
The Latest Security Features of Trezor.com and How They Protect Your Crypto

Introducing the most advanced and secure way to protect your crypto assets – Trezor.com. Our cutting-edge hardware wallet is designed to provide you with the utmost security and peace of mind.
With the increasing prevalence of cyber attacks and hacking incidents, it has become more crucial than ever to safeguard your digital currencies. At Trezor.com, we understand the importance of ensuring the safety of your crypto investments.
Here are just a few of the latest security features that set Trezor.com apart:
- State-of-the-art Encryption: We employ the most advanced encryption algorithms to protect your private keys and ensure that your transactions remain secure.
- Multi-factor Authentication: Trezor.com offers a multi-factor authentication system that adds an extra layer of protection to your account. With this feature enabled, you can rest assured that only authorized individuals will have access to your funds.
- Offline Storage: Unlike online wallets, Trezor.com stores your private keys offline, making it virtually immune to hacker attacks and online threats. Your sensitive information is kept physically disconnected from the internet at all times.
- Pin-Protected Access: To access your funds, you’ll need to enter a unique PIN code on your Trezor device. This additional layer of security ensures that only you can authorize transactions and access your crypto assets.
Invest with confidence and protect your digital wealth with Trezor.com. Our top-notch security features are designed to give you peace of mind and keep your crypto assets safe from unauthorized access.
Don’t compromise on security – choose Trezor.com and safeguard your investments today!
The Latest Security Features of Trezor.com

Trezor.com takes the security of your cryptocurrency seriously. With the latest advancements in technology and encryption, we are constantly updating and improving our security features to ensure the safety and protection of your digital assets.
One of the key security features of Trezor.com is our multi-factor authentication. When you log in to your account, you will be required to provide two separate factors of authentication, such as a password and a unique code generated by your Trezor device. This adds an extra layer of security, making it extremely difficult for unauthorized individuals to gain access to your account.
Additionally, Trezor.com utilizes state-of-the-art encryption to protect your private keys and sensitive data. All communication between your device and Trezor.com is encrypted using industry-standard SSL/TLS protocols, ensuring that your information remains secure and cannot be intercepted.
Another important security feature of Trezor.com is our secure recovery process. In the event that your device is lost or stolen, you can easily recover your funds using the recovery seed. This seed is generated when you set up your device and can be used to restore access to your funds on a new device. It is crucial to store this seed in a safe and secure location.
Furthermore, Trezor.com regularly undergoes rigorous security audits to identify and address any potential vulnerabilities. We work closely with top security experts and conduct frequent penetration testing to ensure that our platform remains secure and reliable.
At Trezor.com, we understand that security is paramount when it comes to cryptocurrency. That’s why we are committed to providing you with the latest security features and continually improving our platform to keep your digital assets safe and secure.
Trust Trezor.com with your cryptocurrency and enjoy peace of mind knowing that your funds are protected by the latest security features.
Protecting Your Crypto

At Trezor.com, we understand the importance of protecting your cryptocurrency assets. With the latest security features, we ensure that your crypto is safe and secure.
Advanced Encryption

