
Can Trezor’s Software Get Infected with Malware?

Trezor, the popular hardware wallet designed to securely store cryptocurrencies, offers users a peace of mind when it comes to protecting their digital assets. However, many wonder if the accompanying software is equally as secure. Can Trezor’s software get infected with malware? In this article, we will delve into this important question and assess the threat it poses to Trezor users.
One of the key features of Trezor is its secure firmware, which is developed and regularly audited by a team of dedicated experts. This firmware serves as the first line of defense against potential malware attacks. It ensures that even if the software running on the user’s computer is compromised, the firmware remains untouched and immune from any infection.
Furthermore, Trezor’s software operates in a sandboxed environment, isolated from other processes and applications on the user’s computer. This means that even if malware manages to infect the user’s computer, it cannot access or manipulate the software that interacts with the Trezor device. This additional layer of protection significantly reduces the risk of malware compromising the security of the user’s cryptocurrency holdings.
However, it is important to note that while Trezor’s software is designed to be highly secure, no system is completely foolproof. As with any software, there is always a small possibility of vulnerabilities or exploits being discovered. Trezor is aware of this and takes proactive measures to address any potential security issues by regularly releasing software updates and patches.
In conclusion, while there is a small inherent risk of malware infecting Trezor’s software, the multiple layers of security provided by the hardware wallet significantly mitigate this threat. Users can confidently rely on Trezor’s robust firmware, sandboxed software environment, and regular updates to protect their valuable cryptocurrencies from potential malware attacks.
Can Trezor’s Software Be Infected?

Trezor is a popular hardware wallet that provides secure storage for cryptocurrencies. While the hardware itself is designed to be secure, there is a potential threat of malware infecting the Trezor’s software.
The Risk of Malware
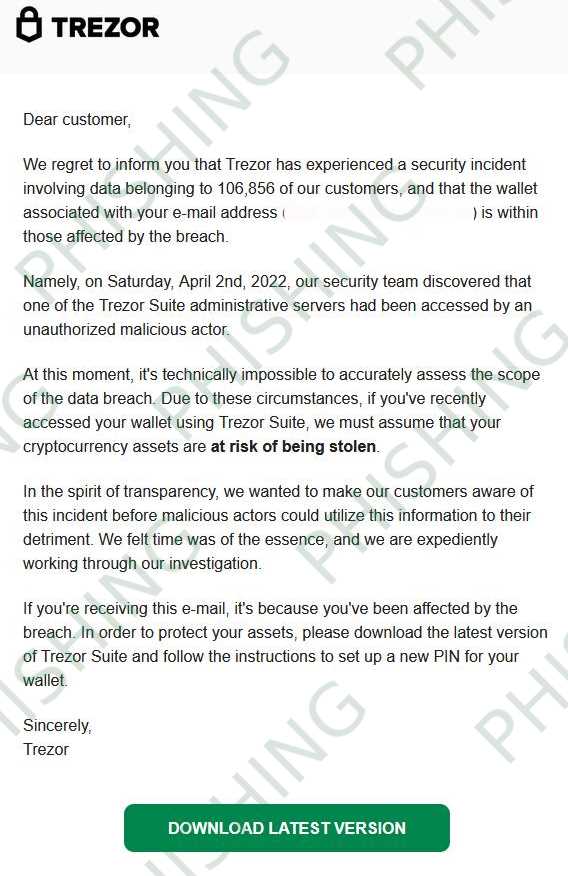
Although Trezor’s firmware undergoes rigorous testing and auditing processes, it is not entirely immune to malware. In fact, any software can be vulnerable to attacks if proper security precautions are not taken.
There have been instances where attackers have successfully targeted users by compromising their computers or tricking them into installing malicious software that interacts with the Trezor’s software.
Once malware infects a user’s device, it can attempt to tamper with the Trezor’s software, potentially stealing private keys or manipulating transactions.
Protecting Against Malware
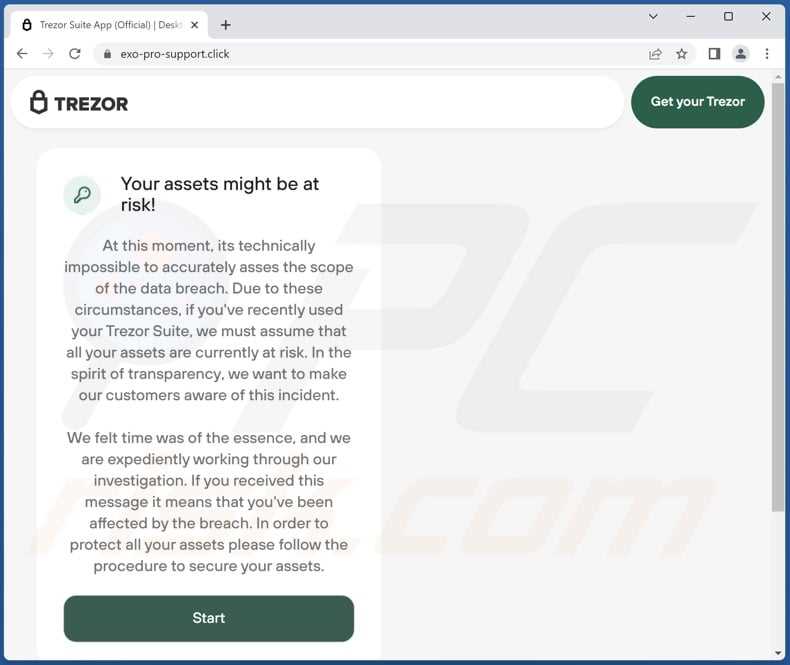
While the threat of malware exists, there are steps that can be taken to reduce the risk:
| 1. Keep Software Up to Date |
|---|
| Regularly update both the Trezor’s firmware and the software on your computer or mobile device. These updates often include security patches that address known vulnerabilities. |
| 2. Verify Sources |
| Only download Trezor’s software and updates from official sources. Be wary of third-party websites or links that may contain malicious software. |
| 3. Use Antivirus Software |
| Install and regularly update antivirus software on your computer to detect and remove malware that could potentially infect your Trezor’s software. |
| 4. Be Vigilant |
| Exercise caution when interacting with suspicious emails, websites, or files, as they may contain malware that can compromise your device’s security. |
By following these best practices, users can significantly reduce the risk of their Trezor’s software being infected with malware. It is essential to stay vigilant and stay informed about the latest security threats to ensure the safety of your cryptocurrency investments.
Evaluating the Risk of Malware

