
Assessing the Legal Consequences of the Trezor Data Breach

Protecting your sensitive information is of utmost importance in today’s digital age.
But what happens when a trusted company experiences a data breach?
That’s the case with the recent Trezor data breach, where unauthorized access to customer data occurred.
Now, you may be wondering:
What are the legal implications of this breach?
At [Your Company Name], we understand the importance of navigating the legal landscape surrounding data breaches.
Our team of experienced attorneys specializes in data privacy and cybersecurity law.
We can help you understand your rights and seek justice for any harm caused by the Trezor data breach.
Don’t let your personal information fall into the wrong hands.
Protect yourself with the legal expertise of [Your Company Name].
Contact us today to schedule a consultation and learn more about how we can assist you.
Legal Considerations for Trezor Data Breach

When a data breach occurs, it is essential to understand the legal ramifications and considerations that come into play. In the case of the Trezor data breach, several key legal factors need to be taken into account.
Data Protection Laws: One of the primary considerations for any data breach is compliance with data protection laws. Companies like Trezor have a legal obligation to protect user information and adhere to privacy regulations. Failure to do so can result in legal actions, fines, and reputational damage.
Data Breach Notification: Another crucial legal consideration is the requirement to notify affected individuals about the breach. Most jurisdictions have laws that mandate timely and transparent communication with impacted users. This helps individuals take appropriate steps to protect themselves from potential harm.
Legal Liabilities: In the case of a data breach, legal liabilities may arise. Affected individuals may suffer financial losses, identity theft, or other damages as a result of the breach. Trezor could potentially face lawsuits and claims for compensation from impacted users, leading to legal battles and financial consequences.
Investigations and Penalties: Data breaches often trigger investigations by regulatory bodies and authorities. These investigations aim to determine the extent of the breach, identify any negligence or wrongdoing on the part of the company, and impose appropriate penalties. Trezor could face sanctions, fines, or other legal consequences if found to be at fault.
Reputational Damage: Data breaches can severely tarnish a company’s reputation. The fallout from a breach, including negative media coverage and public scrutiny, can lead to a loss of trust among customers and investors. Trezor must carefully manage its response to the breach to mitigate reputational damage and restore confidence in its security measures.
| Legal Considerations for Trezor Data Breach |
|---|
| Data Protection Laws |
| Data Breach Notification |
| Legal Liabilities |
| Investigations and Penalties |
| Reputational Damage |
The Importance of Data Security

Data security is more crucial than ever in today’s digital landscape. With the increasing number of data breaches and cyberattacks, organizations and individuals need to recognize the importance of protecting their sensitive information. Here are some key reasons why data security should be a top priority:
- Protecting Confidential Information: Data security is essential to safeguard confidential information such as personal details, financial records, and customer data. Failure to protect this information can lead to significant legal and financial consequences.
- Maintaining Trust: Data breaches can result in a loss of trust from customers, stakeholders, and partners. By implementing robust data security measures, organizations can demonstrate their commitment to protecting sensitive information and maintain the trust of their stakeholders.
- Compliance with Regulations: Many industries have specific regulations and guidelines relating to data security and privacy. Organizations must comply with these regulations to avoid legal penalties and reputational damage.
- Preventing Financial Losses: Data breaches can result in significant financial losses, including costs associated with investigating the incident, notifying affected individuals, and implementing remediation measures. By investing in data security, organizations can mitigate the risk of financial losses.
- Minimizing Disruption: Data breaches can cause severe disruptions to business operations, resulting in downtime, loss of productivity, and damage to reputation. Implementing robust data security measures can help minimize the impact of such incidents and maintain business continuity.
In conclusion, data security is a critical aspect of protecting sensitive information and maintaining trust in today’s digital world. By prioritizing data security, organizations and individuals can mitigate the risks associated with data breaches and cyberattacks and ensure the confidentiality, integrity, and availability of their valuable data.
Understanding the Legal Implications
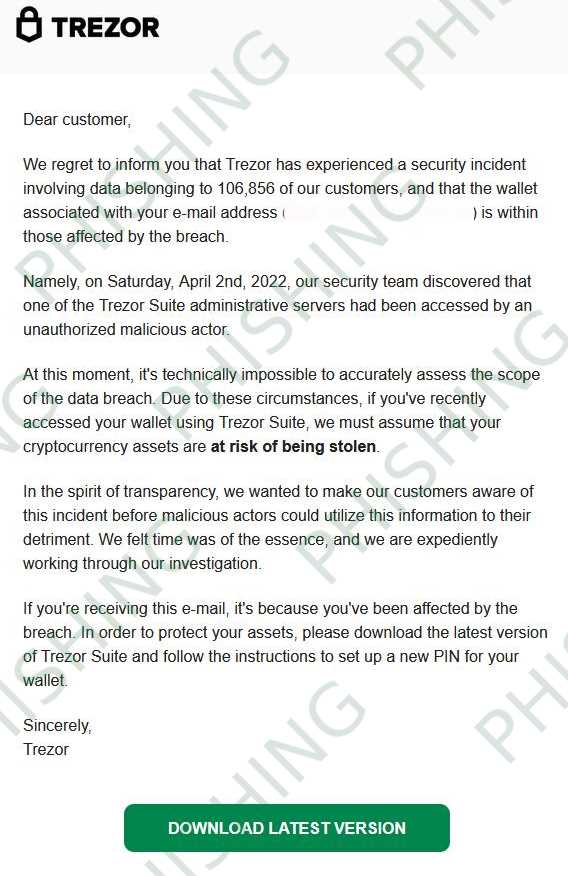
When it comes to the Trezor data breach, it is crucial to understand the legal implications that arise from such a security incident. In today’s digital age, data breaches have become a common occurrence, and companies must be aware of the legal consequences that follow.
The Importance of Data Protection Laws
Data breaches can have severe legal consequences for both the affected individuals and the company responsible for safeguarding their data. With the increasing reliance on technology, governments worldwide have implemented stringent data protection laws to ensure the privacy and security of personal information.
For businesses, failing to comply with these laws can result in hefty fines, reputational damage, and a loss of customer trust. In severe cases, companies may face legal action from affected individuals, leading to significant financial and legal liabilities.
Liability and Compensation

