
Cracking the Vault: Analyzing the Potential Weaknesses of Trezor

When it comes to securing your cryptocurrency assets, hardware wallets like Trezor have gained significant popularity due to their robust security features and offline storage capabilities. With its sleek design and easy-to-use interface, Trezor has become a popular choice among cryptocurrency enthusiasts. However, like any technology, Trezor is not without its potential weaknesses and vulnerabilities.
One potential weakness of Trezor is the vulnerability to physical attacks. Since Trezor is a hardware device, it can be stolen or physically tampered with. If an attacker gains physical access to your Trezor device, they may attempt to extract the private keys stored on the device, giving them access to your cryptocurrency funds. This is why it is crucial to store your Trezor device in a secure location and use additional security measures such as passphrase encryption.
Another potential weakness of Trezor is the risk of supply chain attacks. Like any hardware device, Trezor goes through a supply chain process before reaching the end user. During this process, there is a possibility of the device being tampered with or compromised. An attacker could modify the firmware of the device or implant malicious components, compromising the security of the device and potentially allowing them to steal your cryptocurrency.
Additionally, Trezor relies on computer software and applications to interact with the device. This introduces the risk of software vulnerabilities or malware that could compromise the security of your Trezor device. If your computer or smartphone is infected with malware, it may be possible for an attacker to intercept the communication between your device and the Trezor application, potentially gaining unauthorized access to your cryptocurrency funds.
Despite these potential weaknesses, it is important to remember that Trezor has implemented numerous security measures to mitigate these risks. The device uses a secure element chip to store private keys and implements encryption to protect sensitive data. Trezor also regularly releases firmware updates to address any discovered vulnerabilities and improve the overall security of the device.
Ultimately, maintaining good security practices such as keeping your firmware up to date, using a strong passphrase, and being mindful of your physical security can help mitigate the potential weaknesses of Trezor and ensure the safety of your cryptocurrency investments.
Weaknesses of Trezor: A Deep Dive into Security Concerns
While Trezor is generally considered a highly secure hardware wallet for storing cryptocurrencies, it is not without its weaknesses. This section will delve into some of the potential security concerns associated with using Trezor.
- Physical Vulnerability: Although Trezor is designed to be highly durable, it is not impervious to physical damage or theft. If an attacker gains physical access to the device, they may be able to tamper with or extract sensitive information.
- Seed Phrase Exposure: One of the key security features of Trezor is the use of a seed phrase for wallet recovery. However, if the seed phrase is not adequately protected, it can become a point of vulnerability. If an attacker gains access to the seed phrase, they can potentially gain control of the wallet and steal the funds.
- Supply Chain Attacks: Trezor devices go through a manufacturing process before reaching the end user. Any compromise in the supply chain, such as a malicious actor injecting malware or modifying the device, can undermine the security of the wallet.
- Software Vulnerabilities: The software used in conjunction with Trezor is constantly being updated to address potential vulnerabilities. However, no software is completely immune to bugs or exploits. It is imperative for users to regularly update their software to mitigate potential security risks.
- Phishing Attacks: Trezor’s security measures can be undermined through social engineering tactics, such as phishing attacks. Attackers may attempt to trick users into revealing their seed phrase or other sensitive information by posing as legitimate entities.
It is important to note that while these weaknesses exist, Trezor has implemented numerous security measures to mitigate these risks. However, users must play an active role in maintaining the security of their wallet by employing best practices and remaining vigilant against potential threats.
Evaluating the Vulnerabilities of Trezor Hardware

When it comes to evaluating the vulnerabilities of Trezor hardware, it is important to consider the potential weaknesses that could be exploited by attackers. Although Trezor is considered to be one of the most secure hardware wallets on the market, no device is completely invulnerable to attack.
