
Trezor Wallet Software vs Hardware Wallets Which Offers Superior Protection

In the digital age, protecting your cryptocurrency assets is of utmost importance. With the rise of cyber threats and hacking attempts, it is crucial to choose a secure and reliable wallet to store your digital currencies. Two popular options in the market are Trezor Wallet Software and Hardware Wallets. While both offer protection for your digital assets, they have different levels of security and convenience.
Trezor Wallet Software is a software-based wallet that allows you to securely manage your cryptocurrencies on your computer or mobile device. It offers a user-friendly interface and features like multi-signature support and two-factor authentication for added security. With Trezor Wallet Software, you have full control over your private keys, ensuring that you are the sole owner of your digital assets.
On the other hand, Hardware Wallets are physical devices specifically designed to store and protect your digital currencies. They offer an offline storage solution, keeping your private keys away from the internet and potential hackers. With their built-in security features, such as tamper-proof seals and PIN codes, Hardware Wallets provide an extra layer of protection for your digital assets.
When it comes to protection levels, Hardware Wallets are considered the gold standard in securing your cryptocurrencies. Due to their isolated environment and offline storage, they are less susceptible to online attacks or malware. However, Trezor Wallet Software also provides a high level of security with its robust encryption and authentication protocols. The choice between the two ultimately depends on your preferences and needs.
In conclusion, both Trezor Wallet Software and Hardware Wallets offer strong protection for your digital currencies. While Hardware Wallets provide the highest level of security, Trezor Wallet Software offers convenience and accessibility. It is important to weigh the pros and cons of each option and choose the one that best suits your individual requirements and risk tolerance.
Trezor Wallet Software vs Hardware Wallets
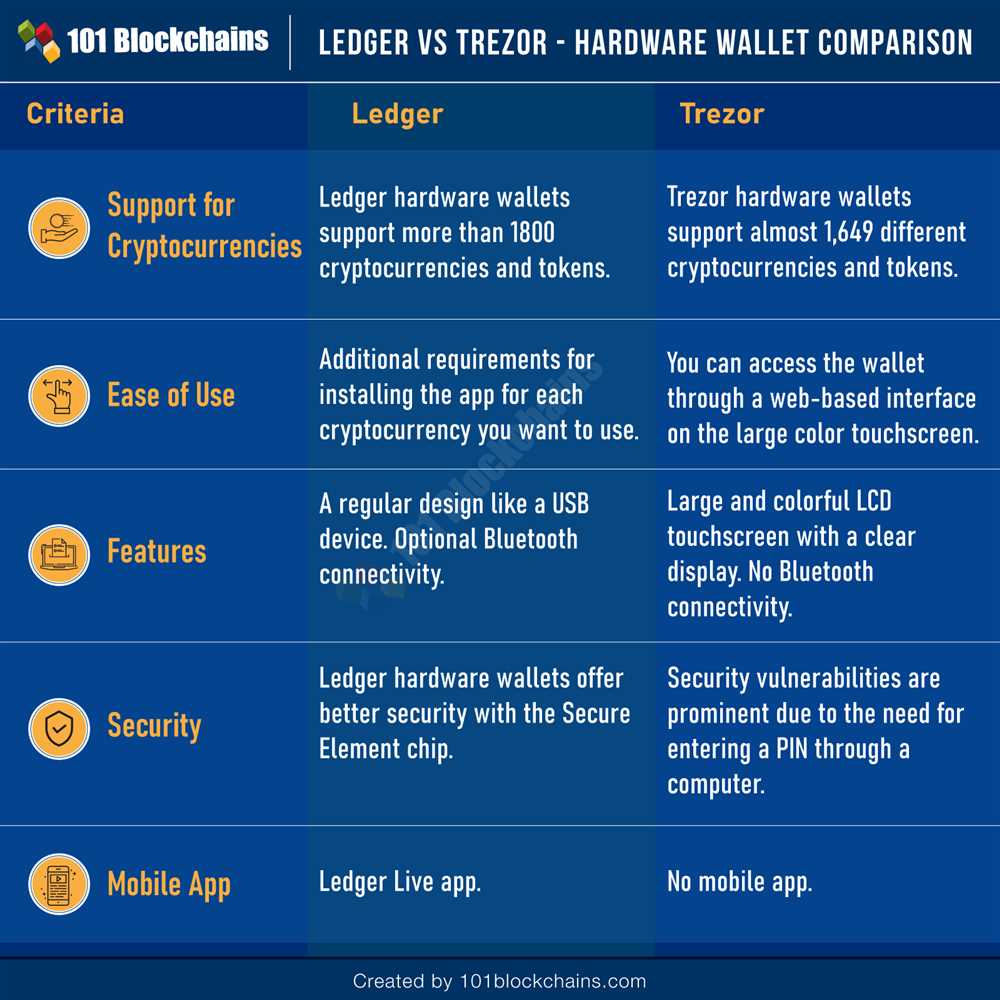
When it comes to protecting your cryptocurrency, there are two main options to consider: Trezor wallet software and hardware wallets. Both offer a high level of security, but there are some key differences between the two. Let’s take a closer look at how Trezor wallet software compares to hardware wallets.
Security: One of the main advantages of using a hardware wallet like Trezor is the enhanced security it offers. Hardware wallets store your private keys offline, which makes it virtually impossible for hackers to gain access to them. On the other hand, Trezor wallet software operates on your computer or mobile device, which makes it slightly more vulnerable to security breaches.
