
Trezor Breach: Anatomy of a Cyber Attack on Cryptocurrency Wallets

In the fast-evolving world of cryptocurrency, security is of utmost importance. With millions of dollars worth of digital assets at stake, investors and traders rely on secure storage solutions to protect their funds. However, a recent cyber attack on Trezor, one of the leading hardware wallet providers, has brought to light the vulnerabilities that exist in cryptocurrency wallets.
Trezor, known for its highly secure hardware wallets, was targeted by a group of skilled hackers who managed to gain unauthorized access to its systems. The breach not only compromised sensitive user data but also exposed the weaknesses in the wallet’s security infrastructure.
One of the main vulnerabilities exploited by the hackers was a flaw in the random number generation process used by Trezor. This flaw allowed the attackers to predict the private keys generated by the wallet, effectively giving them control over the funds stored in it. This highlights the critical importance of secure random number generation in cryptocurrency wallets and the need for constant evaluation and improvement of security measures.
The repercussions of the Trezor breach are significant. It has not only shaken the trust of many cryptocurrency users but has also raised questions about the overall security of hardware wallets. While Trezor has taken immediate steps to fix the vulnerabilities and enhance its security protocols, this incident serves as a wake-up call for the entire industry.
The Impact of the Trezor Breach
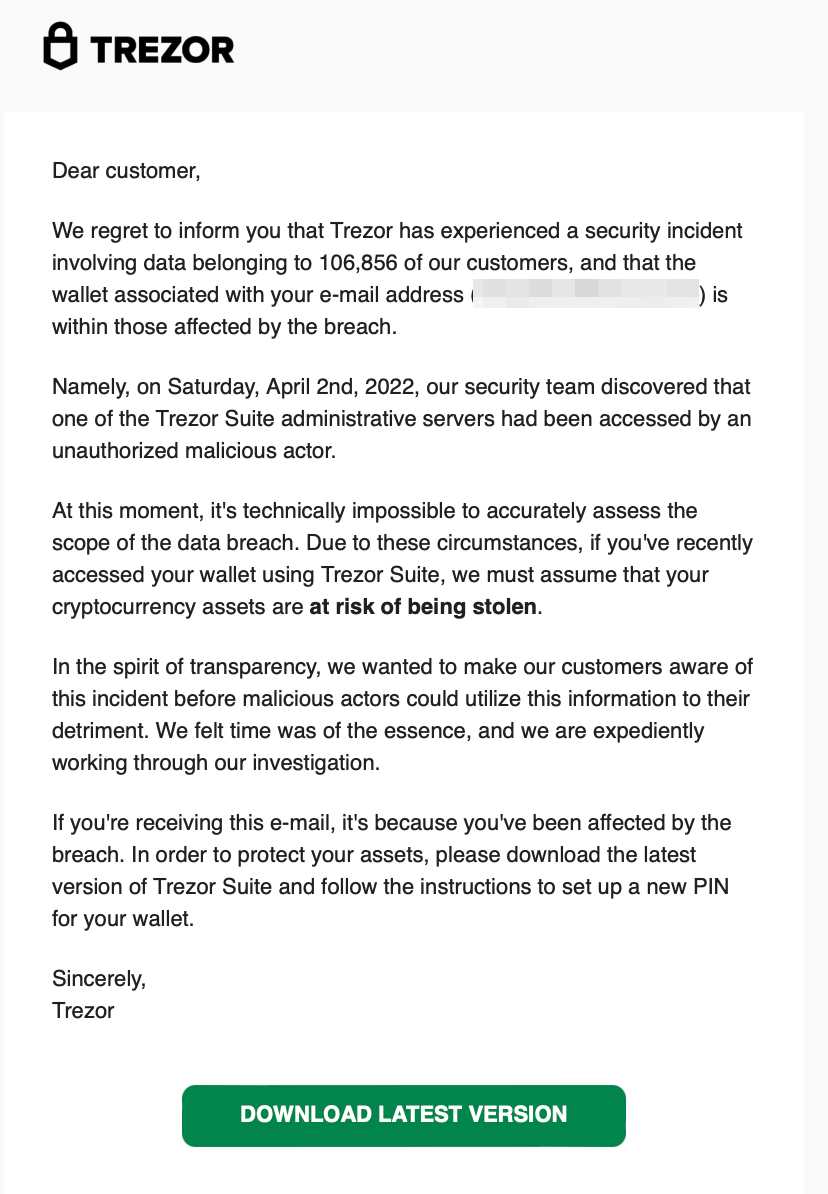
The Trezor breach has had a significant impact on the cryptocurrency community and has raised concerns about the security of digital wallets. This cyber attack exposed vulnerabilities in cryptocurrency wallets, leading to potential risks for users.
One of the main impacts of the Trezor breach is the loss of funds for affected users. Hackers were able to gain unauthorized access to the wallets, allowing them to steal valuable cryptocurrencies. This has resulted in financial losses for individuals who stored their digital assets on Trezor wallets.
Furthermore, the breach has eroded trust in cryptocurrency wallets and security measures. Users now question the safety of their investments and whether their wallets can truly protect their assets. This lack of confidence may lead to a decrease in adoption of cryptocurrencies, as individuals may fear the potential risks associated with storing their funds in digital wallets.
