
Uncovering the dangers of hacking Trezor hardware wallets

In recent years, cryptocurrencies have become increasingly popular, with many people turning to digital currencies as a form of investment. As the value of cryptocurrencies continues to rise, so too does the need for secure storage options. One such option is a hardware wallet, such as the Trezor.
Trezor hardware wallets are often seen as one of the safest ways to store cryptocurrencies. With their offline storage and strong encryptions, Trezor wallets offer a high level of security. However, recent research has shown that even these seemingly impenetrable devices are not completely immune to hacking.
Researchers have discovered several vulnerabilities in Trezor hardware wallets that could potentially allow an attacker to gain access to a user’s private keys and steal their cryptocurrencies. These vulnerabilities include physical attacks, such as tampering with the hardware, as well as software attacks, such as exploiting weaknesses in the device’s firmware.
While these vulnerabilities may be concerning, it’s important to note that the likelihood of an individual being targeted by such an attack is relatively low. Additionally, Trezor has been quick to respond to these findings and has released firmware updates to address the identified vulnerabilities. As a user, it’s crucial to stay informed about the latest security updates and to regularly update your Trezor wallet to ensure you’re protected against potential threats.
Understanding the Security Risks of Hacking Trezor Hardware Wallets

Trezor hardware wallets are a popular choice for storing cryptocurrency securely, but like any technology, they are not immune to security risks. Understanding these risks is crucial for users to make informed decisions about how to protect their assets.
Phishing Attacks
Phishing attacks are one of the most common risks when it comes to hacking Trezor hardware wallets. Hackers can create convincing fake websites or emails that trick users into providing their private keys or recovery phrases. These phishing attempts can lead to complete loss of funds if users unknowingly give away their sensitive information.
Physical Theft

While the primary purpose of a hardware wallet is to protect against online attacks, physical theft is still a risk. If a hacker gains physical access to a Trezor wallet, they can attempt to extract the private keys and gain control of the stored cryptocurrency. Users should always keep their hardware wallets in a secure location and take precautions to prevent theft.
Even if the device is stolen, it’s important to note that the hardware wallets are designed with additional security layers, such as PIN codes and encryption, to make it difficult for attackers to access the funds without the user’s authorization.
It’s also worth mentioning that the hardware wallets require a physical confirmation from the user to complete transactions, making it challenging for hackers to manipulate the device without the user’s knowledge.
Supply Chain Attacks

Supply chain attacks are another risk associated with Trezor hardware wallets. This type of attack involves tampering with the hardware wallet during the manufacturing process or distribution phase. Hackers may insert malicious components or firmware that can compromise the security of the device, allowing them to gain unauthorized access to the stored funds.
To mitigate this risk, users should ensure that they purchase Trezor hardware wallets directly from the official website or trusted resellers. Verifying the authenticity of the device and regularly installing firmware updates provided by the manufacturer are essential steps to protect against supply chain attacks.
Overall, understanding the security risks associated with hacking Trezor hardware wallets is crucial for users to implement appropriate measures to protect their assets. By being aware of phishing attacks, physical theft, and supply chain attacks, users can make informed decisions and take precautionary steps to keep their cryptocurrencies safe.
An Overview of Trezor Hardware Wallets and Their Vulnerabilities
Trezor hardware wallets are one of the most popular and widely used hardware wallets in the cryptocurrency industry. These wallets provide a secure and convenient way for users to store their private keys and cryptocurrencies offline.
One of the key features of Trezor hardware wallets is that they are designed to be resistant to various physical and software attacks. They use a combination of secure elements and encryption to protect the user’s private keys from being compromised.
However, despite their strong security features, Trezor hardware wallets are not completely immune to vulnerabilities. Several security researchers have identified potential attack vectors that could be exploited to compromise the security of these wallets.
Potential Vulnerabilities:

