A deep dive into the Trezor hack and ways to protect your digital assets

In the world of cryptocurrencies, security is of utmost importance. As the value of digital assets continues to rise, so does the incentive for hackers to find vulnerabilities and exploit them. One recent high-profile hacking incident involved Trezor, one of the most popular hardware wallets for storing cryptocurrencies securely.
So, what exactly happened? A group of hackers managed to find a vulnerability in Trezor’s firmware, allowing them to extract sensitive information such as private keys. This meant that if someone had physical access to a compromised Trezor device, they could potentially steal the owner’s digital assets.
The hack raised concerns among cryptocurrency enthusiasts and highlighted the need for robust security measures. In this article, we will delve deep into the Trezor hack, examining the details of the incident and discussing ways to protect your digital assets from similar attacks.
First and foremost, it’s important to understand the nature of the attack. The vulnerability exploited by the hackers was not a flaw in the underlying technology of cryptocurrencies themselves, but rather a weakness in the implementation of the hardware wallet. Trezor is known for its security features, but this incident serves as a reminder that even the most reputable devices can be compromised.
To protect your digital assets, it is crucial to follow best practices for storing and securing your cryptocurrencies. One of the most effective ways to do this is to use a hardware wallet like Trezor. By keeping your private keys offline and away from potentially vulnerable online platforms, you significantly reduce the risk of being hacked.
Additionally, it is essential to keep your firmware and software up to date. Companies like Trezor regularly release updates to address vulnerabilities and improve security. By staying informed and installing the latest updates, you can stay one step ahead of potential hackers.
In conclusion, the Trezor hack serves as a wake-up call for cryptocurrency holders to prioritize security. While no system is completely foolproof, taking proactive measures such as using hardware wallets, keeping software up to date, and following best practices can go a long way in protecting your digital assets from hackers.
A deep dive into the Trezor hack
The Trezor hack was a significant event in the world of cryptocurrency security. Trezor is a popular hardware wallet that allows users to store their digital assets offline, protecting them from online threats such as hacking and phishing attacks. However, in 2017, a group of hackers managed to exploit a vulnerability in the Trezor hardware wallet and gain access to users’ private keys.
The hack began with a phishing attack, where the hackers sent out emails to Trezor users posing as the company itself. These emails contained links to a fake Trezor website that looked identical to the real one. When users clicked on the links and entered their login credentials, the hackers gained access to their accounts.
Once inside the accounts, the hackers were able to steal users’ private keys, which are crucial for accessing and transferring their digital assets. With the private keys in their possession, the hackers could easily transfer the stolen funds to their own wallets without the users’ knowledge.
The Trezor team quickly became aware of the hack and took action to mitigate its effects. They issued a warning to all users, urging them to be cautious of phishing attempts and only access their wallets through the official Trezor website. They also released an update that fixed the vulnerability and enhanced the security of the hardware wallet.
However, the Trezor hack was a wake-up call for the cryptocurrency community. It highlighted the importance of robust security measures when it comes to protecting digital assets. Users were reminded of the need for strong passwords, two-factor authentication, and regular firmware updates to ensure the safety of their funds.
In conclusion, the Trezor hack was a significant event that highlighted the vulnerability of hardware wallets to phishing attacks. It served as a reminder for users to be vigilant and take necessary precautions to protect their digital assets from hackers. By staying informed and following best practices, individuals can ensure the security of their cryptocurrency investments.
The incident and its impact
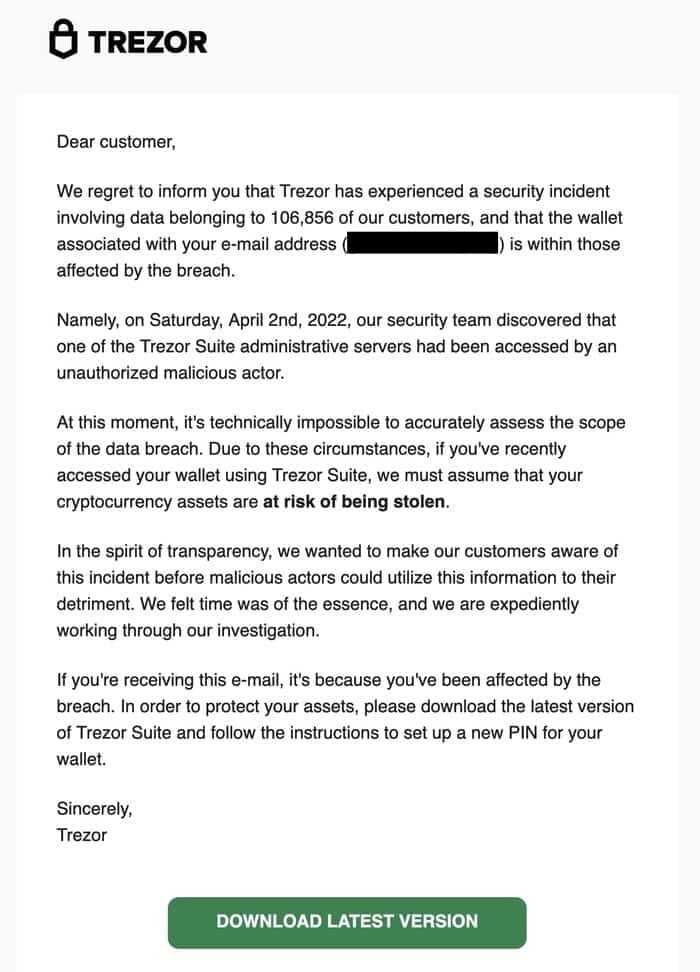
The Trezor hack was a significant event in the world of digital asset security. In January 2020, a team of researchers discovered a vulnerability in the Trezor hardware wallet that allowed hackers to extract the wallet’s private keys. This vulnerability, known as the “evil maid attack,” involved physical access to the device and required the hacker to install malicious firmware. Once the malicious firmware was installed, the private keys stored on the Trezor device could be compromised, leading to potential theft of the digital assets stored in the wallet.
The impact of this incident was far-reaching. Many Trezor users were concerned about the security of their digital assets and questioned the reliability of hardware wallets in general. The incident highlighted the importance of being proactive when it comes to securing digital assets and protecting against potential threats.
Trezor took immediate action to address the vulnerability and released an updated firmware version that addressed the issue. They also provided detailed instructions on how to safely update the firmware to ensure that users could protect their assets. However, the incident served as a reminder that even hardware wallets, which are considered to be one of the most secure methods of storing digital assets, are not immune to attacks.
As a result of the Trezor hack, many users began to explore alternative methods of securing their digital assets. Some turned to other hardware wallets, while others opted for software wallets or other forms of cold storage. The incident also served as a wake-up call to regulators and policymakers, highlighting the need for stronger security standards and regulations in the digital asset space.
- Many Trezor users were concerned about the security of their digital assets.
- The incident highlighted the importance of being proactive when it comes to securing digital assets.
- Trezor released an updated firmware version to address the vulnerability.
- Users began exploring alternative methods of securing their digital assets.
- The incident called for stronger security standards and regulations in the digital asset space.
Understanding the attack vector

