
Steps to Protect Your Trezor Wallet After Data Breach

Keeping your cryptocurrency safe is of utmost importance, especially when it comes to protecting your Trezor wallet. However, despite your best efforts, data breaches can still occur, putting your valuable assets at risk. It is crucial to have a well-prepared response plan in place to effectively handle any potential threats.
1. Stay Calm and Assess the Situation
In the event of a data breach, it is important to stay calm and assess the situation. Try to gather as much information as possible about the breach and its impact on your Trezor wallet. This will help you make informed decisions and take appropriate actions to minimize any potential damage.
2. Change Your Passwords
One of the first steps you should take after a data breach is to change all your passwords associated with your Trezor wallet. This includes your login password, passphrase, and any other passwords used to access your wallet. Make sure to choose strong, unique passwords that are not easily guessable.
3. Enable Two-Factor Authentication
Adding an extra layer of security to your Trezor wallet by enabling two-factor authentication (2FA) is highly recommended. This additional step will require you to provide an additional piece of information, such as a code sent to your mobile device, when logging in to your wallet. This makes it much more difficult for unauthorized individuals to gain access to your wallet.
4. Monitor Your Accounts
After a data breach, it is essential to closely monitor your Trezor wallet and associated accounts for any suspicious activity. Keep a close eye on your transaction history and regularly review your account statements to detect any unauthorized transactions or signs of compromise. If you notice anything unusual, report it immediately to your wallet provider.
5. Keep Your Wallet Software Updated
Regularly updating your Trezor wallet software is crucial for maintaining its security. Developers often release updates to fix vulnerabilities and enhance the overall performance of the wallet. By keeping your software up to date, you ensure that you have the latest security measures in place to protect your wallet from potential threats.
6. Educate Yourself and Stay Informed
Lastly, educating yourself about the latest security practices and staying informed about potential threats is vital in protecting your Trezor wallet. Stay up to date with news and developments in the cryptocurrency community, and regularly check for any security advisories or updates from your wallet provider. By being proactive and well-informed, you can better protect your valuable assets.
Importance of Securing Your Trezor Wallet
When it comes to protecting your cryptocurrencies, securing your Trezor wallet is of utmost importance. Trezor is one of the most popular hardware wallets available, designed to store your digital assets securely offline.
By securing your Trezor wallet, you can ensure the safety of your funds and guard against potential risks such as hacking, phishing, and data breaches. Here are a few key reasons why securing your Trezor wallet is crucial:
Protecting Your Assets
Securing your Trezor wallet is essential to safeguard your assets from theft or loss. As a hardware wallet, Trezor stores your private keys offline, reducing the risk of them being compromised by malware or hackers.
In addition to storing your private keys offline, Trezor also requires user authentication before any transaction can take place. This adds an extra layer of security and ensures that only authorized individuals have access to your funds.
Preventing Data Breaches
Data breaches can have severe consequences, exposing your personal information and potentially compromising your wallet’s security. By securing your Trezor wallet, you lower the risk of your sensitive information being exposed in case of a data breach.
Trezor wallets are designed with advanced encryption techniques to protect your data from unauthorized access. However, it’s important to stay vigilant and regularly update your Trezor wallet’s firmware to take advantage of the latest security features and bug fixes.
Furthermore, staying informed about the latest security threats and best practices can help you mitigate the risk of data breaches and stay one step ahead of potential attackers.
In conclusion, securing your Trezor wallet is crucial for protecting and preserving your valuable digital assets. By following best practices, keeping your firmware updated, and staying informed, you can ensure that your cryptocurrencies remain safe and secure.
Why Protecting Your Trezor Wallet Data is Crucial
Protecting your Trezor wallet data is crucial for the security of your funds. As a hardware wallet, Trezor provides a high level of protection against hackers and malware attacks. However, it’s important to remember that your data can still be at risk if proper security measures are not taken.
Your Trezor wallet data includes sensitive information such as your private keys, recovery seed, and transaction history. If this data falls into the wrong hands, it could lead to unauthorized access to your funds and potential financial loss.
By protecting your Trezor wallet data, you are ensuring that only you have control over your funds. This can be achieved through various security practices:
- Keep your recovery seed offline: The recovery seed is a crucial component of your wallet’s security. Make sure to write it down and store it in a safe place offline, away from prying eyes and potential threats.
- Use a strong and unique password: Set a strong and unique password for your Trezor wallet. Avoid using easily guessable passwords or reusing passwords from other accounts as this can make your wallet vulnerable to attacks.
- Enable two-factor authentication (2FA): Enable 2FA on your Trezor wallet for an added layer of security. This will require you to provide an additional verification step, such as a code sent to your mobile device, in order to access your wallet.
- Regularly update your wallet’s firmware: Stay up to date with the latest firmware updates for your Trezor wallet. These updates often include security enhancements that can protect your wallet from known vulnerabilities.
- Be cautious of phishing attempts: Be mindful of phishing attempts that may try to trick you into providing your wallet data. Always double-check the URLs and ensure you are visiting legitimate Trezor websites or applications before entering any sensitive information.
By following these steps and implementing strong security practices, you can significantly reduce the risk of data breaches and unauthorized access to your Trezor wallet. Remember, the security of your funds is in your hands, so take the necessary precautions to protect your wallet data.
Steps to Strengthen Your Trezor Wallet Security
In order to enhance the security of your Trezor wallet, there are several steps you can take:
1. Use a Strong PIN
Ensure that you set a strong PIN for your Trezor wallet. Avoid using easily guessable numbers, such as dates of birth or sequential numbers. A strong PIN should be unique and contain a combination of numbers, uppercase and lowercase letters, as well as special characters.
2. Enable Two-Factor Authentication

