
Trezor Security Breach Reveals Overall Vulnerability of Cryptocurrency Storage

As the popularity of cryptocurrencies continues to grow, so does the importance of securely storing these digital assets. One of the most popular hardware wallets on the market, Trezor, recently faced a security breach, sparking concerns about the vulnerability of cryptocurrency storage. This incident serves as a wakeup call for users and highlights the need for robust security measures in the world of digital currencies.
Trezor is renowned for its high level of security, providing users with a hardware device that offers cold storage for their cryptocurrencies. However, no system is completely foolproof, and the recent security breach has exposed the potential risks associated with using this popular wallet. The breach involved a sophisticated attack on the firmware, which allowed hackers to gain unauthorized access to user funds. This breach has raised questions about the security practices and protocols employed by Trezor, as well as the potential vulnerabilities inherent in hardware wallets.
The incident serves as a reminder that storing cryptocurrencies offline does not guarantee absolute security. While hardware wallets are generally considered safer than other methods of storage, they are not immune to potential vulnerabilities. This breach highlights the need for constant vigilance and proactive security measures for anyone involved in the world of cryptocurrencies.
Trezor Security Breach

Trezor, a popular hardware wallet used to store cryptocurrencies, experienced a major security breach that exposed the vulnerability of cryptocurrency storage systems. The breach occurred due to a flaw in the device’s security measures, which allowed hackers to gain unauthorized access to users’ private keys and steal their funds.
The vulnerability was discovered by a group of skilled hackers who targeted Trezor’s firmware, the software that runs on the device. By exploiting a flaw in the firmware, the hackers were able to bypass the device’s security features and extract the private keys stored on the device.
This security breach sent shockwaves throughout the cryptocurrency community, as many relied on hardware wallets like Trezor to securely store their digital assets. The incident highlighted the importance of strong security measures and raised concerns about the overall safety of cryptocurrency storage methods.
Trezor quickly responded to the breach by releasing a firmware update that patched the vulnerability and advised all users to update their devices. They also implemented additional security features to prevent similar attacks in the future.
Following the incident, other hardware wallet manufacturers took extra precautions to ensure the security of their devices, recognizing the potential threats posed by hackers. The breach served as a wake-up call for the industry, prompting companies to invest more resources into enhancing the security of their products.
While the Trezor security breach was a significant setback for the cryptocurrency community, it also highlighted the need for constant vigilance and improvement in securing digital assets. It reminded users to carefully research and select secure storage solutions and to regularly update their firmware to protect against potential threats.
Overall, the Trezor security breach was a turning point in the evolution of cryptocurrency storage, shedding light on the vulnerabilities of the technology and driving innovation in security measures. It served as a valuable lesson for the industry, pushing for stronger security protocols and improving the overall safety of cryptocurrency storage.
Understanding the Vulnerability
The Trezor security breach was a wake-up call for many cryptocurrency investors who trusted their digital assets to hardware wallets. It revealed the vulnerability of cryptocurrency storage and highlighted the need for stronger security measures.
The Anatomy of the Breach
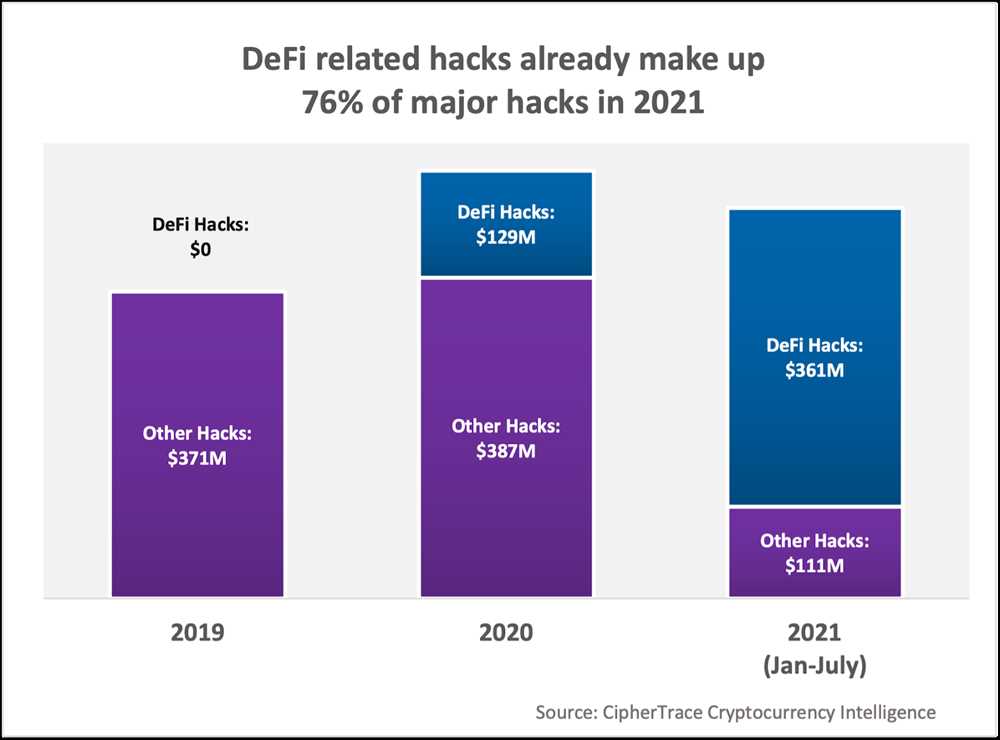
The vulnerability that was exploited in the Trezor security breach involved a physical attack on the device itself. The hackers were able to gain access to the device and extract the private keys, allowing them to steal the stored cryptocurrency. This breach demonstrates that even hardware wallets, which are considered to be one of the most secure forms of cryptocurrency storage, are not immune to attacks.
One of the main factors that contributed to this vulnerability was the reliance on a single point of failure. The private keys stored in the Trezor device were the only barrier between the hackers and the cryptocurrency. Once they were compromised, the funds were easily stolen. This highlights the importance of diversifying security measures and implementing multiple layers of protection in cryptocurrency storage.
Lessons Learned
The Trezor security breach serves as a valuable lesson for the cryptocurrency community. It has shown that no form of storage is 100% foolproof and that constant vigilance and proactive security measures are essential to protect digital assets.
- Regularly updating hardware wallet firmware should be a standard practice to ensure the latest security patches are in place.
- Using strong, unique passwords and enabling 2-factor authentication can provide an additional layer of security.
- Avoiding phishing attempts and suspicious links is crucial to prevent attackers from gaining unauthorized access to cryptocurrency wallets.
- Consider storing a portion of cryptocurrency funds in offline cold storage to mitigate the risk of online attacks.
By understanding the vulnerability exposed by the Trezor security breach and implementing these lessons learned, cryptocurrency investors can better protect their digital assets and reduce the risk of becoming victims of similar attacks in the future.
The Implications for Cryptocurrency Storage

