
Trezor’s response to the security breach and what users can expect

In recent news, Trezor, one of the leading companies in the field of cryptocurrency hardware wallets, has faced a security breach. This incident has raised concerns among the users about the safety of their funds and personal information. However, it is crucial to understand that Trezor has taken immediate action to address this situation and protect its users.
Trezor’s top priority is the security of its customers. The company has implemented robust security measures to prevent unauthorized access and protect sensitive data. Upon discovering the breach, Trezor conducted a thorough investigation to determine the extent of the incident and identify any potential vulnerabilities.
As a result, Trezor has implemented enhanced security protocols and measures to ensure the safety of its users’ funds and information. This includes strengthening the encryption algorithms, implementing multi-factor authentication, and improving the overall security of its systems.
Furthermore, Trezor is working closely with cybersecurity experts and law enforcement agencies to investigate the incident and identify the perpetrators. The company has pledged full transparency throughout this process and will provide regular updates to its users to keep them informed about any developments.
Trezor also recommends its users to take certain precautionary measures to enhance their own security. This includes enabling two-factor authentication, regularly updating firmware and software, and being cautious of phishing attempts. By following these best practices, users can further protect their assets and personal information.
Overall, while the security breach is undoubtedly concerning, Trezor’s swift response and commitment to user security are commendable. The company is taking all necessary steps to rectify the situation, strengthen its security measures, and restore users’ confidence in its product.
Despite this incident, Trezor remains one of the most secure options for storing and managing cryptocurrencies. Users can continue to rely on Trezor’s hardware wallets as a trusted means of safeguarding their digital assets.
Statement from Trezor Regarding Recent Security Incident
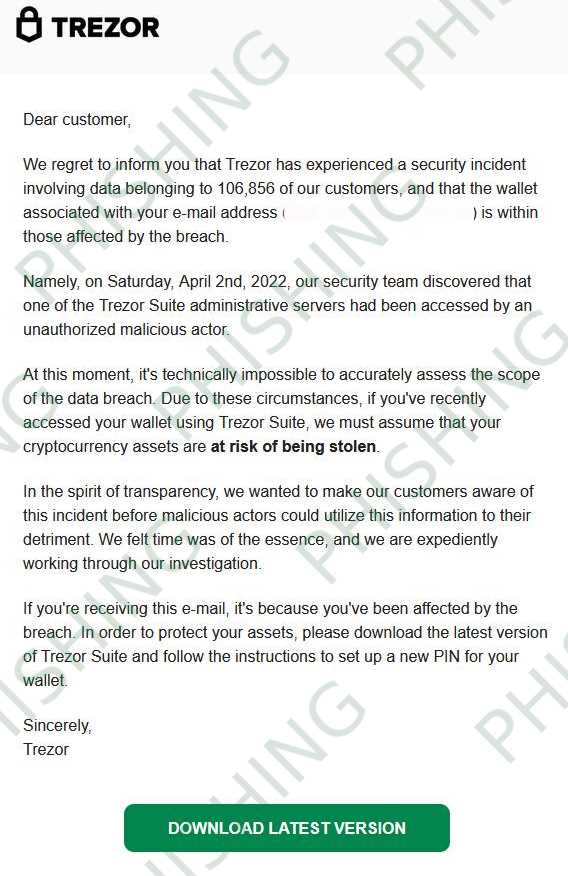
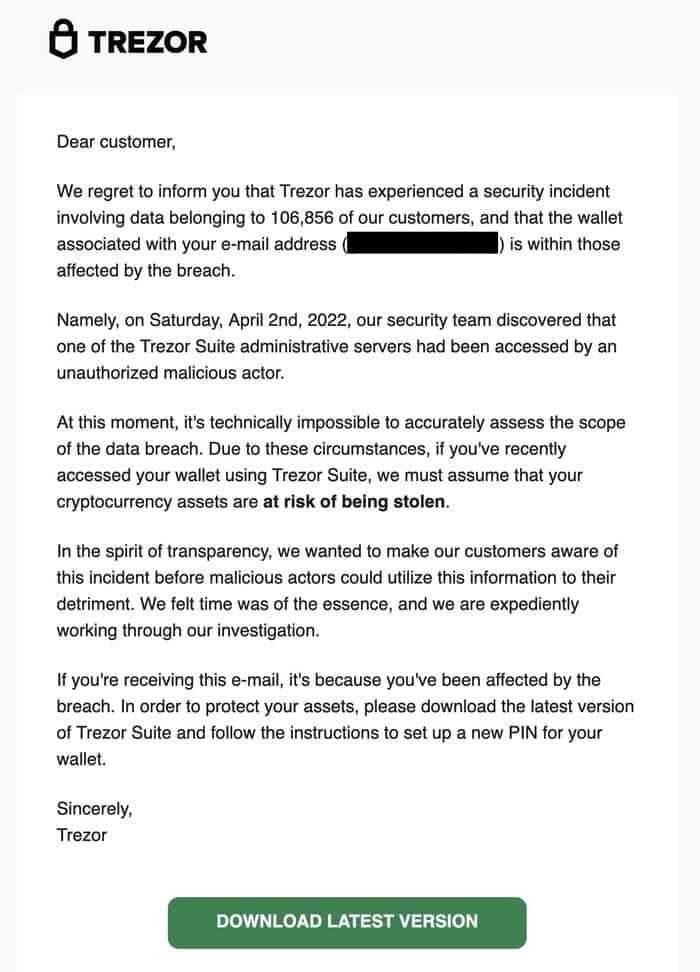
Dear Trezor users,
We are writing to inform you about a recent security incident that affects the security of your Trezor hardware wallet. We apologize for any inconvenience and want to assure you that we are taking immediate action to address the issue.
Upon discovering this incident, our team immediately launched an investigation to determine the extent of the breach and identify any potential vulnerabilities. We are working closely with security experts to ensure the highest level of protection for our users.
In light of this incident, we recommend that all Trezor users take the following steps to secure their assets:
1. Update firmware:
Please ensure that you are running the latest firmware version on your Trezor device. This will include any necessary security updates to mitigate the risks associated with this incident.
2. Change recovery seed:
We recommend generating a new recovery seed and transferring your assets to this new seed. This will ensure that your funds are secure and protected from any potential unauthorized access.
3. Enable passphrase:
If you have not already done so, we strongly encourage you to enable the passphrase feature on your Trezor device. This will provide an additional layer of security by requiring a unique passphrase to access your funds.
We understand that this incident may cause concern and we want to reassure you that the security of your funds is our top priority. We will continue to provide updates and support as we work to resolve this issue.
Thank you for your understanding and patience.
The Trezor Team
Steps Taken by Trezor to Address the Breach
Trezor takes the security breach very seriously and has taken several immediate steps to address the issue and protect its users.
1. Investigation
As soon as the breach was discovered, Trezor initiated a comprehensive investigation to determine the extent of the breach and the potential impact on user information.
2. Security Enhancement
Trezor has strengthened its security measures to prevent similar breaches from occurring in the future. This includes implementing additional encryption and authentication protocols, as well as conducting regular security audits and penetration testing.
3. Communication with Users
Trezor immediately notified its users about the security breach and provided guidance on how to protect their accounts. Regular updates are being sent to keep users informed about the progress of the investigation and any additional steps they need to take to ensure their accounts remain secure.
4. User Support

