
The Trezor Hack: Lessons Learned for the Cryptocurrency Community

Recent news of the Trezor hack has sent shockwaves through the cryptocurrency community, highlighting the importance of security and vigilance when it comes to protecting digital assets. Trezor, one of the most popular hardware wallet providers, was targeted by hackers who were able to gain unauthorized access to users’ wallets.
The hack serves as a wake-up call to all cryptocurrency holders, reminding them of the potential vulnerabilities they face in the digital world. While hardware wallets like Trezor have been considered one of the safest options for storing cryptocurrencies, this incident proves that no security measure is foolproof.
One of the key takeaways from the Trezor hack is the need for multi-layered security. Users should not rely solely on a single security measure, but rather implement a combination of measures, such as strong passwords, two-factor authentication, and regular software updates. This will make it much more difficult for hackers to gain access to your digital assets.
Another important lesson is the importance of staying informed and educated about the latest security threats and best practices. The cryptocurrency landscape is constantly evolving, and new threats emerge on a regular basis. By staying up to date with the latest security measures and following best practices, users can greatly reduce the risk of falling victim to hacks and other security breaches.
In conclusion, the Trezor hack serves as a stark reminder of the need for constant vigilance and proactive security measures in the cryptocurrency community. By adopting multi-layered security practices and staying informed about the latest threats, users can better protect their digital assets in an increasingly digital and interconnected world.
The Trezor Hack: Lessons for Cryptocurrency Community
The recent Trezor hack has highlighted the vulnerabilities that can exist within the cryptocurrency community, particularly when it comes to hardware wallets. This incident serves as a wake-up call for both individuals and businesses involved in cryptocurrencies, emphasizing the importance of robust security measures and constant vigilance.
The Importance of Protecting Private Keys
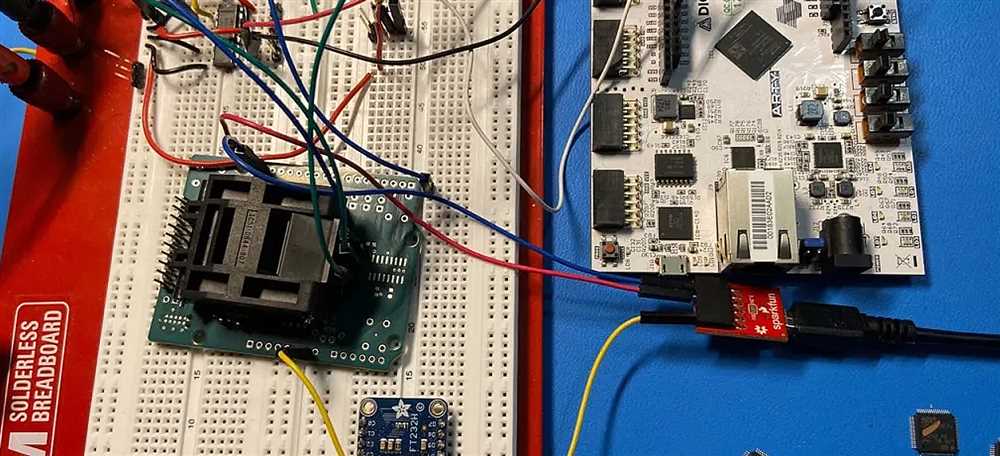
One of the key lessons from the Trezor hack is the criticality of safeguarding private keys. In this attack, the hacker was able to gain unauthorized access to the victim’s private key, enabling them to steal their cryptocurrency funds. This serves as a reminder to cryptocurrency holders of the need to properly manage and protect their private keys.
When using a hardware wallet like Trezor, it is crucial to securely store the recovery seed phrase, which is used to restore access to funds in case of loss or theft. Keeping this seed phrase in a safe and offline location is essential, as it prevents potential hackers from gaining access to it remotely.
The Risks of Phishing Attacks

The Trezor hack also highlighted the risks posed by phishing attacks. The attacker in this case was able to trick the victim into downloading a malicious firmware update, which ultimately led to the compromise of their private key. This underscores the importance of being vigilant and verifying the authenticity of firmware updates or any other requests for sensitive information.
It is advisable to always download firmware updates directly from the official manufacturer’s website and to never click on any suspicious links or provide sensitive information unless you are certain of their legitimacy.
Remember, cryptocurrency transactions are irreversible, so taking steps to prevent phishing attacks is crucial in protecting your funds.
Conclusion
The Trezor hack serves as a reminder for the cryptocurrency community to prioritize security and take necessary precautions to protect their funds. Safeguarding private keys, being cautious of phishing attacks, and staying updated with the latest security measures are essential for mitigating risks in the crypto space. By learning from this incident, individuals and businesses can strengthen their defenses and ensure the safety of their cryptocurrency assets.
Trezor Hardware Wallet: Secure but Vulnerable

