Responding to the Trezor Data Breach: Can the Stolen Funds be Recovered?

In recent years, cryptocurrency has gained significant popularity as a form of digital currency. With this rise in popularity, the threat of cyber attacks and data breaches targeting cryptocurrency holders has also increased. One of the most notable incidents was the Trezor data breach, where a substantial amount of funds were stolen from unsuspecting users.
Trezor, a leading hardware wallet manufacturer, sells devices designed to securely store cryptocurrencies. However, even with the highest level of security measures, no system is completely immune to attacks. In this particular breach, hackers managed to gain access to users’ private keys, allowing them to steal their funds.
The question that many affected users now ask is: can these stolen funds be recovered? Unfortunately, the answer is not straightforward. Cryptocurrency transactions are designed to be irreversible, providing a level of security that traditional banking systems cannot. Once funds are transferred from one wallet to another, it is challenging to trace and recover them.
However, all hope is not lost. Efforts are being made to track down the stolen funds and prevent further illicit activities. Blockchain analysis companies are working closely with law enforcement agencies to identify suspicious transactions and trace the flow of the stolen funds. These companies use advanced technology and algorithms to analyze the blockchain and detect any patterns or anomalies.
Furthermore, affected users are strongly advised to report the incident to the appropriate authorities. By doing so, they can provide valuable information that may aid in the investigation and potentially lead to the recovery of their stolen funds. It is crucial to work together as a community to combat cybercrime and hold the perpetrators accountable.
In conclusion, the recovery of stolen funds from the Trezor data breach is a complex and challenging process. While the odds may be against affected users, it is essential to remain vigilant and proactive in reporting the incident. With the combined efforts of blockchain analysis companies, law enforcement agencies, and affected users, there is a possibility of recovering at least a portion of the stolen funds and bringing the criminals to justice.
Funds Recovery Options for Victims of the Trezor Data Breach
Dealing with the aftermath of a data breach can be a stressful and overwhelming experience, especially when it involves the loss of funds. If you are a victim of the Trezor data breach and have had funds stolen from your account, it is important to explore all available options for recovering your funds. While there may not be a guaranteed solution, there are a few steps you can take to increase your chances of recovering your stolen funds.
Contact the authorities

The first step in recovering your stolen funds is to report the incident to the appropriate authorities. Contact your local law enforcement agency and provide them with all the relevant details of the data breach and the funds that were stolen. They will be able to guide you through the process of filing a report and may initiate an investigation into the matter.
Seek legal assistance
Once you have reported the data breach to the authorities, it may be beneficial to seek legal assistance. Consult with a lawyer who specializes in cybercrime and cryptocurrency cases. They will be able to advise you on the legal options available to you and help you navigate through the complexities of recovering stolen funds.
It is important to note that the legal process can be lengthy and expensive, and success is not guaranteed. However, having a legal expert by your side can provide you with guidance and support throughout the process.
Explore insurance options
If you had insurance coverage at the time of the Trezor data breach, it is worth exploring whether your policy covers the loss of funds due to a cyber attack. Contact your insurance provider and provide them with all the necessary information regarding the breach. They will be able to guide you through the claim process and determine if you are eligible for compensation.
Engage with the crypto community
Since the Trezor data breach affected a significant number of users, reaching out to the crypto community can be helpful. Participate in online forums, social media groups, and communities dedicated to cryptocurrency and data breaches. Share your experience, seek advice, and learn from others who may have gone through similar situations.
Monitor your accounts
While you explore recovery options, it is important to keep a close eye on your accounts and monitor any suspicious activities. Set up transaction alerts and regularly check your account balances. If you notice any unauthorized transactions or suspicious activities, report them immediately to your financial institution and the relevant authorities.
| Recovery Options | Pros | Cons |
|---|---|---|
| Reporting the incident to authorities | Initiates an investigation into the data breach | Success is not guaranteed |
| Seeking legal assistance | Expert guidance and support | Lengthy and expensive process, success is not guaranteed |
| Checking insurance coverage | Potential for compensation | Not all policies cover cyber attacks |
| Engaging with the crypto community | Shared experiences and advice | No guarantee of recovery |
Recovering stolen funds from a data breach can be a challenging and complex process. It requires a combination of legal action, insurance claims, and community support. While there are no guarantees, exploring these options can help increase your chances of recovering your stolen funds.