When it comes to assessing the risk of malware infecting Trezor’s software, it is important to consider several factors. These factors include Trezor’s security measures, the user’s behavior, and the overall threat landscape.
Trezor’s Security Measures

Trezor is known for its strong security measures and reputation. The Trezor hardware wallet uses a secure element chip to store private keys and perform cryptographic operations. This ensures that even if the device is compromised physically, it is difficult for an attacker to extract the private keys.
Additionally, Trezor’s software undergoes thorough testing and code review to identify and eliminate vulnerabilities. Regular firmware updates are also provided to address any security issues that may arise. However, it is crucial for users to keep their firmware up to date to benefit from these security patches.
User Behavior
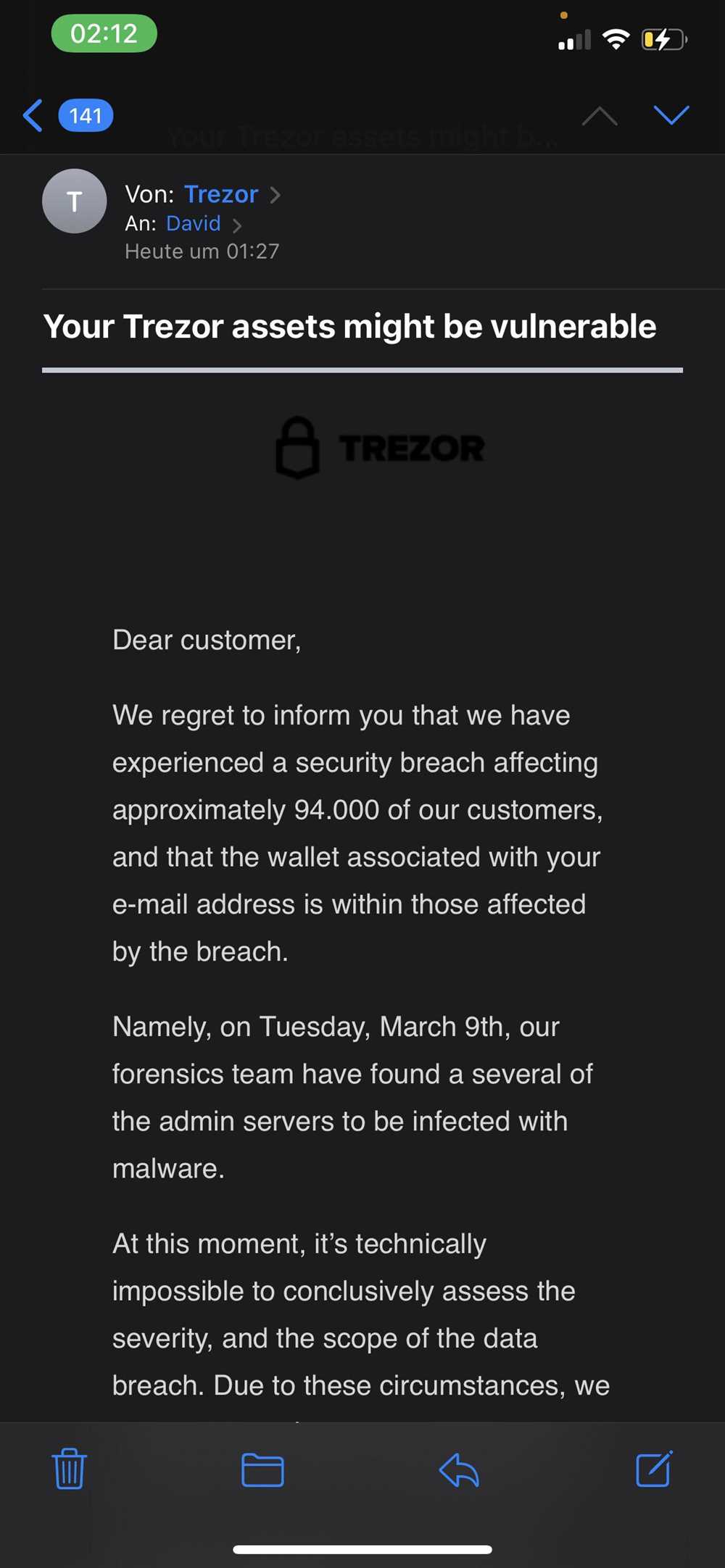
While Trezor provides robust security measures, the user’s behavior can also impact the risk of malware infection. It is important for users to exercise caution and follow best practices when using their Trezor device.
Users should only download firmware updates and applications from official sources, such as the Trezor website. Clicking on suspicious links or downloading software from unauthorized sources can increase the risk of malware infection.
Furthermore, users should also be mindful of their browsing habits. Visiting malicious websites or downloading files from untrusted sources can expose Trezor to potential malware threats.
Overall Threat Landscape
The overall threat landscape is an important factor to consider when evaluating the risk of malware infecting Trezor’s software. The number and sophistication of malware attacks continually evolve, making it crucial for users to stay informed about the latest threats.
By staying aware of the latest malware trends and taking appropriate precautions, users can minimize the risk of their Trezor device being infected. Regularly updating antivirus software, using secure networks, and practicing good cyber hygiene are effective ways to mitigate the risk.
