Trezor Hacked Lessons Learned and Steps Towards a Secure Future

In the fast-paced world of cryptocurrency, security is paramount. When it comes to protecting digital assets, hardware wallets have been touted as the most secure option. However, even the most secure systems can fall victim to hacking attempts. Recently, the popular hardware wallet Trezor was hacked, leaving users wondering about the safety of their funds.
The Trezor hack serves as a stark reminder that no system is impervious to attack. However, it also provides an opportunity to reassess and improve the security measures in place. The incident has highlighted key lessons learned and paved the way for steps towards a more secure future.
Trezor, known for its robust security features, was breached through a sophisticated phishing attack. Hackers created a fake Trezor website that closely resembled the official one, tricking unsuspecting users into entering their wallet seed phrases. This breach emphasizes the need for constant vigilance and education among cryptocurrency users. It is crucial to verify the authenticity of websites and ensure that all communications and transactions are securely encrypted.
Since the Trezor hack, the company has taken swift action to address the issue and improve security. They have introduced additional measures such as two-factor authentication and multi-signature wallets to provide users with added layers of protection. Furthermore, they have ramped up their efforts in educating users about potential threats and best practices for keeping their funds safe.
While the Trezor hack was undoubtedly a setback for both the company and its users, the incident has sparked a renewed commitment to security in the cryptocurrency community. As the industry continues to grow, it is essential for hardware wallet manufacturers and users alike to remain proactive in their approach to security. By constantly evolving and adapting to new threats, we can move towards a future where digital assets are protected to the highest degree possible.
Trezor Hacked: Analyzing the Situation
The recent hack of the Trezor hardware wallet has raised concerns and highlighted the importance of securing our digital assets. Let’s analyze the situation to understand the implications and lessons learned from this incident.
- Attack Method: The hackers used a sophisticated malware attack to gain unauthorized access to the Trezor wallet. This demonstrates the evolving nature of cyberattacks and the need for constant vigilance in protecting our digital currencies.
- Scope of the Hack: The exact extent of the hack is still being investigated, but initial reports suggest that a number of wallets were compromised. This highlights the potential vulnerability of hardware wallets and the need for continuous improvement in their security features.
- User Responsibility: While the hack itself is a concerning event, it also serves as a reminder of the importance of user responsibility in securing our digital assets. Users should follow best practices, such as using strong passwords and enabling two-factor authentication, to enhance the security of their wallets.
- Response from Trezor: Trezor responded swiftly to the incident, acknowledging the breach and reassuring users that steps are being taken to address the vulnerabilities. They have advised users to update their firmware and exercise caution when installing third-party applications.
- Lessons Learned: This incident serves as a wake-up call for the entire cryptocurrency community. It is a reminder of the ever-present threat of cyberattacks and the need for constant improvement in security measures. It also underscores the importance of staying informed about the latest security practices and regularly updating our hardware wallets to ensure maximum protection.
Overall, the Trezor hack serves as a valuable lesson for the industry as a whole, prompting us to reevaluate the security measures we have in place and driving us towards a more secure future for cryptocurrencies.
Understanding the Security Breach and Its Impact

In the world of cryptocurrency, security is paramount. The recent security breach that affected Trezor, a popular hardware wallet, has raised concerns about the safety of digital assets and the vulnerabilities that exist within the system.
The security breach occurred when sophisticated hackers were able to exploit a vulnerability in the firmware of the Trezor device. This allowed them to gain access to the private keys and steal funds from unsuspecting users. The impact of this breach has been significant, with a loss of funds for those affected and a loss of trust in the security measures of Trezor.
One key lesson from this breach is the importance of constant vigilance and the need for regular security updates. It is crucial for users to frequently update the firmware of their Trezor device to ensure the latest security patches are in place. Additionally, users should be cautious about using unofficial software or firmware, as it could potentially expose them to unnecessary risks.
Another important lesson learned is the need for multi-factor authentication. By requiring multiple forms of verification, such as a password and a physical key, the chances of unauthorized access can be significantly reduced. Implementing strong and unique passwords, as well as regularly changing them, is also essential in maintaining a secure system.
The impact of the security breach extends beyond individual users. The reputation of Trezor has been tarnished, and the entire cryptocurrency community has been reminded of the potential risks associated with storing digital assets. However, this incident serves as a call to action for both hardware wallet manufacturers and users to prioritize security and work towards a more secure future.
In conclusion, the recent security breach that affected Trezor has highlighted the importance of constant vigilance, regular security updates, multi-factor authentication, and strong passwords. The impact of this breach has raised concerns within the cryptocurrency community, but it also serves as a reminder to prioritize security and strive for a safer environment.
Identifying the Vulnerabilities and Weaknesses