Enable two-factor authentication (2FA) for your Trezor wallet. This adds an extra layer of security by requiring you to provide a second piece of information, such as a code generated by a trusted mobile app, in addition to your PIN.
3. Regularly Update Firmware

Keep your Trezor wallet’s firmware up to date. Firmware updates often include important security patches and improvements. Check for firmware updates regularly and install them as soon as they become available.
4. Enable Password Encryption
Consider enabling password encryption for your Trezor wallet. This can provide an additional layer of protection by requiring a password to be entered before accessing your wallet, in addition to your PIN and 2FA code.
5. Create a Backup
Always create a backup of your Trezor wallet. This should include a copy of your recovery seed, which is a series of randomly generated words that can be used to recover your wallet in case of loss or damage.
6. Be Cautious of Phishing Attacks

Be vigilant of phishing attacks that may attempt to steal your wallet information. Always verify the legitimacy of any emails, websites, or applications that request your wallet details. Trezor will never ask you to provide your recovery seed or wallet PIN.
By following these steps, you can strengthen the security of your Trezor wallet and help protect your precious cryptocurrency assets.
Enhancing Your Password Complexity for Trezor Wallet
The security of your Trezor Wallet is crucial in protecting your digital assets. One of the most important aspects of securing your wallet is creating a strong and complex password. An easily guessed or simple password can make your wallet vulnerable to hackers and unauthorized access. Here are some steps you can take to enhance your password complexity and ensure the safety of your Trezor Wallet:
1. Use a Unique Password
It is essential to use a unique password that is not used for any other accounts or services. Avoid reusing passwords to prevent hackers from gaining access to multiple accounts if one password is compromised.
2. Make it Long and Complex
Creating a long and complex password significantly increases its security. Use a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using common words or easily guessable information, such as your name, birthdate, or pet’s name. Aim for a password length of at least 12 characters or more.
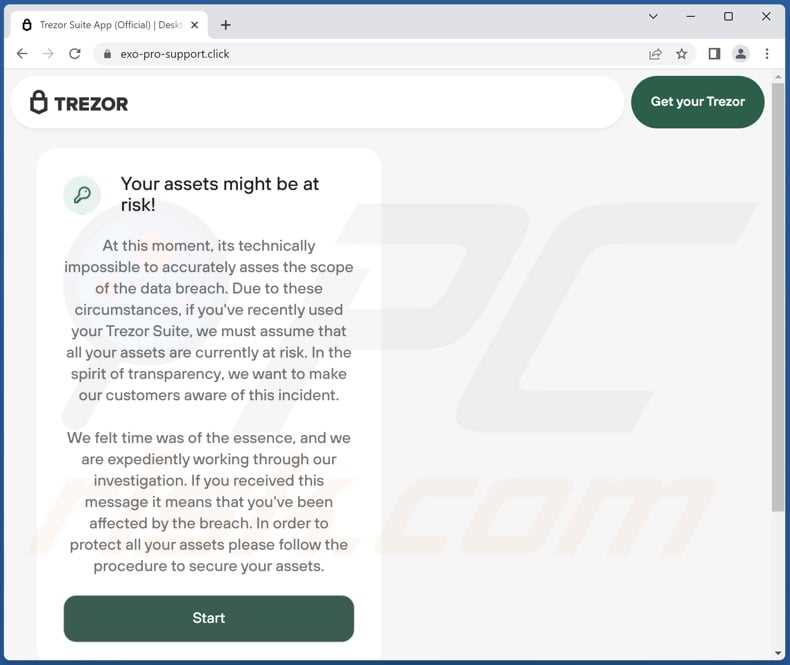
3. Consider Using a Password Manager
A password manager can help you generate and securely store complex passwords. This eliminates the need to remember multiple passwords and ensures the use of unique and robust passwords for each account.
By following these steps and enhancing the complexity of your Trezor Wallet password, you can greatly enhance the security of your digital assets and protect them from potential data breaches and unauthorized access.
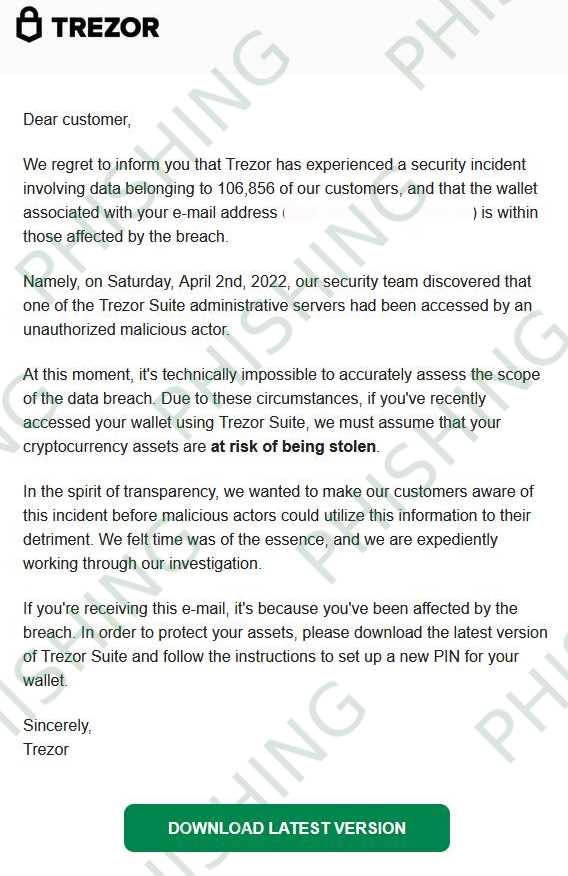
How to Respond to a Data Breach on Your Trezor Wallet
If you suspect that your Trezor wallet has been compromised in a data breach, it’s important to take immediate action to protect your funds. Here are some steps you can take:
1. Stay Calm and Assess the Situation
The first thing you should do is remain calm and carefully evaluate the situation. Take a moment to gather all the details and evidence you have regarding the possible data breach. This will help you make informed decisions moving forward.
2. Change Your Wallet Password