The recent Trezor security breach has highlighted significant vulnerabilities in cryptocurrency storage practices. This breach serves as a reminder that even the most reputable wallets and storage solutions can be susceptible to attacks.
One of the key implications of this breach is the importance of implementing robust security measures when storing cryptocurrencies. Users must not solely rely on hardware wallets or any single solution, but rather adopt a multi-layered approach to mitigate risks. This could involve utilizing a combination of hardware wallets, paper wallets, and cold storage options.
Furthermore, the breach highlights the need for constant vigilance and regular updates when it comes to cryptocurrency storage. Manufacturers and developers must be proactive in identifying and addressing vulnerabilities in their systems, and users need to stay informed and apply the latest security patches and updates. Additionally, it is crucial for users to educate themselves on proper security practices and remain cautious of potential phishing attempts or suspicious links.
The implications of the Trezor security breach also extend beyond individual users. It raises questions about the overall security measures and standards within the cryptocurrency industry. This incident underscores the need for enhanced collaboration and cooperation between wallet manufacturers, exchanges, and regulatory bodies to establish common security guidelines and protocols.
Further research and development into secure storage solutions are also necessary to meet the growing demand for cryptocurrency storage. Innovations such as multi-signature wallets and decentralized storage systems could offer enhanced security features that mitigate the risk of breaches and attacks.
In conclusion, the Trezor security breach serves as a wake-up call for the cryptocurrency industry. It highlights the vulnerabilities of current storage practices and emphasizes the need for improved security measures, heightened user awareness, collaboration, and innovation. By addressing these implications, the industry can strive towards creating a more secure environment for storing and transacting cryptocurrencies.
Question-answer:
What is Trezor?
Trezor is a hardware wallet that allows users to securely store their cryptocurrency.
What is a security breach?
A security breach is an incident where unauthorized individuals or software gain access to confidential information or systems without permission.
What happened in the Trezor security breach?
In the Trezor security breach, a vulnerability in the hardware wallet was exploited, allowing an attacker to gain unauthorized access to the user’s cryptocurrency.
Was anyone’s cryptocurrency stolen in the Trezor security breach?
Yes, some users reported that their cryptocurrency was stolen during the security breach.
How can I protect my cryptocurrency from security breaches?
To protect your cryptocurrency from security breaches, it is recommended to use a hardware wallet like Trezor, keep your wallet software and firmware up to date, and follow best practices for online security, such as using strong passwords and enabling two-factor authentication.


