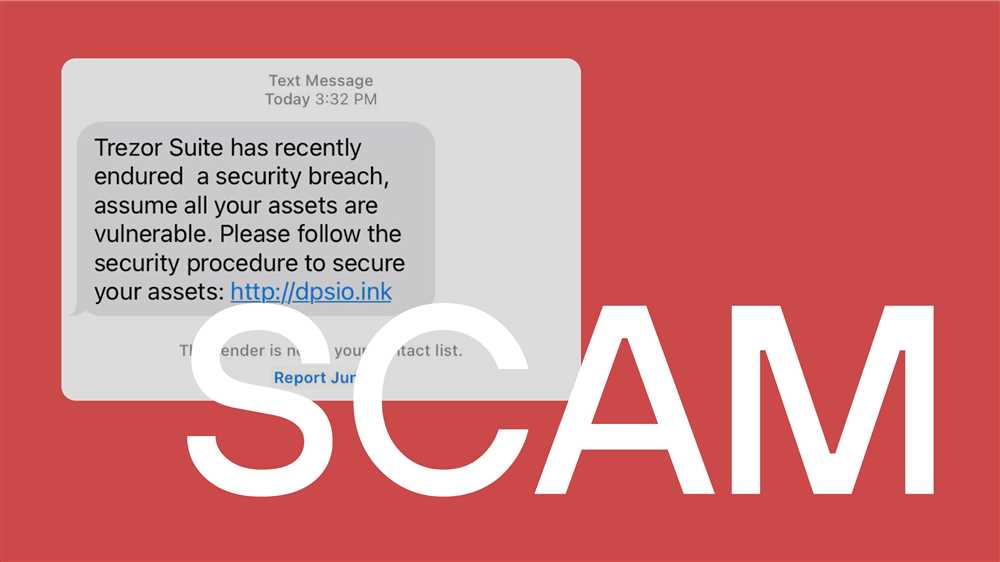
Trezor Data Breach Explained

In today’s digital age, cybersecurity is paramount. The recent Trezor data breach serves as a stark reminder of the importance of protecting our data and being vigilant about potential threats. Trezor, a popular hardware wallet used for storing cryptocurrencies, recently announced that their security had been compromised, potentially exposing sensitive user information.
This breach has raised concerns among users worldwide, as Trezor wallets are widely trusted for their robust security measures. It is crucial for Trezor users to be aware of the potential risks and take immediate steps to mitigate any potential damage.
One of the most alarming aspects of this breach is the possibility of private keys being compromised. Private keys are essential for accessing and managing cryptocurrencies, and if they fall into the wrong hands, it can lead to significant financial losses. Trezor users should act swiftly to protect their funds and consider moving their assets to a more secure wallet, if deemed necessary.
What Happened in the Trezor Data Breach

In the Trezor data breach, which occurred on November 2019, hackers were able to gain unauthorized access to the sensitive data of Trezor users. Trezor is a popular hardware wallet used for storing cryptocurrencies like Bitcoin.
During the breach, the attackers were able to exploit a vulnerability in Trezor’s software, allowing them to gain access to users’ login credentials, private keys, and other sensitive information. This breach put the security of users’ funds at risk.
Once the hackers gained access to the data, they attempted to use the stolen information to steal funds from the affected users’ wallets. This put the affected users at risk of losing their cryptocurrencies if the attackers were successful.
Trezor, upon discovering the breach, immediately took action to mitigate the impact. They notified the affected users and urged them to change their login credentials and enable additional security measures, such as two-factor authentication.
Furthermore, Trezor conducted a thorough investigation into the breach to understand the extent of the damage and identify any potential weaknesses in their security systems. They also worked to patch the vulnerability that was exploited by the attackers to prevent future breaches.
It is important for Trezor users and individuals in general to be aware of this data breach and its implications. It serves as a reminder to always practice good security hygiene when it comes to storing and managing cryptocurrencies. This includes using strong and unique passwords, enabling two-factor authentication, and regularly updating software and firmware.
| Date | Description |
|---|---|
| November 2019 | Hackers gain unauthorized access to Trezor’s sensitive data |
| Exploit a vulnerability in Trezor’s software | |
| Access users’ login credentials, private keys, and other sensitive information | |
| Attempt to steal funds from affected users’ wallets | |
| Trezor takes immediate action to mitigate the impact | |
| Notify affected users and urge them to change login credentials and enable additional security measures | |
| Conduct thorough investigation and patch the vulnerability |
Implications of the Trezor Data Breach
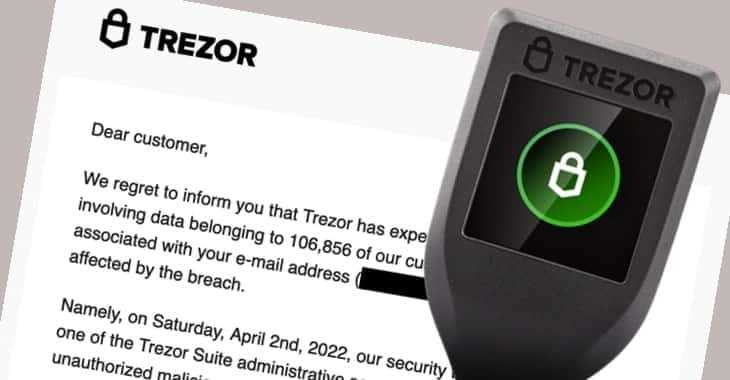
The Trezor data breach has significant implications for both Trezor users and the overall security of cryptocurrency wallets. This breach has exposed personal and financial information of thousands of users, making them vulnerable to various types of cyber attacks and scams.