Convenience: While hardware wallets provide superior security, they can be less convenient to use compared to Trezor wallet software. With a hardware wallet, you need to physically connect it to your computer or mobile device to manage your cryptocurrency. Trezor wallet software, on the other hand, allows you to access your funds and make transactions directly from your computer or mobile device with just a few clicks.
Compatibility: Trezor wallet software is compatible with a wide range of devices and operating systems, including Windows, macOS, Linux, Android, and iOS. This means that you can use it on virtually any device you own. Hardware wallets, on the other hand, may have more limited compatibility and may not work with all devices and operating systems.
User Interface: When it comes to user interface, Trezor wallet software offers a more user-friendly experience compared to hardware wallets. With its intuitive design and easy-to-use interfaces, managing your cryptocurrency becomes a seamless process. Hardware wallets, while secure, may have a steeper learning curve and require some technical knowledge to operate.
Cost: In terms of cost, Trezor wallet software is generally free to use. However, you may need to pay for additional features or services. Hardware wallets, on the other hand, require an upfront investment to purchase the device. While the cost may vary depending on the brand and model, hardware wallets are generally more expensive than using Trezor wallet software.
| Trezor Wallet Software | Hardware Wallets | |
|---|---|---|
| Security | More vulnerable to security breaches | Enhanced security with offline storage |
| Convenience | Easy access and transactions | Requires physical connection to manage cryptocurrency |
| Compatibility | Compatible with various devices and operating systems | May have limited compatibility |
| User Interface | User-friendly and intuitive | May have a steeper learning curve |
| Cost | Free with potential additional costs | Requires upfront investment |
In conclusion, both Trezor wallet software and hardware wallets have their own advantages and disadvantages. If security is your top priority, a hardware wallet may be the better choice. However, if convenience and a user-friendly experience are more important to you, Trezor wallet software can provide a suitable option.
Comparison of Protection Levels
When it comes to protecting your cryptocurrency assets, it is crucial to choose a wallet that offers the highest level of security. Both Trezor Wallet Software and hardware wallets are designed to provide a safe and secure environment for storing your digital coins, but there are some key differences in their protection levels.
Hardware Security

