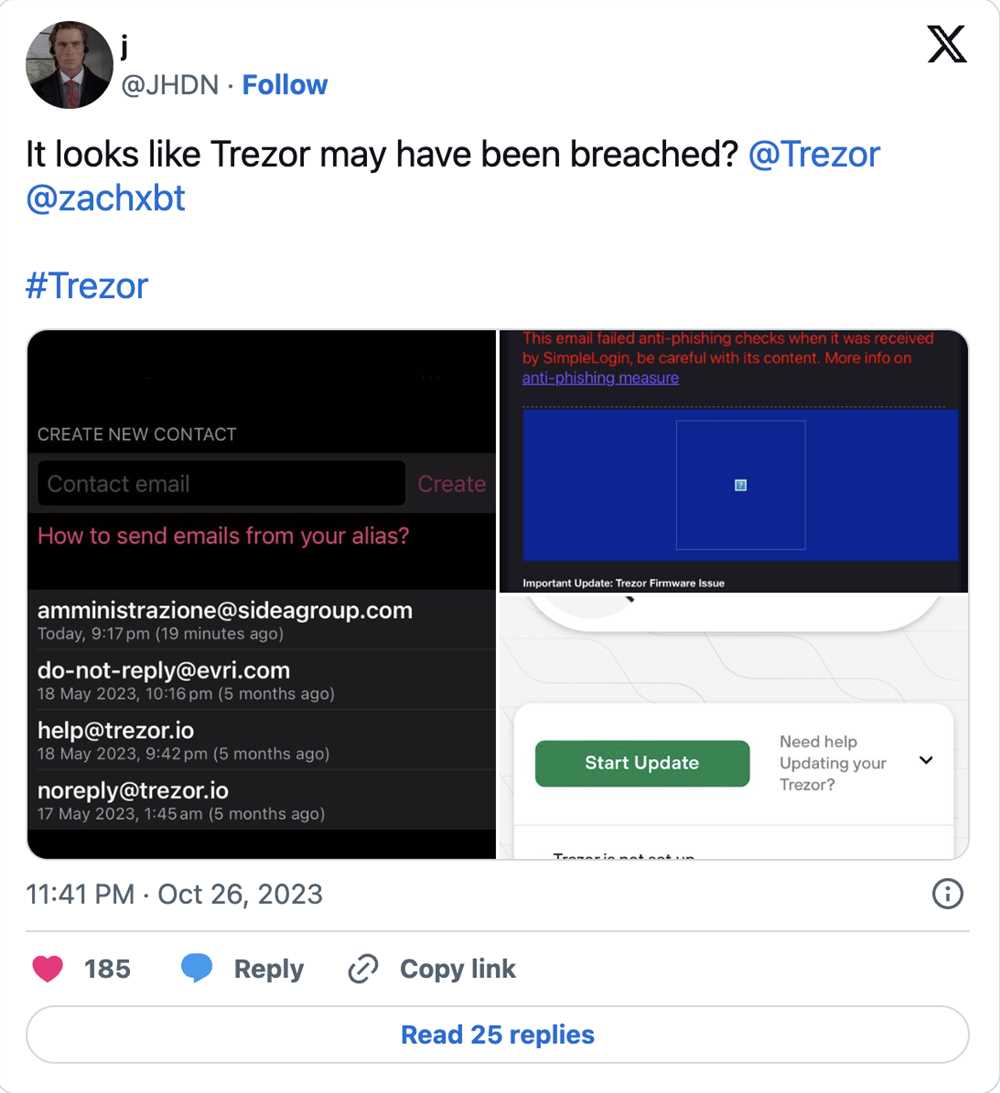
Trezor’s Response to Recent Security Breaches in the Industry

In the wake of recent security breaches in the cryptocurrency industry, Trezor, one of the leading hardware wallet manufacturers, has taken significant steps to enhance the security of their products and protect their users’ assets. With the growing popularity of cryptocurrencies, the industry has become an attractive target for hackers and scammers, highlighting the urgent need for robust security measures.
