Why Trezor Is a Top Target for Hackers

When it comes to securing your cryptocurrencies, Trezor is often hailed as one of the most reliable hardware wallets on the market. With its strong encryption and offline storage, Trezor has gained a reputation for being a safe haven for storing digital assets. However, this very reputation also makes it an attractive target for hackers.
Firstly, Trezor’s popularity among cryptocurrency enthusiasts and investors makes it an obvious target for hackers. With more and more people entering the world of cryptocurrencies, the demand for secure storage solutions has skyrocketed. As a result, Trezor’s user base has been rapidly growing, making it an attractive target for hackers seeking to exploit vulnerabilities to gain unauthorized access to users’ funds.
Secondly, Trezor’s offline storage feature, while highly secure, also presents a potential weakness for hackers to exploit. As Trezor is not connected to the internet, it reduces the risk of online attacks. However, this also means that in order to transact or manage their funds, users need to connect their Trezor device to a computer or mobile phone. This connection introduces the device to potential malware or phishing attacks, which can compromise the security of the wallet and expose users’ private keys.
Furthermore, the fact that Trezor is a physical device also makes it vulnerable to physical attacks. Hackers can attempt to gain access to the device by physically stealing it or by tampering with it in some way. By doing so, they can attempt to extract the private keys stored on the device, which would grant them access to the users’ cryptocurrencies.
In conclusion, while Trezor provides robust security measures to safeguard users’ cryptocurrencies, its popularity, offline storage feature, and physical nature make it an attractive target for hackers. It is essential for Trezor users to remain vigilant and take additional precautionary measures, such as using strong passwords and regularly updating their firmware, to minimize the risk of falling victim to malicious attacks.
Security Vulnerabilities in Trezor

While Trezor is considered to be one of the most secure hardware wallets for storing cryptocurrencies, it is not completely immune to security vulnerabilities. Hackers have been known to exploit weaknesses in its system, putting users’ funds at risk.
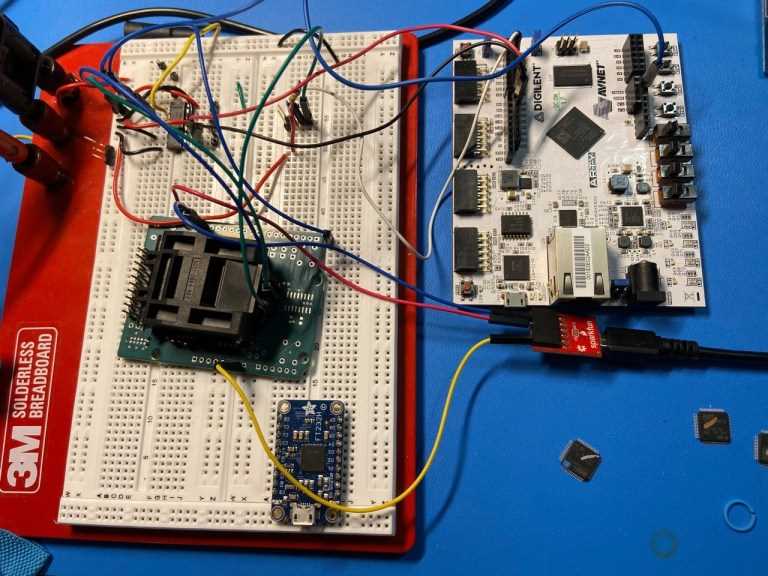
One of the vulnerabilities found in Trezor is related to physical attacks. If a hacker gains physical access to a Trezor device, they can try to extract sensitive data and private keys using various techniques, such as side-channel attacks or glitching. This emphasizes the importance of keeping your Trezor device in a secure location and being cautious with who has access to it.
Another vulnerability is the possibility of firmware tampering. Firmware is the software embedded in the Trezor device that controls its operations. If a hacker manages to tamper with the firmware, they can potentially manipulate the device to compromise the security of the stored cryptocurrency. Therefore, it is crucial to regularly update the firmware to the latest version provided by the official Trezor website and ensure that the device is not tampered with by any unauthorized individuals.