The attack on Trezor wallets involved a clever technique known as a supply chain attack. In this type of attack, the hackers infiltrate the supply chain of a company and compromise the software or hardware before it reaches the end user. By doing so, they gain unauthorized access to the user’s digital assets.
In the case of the Trezor hack, the attackers managed to compromise the firmware of the hardware wallets during the manufacturing process. This allowed them to implant a malicious code that would later be executed when the wallet was used by the victim.
The compromised firmware was specifically designed to exploit a vulnerability in the random number generator, which is an essential part of the cryptographic process used by the wallet. By tampering with the random number generator, the hackers were able to generate predictable private keys, giving them control over the victim’s digital assets.
Once the victim received the compromised Trezor wallet, they would connect it to their computer and enter their password. Unbeknownst to them, the malicious code would activate and send the entered password, along with the predictable private keys, to a remote server controlled by the attackers.
With this information, the attackers could then access the victim’s digital assets and transfer them to their own wallets, leaving the victim with no control over their funds.
It’s important to note that the attack was not due to a flaw in the Trezor hardware or firmware itself, but rather a compromise introduced during the supply chain process. This highlights the importance of verifying the integrity of the hardware or software you use for storing your digital assets.
To protect yourself from supply chain attacks, it is recommended to only purchase hardware wallets and other security-related devices from trusted sources. Additionally, it is wise to regularly check for firmware updates and only download them from the official manufacturer’s website.
By understanding the attack vector and taking necessary precautions, you can better safeguard your digital assets and mitigate the risk of falling victim to such attacks.
Protecting your digital assets

