Trezor One Security Audit Findings and Action Plan

Trezor One, the popular hardware wallet, recently underwent a comprehensive security audit to ensure the integrity of its users’ cryptocurrency holdings. The audit was conducted by a team of renowned cybersecurity experts, who meticulously examined the device’s hardware and software security features.
During the audit, several key findings were made that warrant attention. One of the most significant discoveries was the identification of a potential vulnerability in the random number generator used by Trezor One. This vulnerability, if exploited, could have allowed malicious actors to derive the seed phrase used to generate the wallet’s private keys.
In response to this finding, the team at Trezor One immediately took action to address the issue. They collaborated with the security experts to develop and implement a patch that eliminates the vulnerability. Additionally, Trezor One has reinforced its security protocols and conducted a thorough review of its entire codebase to ensure that all known vulnerabilities are proactively addressed.
The security audit of Trezor One serves as a testament to the company’s commitment to providing its users with the highest level of security. By actively identifying and resolving vulnerabilities, Trezor One exemplifies the importance of continuous improvement and ongoing vigilance in the rapidly evolving field of cryptocurrency security.
Overview of the Audit Process
The security audit conducted on Trezor One was a comprehensive and thorough examination of the device’s security measures. It involved a team of highly skilled experts in the field of cybersecurity who carefully analyzed the device’s hardware and software components.
During the audit process, the team systematically reviewed the Trezor One’s cryptographic algorithms, firmware, and protocols. They assessed the device’s resistance to various attack vectors, including physical attacks, side-channel attacks, and network attacks.
Furthermore, the audit involved vulnerability assessments, penetration testing, and code review to identify any potential security weaknesses. The team also evaluated the Trezor One’s adherence to industry standards and best practices in secure hardware and software development.
Throughout the audit, the team discovered several key findings that required attention and further mitigation measures. These findings were promptly communicated to the Trezor team, who responded with a detailed plan to address each identified issue.
The audit process was conducted with the utmost confidentiality and professionalism to ensure the security of proprietary information and maintain the trust of the Trezor user community. Both the auditors and the Trezor team worked collaboratively to resolve any security concerns and improve the overall security posture of the Trezor One device.
In conclusion, the audit process provided a comprehensive review of Trezor One’s security measures and identified areas for improvement. The collaborative effort between the auditors and the Trezor team ensured that these findings were appropriately addressed, resulting in a more secure and trustworthy device for Trezor users.
Key Findings from the Security Audit
During the security audit of the Trezor One hardware wallet, several key findings were uncovered. These findings provide valuable insights into the strengths and weaknesses of the device’s security features.
1. Limited Attack Surface

One of the main strengths identified in the security audit was the limited attack surface of the Trezor One. The device runs a minimalistic firmware with a reduced number of components, reducing the potential vulnerabilities that attackers can exploit.
2. Robust Encryption and Authentication
The security audit revealed that the encryption and authentication mechanisms implemented in the Trezor One are strong and resistant to known attacks. With its built-in cryptographic features, the device ensures that the private keys remain protected even in the event of physical tampering.
3. Secure Bootloader and Firmware Updates

The audit also confirmed the effectiveness of the secure bootloader and firmware update processes. These features prevent unauthorized firmware modifications, ensuring that the device always runs trusted software and minimizing the risk of compromise.
4. Potential Physical Attacks

While the Trezor One showed robustness against most types of attacks, the security audit revealed potential vulnerabilities to physical attacks. These attacks include side-channel attacks, which rely on analyzing power consumption or electromagnetic radiation to extract sensitive information.
5. User Interface Vulnerabilities

Another key finding was the presence of some user interface vulnerabilities that could potentially be exploited by attackers. These vulnerabilities could allow attackers to trick users into performing unintended actions, such as approving unauthorized transactions.
Overall, the security audit of the Trezor One highlighted the device’s strong security features, but also identified some areas for improvement. By addressing the identified vulnerabilities, the Trezor team can further enhance the device’s security and provide users with even greater peace of mind.
| Strengths | Weaknesses |
|---|---|
| Limited attack surface | Potential physical attacks |
| Robust encryption and authentication | User interface vulnerabilities |
| Secure bootloader and firmware updates |
Response to the Security Audit Findings