The Trezor breach has also highlighted the need for stronger security measures within the cryptocurrency industry. Wallet providers and developers must now invest in improving their security protocols and implementing measures to prevent future breaches. This includes enhancing encryption techniques, implementing multi-factor authentication, and conducting regular security audits to identify and fix vulnerabilities.
Additionally, the incident serves as a reminder for cryptocurrency users to take their own security precautions. This includes using strong and unique passwords, enabling two-factor authentication, and regularly updating their wallets’ firmware to ensure the latest security patches are applied.
In conclusion, the Trezor breach has had a significant impact on the cryptocurrency community. It has exposed vulnerabilities in cryptocurrency wallets, resulting in financial losses for users and undermining trust in digital wallets. However, it also serves as a wake-up call for the industry to improve its security measures and for users to take their own security precautions.
Discovering the Vulnerabilities in Cryptocurrency Wallets
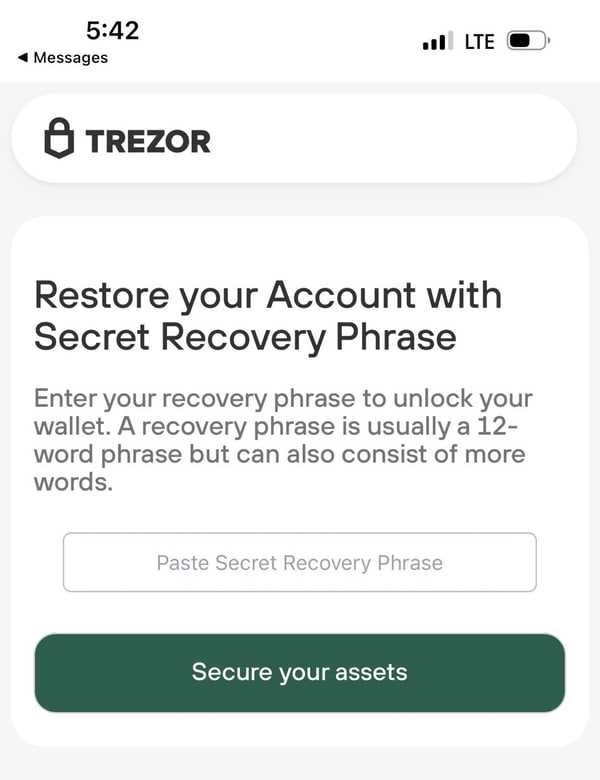
In recent years, the rise of cryptocurrencies has led to an increased demand for secure storage solutions. Cryptocurrency wallets, designed to keep digital assets safe, have become a crucial component of the cryptocurrency ecosystem. However, as the Trezor breach has shown, even these wallets can be vulnerable to cyber attacks.
Understanding the Risks
There are several vulnerabilities that can be exploited by hackers to gain access to cryptocurrency wallets. One common vulnerability is the use of weak or easily guessable passwords. Many individuals fail to use strong passwords, making it easier for hackers to crack the codes and gain unauthorized access to their wallets.
Another vulnerability lies in the software and firmware used by the wallets. As in the case of the Trezor breach, flaws in the wallet’s firmware can be exploited to gain unauthorized access or manipulate transactions. Wallet providers must regularly update their software and firmware to address any potential vulnerabilities and ensure the security of their users’ assets.
The Role of Social Engineering
Social engineering techniques are also commonly used to exploit cryptocurrency wallet vulnerabilities. Phishing attacks, for example, involve sending fraudulent emails or messages to trick wallet users into disclosing their passwords or private keys. These attacks often appear to be from legitimate sources, making it difficult for individuals to spot the deception.
Additionally, hackers may target individuals through social media platforms, pretending to offer support or guidance. These interactions can lead to individuals inadvertently sharing sensitive information or unwittingly installing malware onto their devices.
Protecting Your Wallet
While the vulnerabilities in cryptocurrency wallets may seem concerning, there are steps you can take to protect your digital assets. Firstly, ensure that you use strong, unique passwords for all your wallets and accounts. Additionally, enable two-factor authentication whenever possible to add an extra layer of security.
Regularly updating your wallet’s software and firmware can also help to mitigate potential vulnerabilities. Keep an eye on the wallet provider’s website or subscribe to their newsletter to stay informed about any updates or security patches.
Finally, it’s crucial to remain vigilant and skeptical of any suspicious communication you receive. Be cautious of emails or messages asking for your wallet password or private keys and avoid clicking on any suspicious links. Remember, your digital security is in your hands.
In conclusion, identifying and addressing the vulnerabilities in cryptocurrency wallets is essential to safeguarding your digital assets. By understanding the risks, being aware of social engineering techniques, and taking proactive measures, you can significantly reduce the chances of falling victim to cyber attacks.