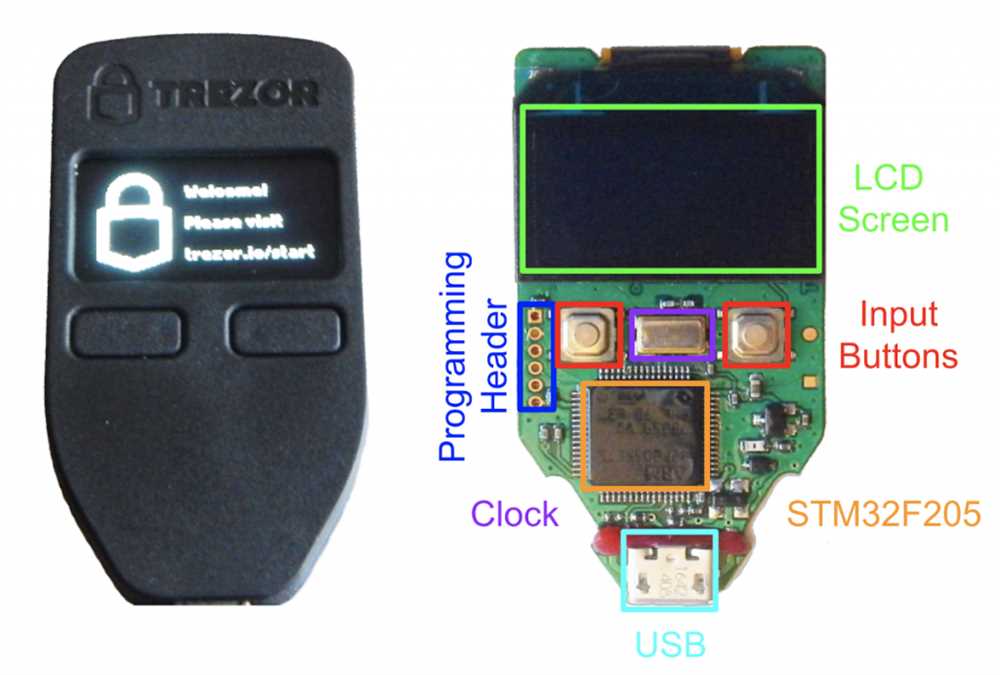
1. Physical Attacks
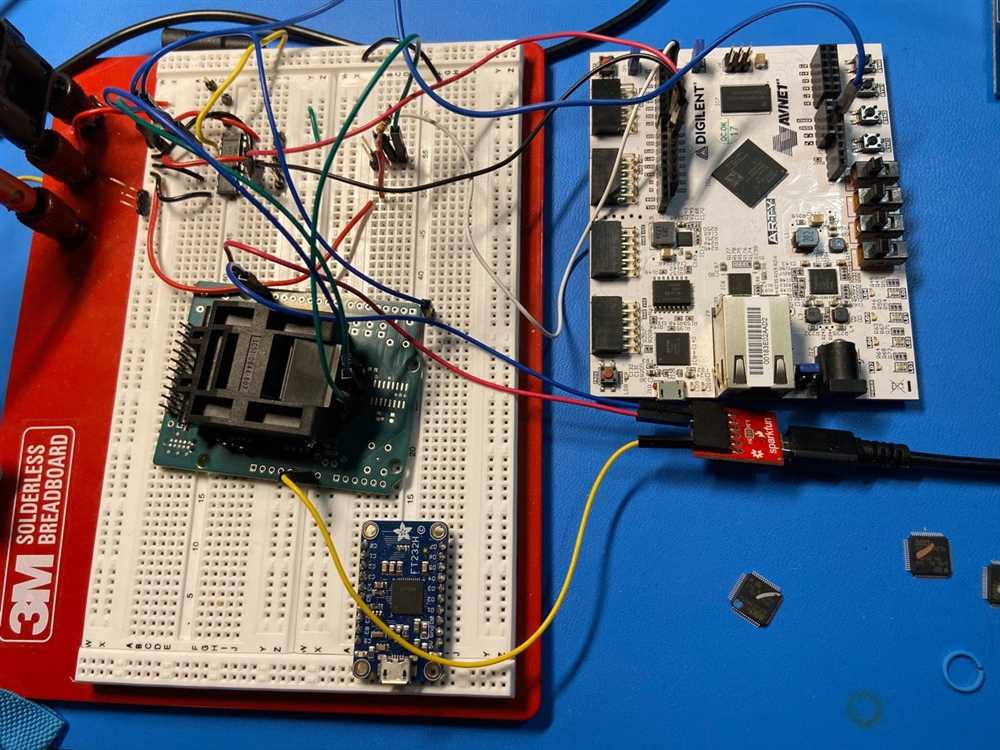
Physical attacks pose a significant risk to Trezor hardware. If an attacker gains physical access to the device, they may try to extract sensitive information or tamper with the hardware. However, Trezor has implemented several security measures to mitigate this risk, such as preventing tampering by sealing the device and using highly secure chips.