In order to protect your digital assets and avoid falling victim to similar attacks, it is crucial to follow some key security measures. Here are a few steps you can take:
1. Use a hardware wallet

One of the best ways to protect your digital assets is by using a hardware wallet, such as Trezor. Hardware wallets store your private keys offline, making it extremely difficult for hackers to access them remotely. It adds an extra layer of security by providing a physical device that you control.
2. Enable two-factor authentication (2FA)

Implementing two-factor authentication adds an extra layer of security to your accounts. By requiring a second verification method, such as a text message code or a fingerprint scan, it becomes much harder for hackers to gain unauthorized access to your digital assets.
3. Keep your software updated

Make sure to regularly update the software and firmware of your hardware wallet. Developers often release updates to fix vulnerabilities and improve security. By staying up to date with the latest patches, you can protect your digital assets from known vulnerabilities.
4. Use strong and unique passwords

Using weak or reused passwords greatly increases the risk of unauthorized access to your accounts. Create strong and unique passwords for each of your accounts and consider using a password manager to securely store and generate passwords.
5. Be cautious of phishing attacks

Phishing attacks are a common method used by hackers to trick users into revealing their sensitive information. Be cautious of any suspicious emails, links, or websites that request your login credentials or personal information. Always verify the authenticity of the source before providing any sensitive data.
By following these security measures, you can greatly reduce the risk of falling victim to attacks and ensure the safety of your digital assets.
Best practices for secure storage

When it comes to storing your digital assets securely, there are several best practices that you should follow:
1. Use a hardware wallet: Hardware wallets, like Trezor, offer an extra layer of security by keeping your private keys offline. This eliminates the risk of being hacked through a software vulnerability or malware. It is an essential tool for protecting your digital assets.
2. Use multisig wallets: Multisig wallets require multiple signatures to authorize a transaction. This provides an added layer of security, as it ensures that even if one private key is compromised, the hacker would still need access to the other signing keys.
3. Enable passphrase protection: Many hardware wallets, including Trezor, allow you to set up an additional passphrase as an extra layer of security. This passphrase should be different from your usual password and never shared with anyone. It adds an extra step of authentication, even if someone gains possession of your hardware wallet.
4. Keep your firmware up to date: Hardware wallet manufacturers regularly release firmware updates to address any security vulnerabilities. By regularly updating your firmware, you can ensure that your wallet has the latest security patches and protection against potential threats.
5. Backup your recovery seed: During the initial setup of your hardware wallet, you will be provided with a recovery seed. This seed is essential for recovering your funds in case your hardware wallet is lost or damaged. It is crucial to write down and safely store this seed in a secure location.
6. Use strong and unique passwords: When creating passwords for your wallets or any online accounts, it is essential to use strong, unique, and complex passwords. Avoid using easily guessable passwords or reusing passwords across multiple platforms.
7. Be cautious of phishing attacks: Phishing attacks are common in the cryptocurrency space. Always double-check the URL of the wallet provider or exchange before entering your login credentials or making any transactions. Avoid clicking on suspicious links or downloading files from unknown sources.
By following these best practices, you can significantly reduce the risk of losing your digital assets to hackers. Remember, the security of your funds is ultimately your responsibility, and taking the necessary precautions is essential to safeguard your assets.
Q&A:
What is the Trezor hack?
The Trezor hack refers to a security vulnerability in the Trezor hardware wallet, which is used to store and protect digital assets such as cryptocurrencies. Hackers found a way to exploit this vulnerability and gain unauthorized access to the wallet, potentially compromising the user’s digital assets.
How did the Trezor hack happen?
The Trezor hack occurred due to a vulnerability in the Trezor hardware wallet’s firmware. Hackers were able to exploit this vulnerability by exploiting a flaw in the device’s security protocols. This allowed them to gain unauthorized access to the wallet and potentially steal the user’s digital assets.