When it comes to the security of devices like Trezor, it is crucial to identify and address any vulnerabilities and weaknesses. By understanding the potential weak points, we can take steps to strengthen the security measures and ensure a secure future.
One vulnerability that was exploited in the Trezor hack was the lack of multi-factor authentication. By implementing an additional layer of authentication, such as a fingerprint or a hardware key, the chances of unauthorized access can be greatly reduced.
Another weakness in the Trezor device lies in the firmware. It is essential to regularly update the firmware to patch any known vulnerabilities. Additionally, conducting regular security audits and penetration testing can help identify any new vulnerabilities and weaknesses.
Furthermore, physical security is equally important. The physical protection of the device should be taken into consideration. Measures like tamper-evident packaging and secure storage can help prevent unauthorized access to the device.
In addition to these vulnerabilities and weaknesses, it is essential to address issues related to social engineering attacks. Educating users about potential threats and implementing strict protocols for verifying identity can help prevent phishing attacks and other forms of social engineering.
| Vulnerabilities | Weaknesses |
|---|---|
| Lack of multi-factor authentication | Outdated firmware |
| Physical security breaches | Social engineering attacks |
By identifying these vulnerabilities and weaknesses, we can take proactive steps to address them and enhance the security of devices like Trezor. With continuous monitoring, updates, and user education, we can ensure a more secure future for cryptocurrency storage.
Lessons Learned from the Trezor Hacking Incident

The Trezor hacking incident served as a wake-up call for the cryptocurrency industry, highlighting the importance of security and the need for constant vigilance in protecting digital assets. The following are key lessons that can be learned from this incident:
1. Regularly Update Security Measures
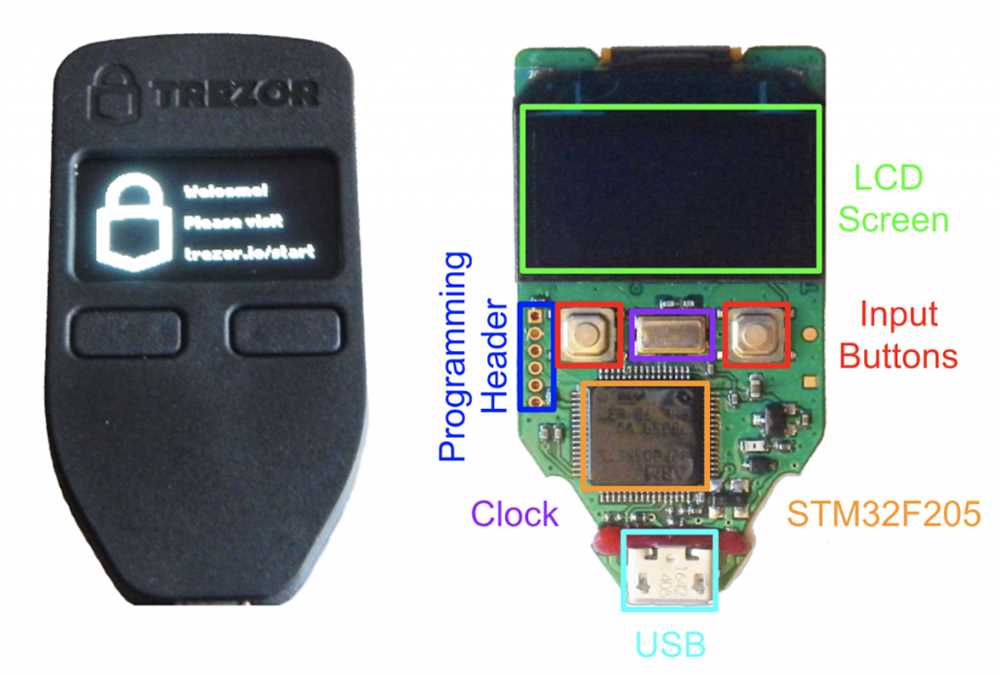
One of the major takeaways from the Trezor hacking incident is the importance of regularly updating security measures. As technology advances and new vulnerabilities are discovered, it is crucial for hardware wallet manufacturers to stay one step ahead by releasing timely firmware updates that address any potential security flaws.
2. Implement Multi-Factor Authentication

