Are Trezor Wallet Security Measures Vulnerable to Cybercriminals?

Trezor wallet is one of the most popular hardware wallets in the market for storing and managing cryptocurrencies. The security measures implemented by Trezor aim to protect users’ digital assets from cybercriminals. However, with the increasing sophistication of hacking techniques, the question arises: Can Trezor wallet security measures be breached by cybercriminals?
Trezor wallet utilizes a combination of physical security and encryption techniques to safeguard users’ private keys and prevent unauthorized access to their digital assets. The device itself is built with tamper-resistant hardware, making it difficult for attackers to physically compromise the wallet.
Furthermore, Trezor wallet employs strong cryptographic algorithms to secure users’ private keys. These keys are stored in an isolated environment on the device and are never exposed to the internet. This significantly reduces the risk of key theft through remote attacks.
However, no security measure is flawless, and there have been instances where hackers have attempted to breach Trezor wallets. The most notable example is the “evil maid” attack, where an attacker gains physical access to the wallet and replaces the firmware with a malicious version. This attack can compromise the security of the device and lead to the theft of private keys.
Overall, while Trezor wallet employs robust security measures to protect users’ cryptocurrencies, it is important for users to stay vigilant and follow best practices for securing their devices and private keys. Regular firmware updates and adherence to recommended security guidelines can help minimize the risk of cybercriminals breaching Trezor wallet security measures.
Is Trezor Wallet Security at Risk from Cybercriminals?

With the ever-increasing popularity and value of cryptocurrencies, ensuring the security of your digital assets has become paramount. Trezor, the popular hardware wallet, is widely considered one of the safest options for storing and managing cryptocurrencies such as Bitcoin and Ethereum. However, no system is completely immune to potential security breaches, and it’s important to evaluate the risks associated with using Trezor.
Trezor wallets employ several security measures to protect users’ funds. The device features a robust hardware design and utilizes advanced encryption algorithms to keep private keys secure. Additionally, Trezor wallets require a physically connected device to access and manage funds, reducing the risk of remote attacks. These measures make it significantly more difficult for cybercriminals to gain unauthorized access to a Trezor wallet.
However, it’s essential to remain vigilant, as cybercriminals are constantly developing new techniques to exploit vulnerabilities. While the Trezor hardware wallet itself is secure, there are potential risks that users should be aware of:
| Potential Risk | Description |
|---|---|
| Physical Theft or Loss | If your Trezor device is stolen or misplaced, an unauthorized person may attempt to access your funds. It’s crucial to keep your Trezor wallet in a safe and secure location and consider using additional security features like a passphrase. |
| Supply Chain Attacks | Attackers may compromise the hardware before it reaches the user by altering the device’s firmware or injecting malicious code. It’s important to purchase Trezor wallets directly from the manufacturer or authorized resellers to minimize the risk of receiving a compromised device. |
| Phishing Attacks | Cybercriminals may attempt to trick users into revealing their Trezor wallet recovery seed or other sensitive information through phishing emails or websites. Always be cautious and verify the legitimacy of any communication before providing any personal or security-related information. |
| Weak Passwords or PINs | Choosing weak or easily guessable passwords or PINs for your Trezor device can undermine its security. It’s crucial to use strong, unique passwords and PINs to protect against unauthorized access. |
While Trezor provides robust security measures, it ultimately depends on the user to practice good security hygiene. Regularly updating firmware, using strong passwords, enabling two-factor authentication when possible, and applying common sense vigilance can significantly reduce the risk of falling victim to cybercriminals.
In conclusion, while Trezor wallet security is generally considered top-notch, users should remain aware of potential risks and take appropriate precautions to protect their digital assets. By following best practices, such as ensuring physical security, avoiding suspicious communications, and using strong passwords, users can mitigate the risks associated with using the Trezor hardware wallet.
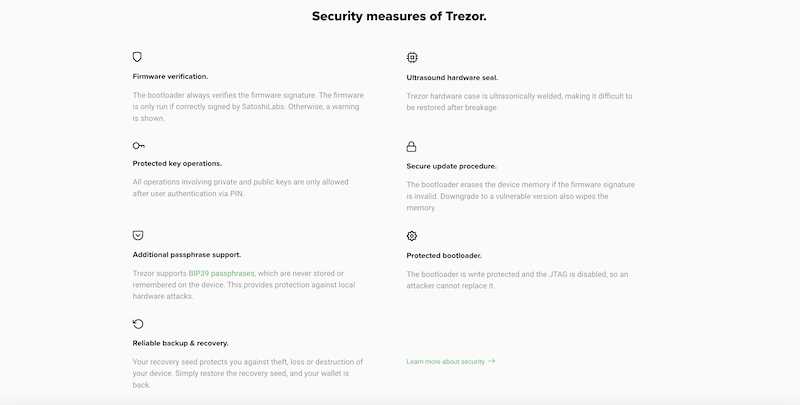
Understanding the Prominent Security Measures Implemented by Trezor