In conclusion, while no system can be completely immune to malware, Trezor takes significant steps to protect its users from such threats. By combining strong security measures, user awareness, and a proactive approach to addressing emerging threats, users can confidently use their Trezor device while minimizing the risk of malware infection.
Inadequate Security Measures

While Trezor’s software is designed with security in mind, there are still some potential vulnerabilities that users should be aware of. One of the main concerns is the possibility of inadequate security measures, which could allow malware to infect the device.
One vulnerability is the use of outdated or insecure firmware. If the firmware on the Trezor device is not regularly updated, it may have vulnerabilities that could be exploited by malware. It is crucial for users to regularly check for firmware updates and install them promptly to ensure the device is protected against known vulnerabilities.
Additionally, users should be cautious when downloading and installing third-party applications that interact with the Trezor device. Malicious developers could create fake apps that appear to be legitimate but are designed to steal sensitive information or compromise the security of the device. It is essential to only use trusted and verified applications from reputable sources.
Another potential weakness is the susceptibility of the device’s hardware to physical tampering. If an attacker gains physical access to the Trezor device, they may be able to modify its components or install malware directly onto the device. Users should take precautions to safeguard their device from physical attacks, such as storing it in a secure location and regularly checking for any signs of tampering.
Overall, while Trezor’s software is designed to be secure, users must remain vigilant and take appropriate measures to protect their device from potential malware infections. By keeping the firmware updated, being cautious with third-party applications, and safeguarding the device from physical tampering, users can reduce the risk of malware infecting their Trezor device.
Protecting Your Trezor Device