- Firmware Vulnerabilities: The firmware running on Trezor hardware wallets can contain vulnerabilities that hackers can exploit. These vulnerabilities could allow an attacker to gain control over the device and extract the user’s private keys.
- Supply Chain Attacks: Trezor hardware wallets are manufactured and distributed through a complex supply chain. If any malicious actor gains access to the supply chain, they could tamper with the hardware wallets and add backdoors or other malicious components.
- Phishing Attacks: Phishing attacks are another potential vulnerability for Trezor hardware wallets. Attackers can create convincing phishing websites or emails that trick users into entering their private key or recovery seed on a malicious site, giving the attacker access to their funds.
Protecting Against Vulnerabilities:
While there are vulnerabilities that exist, there are also steps that users can take to protect themselves and mitigate these risks. It is crucial for users to stay vigilant and follow best practices when using Trezor hardware wallets:
- Always verify the integrity of the device before use, especially if purchased from a third-party seller.
- Keep the firmware of the hardware wallet up to date. Manufacturers often release firmware updates to fix vulnerabilities and enhance security.
- Avoid clicking on suspicious links or opening attachments in emails, as these may be phishing attempts.
- Only enter sensitive information, such as private keys or recovery seeds, on the official Trezor website or wallet software.
- Consider using a passphrase in addition to the PIN for added security.
- Store the recovery seed securely in a separate location from the hardware wallet itself, preferably in a physical format.
By following these precautions, users can minimize the risks associated with using Trezor hardware wallets and ensure the security of their cryptocurrencies.
Common Hacking Techniques Exploited to Access Trezor Hardware Wallets

Phishing
One of the most common hacking techniques used to gain access to Trezor hardware wallets is phishing. This technique involves tricking users into revealing their private keys or seed phrases by posing as a legitimate Trezor website or application. Phishing attacks can occur through email, social media, or even fake hardware wallets.
Malware
Another commonly used hacking technique is the use of malware. Malicious software can be disguised as legitimate applications or plugins and can infect a user’s computer or smartphone. Once installed, the malware can monitor the user’s activities and capture sensitive information, such as private keys or seed phrases, when they are entered into the Trezor hardware wallet.
Brute Force Attacks
Brute force attacks involve systematically trying every possible combination until the correct one is found. In the context of Trezor hardware wallets, this means attempting to guess the user’s PIN or passphrase. Hackers may use automated tools that can quickly iterate through thousands or even millions of combinations in a short amount of time.
Physical Access
Physical access to the Trezor hardware wallet can also be a vulnerability. If a hacker is able to physically steal or gain access to the device, they may be able to extract the private keys or seed phrases stored on it. This can be done through various techniques, such as disassembling the device or using specialized hardware tools.
Supply Chain Attacks
Supply chain attacks involve compromising the security of a product or component during its manufacturing or distribution process. In the context of Trezor hardware wallets, this can include inserting malicious code or hardware into the device during production. This can give hackers a backdoor into the wallet, allowing them to access the user’s private keys or seed phrases remotely.
Social Engineering
Social engineering involves manipulating individuals into divulging sensitive information or performing actions that may compromise their security. Hackers may use various tactics, such as impersonating customer support representatives or posing as trusted individuals, to trick users into revealing their private keys or seed phrases.
Conclusion
It is important for Trezor hardware wallet users to be aware of these common hacking techniques and to take steps to protect their private keys and seed phrases. This includes using strong, unique passwords and keeping them secure, being wary of phishing attempts, regularly updating firmware and software, and verifying the authenticity of hardware wallets.
Protecting Your Trezor Hardware Wallet from Potential Cyber Threats

