
The Trezor hack – a wake up call for the cryptocurrency industry

In the ever-evolving landscape of the cryptocurrency industry, security is a constant concern. With millions of dollars worth of digital assets at stake, it is crucial for companies and individuals to take every precaution to protect their investments. However, a recent hack has highlighted the vulnerabilities that still exist in the industry.
The Trezor hack, which occurred in the past month, sent shockwaves through the cryptocurrency community. Trezor, a popular hardware wallet company, specializes in providing secure storage solutions for cryptocurrencies. However, hackers were able to exploit a vulnerability in the wallet’s firmware, gaining access to users’ private keys and stealing their funds.
This incident serves as a wake-up call for the entire cryptocurrency industry. It demonstrates that even the most supposedly secure storage solutions are not immune to attacks. It exposes the need for companies to invest heavily in improving their security measures and for individuals to remain vigilant in protecting their digital assets.
Understanding the Trezor Hack

The Trezor hack served as a wake-up call for the cryptocurrency industry, highlighting the potential vulnerabilities in hardware wallets. Understanding the nature of the hack and its implications is crucial for both investors and developers in the crypto space.
What is Trezor?
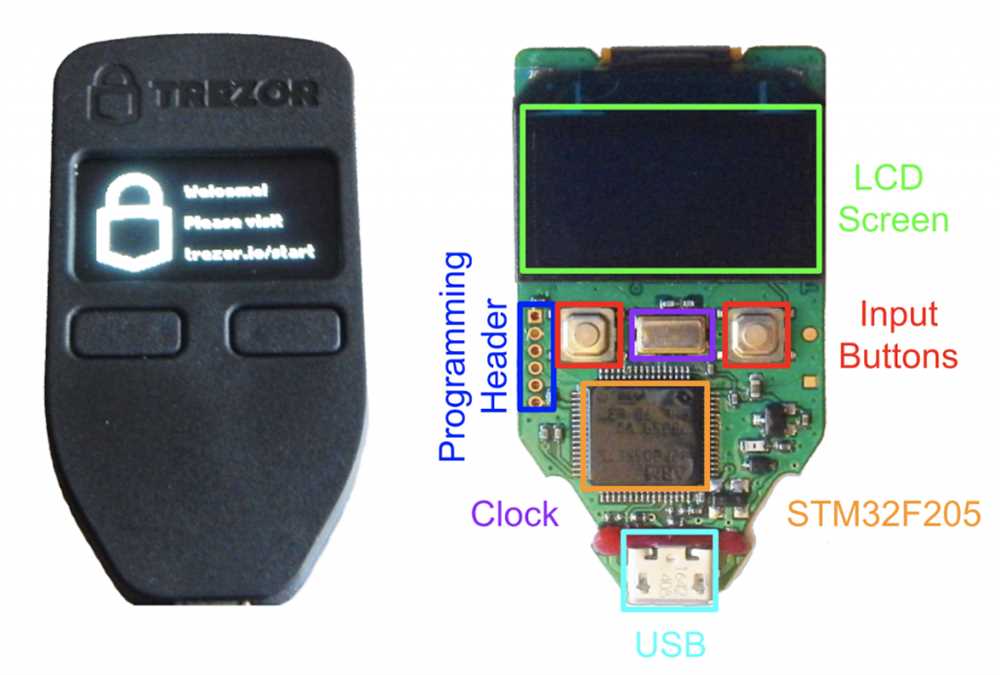
Trezor is a popular hardware wallet used for securing cryptocurrencies. It is designed to store private keys offline, making it less susceptible to hacking compared to online wallets. However, the hack exposed certain vulnerabilities that were previously unknown.
The Hack

In the Trezor hack, the attacker relied on a technique called “side-channel attack.” This involves analyzing the physical traces of the device and using the information gained to deduce the device’s private key. The attacker gained physical access to the device and used specialized equipment to perform the attack.
One of the reasons the hack was successful was due to a vulnerability in the implementation of the firmware on the Trezor device. This allowed the attacker to exploit a weakness and extract the private key from the device.
Implications for the Crypto Industry

The Trezor hack highlighted the need for greater security measures in the hardware wallet industry. While hardware wallets are generally considered more secure than other forms of wallet storage, this incident showed that they are not foolproof and can be compromised under certain circumstances.
Developers in the cryptocurrency industry should learn from this hack and work towards strengthening the security of hardware wallets. This includes regular firmware updates, rigorous security audits, and implementing additional layers of encryption.
Investors, on the other hand, should be aware of the risks associated with hardware wallets and take necessary precautions. This includes choosing reputable hardware wallet providers, keeping firmware up to date, and following best practices for secure storage of private keys.
The Trezor hack serves as a reminder that the crypto industry is still evolving and faces ongoing challenges in terms of security. By understanding the nature of hacks like these, the industry can take steps to improve and provide better protection for investors and their assets.
Implications for the Cryptocurrency Industry