Legal Actions and Investigations in the Trezor Data Breach Case
Following the data breach incident at Trezor, where funds were stolen from users’ accounts, several legal actions and investigations have been initiated to apprehend the perpetrators and recover the stolen funds.
The affected users have filed lawsuits against Trezor, seeking compensation for the losses incurred due to the breach. These legal actions aim to hold Trezor accountable for the security vulnerabilities that led to the unauthorized access of user accounts and subsequent theft of funds.
In addition to the civil lawsuits, law enforcement agencies and cybersecurity firms are actively investigating the data breach to identify the individuals responsible for the attack. These investigations involve analyzing the attack vector, tracing the movements of the stolen funds, and gathering evidences to build a case against the perpetrators.
The investigations are further supported by cooperation from other cryptocurrency exchanges, as the stolen funds might have been transferred or used in transactions on these platforms. Through collaboration and information sharing, investigators hope to establish connections and trace the movement of funds across different platforms.
A task force comprising of cybersecurity experts, law enforcement officials, and legal professionals has been formed to coordinate the investigations and streamline the legal actions. This task force focuses on gathering and analyzing evidence, coordinating with international agencies, and ensuring that all necessary steps are taken to recover the stolen funds.
The legal actions and investigations in the Trezor data breach case highlight the seriousness of such incidents and the need for stronger security measures in the cryptocurrency industry. As the case progresses, it is expected that more information will surface, leading to potential arrests and the recovery of the stolen funds.
| Date | Update |
|---|---|
| October 2021 | Lawsuits filed against Trezor by affected users seeking compensation. |
| November 2021 | Law enforcement agencies initiate investigations into the data breach. |
| December 2021 | Task force formed to coordinate investigations and legal actions. |
| January 2022 | Cooperation established with other cryptocurrency exchanges for information sharing. |
The Role of Blockchain Analysis in Recovering Stolen Cryptocurrency
Blockchain analysis plays a crucial role in the recovery of stolen cryptocurrency, especially in cases like the Trezor data breach. When funds are stolen from a breach, they are typically moved to multiple addresses and sometimes mixed with other funds to obfuscate their origin. Here’s how blockchain analysis can aid in recovering stolen cryptocurrency:
1. Tracking Transactions
Blockchain analysis allows investigators to track the movement of stolen funds through the transparent nature of blockchain technology. By analyzing transaction records, they can identify addresses associated with the stolen funds and trace their movement across the blockchain.
2. Identifying Addresses and Entities

With the help of blockchain analysis, it becomes possible to identify addresses and entities that are linked to the stolen funds. Investigators can explore the blockchain data to gather information about the owners of these addresses, exchanges involved in the transactions, and other relevant entities tied to the stolen funds.
3. Uncovering Patterns and Behaviors
By analyzing the blockchain data, investigators can often uncover patterns and behaviors that can help identify the culprits behind the theft. They may discover common addresses used by the attackers, similar transaction patterns, or other indicators that can be used to narrow down the search for the thieves.
4. Coordinating with Exchanges and Service Providers
Blockchain analysis firms often work closely with exchanges and service providers to trace stolen funds. By sharing information about suspicious addresses, they can help prevent the thieves from cashing out or using the stolen funds on reputable platforms.
5. Building a Case for Legal Action
Blockchain analysis can provide valuable evidence for legal cases involving stolen cryptocurrency. By analyzing transaction records and identifying the involved entities, investigators can gather the necessary evidence to support legal action against the attackers and facilitate the recovery of stolen funds.
In conclusion, the role of blockchain analysis in recovering stolen cryptocurrency cannot be underestimated. It enables investigators to track transactions, identify addresses and entities, uncover patterns and behaviors, coordinate with exchanges and service providers, and build a strong case for legal action. This analysis is crucial in the aftermath of breaches like the Trezor data breach, where quick action and cooperation between various entities can help recover the stolen funds and bring the culprits to justice.