Additionally, there have been cases of phishing attacks targeting Trezor users. Hackers create fake websites or send fraudulent emails that mimic the official Trezor platform, tricking users into entering their seed phrase or other sensitive information. To avoid falling victim to such attacks, it is essential to verify the legitimacy of any website or email before providing any personal information, always accessing the official Trezor website directly.
Trezor has taken measures to address these vulnerabilities and enhance its security. For example, the device has implemented a recovery process that protects against physical attacks, and they continuously provide firmware updates to fix any potential weaknesses. However, it is the responsibility of the users to stay vigilant and follow best practices in order to minimize the risk of being hacked.
| Vulnerability | Description |
|---|---|
| Physical Attacks | Hackers can try to extract sensitive data and private keys if they gain physical access to a Trezor device. |
| Firmware Tampering | If the firmware of a Trezor device is tampered with, hackers can compromise the security of the stored cryptocurrency. |
| Phishing Attacks | Hackers create fake websites or send fraudulent emails to trick users into providing their sensitive information. |
Popularity of Trezor Among Cryptocurrency Users
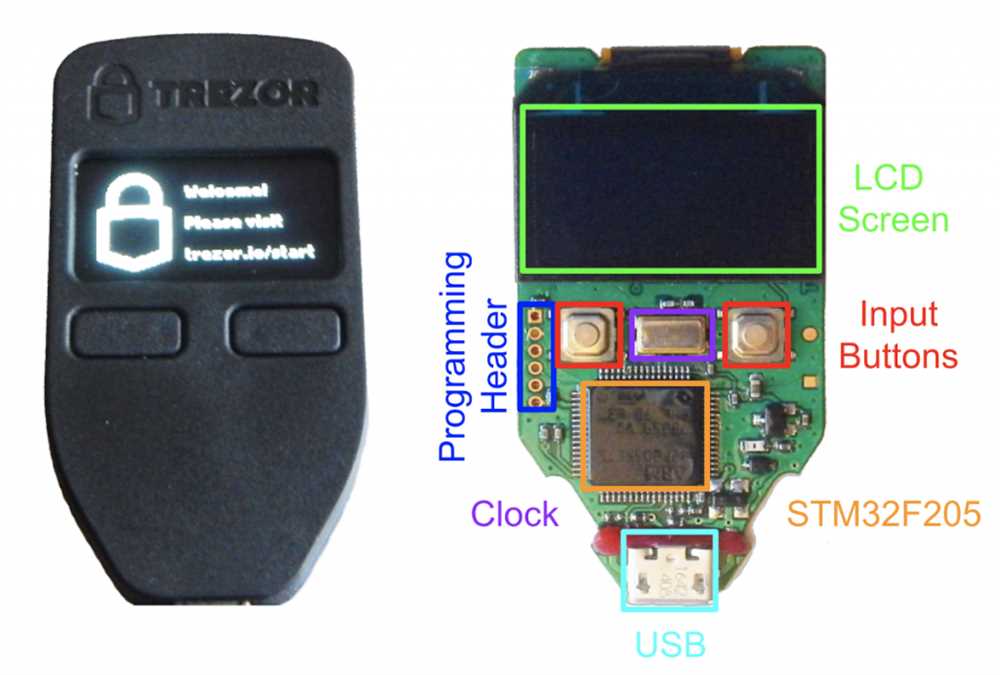
Trezor, a popular hardware wallet, has gained significant popularity among cryptocurrency users due to its advanced security features and user-friendly interface.
One of the main reasons for the popularity of Trezor is its ability to securely store a wide range of cryptocurrencies. From Bitcoin to Ethereum and other altcoins, Trezor supports a diverse array of digital assets, making it a versatile option for cryptocurrency enthusiasts.
Trezor also offers a high level of security through its offline storage and encryption methods. The wallet stores private keys offline, eliminating the risk of online attacks and hacking attempts. Additionally, all transactions made with Trezor are verified on the device itself, further enhancing security.
The user-friendly interface of Trezor is another reason for its popularity. The wallet is designed to be intuitive and easy to navigate, even for beginners. With its clear instructions and straightforward setup process, users can quickly and easily start securing their cryptocurrencies.
