
The Potential Dangers of Exclusively Trusting Trezor for Cryptocurrency Security

In the world of cryptocurrency, security is paramount. With the rising popularity and value of digital assets, it’s crucial for investors and enthusiasts to protect their holdings from potential threats. One popular solution is hardware wallets, with Trezor being one of the leading choices. While Trezor offers a high level of security, it’s important to understand the potential pitfalls of relying solely on this device.
Trezor is a hardware wallet that stores cryptocurrency private keys offline. This ensures that your keys are not susceptible to hacking or online theft. With its strong encryption and secure microprocessors, Trezor provides peace of mind for many users. However, it’s essential to recognize that no security measure is foolproof, and there are potential vulnerabilities to consider.
One issue to be aware of is the potential for physical damage or loss of the device. Trezor wallets are small and portable, making them convenient for users. However, this also means that they can be easily misplaced or damaged. If you lose your Trezor or it gets damaged, there is a risk of permanently losing access to your cryptocurrency. It’s crucial to have a backup plan in place and take extra precautions to ensure the safety of your device.
Another potential pitfall is the reliance on a single point of failure. While Trezor wallets are designed to be secure, they are not immune to bugs or vulnerabilities. If a flaw is discovered in the firmware or software of the device, it could potentially compromise the security of your private keys. Relying solely on Trezor for your crypto security means putting all your eggs in one basket. It’s important to diversify your security measures and consider additional layers of protection.
Risks of Exclusive Trezor Dependency
While Trezor is a popular and widely trusted hardware wallet, relying solely on it for crypto security can pose certain risks. It’s important for crypto holders to be aware of these potential pitfalls to ensure the safety of their digital assets.
- Single Point of Failure: Exclusively relying on Trezor as the sole means of securing crypto assets creates a single point of failure. If the Trezor device malfunctions, is lost, or is stolen, the user could potentially lose access to their funds without any backup plan in place.
- Vulnerability to Physical Threats: While Trezor provides a high level of security against remote attacks, it is still susceptible to physical threats. If an attacker gains physical access to the Trezor device, they might be able to compromise its security measures and gain control over the stored crypto assets.
- Dependency on Third-Party Software: Using Trezor often requires the installation of third-party software and applications. This exposes the user to potential vulnerabilities and security risks associated with those external programs. If the third-party software is compromised, the security of the Trezor device and the stored crypto assets could be compromised as well.
- Limited Compatibility: Although Trezor supports a wide range of cryptocurrencies, there are certain tokens and coins that may not be compatible with the device. A crypto holder relying exclusively on Trezor may face limitations and restrictions when it comes to managing and securing certain digital assets.
- Loss of Backup Options: In the event of a technical failure or loss of access to the Trezor device, relying solely on Trezor means that the user may have limited or no backup options available. It is essential to have alternative security measures and backup strategies in place to prevent loss or theft of crypto assets.
While Trezor can provide a secure and convenient way to store and manage crypto assets, it is advisable to diversify security measures and not rely solely on a single device or method. Implementing a multi-layered security approach can help mitigate the risks and potential pitfalls associated with exclusive Trezor dependency.
Security Vulnerabilities and Exploits
While Trezor is generally considered a reliable and secure hardware wallet for cryptocurrencies, like any technology, it is not without its potential security vulnerabilities and exploits. It is important for users to be aware of these potential risks and take appropriate precautions to protect their digital assets.
Software Vulnerabilities
One potential vulnerability is software bugs or flaws that could be exploited by attackers. Although Trezor has a solid reputation for security, it is not immune to programming errors. If a bug or vulnerability is discovered, hackers could potentially exploit it to gain unauthorized access to a user’s private keys or encrypted data.
Trezor regularly releases firmware updates to address any known vulnerabilities and improve security. It is crucial for users to promptly install these updates to ensure their devices are protected against any potential exploits.
Physical Tampering
Another potential security risk is physical tampering with the device. If an attacker gains access to a user’s Trezor wallet, they may attempt to compromise its integrity by tampering with the hardware.