Steps to Secure Your Cryptocurrency Wallet
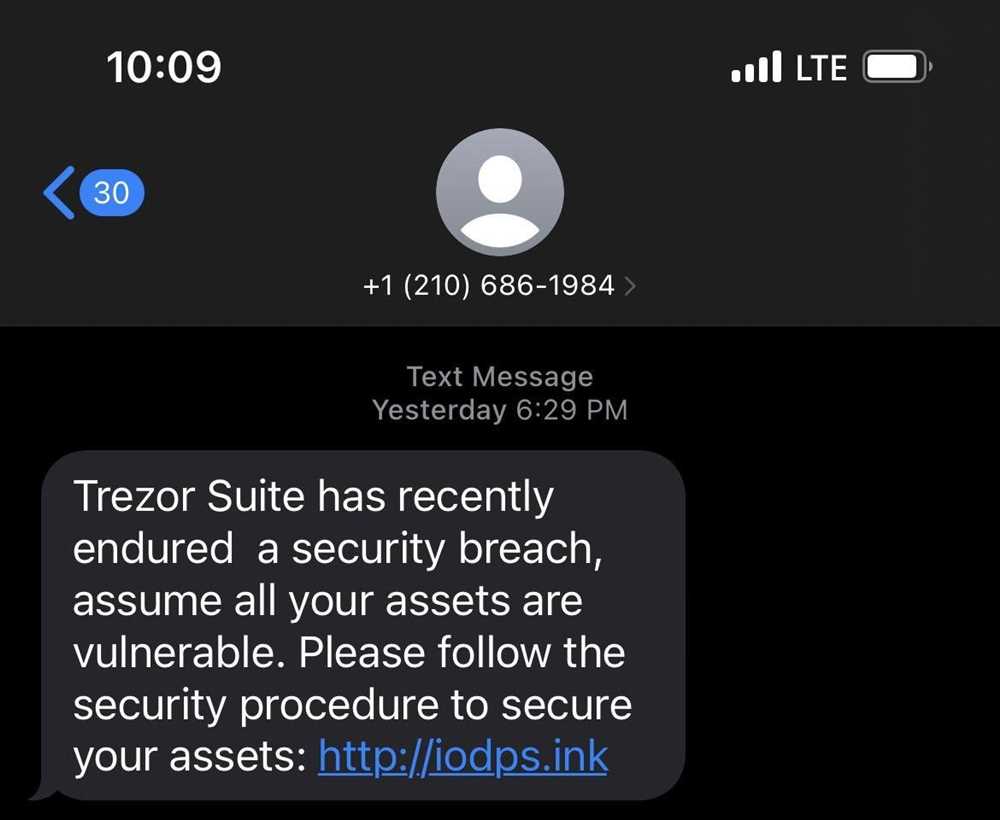
Securing your cryptocurrency wallet is crucial to protect your digital assets. Here are some steps you can take to enhance the security of your cryptocurrency wallet:
- Choose a Hardware Wallet: Consider using a hardware wallet like Trezor or Ledger. These wallets store your private keys offline, making them less vulnerable to cyber attacks.
- Enable Two-Factor Authentication (2FA): Activate 2FA on your cryptocurrency wallet. This adds an extra layer of security by requiring you to provide a second verification step, such as a code from your mobile device, whenever you log in or make a transaction.
- Create a Strong Password: Use a unique and complex password for your cryptocurrency wallet. Avoid using common phrases or easily guessable information. Consider using a password manager to generate and store secure passwords.
- Update Your Wallet Software: Regularly check for software updates for your cryptocurrency wallet and install them promptly. Updates often include security patches that fix vulnerabilities and protect against new threats.
- Be Cautious of Phishing Attempts: Be wary of suspicious emails, messages, or websites that claim to be from your cryptocurrency wallet provider. Phishing attempts can trick you into revealing your login credentials or private keys. Always verify the authenticity of any communication before taking any action.
- Backup Your Wallet: Create a backup of your cryptocurrency wallet and store it in a safe and secure location. This ensures that you can recover your funds in case of loss, theft, or hardware failure.
- Keep Your Operating System and Antivirus Software Updated: Install updates for your operating system and antivirus software to protect against malware and other virus attacks that could compromise the security of your cryptocurrency wallet.
- Use Secure Internet Connections: Avoid using public Wi-Fi networks or other unsecured internet connections when accessing your cryptocurrency wallet. Use a virtual private network (VPN) for added security.
- Be Mindful of Publicity: Be cautious about openly discussing your cryptocurrency holdings or transactions, both offline and online. Maintaining a low profile can help minimize the risk of targeted attacks.
- Monitor Your Transactions: Regularly review the transactions made from your cryptocurrency wallet. If you notice any unauthorized or suspicious activity, take immediate action to secure your funds and report it to your cryptocurrency wallet provider.
Implementing these steps can significantly enhance the security of your cryptocurrency wallet and protect your valuable digital assets from cyber threats.
Q&A:
What is the Trezor Breach?
The Trezor Breach refers to a cyber attack that exposed vulnerabilities in cryptocurrency wallets, specifically targeting the Trezor wallet.
How did the cyber attack on Trezor happen?
The details of the cyber attack on Trezor have not been fully disclosed yet. However, it is believed that hackers exploited a vulnerability in the wallet’s firmware to gain access to users’ funds.