Trezor has dedicated a team of support agents to assist users who may have been affected by the security breach. Users are encouraged to reach out to Trezor’s support team for any questions or concerns they may have.
5. Collaboration with Authorities

Trezor is working closely with law enforcement agencies and regulatory bodies to investigate the breach and identify the responsible parties. This collaboration aims to bring the perpetrators to justice and prevent future breaches.
Trezor remains committed to the security and privacy of its users and will continue to take proactive measures to ensure their funds and information are protected.
Measures Users Should Implement to Protect Their Assets
To ensure the safety of your assets and minimize the risk of hacking or security breaches, it is essential that users implement certain security measures. By following these guidelines, you can significantly enhance the security of your Trezor devices and keep your digital assets safe:
| 1. Enable Two-Factor Authentication (2FA): | Enabling 2FA provides an additional layer of security by requiring users to provide a second form of verification, typically through a mobile app or SMS confirmation, to access their accounts. This adds an extra barrier against unauthorized access. |
| 2. Use Strong Passwords: | Ensure that you use strong, complex passwords that are unique for your Trezor device. Avoid using easily guessable or commonly used passwords, and consider using a password manager to securely store and generate strong passwords. |
| 3. Regularly Update Firmware and Software: | Stay up to date with the latest firmware and software updates provided by Trezor. These updates often include important security patches and fixes that address any vulnerabilities that may have been discovered. |
| 4. Be Cautious of Phishing Attempts: | Be wary of any unsolicited emails or messages requesting personal information or asking you to visit unfamiliar websites. Phishing attempts can often appear legitimate and trick users into divulging sensitive information, so it’s important to exercise caution and verify the authenticity of any requests. |
| 5. Backup Your Recovery Seed: | Always securely backup your Trezor recovery seed. This seed is crucial for recovering your assets in case of loss or theft of your device. Store it in a secure location separate from your device and ensure that it is protected from unauthorized access. |
| 6. Utilize Passphrase (Advanced Users): | If you’re an advanced user, consider utilizing the optional passphrase feature offered by Trezor. This adds an extra layer of security by requiring an additional passphrase to access your device, even if your device itself is compromised. |
| 7. Stay Informed: | Stay informed about the latest security practices and news in the cryptocurrency industry. This will help you stay up to date with any emerging threats or vulnerabilities and enable you to take appropriate actions to protect your assets. |
By implementing these measures, users can enhance the security of their Trezor devices and protect their assets from potential security breaches or hacking attempts.
Future Plans and Improvements in Trezor’s Security System
Trezor takes the security of its users’ assets very seriously, and is dedicated to continuously improving its security system to stay ahead of potential threats. In light of the recent security breach, Trezor has outlined several future plans and improvements:
1. Enhanced Two-Factor Authentication

Trezor plans to implement an enhanced two-factor authentication (2FA) system to provide an additional layer of protection for users. This will require users to authenticate their transactions using multiple authentication methods, such as a physical token and a biometric verification.
2. Advanced Threat Detection
Trezor will invest in advanced threat detection technologies to proactively identify and mitigate potential security risks. This includes implementing machine learning algorithms and artificial intelligence to analyze user behavior and detect any suspicious activities in real-time.
Furthermore, Trezor will collaborate with security experts and researchers to conduct regular security audits and penetration testing to identify and address any vulnerabilities in its system.
Overall, Trezor is committed to providing its users with the highest level of security for their assets. The company will continue to invest in research and development to stay at the forefront of security advancements in the cryptocurrency industry.
Disclaimer: The above plans and improvements are subject to change as Trezor continues to prioritize and evaluate its security measures.
Q&A:
What happened to Trezor’s security?
Trezor recently suffered a security breach, where an attacker was able to gain access to the customer email list. The attacker did not have access to any customer wallets or funds.
Was any customer information compromised in the security breach?
Yes, the attack resulted in the exposure of the customer email list. However, no other customer information, such as passwords or wallet keys, was compromised.


