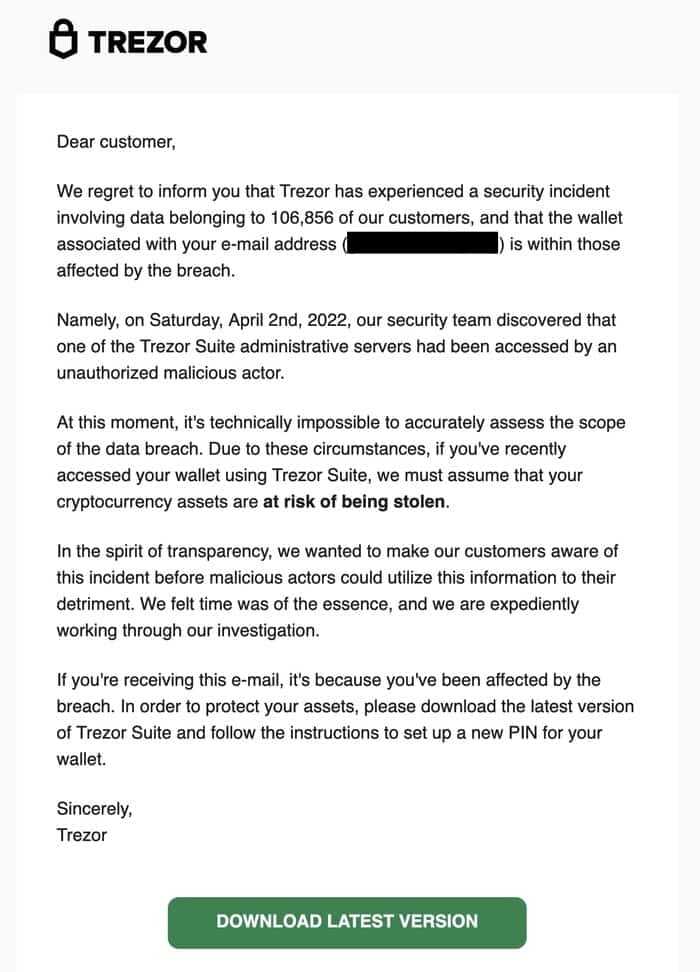
The Trezor Hack aftermath: essential information for users

In today’s digital age, securing your cryptocurrency investments is of utmost importance. However, recent events have sent shockwaves through the crypto community, highlighting the vulnerabilities that even the most popular hardware wallets can possess. The Trezor hack has left many users worried about the safety of their funds and seeking answers.
For those unfamiliar with the situation, Trezor is a well-known brand of hardware wallets that allows users to securely store their cryptocurrencies offline. It is regarded as one of the most secure methods of safeguarding digital assets. However, a recent hacking incident has raised concerns and underscored the need for enhanced security measures.
The hack involved a sophisticated attack on Trezor’s hardware wallet, which allowed the hackers to gain access to users’ private keys. This meant that they could potentially gain control over the funds stored in the wallets. While Trezor has taken steps to address the issue and reassure users, it is important for all Trezor owners to be aware of the implications and take necessary precautions.
First and foremost, if you are a Trezor user, it is crucial to update your firmware to the latest version available. The company has released a security update that patches the vulnerability exploited by the hackers. By installing this update, you can significantly reduce the risk of falling victim to a similar attack in the future. Remember to download the firmware directly from the official Trezor website to avoid any potential malware.
Additionally, it is recommended to enable two-factor authentication (2FA) for your Trezor wallet. This adds an extra layer of security by requiring you to provide a second form of verification, such as a code sent to your mobile device, in order to access your funds. This can help prevent unauthorized access even if your private keys are compromised.
In conclusion, the Trezor hack serves as a wake-up call for all cryptocurrency investors to prioritize their security practices. By staying informed, keeping your hardware wallet updated, and implementing additional security measures, you can mitigate the risk of falling victim to such attacks. Remember, your digital assets are valuable and protecting them should always be a top priority.
