
Trezor targeted: analyzing hackers’ tactics and motivations

In recent years, there has been a surge in cyberattacks targeting cryptocurrency users, with hackers constantly finding new ways to steal digital assets. One such attack that has gained significant attention is the Trezor attack, where hackers exploit vulnerabilities in the popular hardware wallet to gain unauthorized access to users’ funds. In this article, we will analyze the tactics used by the hackers and delve into their motives behind these attacks.
The Trezor attack involves leveraging social engineering techniques to trick users into providing their wallet’s recovery seed phrase, which is a sequence of words used to restore access to the wallet in case of loss or theft. These hackers often impersonate Trezor support representatives or create phishing websites that closely resemble the official Trezor website. Once users unknowingly share their seed phrase, the attackers gain full control over their funds and can transfer them to their own wallets.
What motivates these hackers to carry out such attacks? One of the main motives is financial gain. Cryptocurrency theft can be highly lucrative, especially if the hackers manage to gain access to wallets holding a significant amount of digital assets. Additionally, the relative anonymity of cryptocurrencies makes it difficult to trace stolen funds, increasing the chances of the attackers successfully profiting from their illicit activities.
Another motive behind these attacks could be a desire for notoriety or a demonstration of hacking prowess. Cryptocurrency communities are often highly active and closely follow security breaches and vulnerabilities. By successfully compromising a widely used hardware wallet like Trezor, hackers can garner attention and establish themselves as skilled and knowledgeable individuals in the hacking community.
Given the increasing popularity of cryptocurrencies, it is crucial for users to remain vigilant and implement strict security measures to protect their digital assets. This includes double-checking the authenticity of any communication claiming to be from wallet providers, never sharing seed phrases or private keys with anyone, and regularly updating firmware and software to protect against known vulnerabilities. By understanding the tactics and motives behind these attacks, users can better protect themselves from falling victim to such cybercrimes.
Understanding the Trezor attack
The Trezor attack has been a major concern for cryptocurrency users and the larger blockchain community. Understanding the intricacies of this attack can help us better protect our digital assets and prevent future cyber threats.
The attack on Trezor: an overview

The attack targeted the Trezor hardware wallet, a popular device for storing private keys and conducting cryptographic transactions. The hackers exploited a vulnerability in the firmware of the Trezor wallet, allowing them to gain unauthorized access to users’ funds.
Method of attack: The hackers initiated a phishing campaign, sending fraudulent emails and messages asking users to update their Trezor firmware. The victims were tricked into downloading a malicious firmware update, which enabled the attackers to compromise the security of the wallet.
Motives behind the attack: The primary motive for the Trezor attack appears to be financial gain. By gaining access to users’ private keys and seed phrases, the hackers could steal their cryptocurrency holdings and transfer them to their own wallets. Additionally, the attackers might have been motivated by a desire to disrupt the cryptocurrency market and undermine user confidence.
Lessons learned from the attack
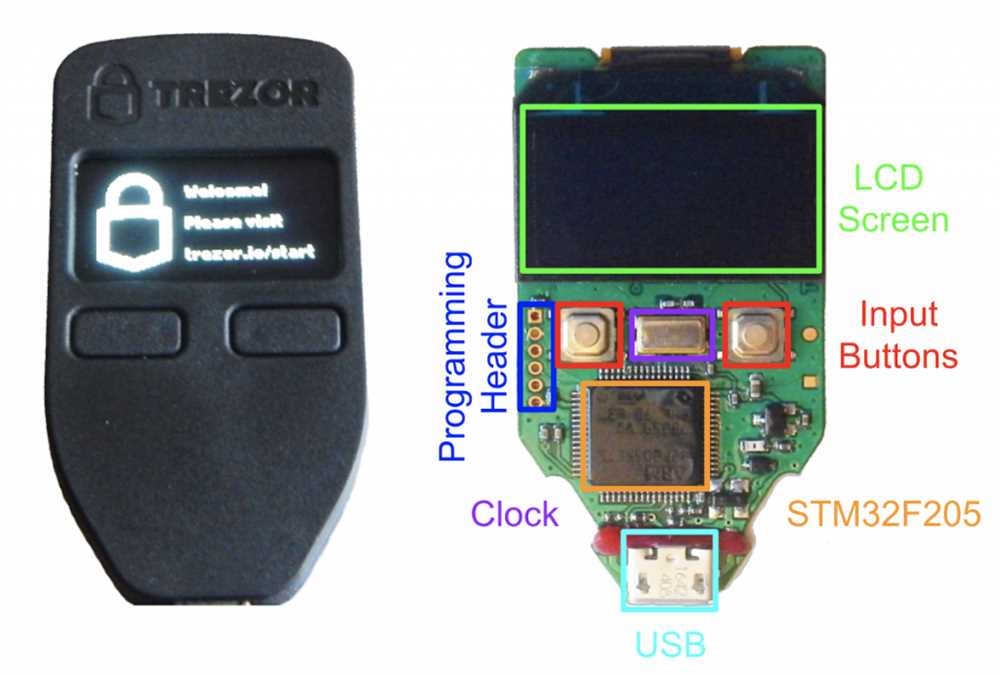
Importance of firmware security: The Trezor attack highlights the importance of regularly updating firmware and maintaining strong security measures. It is crucial for hardware wallet manufacturers to prioritize firmware security to prevent unauthorized access and potential financial losses for their users.
Increased awareness of phishing scams: The attack serves as a reminder of the ever-present threat of phishing scams. Users should be cautious of any unsolicited requests to update their firmware or share sensitive information. Verifying the authenticity of communication and double-checking the validity of firmware updates can help prevent falling victim to such attacks.
In conclusion, understanding the Trezor attack provides valuable insights into the tactics and motives of hackers, enabling us to enhance our cybersecurity practices and ensure the safety of our digital assets. By staying vigilant and adopting robust security measures, we can mitigate the risks associated with such attacks and protect ourselves in the evolving landscape of cryptocurrency security.
Examining the hackers’ tactics
Understanding the tactics employed by hackers in the Trezor attack is crucial in order to enhance security measures and anticipate future threats. By closely examining their methods, we can develop strategies to better protect our assets and data.
One primary tactic used by the hackers was a phishing scheme. They created a fake website that closely resembled the official Trezor website, tricking users into entering their recovery seeds. The hackers then used these recovery seeds to gain unauthorized access to users’ cryptocurrency wallets.
| Tactic | Description |
|---|---|
| Impersonation | The hackers impersonated the official Trezor website, using a similar domain name and design to deceive users. |
| Social engineering | Through carefully crafted emails and messages, the hackers manipulated users into visiting the fake website and entering their recovery seeds. |
| Exploiting trust | By taking advantage of the trust users had in the Trezor brand, the hackers were able to convince individuals to disclose sensitive information. |
| Timing | The hackers launched the attack during a time when users were expecting a firmware update from Trezor, leading to a higher chance of users falling for the scam. |
By analyzing these tactics, it becomes evident that education and awareness are essential in preventing such attacks. Users should be educated on how to identify phishing attempts and verify the authenticity of websites and messages they receive. Trezor and other cryptocurrency wallet providers can also enhance security measures by implementing multi-factor authentication and regularly communicating with users about potential threats.
Uncovering the motives behind the attack
The Trezor attack was a sophisticated cyber-attack aimed at compromising the security of users’ cryptocurrency wallets. To fully understand the motives behind this attack, it is necessary to analyze the tactics employed by the hackers.
Tactic 1: Financial Gain

