The Trezor Incident: Lessons Learned from a Security Breach

Keeping our digital assets safe has become more important than ever. With the increasing popularity of cryptocurrencies, hackers are constantly looking for vulnerabilities to exploit. The recent Trezor incident serves as a stark reminder that even the most secure hardware wallets are not immune to security breaches.
Trezor, one of the leading brands in the cryptocurrency hardware wallet industry, recently faced a major security breach. The incident shook the entire cryptocurrency community, raising concerns about the safety of hardware wallets and highlighting the need for better security practices.
This incident has shed light on several important lessons and takeaways. First and foremost, it reminds us that no system is completely foolproof. While hardware wallets like Trezor are designed to offer maximum security, hackers are constantly evolving their techniques to find new vulnerabilities. As users, we must remain vigilant and stay informed about the latest security practices.
Another important lesson from this incident is the value of regular software updates. Companies like Trezor work diligently to identify and fix any vulnerabilities that may arise. As users, it is crucial to regularly update our hardware wallets with the latest firmware to ensure that we have the most up-to-date security features and protections.
Overall, the Trezor incident serves as a stark reminder that we must always be proactive in protecting our digital assets. By staying informed, remaining vigilant, and adhering to best security practices, we can minimize the risk of falling victim to such security breaches in the future.
Understanding the Trezor Incident

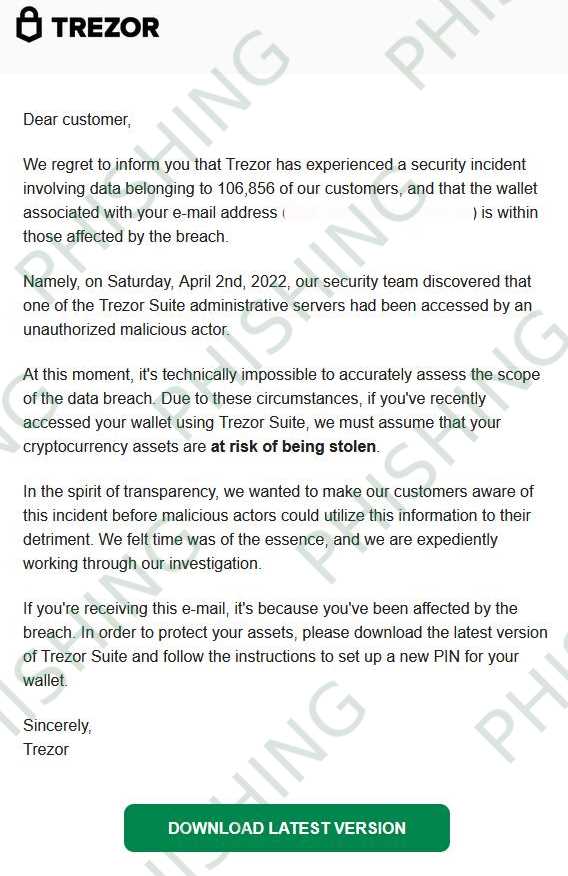
The Trezor incident serves as a cautionary tale for the importance of secure cryptocurrency storage and the potentially devastating consequences of a security breach. In January 2021, Trezor, a popular hardware wallet manufacturer, discovered that someone had acquired a database with customer information.
How did the breach happen?
First, it’s important to note that the breach did not expose any user’s private keys or directly compromise their cryptocurrency holdings. However, the stolen database contained valuable information such as names, email addresses, and shipping addresses. The exact details of the breach are not publicly known, but it appears that an attacker exploited a vulnerability in Trezor’s website infrastructure.
What can we learn from it?
1. Importance of secure infrastructure: The incident emphasizes the need for robust cybersecurity measures and ongoing vulnerability assessments. Companies in the cryptocurrency space must prioritize security and regularly update their code and infrastructure to protect customer data.
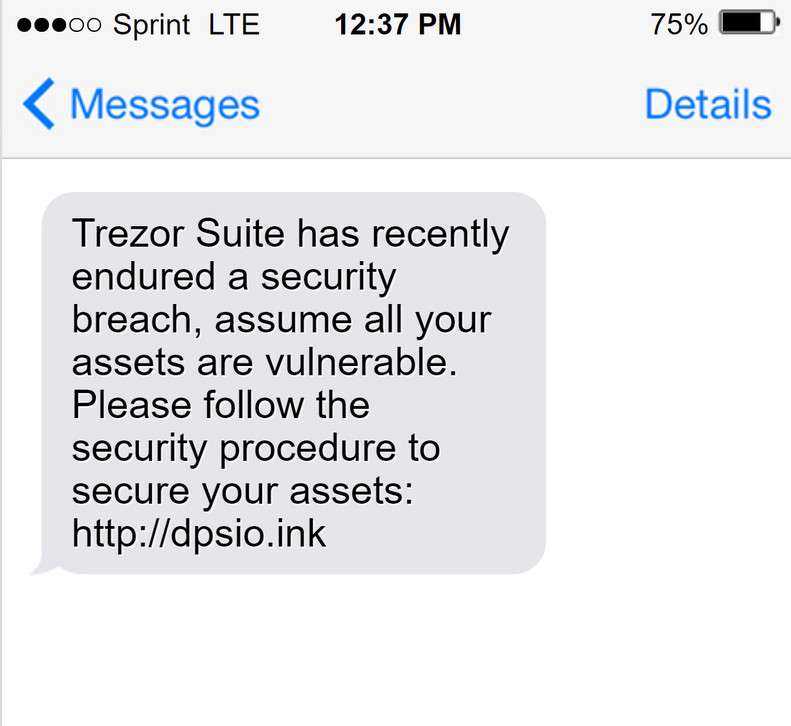
2. Threat of phishing attacks: The stolen customer information could be used in targeted phishing campaigns. Users need to remain vigilant and watch out for suspicious emails or messages, especially those asking for personal information or revealing their cryptocurrency holdings.
3. Multi-factor authentication: To enhance security, individuals should enable multi-factor authentication (MFA) wherever possible. MFA adds an extra layer of protection, making it more difficult for hackers to gain unauthorized access.
4. Educating users: Companies must actively educate their customers about best practices for securely storing and managing cryptocurrencies. This includes guidance on choosing strong passwords, enabling MFA, and avoiding suspicious links or emails.
Conclusion
The Trezor incident serves as a stark reminder of the constant threats faced by the cryptocurrency industry. It highlights the importance of maintaining high security standards, both for companies and individual users. By understanding the incident and implementing the lessons learned, we can collectively work towards a more secure crypto ecosystem.
Importance of Security Measures

