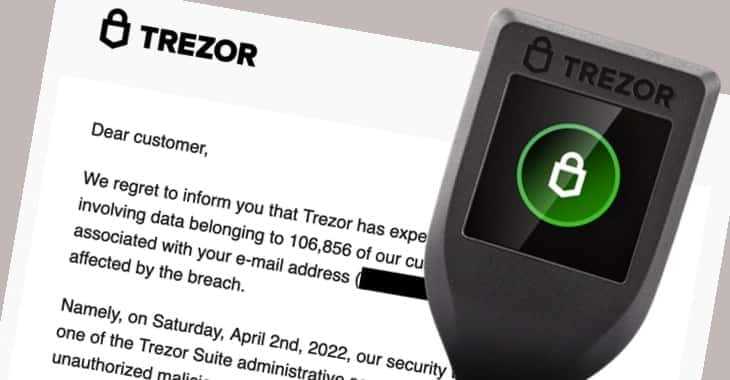
The advanced cybersecurity investigation launched in response to the Trezor data breach aimed to uncover the culprits responsible for the breach and shed light on any potential vulnerabilities within the company’s cybersecurity practices. Through diligent analysis, the investigation sought to not only identify those responsible but also provide valuable insights for strengthening future security measures.
Tracing the Footprints
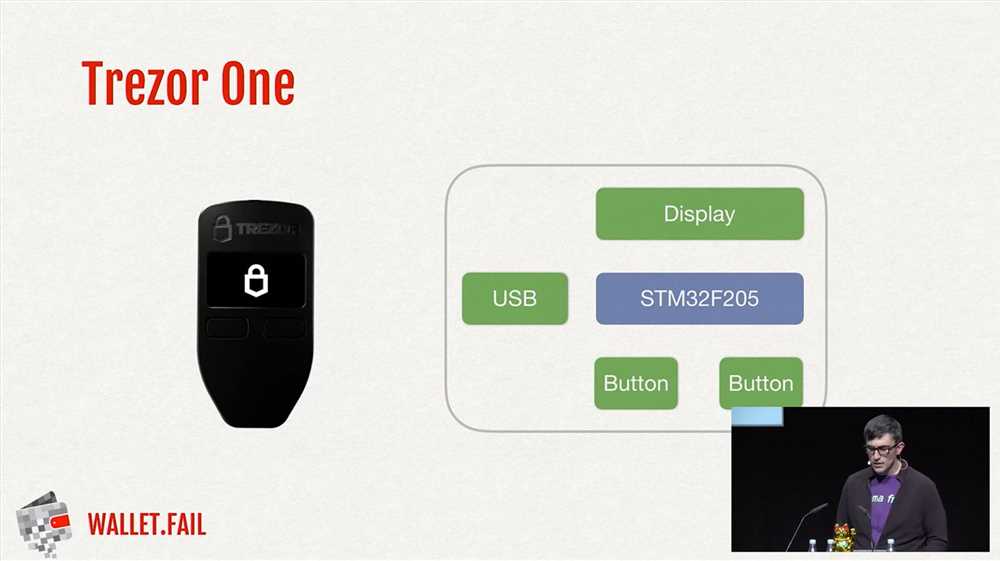
When it comes to identifying the culprits behind the Trezor data breach, it is crucial to trace their footprints in the digital landscape. This requires a meticulous investigation process that involves analyzing various factors and following the trail of evidence.
One of the key steps in tracing the footprints is to examine the server logs and network traffic of the affected systems. By analyzing these logs, security experts can determine the entry point of the attackers, the methods they used to infiltrate the system, and any suspicious activities that took place leading up to the breach.
Additionally, analyzing the malware used in the breach can provide valuable insights into the identity of the perpetrators. Malware analysis involves dissecting the code and behavior of the malicious software, looking for patterns or characteristics that can be linked to known hacking groups or individual hackers. This can help narrow down the list of potential suspects.
Another important aspect of tracing the footprints is gathering intelligence from various sources in the online community. This includes monitoring hacker forums, dark web marketplaces, and other underground channels where cybercriminals operate. By staying informed about the latest trends, tactics, and tools used by hackers, investigators can gain a better understanding of the possible motives and techniques employed by the culprits.