Steps to Secure Your Cryptocurrency Assets and Prevent Theft

With the increasing popularity and value of cryptocurrencies, it is crucial to take steps to secure your cryptocurrency assets and prevent theft. Here are some important measures to consider:
| 1. Use a Hardware Wallet: | A hardware wallet, such as Trezor, is one of the most secure ways to store your cryptocurrency. It keeps your private keys offline, reducing the risk of hacking or online theft. |
| 2. Enable Two-Factor Authentication (2FA): | Enable two-factor authentication for all your cryptocurrency accounts. This adds an extra layer of security by requiring a second verification step, usually a code sent to your phone, when logging in. |
| 3. Use Strong and Unique Passwords: | Create strong and unique passwords for your cryptocurrency accounts. Avoid using easily guessable passwords and consider using a password manager to securely store them. |
| 4. Keep Software Updated: | Regularly update the software on your devices, including your operating system and cryptocurrency wallets. Software updates often include important security patches that can protect against vulnerabilities. |
| 5. Be Cautious of Phishing Attempts: | Be vigilant of phishing attempts, where scammers impersonate legitimate websites or contacts to trick you into revealing your private keys or passwords. Always double-check URLs, email addresses, and messages for authenticity. |
| 6. Backup Your Wallet: | Regularly backup your cryptocurrency wallet and store the backup offline, preferably in a safe or secure location. This ensures that you can recover your funds in case of loss, theft, or damage to your device. |
| 7. Keep Personal Information Private: | Avoid sharing personal information related to your cryptocurrency holdings, such as your wallet addresses or transaction details, publicly or with unknown parties. This reduces the risk of targeted attacks. |
| 8. Educate Yourself: | Stay informed about the latest security practices and threats in the cryptocurrency space. Educate yourself on topics such as wallet security, phishing scams, and best practices for securely handling cryptocurrencies. |