The Trezor hardware wallet has long been regarded as one of the most secure options for storing cryptocurrencies. Its offline cold storage and robust encryption have made it a popular choice among investors and enthusiasts alike.
However, a recent hack has shed light on potential vulnerabilities in the Trezor wallet. While the breach required physical access to the device, it serves as a reminder that even the most secure solutions are not completely immune to risks.
One key takeaway from this incident is the importance of securing physical access to your wallet. In this case, the hacker was able to gain access to the device and exploit a vulnerability in the firmware. This highlights the need for users to keep their wallets in a secure location and take precautions to prevent unauthorized access.
Additionally, the hack underscores the need for regular firmware updates. Trezor has since released an update addressing the vulnerability used in the attack. By regularly updating your wallet’s firmware, you can ensure that you are protected against the latest threats.
It’s important to note that the Trezor hardware wallet is still considered one of the most secure options available. The hack was a result of a highly targeted attack that required physical access to the device. With proper security measures and vigilance, Trezor users can continue to have confidence in the security of their funds.
In conclusion, the recent hack of the Trezor hardware wallet serves as a reminder of the importance of physical security and regular firmware updates. While no system can ever be 100% secure, taking these precautions can help mitigate the risks associated with storing cryptocurrencies.
Key Takeaways for Cryptocurrency Holders

As a cryptocurrency holder, there are several key takeaways from the Trezor hack that you should be aware of:
| 1. Use Hardware Wallets | Hardware wallets, like the Trezor device, offer an added layer of security by storing your private keys offline. This significantly reduces the risk of your funds being compromised by hackers. |
| 2. Keep Firmware Updated | Regularly updating your hardware wallet’s firmware is crucial to protect against potential vulnerabilities. Manufacturers often release updates to fix bugs and enhance security, so make sure to stay up to date. |
| 3. Enable Additional Security Features | Most hardware wallets provide additional security features, such as multi-factor authentication or passphrase protection. Enable these features to further safeguard your cryptocurrencies. |
| 4. Use Strong Passwords | When creating accounts or setting passwords for your wallets and exchanges, ensure you use strong, unique passwords that are not easily guessable. Consider using a password manager to help you generate and store complex passwords securely. |
| 5. Be Wary of Phishing Attempts | Beware of phishing attempts, where scammers impersonate legitimate websites or services to steal your login credentials. Always double-check the URL and verify the authenticity of the website before entering any sensitive information. |
| 6. Backup Your Wallet | Regularly backup your wallet’s recovery seed or private keys and store them in a secure location offline. This ensures that you can still access your funds in case of loss, damage, or theft of your hardware wallet. |
| 7. Diversify Your Holdings | Spreading your cryptocurrency holdings across different wallets and exchanges reduces the risk of losing all your funds in case of a security breach. Consider diversifying your holdings to minimize your exposure. |
| 8. Stay Informed | Keep yourself updated on the latest security practices and news in the cryptocurrency community. Follow reputable sources, join online forums or groups, and participate in discussions to stay informed and learn from other holders’ experiences. |
By following these key takeaways, you can better protect your cryptocurrencies and minimize the risk of falling victim to hacks or security breaches.
Steps to Enhance Security