Our advanced encryption technology keeps your private keys secure. With end-to-end encryption, your crypto transactions are protected from unauthorized access.
Multi-Factor Authentication
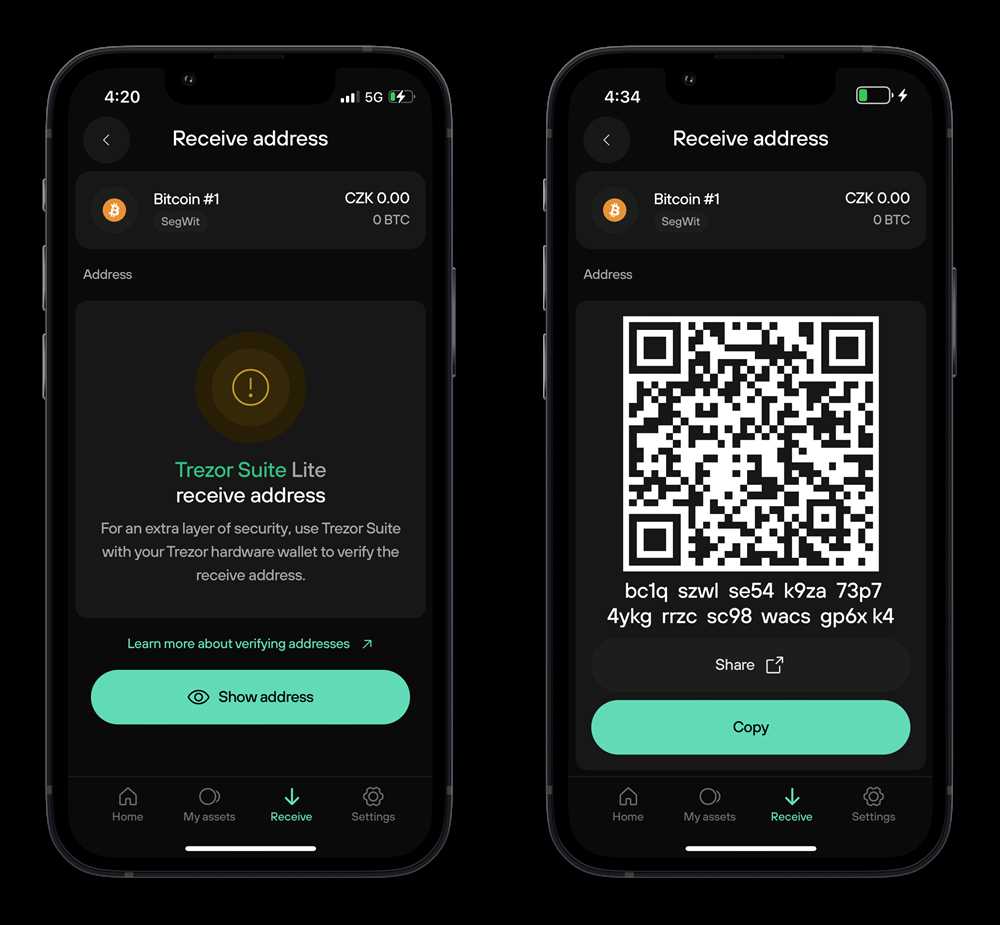
We offer multi-factor authentication options, including biometric authentication and two-factor authentication, to add an extra layer of security to your account. This means that even if someone manages to get hold of your password, they won’t be able to access your crypto without your consent.
With Trezor.com, you can have peace of mind knowing that your crypto assets are well-protected. Don’t compromise on the security of your digital wealth – choose Trezor.com today.
Secure Hardware Wallet

When it comes to protecting your cryptocurrency, nothing is more paramount than having a secure hardware wallet. With the rising number of hacking attempts and data breaches, it is crucial to keep your digital assets safe.
At Trezor.com, we understand the importance of security, which is why we have developed a state-of-the-art hardware wallet that provides the highest level of protection for your crypto. Our secure hardware wallet offers a range of advanced features:
1. Multi-Layered Encryption: Our hardware wallet utilizes multi-layered encryption to ensure that your private keys and sensitive information remain completely secure. With multiple layers of protection, you can have peace of mind knowing that your funds are safe from any unauthorized access.
2. Secure Element Technology: We integrate secure element technology into our hardware wallet, ensuring that your cryptographic operations are performed in a highly secure environment. This technology adds an extra layer of protection by isolating your private keys from potentially vulnerable software and networks.
3. PIN Protection: To further enhance the security of your hardware wallet, we have implemented a PIN protection system. This means that even if your wallet is lost or stolen, no one can access your funds without the correct PIN. With this added layer of security, you can have peace of mind even in the worst-case scenarios.
4. Tamper-Proof Design: Our hardware wallet is designed to be tamper-proof, ensuring that it cannot be physically compromised. With a robust and durable construction, you can trust that your hardware wallet will remain secure, even in the face of attempted tampering.
With our secure hardware wallet, you can confidently store and manage your cryptocurrency without worrying about potential threats. Investing in a high-quality hardware wallet is essential for safeguarding your digital assets and protecting your investment.
Choose Trezor.com and take advantage of our latest security features to protect your crypto today!
Advanced Encryption Technology