Trezor has recognized the gravity of the situation and has made it their top priority to provide the highest level of security to their users. They have implemented a multi-layered approach that combines hardware and software enhancements to ensure the safety and integrity of their wallets. These measures involve both preventive and reactive strategies, aiming to prevent security breaches as well as swiftly respond to any potential threats.
One of the key enhancements introduced by Trezor is the implementation of advanced encryption algorithms. By leveraging cutting-edge cryptography techniques, Trezor ensures that users’ private keys are stored securely and that all transactions are signed in a tamper-resistant environment. This significantly reduces the risk of unauthorized access and ensures that users have full control over their funds at all times.
In addition to encryption, Trezor has also strengthened their firmware and software security. Regular security updates are released to address potential vulnerabilities and provide users with the latest protection against evolving threats. Trezor’s commitment to ongoing security improvements sets a standard for the industry, elevating the level of security for all hardware wallet users.
Furthermore, Trezor has been proactive in collaborating with external security experts and engaging in thorough security audits. By subjecting their products to rigorous testing and independent evaluation, Trezor ensures that any potential vulnerabilities are identified and addressed promptly. This ongoing collaboration with the security community reinforces Trezor’s commitment to transparency and their dedication to protecting their users’ assets.
With their comprehensive security measures, Trezor aims to set a new benchmark for hardware wallet security in the cryptocurrency industry. By taking proactive steps and continuously improving their products, Trezor is committed to providing their users with the highest level of security and peace of mind. As the industry faces ever-increasing threats, Trezor’s efforts to enhance security are a testament to their unwavering commitment to protecting their users’ funds.
Trezor’s Latest Security Measures
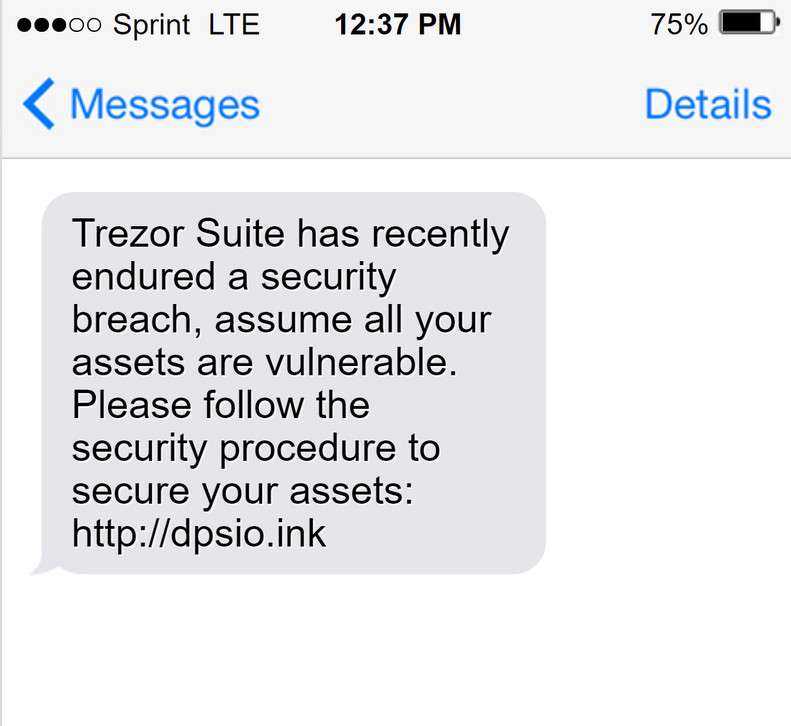
Trezor, one of the leading providers of cryptocurrency hardware wallets, understands the importance of security in the industry. In response to recent security breaches in the industry, Trezor has introduced a number of latest security measures to ensure the safety of its users’ funds.
Secure Firmware: Trezor has developed a secure firmware that is regularly updated to address any potential vulnerabilities. The firmware undergoes rigorous testing and auditing to ensure its integrity and resistance to attacks.
Enhanced Encryption: Trezor has implemented enhanced encryption algorithms to protect users’ private keys and seed phrases. This ensures that even if the device is compromised, the sensitive information remains secure and cannot be accessed by unauthorized individuals.