Furthermore, cooperation and collaboration between different organizations and law enforcement agencies are pivotal in tracing the footprints of the Trezor data breach. Sharing information and working together can greatly enhance the investigation process by pooling resources and expertise. This may involve cross-border coordination and assistance, especially if the attackers are operating from a different jurisdiction.
In conclusion, tracing the footprints in the aftermath of the Trezor data breach is a complex and thorough process. It requires a combination of technical skills, intelligence gathering, and cooperation among various stakeholders. By following the trail of evidence, analyzing server logs and malware, and leveraging online sources, investigators can increase the chances of identifying the culprits responsible for the breach.
Identifying the Perpetrators
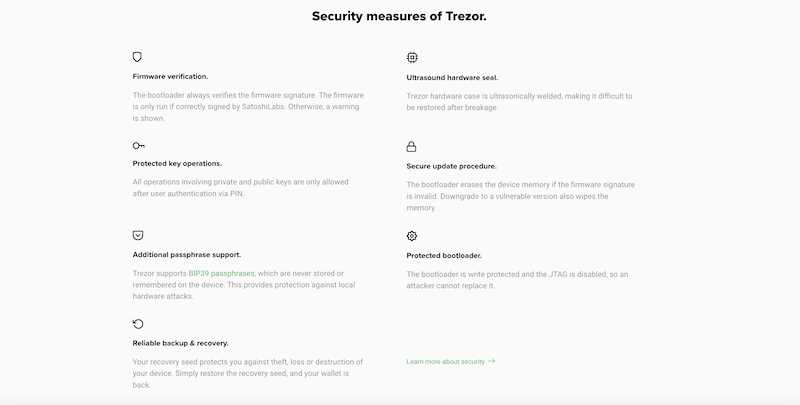
Identifying the individuals responsible for the Trezor data breach is a complex task that requires extensive investigation and forensic analysis. The process involves analyzing various types of evidence, such as digital footprints, logs, and IP addresses, to identify potential suspects.
One of the key methods used to trace the culprits is analyzing the patterns and techniques used in the attack. These can provide valuable insights into the expertise and motivations of the attackers. For example, the type of malware used, the methods of infiltration, and the manner in which the stolen data was accessed are all important clues that can be used to narrow down the list of potential perpetrators.
In addition to technical analysis, law enforcement agencies often collaborate with cybersecurity firms and other experts to gather intelligence on known cybercriminals and their activities. This includes monitoring underground forums, analyzing dark web marketplaces, and tracking bitcoin transactions to identify any suspicious activity or connections to the Trezor data breach.
Attribution Challenges

Identifying the culprits behind a data breach like the one that affected Trezor poses unique challenges. Cybercriminals often employ various techniques to conceal their identities and obfuscate their actions. They may use sophisticated encryption methods, anonymization services, and other tactics to hide their tracks.
Furthermore, attribution can be particularly challenging in cases where multiple individuals or groups are involved in the attack. Hacktivist collectives, nation-state-sponsored actors, and organized crime groups may collaborate or share resources, making it difficult to pinpoint individual perpetrators.
However, with the advancement of forensic techniques and international cooperation among law enforcement agencies, the chances of identifying the perpetrators are increasing. The use of digital forensics, data analytics, and intelligence-sharing platforms helps investigators to connect the dots and uncover the individuals or groups responsible for the breach.
In conclusion, identifying the perpetrators of the Trezor data breach requires a combination of technical expertise, investigative skills, and cooperation among various stakeholders. While there are challenges in tracing cybercriminals, advancements in technology and collaboration are improving the chances of identifying and bringing the culprits to justice.
Question-answer:
What is the Trezor Data Breach?
The Trezor Data Breach refers to a recent incident where the user data of Trezor, a popular hardware cryptocurrency wallet, was compromised.
How did the Trezor Data Breach happen?
The exact details of how the Trezor Data Breach occurred are still under investigation. However, it is believed that hackers gained unauthorized access to the Trezor servers and obtained user data.