Hardware wallets, such as the Trezor Wallet, are specifically designed for storing cryptocurrencies offline, making them less vulnerable to hacking attempts. These wallets utilize physical buttons and secure chips to safeguard your private keys, ensuring that they are never exposed to the internet.
With a hardware wallet, your private keys are stored on a separate device, disconnected from the internet, which significantly reduces the risk of unauthorized access. Even if your computer is infected with malware, your cryptocurrencies will remain safe.
Software Security

On the other hand, Trezor Wallet Software offers a higher level of convenience, as it can be installed directly on your computer or mobile device. This allows you to access your cryptocurrency assets easily and quickly, without the need for a separate hardware device.
However, software wallets are more susceptible to malware attacks and phishing attempts. If your computer or mobile device is compromised, hackers can gain access to your private keys and steal your cryptocurrencies. Therefore, it is crucial to ensure that your device is secure and protected against malware and other malicious activities.
- Trezor Wallet Software offers 2-factor authentication, enhancing the security of your wallet by requiring an additional verification step.
- Hardware wallets, on the other hand, provide an added layer of protection by isolating your private keys from the internet and possible malware attacks.
- Both options offer recovery seed phrases, which allow you to regain access to your wallet in case of loss or damage.
- Hardware wallets are generally considered to be the most secure option for storing large amounts of cryptocurrency, while software wallets may be more suitable for smaller transactions and day-to-day use.
In conclusion, the level of protection provided by Trezor Wallet Software and hardware wallets differs. Hardware wallets offer enhanced security by keeping your private keys offline, while software wallets provide greater convenience but are more vulnerable to malware attacks. It is important to weigh the pros and cons of each option and choose the one that best suits your individual needs and risk tolerance.
Overview of Trezor Wallet Software

Trezor Wallet Software is a digital wallet that provides a secure and user-friendly way to manage cryptocurrencies. It offers a range of features and functionalities that make it an ideal choice for both beginners and advanced users in the crypto world.
User Interface
The Trezor Wallet Software has a clean and intuitive user interface, making it easy for users to navigate and interact with their digital assets. The interface is designed to provide a seamless experience, allowing users to easily send, receive, and store their cryptocurrencies.
Security Features

One of the main advantages of the Trezor Wallet Software is its emphasis on security. It uses multiple layers of protection to ensure that users’ funds and private keys are safe from hackers or other malicious actors.
- Hardware Wallet Integration: The software is designed to work seamlessly with Trezor hardware wallets, providing an additional layer of security. The private keys are stored securely in the hardware wallet, reducing the risk of theft or unauthorized access.
- Two-Factor Authentication (2FA): Trezor Wallet Software supports 2FA, adding an extra layer of security to the login process. This feature requires users to provide a second form of verification, such as a physical token or a fingerprint scan, to access their wallets.
- Passphrase Protection: Users can enable passphrase protection to add an extra layer of security to their wallets. This feature requires users to enter a passphrase in addition to their PIN or password, making it harder for unauthorized individuals to access their funds.
- Backup and Recovery: Trezor Wallet Software provides a backup and recovery feature, allowing users to restore their wallets in case of loss or theft. The software generates a 24-word recovery seed that can be used to restore the wallet on a new device.
All these security features make Trezor Wallet Software a highly secure option for storing and managing cryptocurrencies.
Security Features and Benefits
When it comes to protecting your cryptocurrencies, security is of utmost importance. Trezor Wallet Software and hardware wallets offer various security features and benefits to ensure the safety of your digital assets.
One of the key security features of Trezor Wallet Software is its strong encryption. The software uses cutting-edge cryptographic algorithms to encrypt your private keys and keep them safe from unauthorized access. This means that even if your computer is compromised, your cryptocurrencies will remain secure.
Hardware wallets, on the other hand, offer an additional layer of security by keeping your private keys offline. These devices store your private keys on a secure chip, which is not connected to the internet. This makes it virtually impossible for hackers to access your private keys remotely.
Another security feature of hardware wallets is the use of secure elements. These secure chips are designed to resist physical attacks and tampering. They store your private keys in an isolated environment, protecting them from being exposed to potential threats.
Both Trezor Wallet Software and hardware wallets offer the benefit of multi-factor authentication. This means that in order to access your cryptocurrencies, you need to provide multiple forms of authentication, such as a PIN code or a password. This adds an extra layer of protection, making it more difficult for attackers to gain access to your funds.
Furthermore, Trezor Wallet Software and hardware wallets have built-in features to protect against malware and phishing attacks. They use secure protocols and provide users with warnings and alerts if they detect any suspicious activity or potential threats.
In conclusion, Trezor Wallet Software and hardware wallets offer a range of security features and benefits to ensure the safety of your cryptocurrencies. Whether it’s strong encryption, offline storage, secure elements, or multi-factor authentication, these tools provide the necessary tools to protect your digital assets from potential threats.
Hardware Wallets: What Makes Them Different

When it comes to protecting your cryptocurrency assets, hardware wallets offer a level of security that sets them apart from other wallet options. Here are some key factors that make hardware wallets different:
1. Offline Storage
Unlike software wallets or online exchanges, hardware wallets store your private keys offline. This means that they are not connected to the internet, making it virtually impossible for hackers to access your funds remotely. By keeping your private keys offline, hardware wallets provide an added layer of protection against cyber attacks.
2. Encryption
Hardware wallets use advanced encryption algorithms to secure your private keys. This ensures that even if someone gains physical access to your device, they won’t be able to retrieve your private keys without your authorization. The encryption methods used in hardware wallets are highly secure and resistant to hacking attempts.
3. Secure Element