User Accounts at Risk
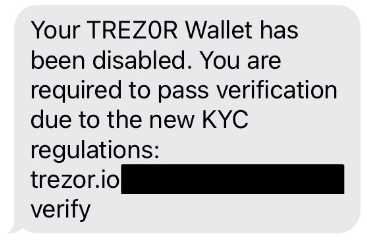
First and foremost, the data breach puts the affected users’ accounts at risk. Hackers have gained access to their usernames, email addresses, and potentially even passwords. This information can be used to launch targeted attacks, such as phishing attempts or credential stuffing attacks, to gain unauthorized access to users’ accounts.
With access to user accounts, hackers can potentially steal funds, initiate unauthorized transactions, or compromise the security of the cryptocurrency wallets. This can result in financial losses for the affected users and erode trust in the security measures implemented by Trezor.
Reputation Damage and Loss of Trust
The data breach not only affects the individuals whose data has been compromised but also has wider implications for Trezor as a company. Such incidents can severely damage the reputation of the company and undermine user trust. Users may become reluctant to use the Trezor wallet or any other cryptocurrency wallet, fearing similar breaches in the future.
Loss of trust can also extend to the wider cryptocurrency community. If users perceive that Trezor, one of the leading hardware wallet providers, is unable to protect their personal and financial information, they may question the security of the entire industry. This can have long-lasting implications for the adoption and acceptance of cryptocurrencies.
Trezor’s Response and Security Measures
Trezor must take swift and effective measures to address the data breach and restore user confidence. They should implement enhanced security protocols and procedures to prevent future breaches. Additionally, they should provide clear and timely communication to affected users, explaining the steps they are taking to mitigate the impact of the breach and protect their accounts.
Users are also advised to take immediate action to protect their accounts and personal information. This includes changing passwords, enabling two-factor authentication, and remaining vigilant against phishing attempts and suspicious activities.
In conclusion, the Trezor data breach has far-reaching implications for both the affected users and the wider cryptocurrency community. It highlights the need for robust security measures and constant vigilance in the face of evolving cyber threats.
What You Need to Do to Protect Yourself
With the recent data breach at Trezor, it is important to take steps to protect yourself and your personal information. Here are some actions you should consider:
1. Change your passwords: Start by changing your passwords for all online accounts, especially those that are linked to your Trezor wallet or contain sensitive information. Make sure to use strong, unique passwords that are difficult to guess.
2. Enable two-factor authentication: Two-factor authentication adds an extra layer of security to your accounts by requiring a second form of verification, such as a code sent to your mobile device. Enable this feature wherever possible.
3. Monitor your accounts: Keep a close eye on your bank accounts, credit cards, and other online accounts for any suspicious activity. Report any unauthorized transactions or unusual activity to your financial institution immediately.
4. Be cautious of phishing attempts: Be wary of any emails or messages that ask for personal information or prompt you to click on suspicious links. Always double-check the sender’s email address or contact the company directly to verify the legitimacy of the request.
5. Keep your software up to date: Regularly update your operating system, antivirus software, and other applications to ensure you have the latest security patches. This helps protect against known vulnerabilities that cybercriminals may exploit.
6. Consider using a password manager: A password manager can help you generate strong, unique passwords for each of your accounts and store them securely. This eliminates the need to remember multiple passwords and reduces the risk of password reuse.
7. Be cautious of public Wi-Fi networks: Avoid using public Wi-Fi networks for sensitive activities, such as accessing your Trezor wallet or banking accounts. If you must use public Wi-Fi, use a virtual private network (VPN) to encrypt your connection and protect your data.
Remember, taking steps to protect yourself and your personal information is crucial in the aftermath of a data breach. Stay vigilant and proactive in securing your online accounts and financial transactions.
Question-answer:
What is the Trezor data breach?
The Trezor data breach refers to a security incident where the personal information of Trezor cryptocurrency wallet users was compromised.
How did the data breach happen?
The data breach occurred due to a phishing attack, where hackers tricked users into providing their login credentials on a fake website that looked like the official Trezor site.
What information was compromised in the data breach?
The compromised information includes the email addresses, names, and possibly the physical addresses of Trezor wallet users.
What should Trezor wallet users do to protect themselves?
Trezor wallet users should immediately change their passwords, enable two-factor authentication, and be cautious of any suspicious emails or requests for personal information.