Trezor has been globally recognized as one of the most secure hardware wallets available in the market. This reputation is primarily due to the implementation of several prominent security measures that curb the risks of cybercriminal breaches. Here are some of the key security features and practices that Trezor employs to ensure the safety of user funds and sensitive information:
| Offline Storage: | Trezor wallets operate on an offline system, known as cold storage, which ensures that private keys and sensitive information never come in contact with internet-connected devices. By keeping the wallets offline, the risk of remote attacks and hacking is greatly diminished. |
| Two-Factor Authentication (2FA): | Trezor supports the use of two-factor authentication, which adds an extra layer of security to the wallet. Users are required to provide a second form of verification, such as a physical button on the device or a biometric scan, to access their funds. This makes it significantly harder for cybercriminals to gain unauthorized access. |
| Secure PIN Entry: | Trezor wallets have an on-device PIN entry feature, which ensures that even if the device is compromised or stolen, an attacker cannot gain access to the funds without knowing the correct PIN. This adds an additional layer of protection against physical attacks. |
| Recovery Seed: | During the setup process, Trezor generates a recovery seed consisting of 24 words. This seed acts as a backup and can be used to restore the wallet in case of loss or damage. It is crucial to keep this seed secure and offline to prevent unauthorized access. |
| Hierarchical Deterministic Wallets (HD Wallets): | Trezor utilizes HD wallets, which means that a new public key is generated for each transaction. This feature enhances privacy and security as it minimizes the risks associated with reusing addresses. |
| Firmware Integrity Check: | Trezor regularly releases firmware updates that include security enhancements and bug fixes. Before installing any firmware, the device performs an integrity check to ensure that the firmware has not been tampered with or modified by a malicious entity. |
| Open-Source Software: | Trezor’s software is open-source, allowing developers and security experts to audit the code and identify any vulnerabilities. This transparency aids in building trust and ensures that any potential security issues can be promptly addressed. |
By employing these robust security measures, Trezor aims to provide users with a reliable and secure platform to store their cryptocurrencies without worrying about cybercriminal breaches. Although no security system is entirely foolproof, Trezor’s commitment to continuous improvement and comprehensive security practices significantly minimizes the risks involved.
Potential Vulnerabilities and Risks Associated with Trezor

While Trezor is considered to be one of the most secure hardware wallets on the market, it is not completely immune to potential vulnerabilities and risks. As with any technology, there are factors that could potentially compromise the security of a Trezor wallet.
One potential vulnerability is physical tampering. Although Trezor devices are designed to be tamper-proof, it is still possible for an attacker to physically access the device and attempt to compromise its security measures. This could involve opening the device, modifying its hardware, or attempting to extract sensitive information from the memory or firmware of the device.
Another potential risk is the possibility of a supply chain attack. This occurs when an attacker gains access to the manufacturing or distribution process of the Trezor wallet and injects malicious hardware or firmware into the device. The compromised device could then be used to steal the user’s private keys or perform other malicious activities.
There is also a risk of phishing attacks, where an attacker attempts to trick the user into revealing their private keys or other sensitive information by impersonating a legitimate website or application. This can be achieved through various means, such as sending fake emails or creating fake websites that mimic the official Trezor website or wallet interface.
Additionally, there is a risk of social engineering attacks. Cybercriminals may try to exploit human vulnerabilities by posing as customer support representatives or trusted individuals in order to gain access to the user’s wallet or sensitive information. This can be done through phone calls, emails, or other forms of communication.
It’s important to note that while these vulnerabilities and risks exist, the Trezor team takes security seriously and continuously works to mitigate these potential threats. They regularly release firmware updates to address any discovered vulnerabilities and provide guidance on best practices to ensure the maximum security of the wallet.
To minimize the risks associated with using Trezor, it is recommended to always purchase devices directly from the official Trezor website or authorized resellers. It is also important to follow best security practices, such as enabling two-factor authentication, regularly updating firmware, and being cautious of phishing attempts or suspicious communication.
In conclusion, while Trezor is generally a secure and reliable hardware wallet, it is crucial for users to remain vigilant and aware of potential vulnerabilities and risks. By taking necessary precautions and staying informed about the latest security practices, users can minimize the likelihood of falling victim to cybercriminals.
Best Practices to Ensure the Maximum Security of Your Trezor Wallet