2. Firmware Vulnerabilities

Trezor’s firmware is another potential weak point that could be exploited. If there are vulnerabilities in the firmware, attackers may be able to exploit them to gain unauthorized access to the device. Trezor regularly updates its firmware to address any potential vulnerabilities and encourages users to keep their devices up to date.
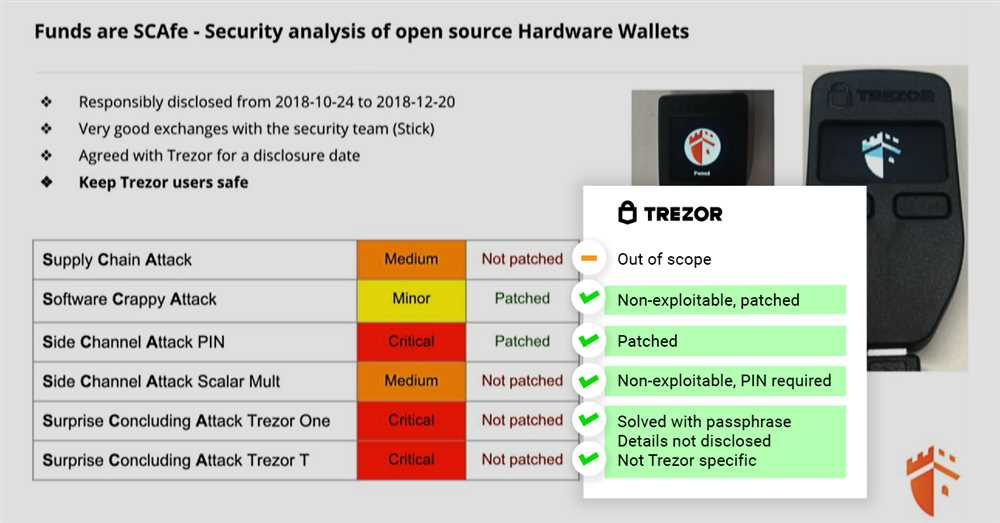
3. Supply Chain Attacks
Supply chain attacks are a concern for any hardware wallet manufacturer, including Trezor. If an attacker manages to compromise the supply chain, they could insert malicious code or tamper with the device during the manufacturing process. Trezor takes precautions to protect against supply chain attacks and works with trusted suppliers to ensure the integrity of its hardware.
4. Social Engineering
Social engineering attacks target the user rather than the hardware itself. Attackers may try to trick users into revealing their sensitive information or manipulating them into performing actions that could compromise the security of their Trezor device. Users need to be cautious and follow best practices to avoid falling victim to social engineering attacks.
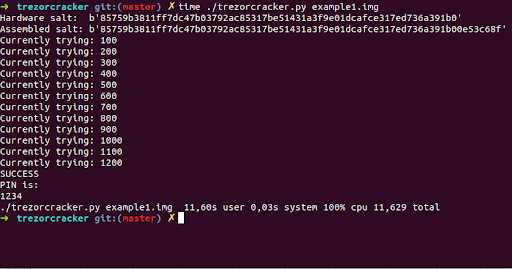
5. Side Channel Attacks

Side channel attacks exploit information leaked during the execution of cryptographic operations. Although Trezor is designed to resist side channel attacks, it is impossible to eliminate them completely. However, these attacks generally require physical access to the device and specialized equipment, making them less of a concern for the average user.
In conclusion, while Trezor is generally considered to be a highly secure hardware wallet, it is important to be aware of its potential vulnerabilities. By understanding these weaknesses and taking appropriate precautions, users can minimize the risk of their Trezor device being compromised.
Understanding the Potential Risks of Software Exploitation
As with any software-based system, Trezor is not immune to potential risks of software exploitation. While Trezor is built with a high level of security in mind, it is important to understand the potential risks and take necessary precautions to mitigate them.