The Trezor hack serves as a wake-up call for the cryptocurrency industry, highlighting the vulnerabilities and risks associated with storing digital assets. This incident raises several important implications for both individual investors and the industry as a whole.
Firstly, the hack underscores the need for improved security measures in the storage and management of cryptocurrencies. While hardware wallets like Trezor are generally considered to be among the most secure options available, this incident demonstrates that no storage method is completely immune to attacks. It is crucial for individuals and businesses to continuously update their security protocols and stay vigilant against emerging threats.
Secondly, the Trezor hack highlights the importance of education and awareness in the cryptocurrency industry. Many users may not be fully aware of the potential risks and security best practices associated with storing cryptocurrencies. This incident should encourage individuals to educate themselves about the various security measures available and make informed decisions about the storage of their digital assets.
Furthermore, this hack could lead to increased regulation and oversight in the cryptocurrency industry. As incidents like this one continue to occur, regulators and policymakers may feel compelled to implement stricter regulations to protect investors and prevent future hacks. This could potentially impact the way exchanges, wallets, and other cryptocurrency-related entities operate in the future.
Additionally, the hack raises questions about the overall trustworthiness and reliability of cryptocurrency hardware wallets. As more individuals and institutions enter the cryptocurrency market, it is important for them to have confidence in the security measures implemented by companies offering storage solutions. The Trezor hack could lead to a decline in trust and increased scrutiny of hardware wallet providers, potentially impacting the overall adoption of cryptocurrencies.
Lastly, the incident serves as a reminder of the potential financial losses associated with storing cryptocurrencies. While the decentralized nature of cryptocurrencies is one of their key features, it also means that individuals are solely responsible for their own security. The Trezor hack should serve as a wake-up call for individuals to take personal responsibility for the security of their digital assets and exercise caution when managing their cryptocurrencies.
In conclusion, the Trezor hack has significant implications for the cryptocurrency industry. It highlights the need for improved security measures, increased education and awareness, potential regulatory changes, and the importance of personal responsibility. The industry must learn from this incident and work together to strengthen security protocols and ensure the long-term trust and viability of cryptocurrencies.
Enhancing Security Measures

The Trezor hack serves as a wake-up call for the entire cryptocurrency industry, highlighting the urgent need for enhanced security measures. While the incident was alarming, it presents an opportunity for the industry to learn and improve, ensuring that such hacks do not happen again.
1. Multi-factor authentication: One of the most effective ways to enhance security is by implementing multi-factor authentication. This involves requiring users to provide two or more pieces of evidence to verify their identity, such as a password and a fingerprint or a one-time code sent to their phone.
2. Hardware wallet improvements: The Trezor hack highlighted vulnerabilities in hardware wallets, which are meant to be one of the most secure ways to store cryptocurrencies. As a result, manufacturers should invest in regular security audits, thorough testing, and constant updates to address any identified weaknesses and provide users with the highest level of protection.
3. Education and awareness: Users need to be educated about the risks and best security practices when it comes to cryptocurrency storage. Many individuals new to the industry may not be aware of the various threats they face and the necessary precautions they can take. By providing comprehensive educational materials and raising awareness, the industry can empower users to protect their assets.
4. Collaboration and information sharing: The Trezor hack serves as a reminder that security is a collective effort. Industry players should collaborate and share information about potential threats and vulnerabilities. By working together, they can pool resources and expertise to develop stronger security measures and respond effectively to any emerging risks.
5. Regular software updates: Just as hardware wallets should be regularly updated, so should any software used in cryptocurrency transactions or storage. Developers should adopt agile methodologies, allowing them to quickly address any security vulnerabilities that are discovered and release regular updates to users.
6. Security audits: Regular security audits should be conducted by independent third-party firms to identify any weaknesses or potential vulnerabilities in cryptocurrency platforms, wallets, and exchanges. These audits should be thorough and comprehensive to ensure that all security measures are up to date and effective.
7. Continuous monitoring: Implementing continuous monitoring and robust intrusion detection systems can help detect and prevent security breaches in real-time. By regularly monitoring network traffic and system logs, any suspicious activities or unauthorized access attempts can be identified and stopped promptly.
In conclusion, the Trezor hack has highlighted the need for the cryptocurrency industry to enhance its security measures. By implementing multi-factor authentication, improving hardware wallets, providing education and awareness, promoting collaboration, regularly updating software, conducting security audits, and implementing continuous monitoring, the industry can better protect itself and its users from potential threats.
Q&A:
What is the Trezor Hack?
The Trezor Hack refers to a security vulnerability that was discovered in the Trezor hardware cryptocurrency wallet. This vulnerability allowed potential attackers to extract the private keys from the device, potentially giving them access to the funds stored in the wallet.
How was the Trezor Hack discovered?
The Trezor Hack was discovered by a team of security researchers who were conducting a thorough analysis of the device’s security measures. They identified a weakness in the random number generation process, which allowed them to retrieve the private keys stored on the device.