Security measures are of utmost importance in any digital system, especially when it comes to storing and managing sensitive data like cryptocurrencies. The Trezor incident serves as a reminder of the risks involved and the need for robust security practices.
One of the key takeaways from the Trezor incident is the importance of strong encryption. Encryption scrambles data, making it unreadable to unauthorized users. It is crucial to use encryption algorithms that are resistant to attacks and regularly update the encryption protocols to stay ahead of potential vulnerabilities.
Another crucial security measure is two-factor authentication (2FA). 2FA adds an extra layer of security by requiring users to provide two forms of identification before accessing their accounts or making transactions. This can include something the user knows, like a password, and something the user has, like a physical device or a biometric identifier.
Regular software updates are also essential in maintaining security. Developers frequently release updates that patch vulnerabilities and improve the overall security of their systems. It is crucial for users to stay up-to-date with these updates and install them as soon as they become available.
Furthermore, users should be mindful of their online presence and avoid sharing sensitive information on unsecured websites or networks. This includes using strong, unique passwords for all online accounts and refraining from using public Wi-Fi networks for financial transactions.
A comprehensive security strategy should also include regular data backups. By regularly backing up important data, users can mitigate the risk of losing their valuable information in case of a security breach.
| Key Security Measures |
|---|
| Strong encryption |
| Two-factor authentication |
| Regular software updates |
| Vigilance in online activities |
| Regular data backups |
In conclusion, the Trezor incident highlights the critical importance of implementing robust security measures in any digital system. By prioritizing strong encryption, two-factor authentication, regular software updates, vigilance in online activities, and regular data backups, users can help safeguard their sensitive data and minimize the risk of security breaches.
Lessons Learned from the Trezor Incident