As a precautionary measure, change the password for your Trezor wallet. This will help to prevent unauthorized access to your funds. Choose a strong and unique password that is not easily guessable.
3. Update Your Firmware and Software
Make sure that you are using the latest version of the Trezor firmware and software. Regularly updating your wallet’s firmware and software helps protect against vulnerabilities and potential exploits.
4. Scan Your Computer for Malware

Perform a thorough scan of your computer with reputable antivirus and malware detection software. This will help identify any potential threats that may have compromised your wallet’s security.
5. Monitor Your Transactions
Keep a close eye on your wallet’s transaction history. Look for any suspicious or unauthorized transactions. If you notice anything out of the ordinary, report it immediately to the appropriate authorities and your wallet provider.
6. Enable Two-Factor Authentication
Add an extra layer of security to your Trezor wallet by enabling two-factor authentication. This will require a verification code in addition to your password, making it more difficult for unauthorized individuals to gain access to your funds.
7. Contact Trezor Support
If you believe that your Trezor wallet has indeed been compromised, contact the support team at Trezor immediately. They have the necessary expertise to assist you in securing your wallet and protecting your funds.
Remember, being proactive and taking swift action is crucial when responding to a data breach. By following these steps and staying vigilant, you can minimize the potential damage and protect your Trezor wallet.
Recognizing Signs of Data Breach on Your Trezor Wallet
Protecting your Trezor wallet from data breaches is important in order to safeguard your digital assets. One of the key steps in protecting your wallet is being able to recognize signs of a data breach. Here are some indicators that may suggest your Trezor wallet has been compromised:
- Unauthorized transactions: If you notice any transactions on your Trezor wallet that you did not initiate, it could be a sign of a data breach. Check your transaction history regularly and report any suspicious activity immediately.
- Changes to wallet settings: If you notice any unexpected changes to your wallet settings, such as new addresses or altered security features, it could indicate that someone has gained unauthorized access to your Trezor wallet.
- Unusual device behavior: If your Trezor device starts behaving abnormally, such as freezing, crashing, or displaying error messages, it could be a sign that your wallet has been compromised.
- Phishing attempts: If you receive any suspicious emails, messages, or notifications requesting your Trezor wallet details or personal information, it could be a phishing attempt. Do not click on any links or provide any information and report the incident to Trezor support.
- Unrecognized software updates: If your Trezor device prompts you to install an unexpected software update, it may be an attempt to compromise your wallet. Always verify software updates through the official Trezor website or app.
If you notice any of these signs or suspect that your Trezor wallet has been breached, it is crucial to take immediate action. Contact Trezor support and follow their instructions for securing your wallet and protecting your funds.
By staying vigilant and recognizing the signs of a data breach, you can better protect your Trezor wallet and keep your digital assets safe.
Question-answer:
What is Trezor wallet?
Trezor wallet is a hardware wallet that stores the private keys to your digital assets offline, providing a secure way to store and access your cryptocurrencies.
Why is it important to protect your Trezor wallet?
It is important to protect your Trezor wallet because it stores your private keys, which are essential for accessing and managing your cryptocurrencies. Without proper protection, your funds can be at risk of theft or loss.
What are some steps to protect your Trezor wallet?
Some steps to protect your Trezor wallet include regularly updating the device’s firmware, using a strong and unique PIN, enabling two-factor authentication, carefully managing and storing your recovery seed, and keeping your device and recovery seed in secure locations.
What should I do if my Trezor wallet is compromised?
If your Trezor wallet is compromised, you should immediately disconnect it from your computer or mobile device, contact Trezor support for assistance, and transfer your funds to a new and secure wallet using your recovery seed.