One of the most obvious motives behind the Trezor attack is financial gain. By compromising the security of users’ wallets, the hackers could potentially gain access to their funds and steal their cryptocurrencies. This can be a highly lucrative activity, especially considering the rising value of many cryptocurrencies in recent years.
Tactic 2: Reputation Damage

Another possible motive for the attack is to damage the reputation of Trezor and undermine users’ trust in the company. By successfully compromising the security of a popular hardware wallet like Trezor, the hackers can create doubt and uncertainty in the minds of users, potentially driving them to switch to alternative wallet providers.
In order to further understand the motives behind the attack, it is important to consider the potential impact on the wider cryptocurrency ecosystem. The attack not only targeted individual users, but also had the potential to disrupt the entire cryptocurrency market. This disruption could lead to a decline in market confidence and a subsequent drop in cryptocurrency prices.
In conclusion, financial gain and reputation damage are two key motives that might explain the Trezor attack. By compromising the security of users’ wallets and potentially accessing their funds, the attackers could stand to gain significant profits. Additionally, by damaging the reputation of Trezor and undermining trust in the company, the attackers could drive users to seek alternative wallet providers.
| Motives | Tactics |
|---|---|
| Financial Gain | Gaining access to users’ funds and stealing cryptocurrencies |
| Reputation Damage | Undermining trust in Trezor and driving users to switch to alternative wallet providers |
Protecting against future attacks

In order to protect against future attacks similar to the Trezor attack, it is important to take certain measures to enhance security. Here are some recommended steps to safeguard your assets:
| 1. | Keep your software updated |
| 2. | Enable two-factor authentication |
| 3. | Use a hardware wallet |
| 4. | Store your assets offline |
| 5. | Verify the authenticity of your wallet provider |
| 6. | Enable strong and unique passwords |
| 7. | Be cautious of phishing attempts |
| 8. | Regularly review your transaction history |
| 9. | Consider using a VPN |
| 10. | Stay informed about the latest security practices |
By following these recommendations, you can greatly reduce the risk of falling victim to future attacks and ensure the safety of your digital assets. It is essential to stay vigilant and proactive in protecting your funds in the ever-evolving landscape of cybersecurity.
Q&A:
What is the Trezor attack?
The Trezor attack refers to a cyber attack that targeted users of the Trezor hardware wallet, a popular cryptocurrency storage device. The attack involved a malicious app that was designed to trick users into entering their recovery seed, compromising the security of their wallets.
How did the hackers carry out the Trezor attack?
The hackers carried out the Trezor attack by creating a fake app called “Trezor Wallet” and uploading it to the Google Play Store. This app looked very similar to the official Trezor app, but it was actually a phishing tool that aimed to steal users’ recovery seeds.


