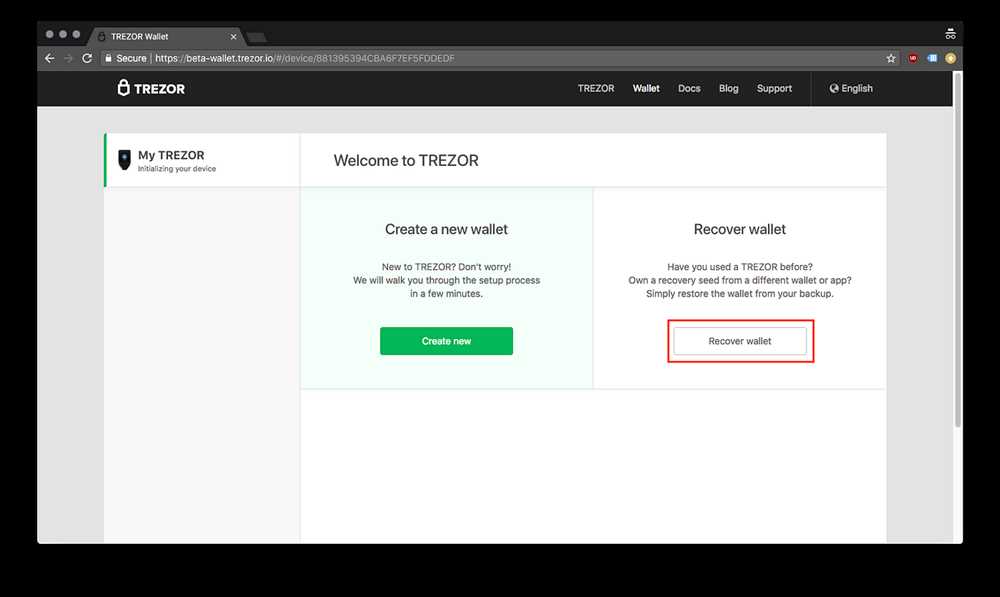
Understanding the Trezor Recovery Process

In the world of cryptocurrencies, security is paramount. With the increasing popularity of digital assets, there has been a surge in attempts to steal or hack into crypto wallets. In order to protect your hard-earned assets, it is essential to choose a secure and reliable wallet. One such wallet is Trezor.
Trezor is a leading hardware wallet that provides a high level of security for your crypto assets. It is a small, portable device that stores your private keys offline, away from prying eyes and potential hackers. However, like any other wallet, there is always a risk of losing or damaging your Trezor device. That’s where the Trezor recovery process comes in.
The Trezor recovery process allows you to regain access to your crypto assets in the event that your Trezor device is lost, stolen, or damaged. It involves the use of a recovery seed, which is a set of randomly generated words that act as a backup for your wallet. This seed can be used to restore your wallet on a new Trezor device or on compatible software wallets.
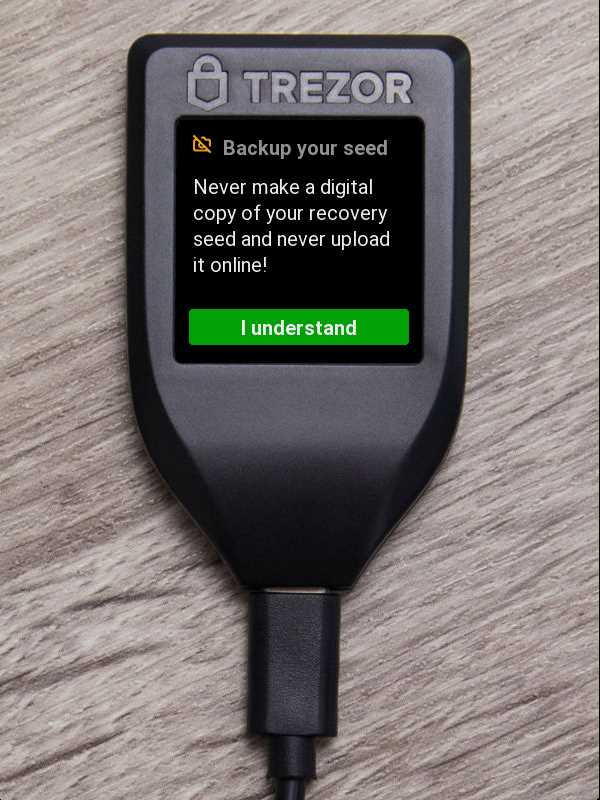
It is important to note that the recovery seed is the most crucial piece of information when it comes to securing your crypto assets with Trezor. It is recommended to write down the seed on a piece of paper and store it in a safe place, such as a lockbox or a fireproof safe. It is also advisable to store multiple copies of the seed in different locations, to minimize the risk of loss or theft.
By following the Trezor recovery process and taking proper precautions to store your recovery seed, you can ensure the security of your crypto assets. Trezor provides a simple and user-friendly interface for recovering your wallet, making it accessible to both beginners and experienced users. With Trezor, you can have peace of mind knowing that your crypto assets are protected by one of the most secure wallets in the market.