The Trezor Hack Aftermath
The recent hack of the Trezor hardware wallet has raised concerns among users regarding the security of their funds. While Trezor has taken immediate action to address the issue and enhance the security measures, it is crucial for users to take certain precautions to protect their assets.
Here are some essential steps to follow after the Trezor hack:
- Update your firmware: Trezor has released an updated firmware that includes additional security improvements. Make sure to install the latest version to benefit from these enhancements.
- Change your recovery seed: If you suspect that your recovery seed may have been compromised, it is advisable to generate a new one. This can be done through the Trezor wallet interface.
- Enable passphrase protection: Consider enabling passphrase protection for an extra layer of security. This feature allows you to add an additional passphrase to your recovery seed, making it more difficult for attackers to gain access to your funds.
- Keep your device offline: Whenever possible, keep your Trezor wallet offline to minimize the risk of remote attacks. Only connect it to your computer when necessary for transactions.
- Monitor your accounts: Regularly check your wallet and associated accounts for any suspicious activity. Report any unauthorized transactions or signs of tampering to Trezor support immediately.
- Stay informed: Keep yourself updated on the latest news and developments regarding the Trezor hack. Follow official communication channels of Trezor for accurate information.
Remember, while the Trezor hack was a concerning incident, taking appropriate measures can help safeguard your assets. By staying vigilant and following the recommended steps, you can continue to enjoy the benefits of using a hardware wallet with peace of mind.
What Happened: A Summary of the Trezor Hack

In the aftermath of the Trezor hack, it is vital for users to understand what actually occurred and the potential risks involved. Here is a summary of what happened:
1. Exploit Utilized
The hacker exploited a vulnerability in the Trezor firmware, allowing them to gain unauthorized access to the device and its contents. This vulnerability allowed them to extract private keys and steal cryptocurrency stored on the device.
2. Attack Method
The hacker utilized a phishing attack, tricking users into installing a malicious firmware update. Once the update was installed, the attacker had control over the user’s Trezor device, enabling them to steal funds.
3. Nature of the Attack
This attack targeted specific individuals rather than being a widespread attack on all Trezor users. It required the hacker to have physical access to the device or the ability to manipulate the firmware update process.
4. Response from Trezor
Trezor has taken immediate action to address the vulnerability and protect their users. They have released a firmware update that fixes the exploit and have provided instructions on how to install it securely.
5. Importance of Protecting Private Keys
This hack highlights the importance of protecting private keys and following best practices for securely storing cryptocurrency. Users should always verify the authenticity of firmware updates and never install them from untrusted sources.
By understanding what happened during the Trezor hack, users can take the necessary steps to protect their funds and prevent similar incidents in the future.
Protecting Your Assets: Essential Tips for Trezor Users
When it comes to securing your cryptocurrency assets, taking the necessary precautions is essential. As a Trezor user, you already have a hardware wallet that provides an added layer of security. However, it’s crucial to follow these additional tips to protect your assets:
1. Keep your recovery seed offline: Your recovery seed is the key to accessing your funds. Make sure to store it safely offline, preferably on a piece of paper or on a hardware device designed for this purpose. Never store it digitally or share it with anyone.
2. Enable passphrase protection: Adding a passphrase to your Trezor device can provide an extra layer of security. This adds an additional phrase to your recovery seed, making it even harder for potential attackers to gain access to your funds. Remember, if you forget your passphrase, your funds may become inaccessible.
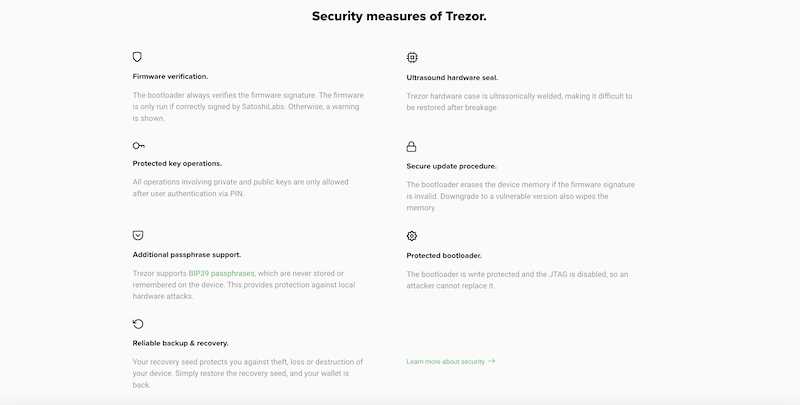
3. Keep your firmware up to date: Trezor regularly releases firmware updates to address any potential security vulnerabilities. Make sure to regularly update your device’s firmware to benefit from the latest security enhancements.