Keeping your Trezor device secure is essential to protecting your cryptocurrencies from malware and other threats. Here are some key steps you can take to ensure the safety of your device:
1. Purchase from an official source: To minimize the risk of purchasing a compromised or counterfeit device, always buy your Trezor from an official distributor or the manufacturer’s website.
2. Verify the integrity of the device: Before using your Trezor, make sure to check for any signs of tampering. Look for damage to the packaging or signs that the device has been opened previously.
3. Keep the firmware up to date: Trezor regularly releases firmware updates to fix security vulnerabilities and improve overall performance. Make sure to install these updates promptly to ensure your device remains protected.
4. Create a strong passphrase: In addition to the PIN code, you can add an extra layer of security by setting up a passphrase. Make sure to choose a unique and complex passphrase that is not easily guessed.
5. Enable the two-factor authentication: Trezor devices offer an additional layer of security through two-factor authentication. Enable this feature and pair your device with a compatible authentication app for an added level of protection.
6. Beware of phishing attempts: Be cautious of any emails or websites that request your seed phrase or personal information. Trezor will never ask you for this information, so always double-check the source before providing any sensitive data.
7. Use a dedicated computer: Consider using a dedicated computer or virtual machine for your Trezor transactions. Avoid using public or shared devices that may be compromised with malware or keyloggers.
8. Keep your recovery seed safe: Your recovery seed is the key to restoring access to your funds in case your Trezor device is lost or damaged. Store it in a secure location, preferably offline, and keep multiple copies in case one becomes inaccessible.
9. Be cautious of physical attacks: Keep your Trezor device protected from physical attacks, such as theft or damage. Avoid leaving it unattended in public places and consider using a protective case or safe storage solution.
By following these security measures, you can minimize the risk of malware and other threats compromising your Trezor device and keep your cryptocurrencies safe.
Vigilance in the Face of Emerging Threats

As technology continues to advance, so do the threats posed by malware and other malicious software. In the case of Trezor’s software, it is essential to exercise vigilance and stay informed about emerging threats.
While Trezor is known for its robust security measures, it is not immune to potential infections. Malware can find its way onto a user’s computer through various vectors, such as phishing attacks or compromised downloads.
To stay ahead of these threats, it is crucial to keep your Trezor software up to date by regularly installing the latest firmware and software updates provided by the Trezor team. Additionally, always download software and updates directly from the official Trezor website to avoid the risk of downloading compromised versions from unreliable sources.
It is also advisable to implement other security measures, such as using reliable antivirus software and enabling two-factor authentication whenever possible. Regularly scanning your computer for malware and being cautious when interacting with suspicious emails or websites can also help mitigate the risk of infection.
Furthermore, staying informed about the latest security trends and techniques used by cybercriminals can help you recognize potential threats and take necessary precautions. Following reputable cybersecurity blogs and news sources can provide valuable insights into emerging threats and best practices for safeguarding your Trezor device.
In conclusion, while Trezor’s software is designed with security in mind, it is crucial to remain vigilant and proactive in protecting your device from potential malware infections. By taking the necessary precautions and staying informed about emerging threats, you can confidently use your Trezor device while minimizing the risk of compromise.
Question-answer:
What is Trezor’s Software?
Trezor’s Software is a cryptocurrency wallet software developed by SatoshiLabs. It is designed to securely store private keys and enable users to manage their digital assets.
How does Trezor’s Software work?
Trezor’s Software works by generating and storing private keys in a secure environment called the “Trezor device”. When a user wants to make a transaction, the software signs the transaction with the private key stored in the device, ensuring the security of the transaction.
Is Trezor’s Software vulnerable to malware infections?
Trezor’s Software is generally considered to be secure and resistant to malware infections. However, it is important to note that no software is completely immune to all forms of malware, and users should always take precautions to ensure the security of their digital assets.
How can Trezor’s Software get infected with malware?
Trezor’s Software can potentially get infected with malware if a user’s computer or the computer they use to interact with the software is compromised. This can happen through various means, such as downloading infected files or visiting malicious websites.
What are the potential risks of Trezor’s Software being infected with malware?
If Trezor’s Software is infected with malware, it could potentially lead to the theft of a user’s private keys and the loss of their digital assets. Malware could also tamper with the software’s functions, leading to incorrect transaction signing or other security vulnerabilities.