Multi-Factor Authentication: Trezor now offers multi-factor authentication options, such as the use of biometric data or hardware tokens, to provide an additional layer of security. This ensures that even if an attacker gains access to a user’s device, they would still need additional authentication factors to access the funds.
Physical Tamper-proof Design: Trezor’s hardware wallets are designed with physical tamper-proof mechanisms, making it extremely difficult for attackers to tamper with the device without leaving noticeable traces. This provides users with confidence that their device has not been compromised during shipping or in any other way.
Continuous Security Audits: Trezor conducts regular security audits by independent third-party companies to identify and address any potential vulnerabilities. This helps ensure that Trezor’s security measures are up to date and in line with industry best practices.
By implementing these latest security measures, Trezor aims to provide its users with a highly secure and trusted cryptocurrency storage solution. Users can have peace of mind knowing that their funds are protected by state-of-the-art security features.
Strengthened Hardware Security
In response to the recent security breaches in the industry, Trezor has taken significant measures to strengthen the hardware security of its devices. These measures aim to enhance the resistance of Trezor wallets against physical attacks and tampering attempts.
One of the key improvements is the implementation of a secure element in Trezor devices. This secure element provides an extra layer of protection by storing sensitive information, such as private keys, in a dedicated and isolated hardware chip. This isolation prevents unauthorized access to the keys, even if the main microcontroller is compromised.
Furthermore, Trezor has introduced advanced anti-tampering measures to detect any unauthorized attempts to open or modify the device. The device’s hardware is designed to provide visual and physical indicators of tampering, such as seals that break upon opening and internal sensors that detect changes in the device’s integrity. If any tampering is detected, the device will enter a secure mode and prevent any further operations.
Trezor also employs rigorous testing and verification processes during the manufacturing of its devices to ensure the integrity and security of the hardware. This includes sophisticated inspections and quality assurance procedures to detect and prevent any potential vulnerabilities or defects.
Benefits of Strengthened Hardware Security
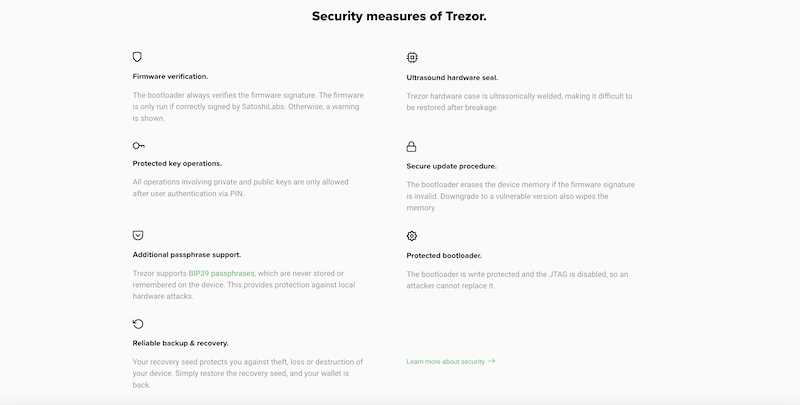
The strengthened hardware security measures implemented by Trezor offer several benefits:
- Enhanced Protection: The secure element and anti-tampering measures significantly increase the overall security of Trezor devices, safeguarding the user’s private keys and digital assets.
- Peace of Mind: With the strengthened hardware security, users can have greater confidence in the integrity and reliability of their Trezor wallets.
- Resistance to Physical Attacks: The additional security measures make it more difficult for attackers to gain physical access to the device and extract sensitive information.
- Prevention of Tampering: The anti-tampering features help users detect and prevent any unauthorized attempts to modify or compromise their Trezor wallets.
By continuously investing in hardware security advancements, Trezor remains committed to providing its users with the highest level of protection for their digital assets.
Enhanced Firmware Protection

Trezor understands the importance of firmware security in safeguarding our users’ cryptocurrencies. In light of recent security breaches in the industry, we have implemented enhanced measures to protect the firmware of our hardware wallets.