4. Verify SSL certificate: When interacting with the Trezor website or any related application, always ensure that the SSL certificate is valid. This helps protect you from phishing attacks and ensures that you’re communicating securely with Trezor’s official servers.
5. Be cautious of phishing attempts: Exercise caution when clicking on links or entering your sensitive information online. Always double-check the URL, look for secure connections (HTTPS), and avoid sharing your recovery seed or private keys with anyone. Trezor will never ask you for this information.
6. Use a strong and unique PIN: Your Trezor device requires a PIN for access. Make sure to use a PIN that is difficult to guess and avoid using common patterns or sequences. Additionally, use a unique PIN for your Trezor device and avoid reusing it for other accounts.
7. Backup your wallet regularly: Regularly backup your wallet by exporting your public addresses and private keys. Store this information securely offline and exercise caution when importing your wallet into other services.
8. Keep your device physically secure: Treat your Trezor device like you would treat cash or any valuable item. Keep it in a safe place and avoid leaving it unattended in public areas. This reduces the risk of physical theft or tampering.
By following these essential tips, you can enhance the security of your Trezor device and protect your valuable cryptocurrency assets from potential threats.
What Now: Recovery and Future Security Measures
After the Trezor hack, it is crucial for users to take immediate action to protect their assets and ensure their future security. Here are the steps you should take:
1. Change Your Passwords
The first step is to change your passwords for all your online accounts, including your email, cryptocurrency exchanges, and any other platforms you use. Make sure to create strong, unique passwords that are not easily guessable. Consider using a password manager to securely store and generate passwords.
2. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security to your accounts. Enable 2FA wherever possible and use an authenticator app, such as Google Authenticator, instead of SMS-based verification. This will protect your accounts even if your phone number gets compromised.
3. Check for Suspicious Activity

Regularly monitor your accounts for any suspicious activity. Look for any unauthorized transactions, changes in settings, or unfamiliar devices connected to your accounts. If you notice anything suspicious, report it to the platform immediately and take appropriate action to secure your accounts.
4. Consider Hardware Wallets
A hardware wallet is a physical device that securely stores your cryptocurrency private keys offline. Consider investing in a reputable hardware wallet, such as Trezor or Ledger, to enhance the security of your assets. These wallets provide an extra layer of protection by keeping your private keys offline and away from potential hackers.
5. Educate Yourself on Phishing and Social Engineering

Phishing and social engineering are common tactics used by hackers to trick users into revealing their sensitive information. Educate yourself on how to identify and avoid these scams. Be cautious of any unsolicited emails, messages, or calls asking for your personal or financial information.
6. Stay Informed about Security Updates
Keep yourself updated about the latest security measures and patches released by the platform or service you use. Follow official announcements, subscribe to security newsletters, and regularly visit reputable sources for information related to cryptocurrency security. Ensure you are running the latest firmware and software versions on your devices.
By taking these recovery and future security measures, you can minimize the risk of falling victim to hacks and protect your cryptocurrency assets. Stay proactive and vigilant to ensure the safety of your funds.
Q&A:
What is the Trezor hack?
The Trezor hack refers to the unauthorized access and theft of funds from the Trezor hardware wallet. In this incident, hackers exploited a vulnerability in the wallet’s firmware to gain access to the private keys stored on the device, allowing them to steal the funds.
How did the Trezor hack affect users?
The Trezor hack had a significant impact on users who stored their funds on the hardware wallet. Those affected by the hack had their funds stolen by the hackers, resulting in financial losses. It also highlighted the importance of keeping hardware wallets and their firmware up to date to minimize the risk of similar attacks.