Compatibility and Integration
Trezor is compatible with popular operating systems like Windows, macOS, and Linux, making it accessible to a wide range of users. Additionally, it supports integration with popular cryptocurrency wallets and platforms, allowing users to manage their assets seamlessly.
Moreover, Trezor’s popularity is also driven by its commitment to open-source development. By allowing the community to contribute to its software, Trezor ensures continuous improvement and innovation, making it a trusted and reliable choice for cryptocurrency users.
Community and Support
The Trezor community is vibrant and active, providing a wealth of resources and support for users. From online forums to social media groups, users can find answers to their questions, share their experiences, and learn from others.
Trezor also offers excellent customer support, ensuring that users can quickly resolve any issues they might encounter. The dedicated support team is available through various channels, including email and live chat, to assist users with their inquiries.
| Benefits | Drawbacks |
|---|---|
| Advanced security features | Potential vulnerability to physical attacks |
| User-friendly interface | Relatively higher cost compared to software wallets |
| Wide range of supported cryptocurrencies | Limited physical availability in some regions |
Potential for High Financial Gain

One of the main reasons why Trezor attracts hackers is its potential for high financial gain. As a hardware wallet designed to securely store cryptocurrencies, Trezor could be a treasure trove for hackers seeking to steal digital assets.
With a large number of users relying on Trezor to store their valuable cryptocurrencies, successfully breaching its security measures could result in a significant financial windfall for hackers. This makes Trezor an enticing target for cybercriminals who are constantly searching for new ways to exploit vulnerabilities in cryptocurrency storage systems.
Moreover, since Trezor supports a wide range of cryptocurrencies, including Bitcoin, Ethereum, and Litecoin, hacking into a single device could grant hackers access to multiple digital wallets and vast amounts of money. This increases the potential reward for hackers, making Trezor an even more tempting target.
Hackers also target Trezor because of its reputation as a secure hardware wallet. By compromising a widely respected brand like Trezor, hackers can not only gain access to valuable cryptocurrencies but also undermine users’ trust in the security of hardware wallets as a whole. This could lead to widespread panic and the abandonment of hardware wallets in favor of less secure alternatives.
To protect against the potential financial gain that comes with breaching Trezor’s security measures, it is crucial for users to remain vigilant and implement additional security measures. This includes regularly updating the firmware of their Trezor devices, using a strong password, enabling two-factor authentication, and keeping their recovery seed phrase offline and secure.
Overall, the potential for high financial gain is a significant factor that makes Trezor a prime target for hackers. By understanding the motivations behind these attacks and taking proactive steps to enhance security, users can better protect their valuable cryptocurrencies stored in a Trezor wallet.
Lack of Alternative Secure Cold Storage Solutions
When it comes to securing digital assets, a lack of alternative secure cold storage solutions is a significant problem. While there are several hardware wallet options available, Trezor is often the top choice for many cryptocurrency users due to its reputation and security features.
However, this reliance on Trezor as the primary cold storage solution also makes it a prime target for hackers. If there were more alternatives that offered the same level of security and ease of use, the risk would be distributed among multiple devices, reducing the chances of a successful attack.
Additionally, having more secure cold storage options would encourage competition among wallet providers, driving innovation and the development of even stronger security measures. Currently, Trezor’s dominance in the market can create a false sense of security, as there are limited options for users who want to store their digital assets offline.
It is essential for the cryptocurrency community to encourage the development and adoption of alternative secure cold storage solutions. By diversifying the available options, we can reduce the risk of hacking attempts and ensure that users have a wider range of choices when it comes to securing their digital assets.
Q&A:
How secure is Trezor?
Trezor is considered one of the most secure hardware wallets available on the market. It uses various security measures such as encryption, secure element, and two-factor authentication to protect users’ private keys.
What makes Trezor a prime target for hackers?
Trezor is a prime target for hackers due to its popularity and reputation as a secure wallet. It holds a large number of cryptocurrencies and is widely used by individuals and businesses, making it an attractive target for attackers.
Has Trezor ever been hacked before?
No, Trezor has not been hacked before. While there have been some attempts to compromise the device’s security, the company has implemented measures to prevent successful attacks. However, it’s important for users to follow best security practices and keep their firmware and software updated to minimize risks.