To mitigate this risk, it is important to keep the Trezor wallet in a secure location and be cautious when handling it. Users should also ensure that they only purchase their devices from trusted sources to reduce the risk of receiving a compromised or tampered device.
Phishing Attacks
Phishing attacks are another common method used by hackers to steal sensitive information, including cryptocurrency credentials. In a phishing attack, the attacker poses as a legitimate entity or service and tricks the user into revealing their private key or seed phrase.
Trezor users should be cautious of any suspicious emails, links, or requests for sensitive information. It is important to only access the Trezor wallet through the official website and never enter any sensitive information on a website that is not verified as legitimate.
To protect against phishing attacks:
- Double-check the URL of the website before entering any sensitive information.
- Avoid clicking on suspicious links or downloading unknown files.
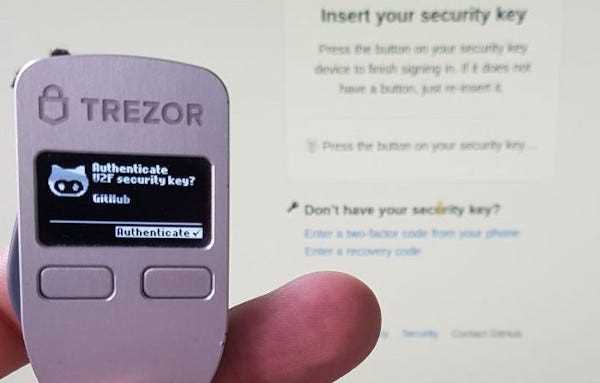
- Enable two-factor authentication for additional security.
- Keep antivirus software up to date to detect and prevent phishing attempts.
In conclusion, while Trezor is a reputable hardware wallet, it is important for users to be aware of potential security vulnerabilities and take necessary precautions to protect their crypto assets.
Single Point of Failure
While Trezor is a popular choice for securing cryptocurrencies, it is important to recognize that relying solely on this hardware wallet can create a single point of failure. A single point of failure refers to a system or component that, if it fails, would result in the entire system becoming inoperable or compromised.
When it comes to crypto security, having a single point of failure can be extremely risky. If something were to happen to your Trezor device, such as loss, theft, or damage, you could potentially lose access to all of your cryptocurrencies. This is because the private keys that provide access to your funds are stored on the device itself.
It is crucial to have a backup plan in place to mitigate the risks associated with a single point of failure. One possible solution is to use multiple hardware wallets from different manufacturers. By diversifying your security measures, you decrease the likelihood of a complete loss in the event of a failure. Additionally, regularly backing up your private keys to an offline storage solution, such as a hardware wallet or paper wallets, can provide an extra layer of protection.
Security Considerations
When relying solely on Trezor for crypto security, it is important to take certain security considerations into account:
- Keep your Trezor device in a secure location, such as a safe or lockbox, to minimize the risk of loss or theft.
- Regularly update the firmware and software on your device to ensure you have the latest security patches.
- Enable additional security features offered by Trezor, such as passphrase protection, to further enhance the security of your funds.
Conclusion
While Trezor is a reputable and widely used hardware wallet, it is important to recognize its limitations as a single point of failure. By diversifying your security measures and implementing additional backup strategies, you can better protect your cryptocurrencies from potential pitfalls.
| Pros | Cons |
|---|---|
| Convenient and user-friendly | Single point of failure |
| Strong security features | Risk of loss, theft, or damage |
| Reputable brand | Limited backup options |
Importance of Diverse Security Measures
While Trezor is widely regarded as a secure hardware wallet for cryptocurrencies, relying solely on a single security measure can be risky. It is essential to understand the importance of diversifying security measures to safeguard your digital assets effectively.
Diversifying Security Measures

1. Use Multiple Wallets: Instead of relying solely on Trezor, consider using multiple hardware wallets from different manufacturers, such as Ledger or KeepKey. This way, even if one wallet is compromised, your other wallets remain secure.
2. Implement Multi-Factor Authentication: Enable multi-factor authentication (MFA) for all your cryptocurrency-related accounts. This adds an extra layer of security by requiring additional verification beyond a password, such as a fingerprint or a one-time code.