When it comes to the security of your digital assets, protecting your Trezor hardware wallet from potential cyber threats is of utmost importance. With the rise in popularity of cryptocurrencies, hackers have become more sophisticated in their attempts to gain unauthorized access to wallets.
Here are some measures you can take to ensure the safety of your Trezor hardware wallet:
1. Keep Your Firmware Updated
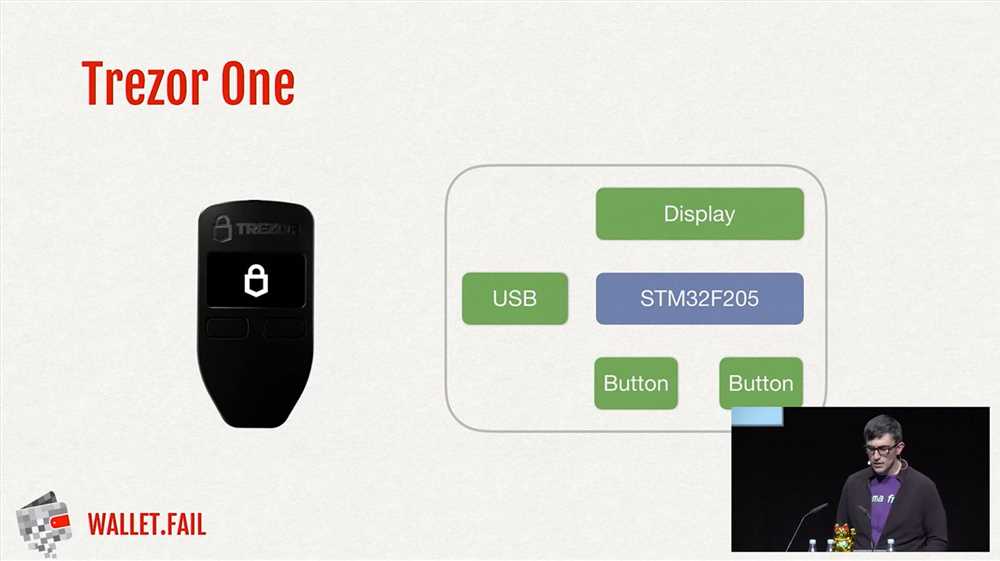
Regularly updating the firmware of your Trezor hardware wallet is crucial as it helps address any potential vulnerabilities. The wallet manufacturer often releases firmware updates that include security patches and bug fixes. By keeping your firmware up to date, you can reduce the chances of falling victim to cyberattacks.
2. Use a Strong and Unique PIN

Your PIN serves as the first line of defense against unauthorized access to your Trezor wallet. Make sure to choose a strong and unique PIN that is not easily guessable. Avoid using common patterns or sequences of numbers. By selecting a complex PIN, you can add an extra layer of protection to your wallet.
Remember: Do not share your PIN with anyone, and avoid storing it on your computer or phone.
3. Enable Two-Factor Authentication

Enabling two-factor authentication (2FA) adds an additional layer of security to your Trezor hardware wallet. By requiring a second form of verification, such as a code from an authenticator app or a physical security key, it becomes much more difficult for hackers to gain access to your wallet even if they manage to obtain your PIN.
Note: It is important to securely store your backup codes or physical security keys in case you lose access to your 2FA device.
By following these simple steps, you can significantly enhance the security of your Trezor hardware wallet and protect your digital assets from potential cyber threats. Remember, taking proactive measures to safeguard your wallet is essential in the ever-evolving landscape of cybersecurity.
Question-answer:
What are the risks of hacking Trezor hardware wallets?
The risks of hacking Trezor hardware wallets include theft of cryptocurrencies, unauthorized access to sensitive user information, and the ability for attackers to manipulate transactions or steal private keys.
How can hackers exploit vulnerabilities in Trezor hardware wallets?
Hackers can exploit vulnerabilities in Trezor hardware wallets through various methods such as phishing attacks, supply chain attacks, physical tampering, or by exploiting software vulnerabilities.
What steps can users take to protect their Trezor hardware wallets from hacking?
Users can protect their Trezor hardware wallets from hacking by keeping their firmware and software up to date, using strong and unique passwords, enabling two-factor authentication, being cautious of phishing attempts, and storing their recovery seeds in a secure location.