Many hardware wallets come equipped with a secure element, a small chip that provides additional security for your private keys. The secure element is designed to withstand physical attacks and tampering, making it extremely difficult for anyone to extract the private keys stored within the device.
4. Two-Factor Authentication

Most hardware wallets require two-factor authentication (2FA) to access your funds. This means that in addition to entering your PIN code, you also need to physically confirm transactions on the device itself. This provides an extra layer of security, as even if someone manages to guess or steal your PIN code, they won’t be able to complete transactions without physical access to the device.
5. Recovery Options
In the event that your hardware wallet is lost, stolen, or damaged, most devices offer recovery options. These typically involve generating a recovery seed, a series of randomly generated words that can be used to restore access to your funds. It’s important to store this recovery seed in a safe and secure location, as anyone with access to it can potentially gain control over your funds.
In conclusion, hardware wallets are different from other wallet options due to their offline storage, encryption, secure element, two-factor authentication, and recovery options. These features combine to provide a high level of protection for your cryptocurrency assets, making hardware wallets an ideal choice for storing and managing your digital wealth.
Understanding the Enhanced Security

When it comes to protecting your digital assets, security is of utmost importance. Trezor Wallet Software and hardware wallets both offer enhanced security measures to ensure the safety of your cryptocurrencies. Understanding how these security features work is crucial in making an informed decision about which option is best for you.
Trezor Wallet Software utilizes a combination of encryption and authentication to protect your funds. The software is designed to create a secure environment on your device, isolated from any potential malware or hacking attempts. It uses the concept of “seeds” or a random phrase that acts as the master key to your account. This seed is generated and stored offline, making it virtually impossible for hackers to gain access to your funds. Additionally, the software includes a PIN code and passphrase feature, adding an extra layer of protection to your wallet.
On the other hand, hardware wallets are physical devices that provide an even higher level of security. These wallets store your private keys offline, keeping them away from potential threats on your computer or smartphone. When you want to make a transaction, you need to physically connect the hardware wallet to your device and enter a PIN code. This two-factor authentication ensures that even if your computer or phone is compromised, your cryptocurrency assets remain safe. The physical nature of the hardware wallet also protects against remote attacks and phishing attempts.
| Trezor Wallet Software | Hardware Wallets |
|---|---|
| Utilizes encryption and authentication | Stores private keys offline |
| Creates a secure environment on your device | Requires physical connection for transactions |
| Uses seeds as master keys | Provides two-factor authentication |
| Includes PIN code and passphrase feature | Protects against remote attacks and phishing attempts |
While both options offer enhanced security, hardware wallets have the advantage of being completely offline, reducing the risk of online attacks. However, they may be less convenient to use as they require physical interaction. Trezor Wallet Software provides a balance between security and usability by offering a secure environment on your device. Ultimately, the choice between the two depends on your individual preferences and the level of security you require for your digital assets.
Question-answer:
What is a hardware wallet?
A hardware wallet is a physical device that is used to store and manage cryptocurrency private keys offline. It provides an extra layer of security by keeping the private keys separate from internet-connected devices.
How does a Trezor wallet protect my cryptocurrency?
Trezor wallet protects your cryptocurrency by storing your private keys offline on the hardware device. It uses advanced encryption algorithms to secure the keys and requires physical verification for transactions to take place.
Can Trezor wallets be hacked?
Trezor wallets are designed with strong security measures in place to prevent hacking. While no system is completely hack-proof, Trezor wallets have not been successfully hacked to date.
What are the advantages of using a hardware wallet over a software wallet?
Using a hardware wallet provides several advantages over a software wallet. Hardware wallets keep the private keys offline, protecting them from malware and online attacks. They also provide secure transaction verification and are more resistant to physical damage or loss.
Is it necessary to use a hardware wallet for cryptocurrency storage?
While it is not strictly necessary to use a hardware wallet for cryptocurrency storage, it is highly recommended for those who want to ensure the highest level of security for their funds. Hardware wallets offer the best protection against hacking and unauthorized access.