The Trezor incident serves as a stark reminder of the importance of strong security practices and constant vigilance when it comes to protecting digital assets.
1. Implement Multifactor Authentication: The incident highlighted the need for multifactor authentication to provide an additional layer of security. By requiring multiple forms of verification, such as something the user knows (password) and something the user has (a physical token), the likelihood of unauthorized access is significantly reduced.
2. Regularly Update Security Measures: It is crucial to stay up to date with the latest security measures and updates. This includes regularly updating software and firmware, as well as taking advantage of any security patches or fixes. By keeping security measures current, potential vulnerabilities can be addressed and mitigated.
3. Practice Safe Online Habits: Users should always exercise caution when interacting online. This includes avoiding suspicious websites, links, and downloads, as well as being wary of phishing attempts. By practicing safe online habits, the risk of falling victim to cyberattacks is significantly reduced.
4. Keep Private Keys Offline: The incident highlights the importance of keeping private keys offline and stored in secure hardware wallets. By keeping private keys offline, they are less susceptible to hacking attempts and unauthorized access. Hardware wallets, such as Trezor, provide an additional layer of protection for private keys.
5. Perform Regular Security Audits: Regularly auditing security measures can help identify potential vulnerabilities and address them before they are exploited. This includes conducting penetration testing, code reviews, and security assessments. By proactively assessing security measures, weaknesses can be identified and addressed.
6. Stay Informed: It is crucial to stay informed about the latest security threats and best practices. Subscribing to security newsletters and following reputable sources can provide valuable insights and guidance. By staying informed, users can actively take steps to protect their digital assets.
7. Educate and Train Users: User education and training play a crucial role in preventing security incidents. By teaching users about common security risks, best practices, and how to identify potential threats, the likelihood of falling victim to cyberattacks is reduced. Ongoing training and education are necessary to keep users up to date with the evolving threat landscape.
By learning from the Trezor incident and implementing these lessons, individuals and organizations can enhance their security practices and protect their digital assets from potential breaches.
Key Takeaways for Better Security
When it comes to securing your digital assets, the Trezor incident teaches us several important lessons:
1. Choose Your Wallet Carefully

It’s crucial to research and select a wallet that has a strong reputation for security. Look for wallets that have undergone independent security audits and have a track record of protecting users’ funds.
2. Keep Your Software Up to Date
Regularly update your wallet software, firmware, and operating system to ensure you have the latest security patches. Developers are constantly improving their software to address vulnerabilities, so it’s important to stay up to date.
3. Use Two-Factor Authentication

Enable two-factor authentication (2FA) whenever possible. This adds an extra layer of security by requiring you to provide a secondary form of verification, such as a code from a mobile app or a physical device.
4. Be Mindful of Phishing Attempts

Be cautious of any requests for your login credentials or personal information. Phishing attempts often come disguised as legitimate emails or websites. Always double-check the URL and ensure you’re interacting with the official website or software.
5. Keep Your Recovery Seed Secure

Your recovery seed is the key to accessing your digital assets if your wallet is lost or stolen. Store it securely, preferably offline, and never share it with anyone. Consider using a hardware wallet for added protection.
6. Stay Informed on Security Practices
Stay up to date with the latest security practices and news within the cryptocurrency community. Educate yourself on common security risks and best practices for protecting your assets.
By following these key takeaways, you can significantly enhance the security of your digital assets and reduce the risk of falling victim to a security breach.
Q&A:
What is the Trezor Incident?
The Trezor Incident refers to a security breach that occurred in 2020 involving the Trezor hardware wallet. During the incident, a hacker was able to gain unauthorized access to a user’s funds by exploiting a vulnerability in the wallet’s firmware.
How did the hacker gain access to the user’s funds?
The hacker exploited a vulnerability in the firmware of the Trezor hardware wallet. By taking advantage of this vulnerability, they were able to extract the private keys from the wallet and gain access to the user’s funds.
Was the vulnerability in the Trezor hardware wallet fixed after the incident?
Yes, the vulnerability in the Trezor hardware wallet was fixed after the incident. The company released a firmware update that addressed the vulnerability and urged all users to update their devices as soon as possible to mitigate the risk of similar attacks.
What lessons can be learned from the Trezor Incident?
The Trezor Incident highlights the importance of regularly updating firmware and software to protect against known vulnerabilities. It also emphasizes the need for users to store their cryptocurrency securely and follow best practices such as using strong, unique passwords and enabling two-factor authentication. Additionally, this incident underscores the risks associated with storing large amounts of cryptocurrency on a single device.