We would like to thank the security audit team for their detailed analysis of the Trezor One device. Their findings have allowed us to further strengthen the security measures and address potential vulnerabilities. We take these results seriously and have already taken steps to address the issues identified in the security audit.
Fixing Vulnerabilities
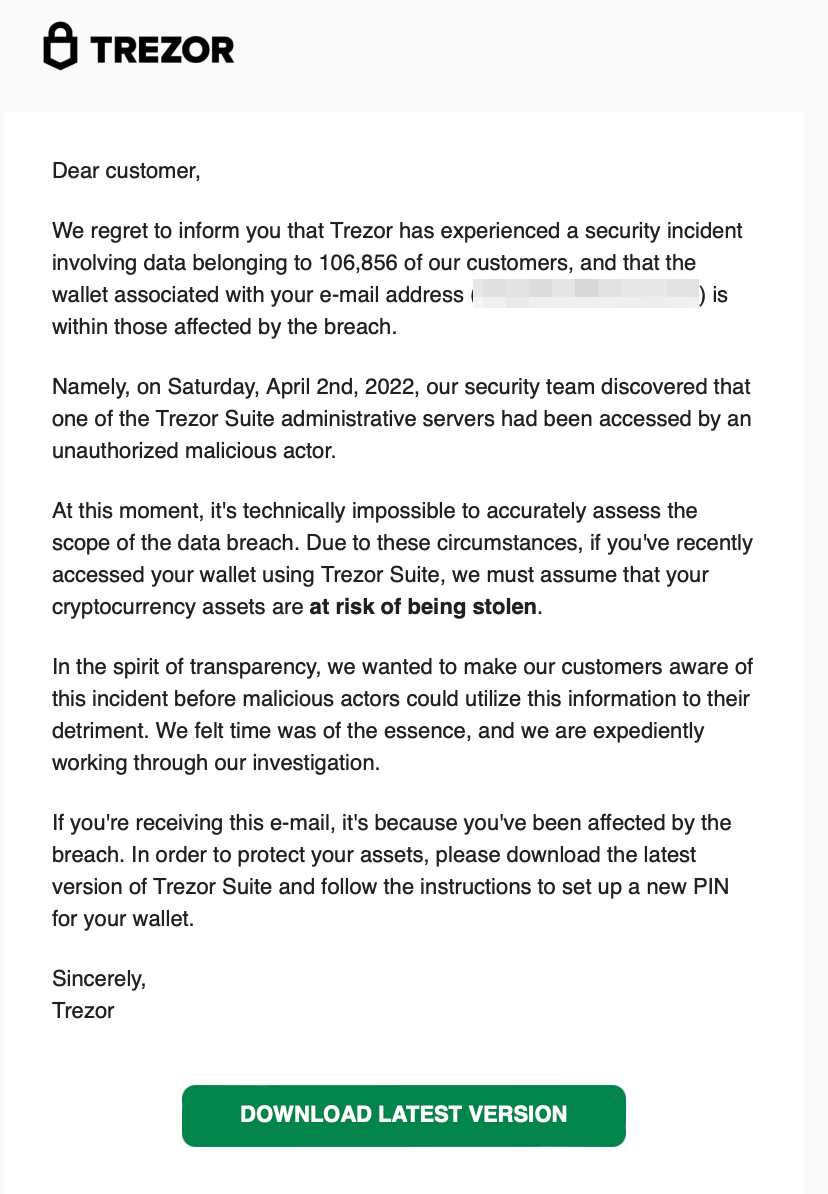
Based on the security audit findings, we have implemented several fixes to address the vulnerabilities that were identified. These fixes include:
- Updating the firmware to address potential attack vectors
- Improving the implementation of encryption algorithms
- Increasing the complexity of the PIN verification process
We understand the importance of constantly improving our security measures to protect our users’ funds and data. By promptly addressing the vulnerabilities identified in the security audit, we aim to provide a safer and more secure experience for Trezor One users.
Enhancing Security Practices

In addition to fixing vulnerabilities, we are continuously working to enhance our security practices. We believe that security is an ongoing process, and we are committed to staying ahead of potential threats. To achieve this, we have implemented the following measures:
- Regularly conducting internal security audits
- Engaging external security experts for third-party audits
- Collaborating with the wider security community to gather feedback and improve our security practices
By constantly evaluating and improving our security practices, we strive to maintain the highest level of security for our users.
We are grateful to the security audit team for their valuable insights and recommendations. The findings from the security audit have allowed us to make important enhancements to the Trezor One device, ensuring our users’ peace of mind when it comes to the security of their funds.
Q&A:
What is Trezor One?
Trezor One is a hardware wallet developed by SatoshiLabs. It is designed to securely store cryptocurrencies, such as Bitcoin, Ethereum, and many others.
What was the purpose of the security audit of Trezor One?
The purpose of the security audit was to identify any potential vulnerabilities or weaknesses in the Trezor One hardware wallet that could compromise the security of users’ cryptocurrency holdings.