At Trezor.com, we understand the importance of protecting your valuable cryptocurrencies. That’s why we have implemented advanced encryption technology to ensure the utmost security for your digital assets.
Our cutting-edge encryption algorithms utilize industry-standard cryptographic techniques, guaranteeing the confidentiality and integrity of your crypto transactions. With our state-of-the-art encryption technology, you can have peace of mind knowing that your funds are safe from unauthorized access.
Secure Key Storage
One of the key aspects of our advanced encryption technology is secure key storage. Your private keys, which are crucial for accessing and managing your crypto assets, are stored securely within the Trezor hardware wallet.
By keeping your private keys offline and inaccessible to the internet, Trezor.com ensures that your keys are protected from potential threats such as hacking attempts and malware attacks. This layer of security minimizes the risk of unauthorized access to your digital assets.
Multi-factor Authentication

In addition to secure key storage, Trezor.com offers multi-factor authentication to add an extra layer of protection to your crypto holdings. By enabling this feature, you will need to provide an additional verification code, generated by your Trezor device, in order to access your wallet and authorize transactions.
With multi-factor authentication, even if someone gains unauthorized access to your password, they will still be unable to access your wallet without the physical Trezor device and the associated verification code. This innovative approach significantly enhances the security of your crypto assets.
| Benefits of Advanced Encryption Technology at Trezor.com: |
|---|
| Ensures the confidentiality and integrity of your crypto transactions |
| Provides secure key storage to protect your private keys from unauthorized access |
| Offers multi-factor authentication for an additional layer of security |
| Eliminates the risk of hacking attempts and malware attacks |
| Enhances the security of your digital assets |
Multi-factor Authentication

At Trezor.com, we understand the importance of strong security measures to protect your cryptocurrency. That’s why we offer multi-factor authentication for added peace of mind.
Multi-factor authentication (MFA) adds an extra layer of security to your account by requiring more than just a password for access. When you enable MFA on your Trezor account, you’ll need to provide a second form of verification, such as a unique code generated by an authentication app on your smartphone.
This additional step ensures that even if your password is compromised, unauthorized individuals won’t be able to access your account without the second factor. With MFA in place, you can rest assured that your cryptocurrencies are safe, even in the event of a data breach or stolen password.
Enabling MFA is quick and easy. Simply go to the security settings in your Trezor account and follow the instructions to set up your preferred method of authentication. We recommend using an authentication app for increased security, but you can also choose to receive codes via SMS or email.
Protect your investment with multi-factor authentication from Trezor.com. Don’t leave your cryptocurrencies vulnerable to hackers. Take the extra step to secure your account and keep your funds safe.
Key Features:
- Added layer of security
- Protection against unauthorized access
- Easy setup and configuration
- Various authentication methods available
- Peace of mind for cryptocurrency holders
Invest in your security and safeguard your cryptocurrencies with the latest multi-factor authentication technology from Trezor.com.
Q&A:
What are the security features of Trezor.com?
Trezor.com has several security features to protect your crypto. It uses a multi-layered approach to secure your private keys and transactions. Some features include secure element chips, passphrase protection, and two-factor authentication.
How does Trezor.com protect my private keys?
Trezor.com uses secure element chips to protect your private keys. These chips are tamper-resistant and provide a secure environment for key management. This helps to prevent unauthorized access to your crypto.
What is passphrase protection and how does it work?
Passphrase protection is an additional layer of security provided by Trezor.com. It allows you to set a unique passphrase that is required to access your crypto. This adds an extra level of protection against unauthorized access, even if your device is lost or stolen.
Does Trezor.com support two-factor authentication?
Yes, Trezor.com supports two-factor authentication. This means that in addition to your password, you will need to provide a second piece of information, such as a verification code sent to your phone, to access your crypto. This helps to prevent unauthorized access to your account even if your password is compromised.