After understanding the vulnerabilities exposed in the Trezor hack, it is crucial for the cryptocurrency community to take proactive steps to enhance security. Here are some recommended measures:
1. Keep software up to date: Regularly update your hardware wallet’s firmware and software to ensure you have the latest security patches and bug fixes. Manufacturers often release updates to address vulnerabilities.
2. Enable two-factor authentication (2FA): Activate 2FA on your hardware wallet and any associated accounts or platforms. This adds an extra layer of security by requiring a second verification step, such as a unique code or biometric authentication.
3. Use strong, unique passwords: Avoid using the same password for multiple accounts as it increases your vulnerability to hacking. Utilize a password manager to generate and store complex passwords securely.
4. Implement multi-signature wallets: Consider utilizing multi-signature wallets, which require multiple private keys to access funds. This provides an additional layer of protection against unauthorized access.
5. Be cautious of phishing attempts: Always verify the authenticity of any communication or website before entering sensitive information. Phishing attacks are a common method of obtaining access to private keys and passwords.
6. Store backups securely: Maintain offline backups of your cryptocurrency wallets and store them in secure locations. This protects against physical theft, damage, or data loss due to hardware failures.
7. Educate yourself: Stay informed about the latest security best practices and emerging vulnerabilities in the cryptocurrency space. Regularly research and educate yourself to minimize risks and stay ahead of potential threats.
8. Consider using a hardware wallet: Hardware wallets, such as Trezor, are designed specifically for securely storing cryptocurrency. Consider using one to provide an extra layer of security compared to software or online wallets.
9. Be mindful of physical security: Protect your hardware wallet from theft or loss by keeping it in a secure location. Avoid using public Wi-Fi networks or computers when accessing or managing cryptocurrency assets.
10. Regularly review transactions: Periodically review your transaction history to identify any unauthorized or suspicious activity. Promptly report any discrepancies or concerns to your wallet provider or relevant authorities.
By following these steps, users can enhance the security of their cryptocurrency assets and reduce the risk of falling victim to hacking or fraud. It is crucial to prioritize security measures and remain vigilant in the ever-evolving landscape of digital assets.
Future of Hardware Wallets

The Trezor hack has highlighted the vulnerabilities of hardware wallets and raised questions about their future. While hardware wallets have generally been considered one of the safest ways to store cryptocurrencies, this incident has shown that they are not immune to attacks.
However, this doesn’t mean the end of hardware wallets. Rather, it underscores the need for continuous improvement and innovation. Developers and manufacturers need to learn from this incident and take steps to make hardware wallets even more secure.
One possible avenue for improvement is the integration of additional security features. This could involve incorporating biometric authentication, such as fingerprint scanning or facial recognition, to enhance the device’s security. Furthermore, there may be room for advancements in encryption algorithms and secure elements to further protect the private keys stored within the hardware wallet.
Another area for development is user education. Many users may not fully understand the importance of securely storing their private keys or may not be aware of potential attack vectors. Hardware wallet manufacturers should invest in educating users on best practices for using and securing their devices, as well as raising awareness about potential risks.
Additionally, collaborations and standards across the industry could play a vital role in improving the security of hardware wallets. By sharing knowledge and best practices, developers and manufacturers can work together to establish common standards for security and develop guidelines for auditing and testing the devices.
Looking further ahead, advancements in technology such as quantum computing may pose new challenges for hardware wallets. As quantum computers become more powerful, they may be able to break the encryption algorithms used in existing hardware wallets. In response, hardware wallet developers will need to embrace quantum-resistant algorithms and update their devices accordingly.
Overall, while the Trezor hack serves as a wake-up call for the cryptocurrency community, it also presents an opportunity for growth and improvement. By embracing innovation, education, collaboration, and adapting to emerging technologies, the future of hardware wallets can be made even more secure.
Q&A:
What is the Trezor hack?
The Trezor hack refers to a security breach that occurred with the Trezor hardware wallet, a popular device used for storing cryptocurrency. Hackers were able to exploit a vulnerability in the device and gain access to users’ private keys, allowing them to steal their funds.
How did the hackers gain access to the Trezor wallets?
The hackers exploited a vulnerability in the Trezor hardware wallet. They were able to extract the private keys from the device by physically tampering with it. This allowed them to gain full control over the users’ cryptocurrencies.
What can be done to protect against this type of hack?
To protect against this type of hack, it is important to always use the latest firmware version of the Trezor hardware wallet. Additionally, users should ensure that their devices are purchased directly from the official Trezor website or trusted retailers to avoid the risk of tampered devices. It is also recommended to enable the passphrase feature and use a strong, unique passphrase for added security.
Was the stolen cryptocurrency ever recovered?
No, the stolen cryptocurrency was not recovered. Once the hackers gained access to the private keys, they were able to transfer the funds to their own wallets. Cryptocurrency transactions are typically irreversible, so once the funds are stolen, it is very difficult to recover them.
What lessons can the cryptocurrency community learn from the Trezor hack?
The Trezor hack serves as a reminder of the importance of securing cryptocurrencies. It highlights the need for users to carefully research and choose secure hardware wallets, keep their firmware up to date, and enable additional security measures such as a passphrase. Users should also be cautious of purchasing devices from third-party sellers or using tampered devices, as this can put their funds at risk.