Why Secure Your Crypto Assets?
As the popularity of cryptocurrencies continues to rise, so does the importance of securely storing your crypto assets. Whether you have just started your crypto journey or have been a long-time investor, it is crucial to prioritize the security of your digital assets.
Here are a few reasons why securing your crypto assets is essential:
| Protection against hacks and theft | With the increasing value of cryptocurrencies, hackers are constantly looking for ways to compromise security. By implementing strong security measures, such as using hardware wallets like Trezor, you can significantly reduce the risk of your assets being stolen. |
| Peace of mind | Knowing that your crypto assets are securely stored gives you peace of mind. You can focus on other aspects of your crypto journey without constantly worrying about the safety of your investments. |
| Protecting yourself from human error | Mistakes happen, and when it comes to handling cryptocurrencies, even a small mistake can lead to irreversible consequences. By securing your assets with a reliable recovery process, such as the one offered by Trezor, you can protect yourself from accidental loss or deletion of your crypto holdings. |
| Preparing for the future | The crypto landscape is constantly evolving, and regulations may be introduced to ensure the security of digital assets. By proactively securing your crypto assets, you are positioning yourself ahead of any potential regulatory requirements, ensuring that you are ready for the future of crypto. |
In conclusion, securing your crypto assets is not just a choice, but a necessity in today’s digital world. By taking proactive steps to protect your investments, you can mitigate risks and enjoy a more secure and stress-free crypto experience.
Step-by-Step Guide: Securing Your Crypto Assets with Trezor
Securing your crypto assets is crucial in protecting your investment. Using the Trezor hardware wallet is one of the most secure ways to safeguard your cryptocurrencies. Follow these step-by-step instructions to secure your crypto assets with Trezor:
- Connect your Trezor device to your computer using the USB cable.
- Visit the Trezor website and download the Trezor Bridge software.
- Install the Trezor Bridge software on your computer.
- Open the Trezor website and follow the instructions to set up your Trezor device.
- Create a strong and unique PIN for your Trezor device.
- Write down your recovery seed on the recovery card provided by Trezor. Make sure to keep this card in a safe and secure place.
- Set a passphrase for your device to add an extra layer of security.
- Install the Trezor Wallet software on your computer or use the web wallet.
- Connect your Trezor device to your computer and unlock it using your PIN.
- Access the Trezor Wallet interface and manage your crypto assets securely.
- When making transactions, always verify the details on your Trezor device.
- Keep your Trezor device and recovery card in separate locations to prevent loss or theft.
Following these steps will ensure that your crypto assets are safely stored in your Trezor hardware wallet. Remember to regularly update your Trezor firmware and keep your recovery card and PIN secure.
Start securing your crypto assets with Trezor today and enjoy peace of mind knowing that your investment is protected.
Benefits of Using the Trezor Recovery Process
When it comes to securing your crypto assets, the Trezor recovery process offers several key benefits:
1. Enhanced Security: The Trezor recovery process is designed to provide additional layers of security for your crypto assets. By using a combination of encryption and multifactor authentication, Trezor ensures that your private keys are protected from unauthorized access.
2. User-Friendly Interface: The Trezor recovery process is designed to be user-friendly, making it easy for even beginners to secure their crypto assets. The device features a simple interface with clear instructions and prompts, allowing you to navigate through the recovery process with ease.
3. Offline Recovery: Unlike other recovery processes that require an internet connection, the Trezor recovery process can be done completely offline. This adds an extra layer of security, as it eliminates the risk of your recovery information being intercepted by hackers or malware.
4. Compatibility: The Trezor recovery process is compatible with a wide range of cryptocurrencies, including Bitcoin, Ethereum, and many others. This means that no matter what type of crypto assets you hold, Trezor can help you secure them.
5. Peace of Mind: By using the Trezor recovery process, you can have peace of mind knowing that your crypto assets are secure. The device is built with the highest standards of security and has been thoroughly tested to ensure its reliability.
Overall, the Trezor recovery process offers a secure and user-friendly way to protect your crypto assets. Whether you’re a beginner or an experienced crypto investor, using Trezor can provide you with the peace of mind you need to confidently navigate the crypto world.
Q&A:
Why is it important to secure crypto assets?
Securing crypto assets is crucial because unlike traditional financial systems, cryptocurrencies do not have a central authority that can control or reverse transactions. Without proper security measures, crypto assets can be vulnerable to theft or loss, and once they are gone, they cannot be recovered.
What is the Trezor recovery process for crypto assets?
The Trezor recovery process is a method of restoring access to your crypto assets in case your Trezor hardware wallet is lost, stolen, or damaged. It involves using a recovery seed, which is a set of randomly generated words that act as a backup to your wallet’s private keys. By entering the recovery seed into a new Trezor device or compatible wallet software, you can regain control of your crypto assets.