While Trezor does offer password protection, the incident showed that this may not be sufficient to prevent unauthorized access to funds. To enhance security, hardware wallets should implement multi-factor authentication, such as using a combination of PIN codes, biometrics, and time-based one-time passwords (TOTP). This adds an extra layer of security and makes it much more difficult for hackers to gain unauthorized access.
3. Conduct Regular Security Audits

Hardware wallet manufacturers should conduct regular security audits to identify potential vulnerabilities and ensure that their devices meet the highest security standards. These audits should involve both internal teams and external experts who can thoroughly assess the device’s security architecture and offer recommendations for improvement.
4. Educate Users on Security Best Practices

Users must be educated on security best practices to minimize the risk of being targeted by hackers. Hardware wallet manufacturers should provide clear and comprehensive instructions on how users can secure their devices, including setting strong passwords, enabling PIN codes, and avoiding phishing attempts. Additionally, manufacturers should regularly update their user manuals and support resources to reflect the latest security recommendations.
5. Maintain Open Communication with the Community

Transparency and open communication are essential in building trust within the cryptocurrency community. In the event of a security incident, hardware wallet manufacturers should promptly disclose the details to their users and the wider community. This helps raise awareness, enables users to take proactive measures, and fosters a culture of collaboration in addressing security concerns.
By implementing these lessons learned from the Trezor hacking incident, hardware wallet manufacturers can take significant steps towards improving the security of their devices and ultimately ensuring the protection of users’ digital assets.
Analyzing the Mistakes Made and Their Consequences
When it comes to the security of cryptocurrency wallets, mistakes can have serious consequences. The recent hacking incident involving Trezor, one of the leading hardware wallet providers, serves as a stark reminder of this fact. It is crucial to analyze the mistakes made in order to prevent similar situations in the future and ensure a secure environment for users.
1. Lack of Two-Factor Authentication
One of the main mistakes made by Trezor was the lack of two-factor authentication (2FA) for accessing the wallet. Two-factor authentication adds an extra layer of security by requiring users to provide a second verification method, such as a code sent to their mobile device, in addition to their password. By not implementing 2FA, Trezor left its users vulnerable to attacks where hackers could gain access to their wallets simply by obtaining or cracking their password.
Consequence: The absence of 2FA made it easier for hackers to compromise the security of Trezor wallets, potentially leading to the loss of users’ funds.
2. Insufficient Firmware Update Process

Another mistake made by Trezor was an insufficient firmware update process. Firmware updates are crucial for fixing known vulnerabilities and maintaining the security of the wallet. However, Trezor’s firmware update process was not robust enough, making it easier for hackers to exploit vulnerabilities and gain unauthorized access to the wallets.
Consequence: This weakness in the firmware update process allowed hackers to manipulate the security features of Trezor wallets, putting users’ funds at risk.
Overall, the hacking incident involving Trezor serves as a valuable lesson for the cryptocurrency industry. It emphasizes the need for robust security measures, including two-factor authentication and a strong firmware update process, to ensure the safety of users’ funds. By analyzing the mistakes made and their consequences, the industry can take steps towards a more secure future for cryptocurrency wallets.
Question-answer:
How was the Trezor hacked?
The Trezor was not officially hacked. The article discusses a hypothetical scenario in which a hacker gains physical access to the Trezor device and attempts to retrieve the private keys stored inside. The author demonstrates various techniques that a determined hacker could potentially use to extract the private keys.
What are the lessons learned from the Trezor hack?
The main lessons learned from the hypothetical Trezor hack are the importance of physical security, the need for regular firmware updates, and the value of using strong passwords. Additionally, the article emphasizes the significance of choosing a reputable hardware wallet manufacturer and understanding the potential risks associated with storing cryptocurrency.
What steps can be taken to ensure a secure future for cryptocurrency storage?
To ensure a secure future for cryptocurrency storage, it is recommended to follow best practices such as keeping hardware wallets in secure locations, regularly updating firmware, using strong passwords, and enabling additional security features like two-factor authentication. It is also crucial to stay informed about the latest security vulnerabilities and advances in the field of cybersecurity.