When it comes to securing your Trezor wallet, following best practices is essential to ensure maximum security. Here are some key steps you can take to safeguard your cryptocurrencies:
| 1. Purchase directly from the official website: | Always purchase your Trezor wallet directly from the official website to avoid counterfeit products or tampered devices. |
| 2. Verify the authenticity: | Before using your Trezor wallet, make sure to verify its authenticity by checking the security seal and ensuring that the holographic sticker is intact. |
| 3. Keep your firmware up to date: | Regularly update your Trezor firmware to benefit from the latest security features and bug fixes. |
| 4. Enable the passphrase feature: | Use the passphrase feature on your Trezor wallet to add an extra layer of security. This feature requires an additional passphrase to access your account, making it harder for unauthorized individuals to gain access to your funds. |
| 5. Use a strong and unique PIN: | Create a strong and unique PIN for your Trezor wallet. Avoid using common or easily guessable combinations. |
| 6. Secure your recovery seed: | Protect your recovery seed, which is used to restore your wallet in case of loss or damage. Keep it in a safe place, preferably offline, and away from prying eyes. |
| 7. Be cautious of phishing attempts: | Beware of phishing attempts where cybercriminals masquerade as legitimate sources to trick you into revealing your wallet information. Always ensure you are using the official Trezor website and carefully double-check URLs or email addresses before entering any sensitive information. |
| 8. Avoid public Wi-Fi: | Avoid connecting your Trezor wallet to public Wi-Fi networks, as they can be vulnerable to hacking attempts. Use a trusted and secure internet connection instead. |
| 9. Utilize the “Limited USB Access” feature: | Enable the “Limited USB Access” feature on your Trezor wallet to restrict connections only to trusted devices. This can prevent potential attacks from compromised or malicious computers. |
| 10. Regularly backup your wallet: | Regularly backup your wallet by exporting your public keys and addresses. Store these backups securely in multiple locations to ensure you can recover your funds if your Trezor wallet is lost, stolen, or damaged. |
By following these best practices, you can significantly enhance the security of your Trezor wallet and protect your cryptocurrencies from potential cyber threats.
Q&A:
What security measures does the Trezor wallet have to protect against cybercriminals?
The Trezor wallet has several security measures in place to protect against cybercriminals. It uses a secure chip to store private keys and perform cryptographic operations, which makes it resistant to physical attacks. It also requires a PIN code to access the device, and supports passphrase protection for an added layer of security. Additionally, Trezor uses a secure bootloader to prevent firmware tampering, and offers a recovery seed that can be used to restore the wallet in case of loss or theft.
Is it possible for cybercriminals to hack into a Trezor wallet remotely?
No, it is highly unlikely for cybercriminals to remotely hack into a Trezor wallet. The device utilizes a secure element chip to protect against physical attacks and also requires physical access to enter the PIN code. Without the physical device and the correct PIN code, it is virtually impossible for cybercriminals to access the funds stored in a Trezor wallet.
Can cybercriminals steal funds from a Trezor wallet by guessing the recovery seed?
Gaining access to funds stored in a Trezor wallet by guessing the recovery seed is almost impossible for cybercriminals. The recovery seed is a 24-word passphrase that is randomly generated and displayed only once during the initial setup of the wallet. It has 2048 possible combinations for each word, making the number of potential combinations astronomically large. Brute-forcing the seed to gain access to the wallet is highly unlikely, which makes it a secure method for recovering funds in case of loss or theft.