1. Malware and Phishing Attacks
One potential risk is the infiltration of malware or falling victim to phishing attacks. Malware can be designed to specifically target cryptocurrency wallets, such as Trezor, aiming to steal private keys or gain unauthorized access to funds. Phishing attacks, on the other hand, involve tricking users into revealing their credentials or providing sensitive information.
To protect against these risks, it is important to only download software or applications from trusted sources, such as the official Trezor website. Additionally, users should be cautious of clicking on suspicious links or providing sensitive information to untrusted sources.
2. Software Vulnerabilities

Software vulnerabilities are another potential risk associated with software exploitation. Even with rigorous security measures in place, there is always a possibility of undiscovered vulnerabilities that could be exploited by malicious actors. These vulnerabilities could potentially allow unauthorized access to the device or compromise the security of the private keys.
To mitigate this risk, it is crucial to keep the Trezor firmware and software up to date. Trezor regularly releases security updates and patches, addressing any potential vulnerabilities. Users should regularly check for updates on the official Trezor website and promptly install them to ensure they are protected against any known security issues.
It is highly recommended not to use any third-party apps or modifications that claim to enhance the functionality of Trezor, as these may introduce additional vulnerabilities.
Remember, staying vigilant and adopting best security practices is essential to safeguarding your cryptocurrency investments.
Examining the Challenges of Physical Attacks and Social Engineering
When it comes to securing cryptocurrencies, one of the most important aspects to consider is protecting against physical attacks and social engineering tactics. These types of attacks can compromise the security of Trezor or any other hardware wallet, and it’s crucial to understand the potential weaknesses.
Physical attacks involve directly tampering with the physical device, such as trying to extract the private keys or manipulating the hardware components. While Trezor has implemented several security measures to prevent physical attacks, it’s not entirely immune to them. Sophisticated attackers with specialized tools and knowledge may still find ways to exploit vulnerabilities.
Social engineering, on the other hand, is a type of attack that exploits human psychology to gain unauthorized access or sensitive information. Attackers might impersonate support representatives or trustworthy individuals to deceive users into disclosing their private keys or granting access to their wallets. Trezor users should be vigilant and never share their private keys or sensitive information with anyone, as Trezor will never ask for them.
To protect against physical attacks, it’s recommended to store the hardware wallet in a secure location, such as a safe or a lockbox. Additionally, users should regularly inspect their devices for any signs of tampering or unusual behavior.
To safeguard against social engineering attacks, users should never click on suspicious links or download software from untrusted sources. It’s essential to verify the authenticity of any communication claiming to be from Trezor support or any other official channel. Users should also enable two-factor authentication and practice good password hygiene.
While Trezor addresses these challenges through rigorous security measures, it’s essential for users to understand the risks and take proactive steps to protect their funds and personal information. By being aware of the potential weaknesses and implementing best practices, users can enhance the security of their cryptocurrencies and have peace of mind.
Q&A:
What is Trezor and what does it do?
Trezor is a hardware wallet that allows users to securely store their cryptocurrency private keys. It provides an offline storage solution to protect against the risk of online hacks and theft.
Are there any potential weaknesses or vulnerabilities in Trezor?
Yes, there are potential weaknesses and vulnerabilities in Trezor. Although it is considered one of the most secure hardware wallets available, there have been some reported vulnerabilities in the past that have allowed attackers to exploit the device.
What are some of the reported weaknesses of Trezor?
Some reported weaknesses of Trezor include physical attacks that could compromise the device, such as extracting the private keys from the hardware itself. There have also been vulnerabilities found in the firmware of the device that could potentially be exploited.
Has Trezor taken any measures to address these weaknesses?
Yes, Trezor has taken measures to address these weaknesses. They regularly release firmware updates that fix any reported vulnerabilities, and they have a responsible disclosure policy that encourages researchers to report any discovered weaknesses so they can be addressed promptly.
Is Trezor still considered a secure option for storing cryptocurrency?
Yes, Trezor is still considered a secure option for storing cryptocurrency. While there may be potential weaknesses, the company has a strong track record of addressing vulnerabilities and taking security seriously. It is important for users to keep their devices and firmware up to date to ensure maximum security.