3. Utilize Cold Storage: In addition to hardware wallets like Trezor, consider utilizing cold storage solutions, such as offline or paper wallets. These wallets are not connected to the internet, making them less susceptible to hacking attempts.
4. Regularly Update Software: Keep your wallets, operating systems, and antivirus software up to date. Developers frequently release updates that contain security patches and enhancements to address potential vulnerabilities.
Benefits of Diverse Security Measures

1. Mitigate Single Point of Failure: Relying solely on one security measure makes your digital assets vulnerable to exploitation. Diverse security measures reduce the risk of a single point of failure by adding multiple layers of protection.
2. Enhanced Resilience: By diversifying security measures, you increase the resilience of your crypto security strategy. Even if one measure is compromised, the others can still provide protection and mitigate potential threats.
3. Stay Ahead of Emerging Threats: Cybercriminals are constantly developing new methods to breach security measures. By diversifying your security measures, you increase the likelihood of staying ahead of emerging threats and minimizing the impact of potential attacks.
- Conclusion
In conclusion, while Trezor is a reputable and secure hardware wallet, it is crucial to diversify your security measures to effectively protect your cryptocurrencies. Employing multiple wallets, implementing multi-factor authentication, utilizing cold storage, and regularly updating software are essential steps towards safeguarding your digital assets.
Multi-Factor Authentication

Multi-Factor Authentication (MFA) is a security measure that adds an extra layer of protection to online accounts. It requires users to provide multiple forms of verification before granting access. By using multiple factors, MFA significantly reduces the risk of unauthorized access, especially in cases where a single factor, such as a password, is compromised or stolen.
There are three main types of factors used in MFA:
- Something you know: This factor involves information that only the user should know, such as a password, PIN, or answer to a security question.
- Something you have: This factor refers to a physical object that the user possesses, such as a smartphone, a hardware token, or a smart card.
- Something you are: This factor involves a unique biological attribute of the user, such as a fingerprint, voice recognition, or iris scan.
By combining two or more of these factors, MFA provides a higher level of security than just relying on a password or a hardware wallet like Trezor. For instance, a common implementation of MFA is to require users to enter their password (something they know) and provide a unique code generated by an authenticator app on their smartphone (something they have).
While Trezor provides strong security for storing and managing cryptocurrencies, it is important to note that it does not offer multi-factor authentication. Therefore, solely relying on a Trezor device could potentially expose users to risks in case their Trezor is lost, stolen, or compromised.
To enhance the security of their crypto assets, individuals should consider using a combination of hardware wallets and MFA. By using MFA, users can ensure that even if their hardware wallet is compromised, unauthorized access to their funds is still highly improbable.
It is important to note that the implementation of MFA can vary depending on the service or platform. Some may offer SMS verification codes, email verification links, or biometric authentication methods. It is advisable to choose MFA methods that are considered more secure, such as time-based one-time passwords (TOTP) generated by authenticator apps.
In conclusion, while Trezor provides excellent security for storing cryptocurrencies, relying solely on it for security can leave users vulnerable in certain situations. Implementing multi-factor authentication can greatly enhance the security of crypto assets by adding an additional layer of protection. It is crucial to adopt a multi-layered security approach to safeguard digital assets from potential threats.
Question-answer:
What are some potential pitfalls of relying solely on Trezor for crypto security?
Some potential pitfalls of relying solely on Trezor for crypto security include the risk of hardware failure, loss of access to funds in case of damage or loss of the device, and the possibility of a security breach if the device is compromised.
Can Trezor be hacked?
Although Trezor is considered to be highly secure, it is not completely immune to hacking. There have been instances where hackers were able to compromise Trezor devices through phishing attacks or by exploiting vulnerabilities in the device’s software.
Is it recommended to use only Trezor for cryptocurrency security?
While Trezor is a popular and trusted hardware wallet for storing cryptocurrencies, it is generally recommended to use multiple layers of security to protect your funds. Relying solely on Trezor can be risky, as any single point of failure can result in the loss of your funds. It is advisable to use a combination of hardware wallets, software wallets, and other security measures to enhance the overall security of your crypto assets.