Secure Code Development Practices

Our team of expert developers follows strict secure code practices when developing and maintaining the firmware for our Trezor wallets. This includes adhering to industry best practices, conducting regular code reviews, and performing comprehensive testing to identify and fix any potential vulnerabilities.
We also prioritize the use of open-source software to foster transparency and allow the community to contribute to the security of our products. By opening up our code for auditing, we ensure that any potential weaknesses can be identified and addressed promptly.
Multi-Factor Authentication

In addition to secure code practices, Trezor implements multi-factor authentication to enhance the protection of the firmware. Users are required to go through a two-step authentication process before making any changes to the firmware or accessing their cryptocurrencies.
With the implementation of multi-factor authentication, even if an attacker manages to gain unauthorized physical access to the device, they would still need to provide the correct authentication credentials to carry out any malicious activities. This adds an extra layer of security, significantly reducing the risk of unauthorized firmware modifications.
At Trezor, we are committed to continuously improving the security of our products and providing our users with the highest level of protection for their cryptocurrencies. Our enhanced firmware protection measures are just one aspect of our comprehensive security approach, aimed at ensuring the safety and peace of mind of our users.
Improved User Authentication
Trezor is committed to providing a secure and seamless user experience, and as part of our latest measures in response to security breaches in the industry, we have implemented enhanced user authentication methods.
One of the key improvements we have made is the introduction of multi-factor authentication. This means that in addition to entering your username and password, you will also need to provide a secondary form of verification, such as a one-time password (OTP) generated by an authentication app or sent to your registered mobile phone number.
With multi-factor authentication, even if an attacker manages to obtain your username and password, they will still be unable to access your account without the secondary verification code. This significantly reduces the risk of unauthorized access.
In addition to multi-factor authentication, we have also introduced stronger password requirements. This ensures that your account is better protected against brute-force attacks and makes it more difficult for hackers to guess or crack your password.
Biometric Authentication

Another exciting feature we have introduced is biometric authentication. With this technology, you can now use your unique biological traits, such as your fingerprint or facial recognition, to unlock your Trezor device and authorize transactions.
Biometric authentication provides an added layer of security as it is nearly impossible for someone to replicate your fingerprints or facial features. This ensures that only you have the ability to access your Trezor device and perform transactions.
Push Notifications
To further enhance user authentication, we have also implemented push notifications. Whenever there is a login attempt or a transaction request on your account, you will receive a notification on your registered mobile device. You can then review the details and either approve or deny the request directly from your device.
This system allows you to quickly and conveniently verify any login or transaction activity, ensuring that you are always in control of your account and alerted to any potentially unauthorized access.
At Trezor, we understand the importance of keeping your digital assets secure, which is why we are continuously improving our user authentication methods. With these enhanced security measures in place, you can have peace of mind knowing that your Trezor account is protected against potential security breaches in the industry.
Q&A:
Why are security breaches in the cryptocurrency industry a concern to users?
Security breaches in the cryptocurrency industry are a concern to users because they can result in the theft of their digital assets. Cryptocurrency is stored in digital wallets, and if these wallets are compromised, users can lose all of their funds.
What are some of the security measures that Trezor has implemented to address security breaches?
Trezor has implemented several security measures to address security breaches. One measure is the use of a secure chip that helps protect the private keys stored on the device. The company also uses an open-source firmware that undergoes regular security audits. Additionally, Trezor encourages users to enable the passphrases feature and regularly updates its software to fix any vulnerabilities.
How does Trezor’s use of a secure chip help protect users’ private keys?
Trezor’s use of a secure chip helps protect users’ private keys by storing them in a separate, isolated environment. This means that even if the device is compromised, the private keys cannot be extracted from the secure chip. The secure chip also helps to ensure that the private keys are generated and signed securely, further reducing the risk of theft.
What are the benefits of using an open-source firmware for Trezor?
Using an open-source firmware for Trezor offers several benefits. First, it allows independent security audits to be conducted, helping to identify and fix any vulnerabilities. Second, it allows the community to contribute to the codebase, which can lead to improvements in security. Finally, an open-source firmware builds trust with users, as they can review the code themselves and ensure that there are no hidden backdoors or vulnerabilities.