In the aftermath of a data breach, companies may be held liable for any damages caused, including financial losses, identity theft, and emotional distress suffered by affected individuals. The legal process often involves the determination of negligence, examining whether the company took adequate steps to secure the personal data.
Furthermore, affected individuals may seek compensation for the harm caused by the data breach. This compensation can cover various aspects, such as financial losses, costs incurred for credit monitoring, and any other damages resulting from the breach.
| Legal Ramifications | Description |
|---|---|
| Fines and Penalties | Companies may face significant fines and penalties imposed by regulatory authorities for failing to adequately protect personal data. |
| Legal Expenses | The process of defending against legal claims and meeting regulatory requirements can be costly, leading to financial strain on the company. |
| Reputational Damage | Data breaches often result in negative publicity and a loss of trust from customers, potentially impacting the company’s reputation and future business prospects. |
| Criminal Investigations | In some cases, data breaches can lead to criminal investigations, especially if it is discovered that the breach was a result of intentional wrongdoing or negligence. |
Therefore, understanding the legal implications of a data breach such as the Trezor incident is crucial for both individuals and companies. By complying with data protection laws, implementing robust cybersecurity measures, and being prepared to handle breaches effectively, businesses can mitigate the legal risks associated with data breaches and protect themselves and their customers.
Protecting Your Business from Liability

As a business owner, it is crucial to take necessary steps to protect your organization from potential liabilities that may arise from data breaches. Implementing robust security measures and following best practices can greatly reduce the risk of a breach and help safeguard sensitive information. Here are some key strategies to consider:
1. Strengthen your cybersecurity defenses
Investing in comprehensive cybersecurity measures is essential in today’s digital landscape. Ensure that your business has a strong firewall, up-to-date antivirus software, and regular security updates installed on all devices and systems. Implementing multifactor authentication and encryption techniques can also provide an additional layer of protection.
2. Educate your employees
Human error is one of the leading causes of data breaches. Train your employees on cybersecurity best practices, such as creating strong passwords, recognizing phishing emails, and avoiding suspicious websites and downloads. Regularly remind them of the importance of data security and the potential consequences of a breach.
In addition, consider implementing a clear data protection policy that outlines your expectations for handling sensitive information. This policy should cover proper data storage, usage, and disposal procedures.
3. Conduct regular security audits
Regularly assess your systems and networks for potential vulnerabilities and weaknesses. Conducting thorough security audits can help identify any areas that require attention and enable you to take proactive steps to address them. Partnering with a reputable cybersecurity firm can provide you with expert guidance and support in this process.
Furthermore, consider implementing intrusion detection and prevention systems that can help detect and mitigate potential threats before they result in a breach.
4. Plan for incident response
Despite your best efforts, there is always a possibility of a data breach. Developing a comprehensive incident response plan can help minimize the impact of a breach and ensure a swift and effective response. This plan should include steps to contain the breach, notify affected parties, and cooperate with law enforcement and regulatory authorities.
Regularly test and update your incident response plan to reflect any changes in your business operations or regulatory requirements.
By proactively implementing these strategies, you can significantly reduce the risk of a data breach and mitigate potential liability for your business. Protecting sensitive information should be an ongoing priority, as the consequences of a breach can be detrimental to your organization’s reputation, finances, and legal standing.
Q&A:
What is the Trezor data breach?
The Trezor data breach refers to the unauthorized access and acquisition of sensitive information from the Trezor hardware wallet.
When did the Trezor data breach occur?
The Trezor data breach occurred on January 2020.
What information was compromised in the Trezor data breach?
In the Trezor data breach, personal information such as names, email addresses, and passwords were compromised.
How can I protect myself from the Trezor data breach?
To protect yourself from the Trezor data breach, it is important to regularly update your Trezor hardware wallet’s firmware and use strong, unique passwords.