| 9. Consider Cold Storage: | Consider using cold storage solutions, such as offline paper wallets or dedicated hardware wallets. These keep your private keys completely offline, minimizing the risk of online hacking or theft. |
| 10. Use Trusted and Secure Exchanges: | When trading or exchanging cryptocurrencies, use reputable and secure exchanges. Research and choose platforms with a strong track record for security and user protection. |
By implementing these steps, you can greatly enhance the security of your cryptocurrency assets and reduce the risk of theft or loss. Remember, being proactive and taking preventive measures is crucial in the world of cryptocurrencies.
Q&A:
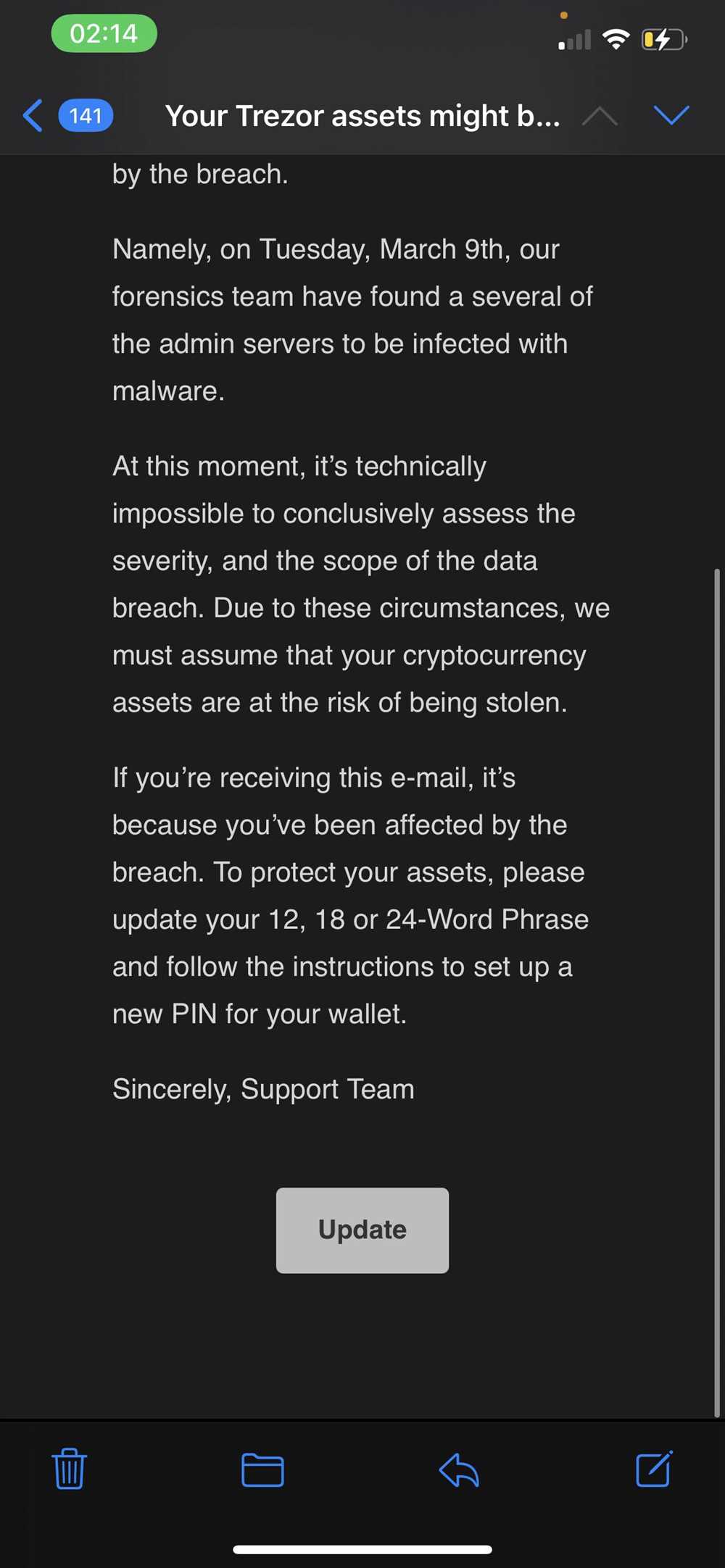
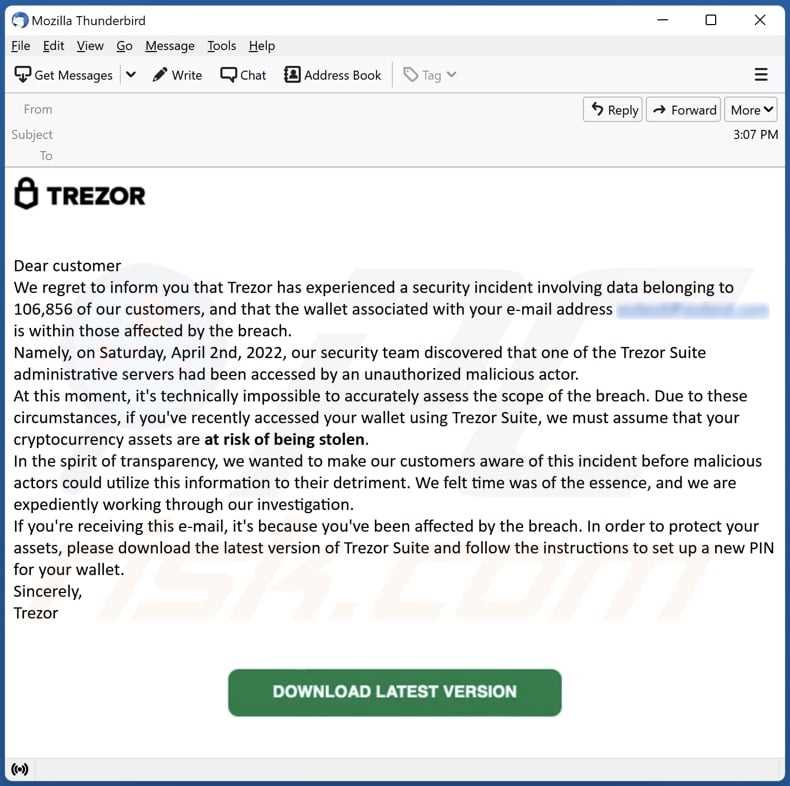
How were the funds stolen in the Trezor data breach?
In the Trezor data breach, the funds were stolen through a phishing attack. Users unknowingly entered their recovery seed phrases on a fake website, allowing the hackers to gain access to their wallets and steal their funds.
Is it possible to trace the stolen funds from the Trezor data breach?
Tracing the stolen funds from the Trezor data breach can be quite challenging. Cryptocurrencies are designed to be decentralized and anonymous, making it difficult to track the flow of funds. However, law enforcement agencies and cybersecurity firms may employ various techniques and technologies to trace the stolen funds.
Can the stolen funds from the Trezor data breach be recovered?
Recovering stolen funds from the Trezor data breach is not guaranteed. Once the funds are transferred to the hacker’s wallet, it becomes challenging to reverse the transactions. However, there have been cases where law enforcement agencies and cybersecurity experts have successfully recovered stolen funds in similar incidents. It depends on various factors, including the cooperation of the authorities and the technical capabilities of the experts involved.


