Protecting Your Trezor.io Login from Phishing Attacks

Are you concerned about the security of your Trezor.io login? Phishing attacks are a common method used by hackers to steal sensitive information, such as login credentials. However, with a few simple tips, you can protect yourself from falling victim to these attacks and ensure the safety of your Trezor.io account.
Tip #1: Verify the Website URL
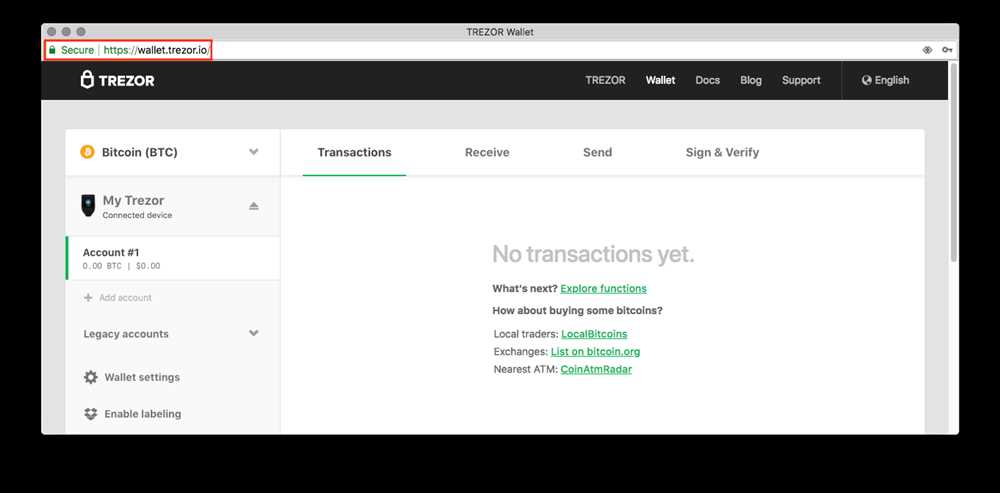
One of the easiest ways to protect yourself from phishing attacks is to always verify the website URL before entering your login credentials. Phishing websites often use URLs that are similar to the legitimate website, but with slight variations. Make sure to double-check the URL and ensure that you are on the official Trezor.io website before logging in.
Tip #2: Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your login process. By enabling 2FA on your Trezor.io account, you will be required to provide an additional verification code, typically sent to your mobile device, in addition to your usual login credentials. This makes it much more difficult for hackers to gain unauthorized access to your account, even if they have obtained your login information through a phishing attack.
Tip #3: Stay Updated on Security Practices
Keeping yourself informed about the latest security practices is crucial in protecting your Trezor.io login from phishing attacks. Subscribe to the Trezor.io newsletter or follow their official social media accounts to stay updated on any security updates or alerts. By staying informed, you can ensure that you are aware of any potential threats and take appropriate measures to secure your account.
Tip #4: Be Cautious of Suspicious Emails and Links
Phishing attacks often rely on sending deceptive emails that appear to be from legitimate sources, such as Trezor.io. These emails may contain links that lead to phishing websites designed to steal your login information. Always be cautious when clicking on links in emails, especially if they ask you to login or provide sensitive information. Instead of clicking on the link, open a new browser window and manually type in the website URL to ensure that you are accessing the legitimate website.
By following these tips, you can greatly reduce the risk of falling victim to phishing attacks and secure your Trezor.io login. Remember, staying vigilant and informed is the key to protecting yourself online.
Protect Your Trezor.io Account from Phishing Attempts

Phishing attempts are a common method used by hackers to gain access to your online accounts and steal your personal information. In order to protect your Trezor.io account from these types of attacks, it is important to follow the tips below:
1. Be cautious of emails or messages asking for your Trezor.io login credentials. Hackers can create fake emails or messages that appear to be from Trezor.io, but are actually designed to steal your information. Always double-check the sender’s email address and be skeptical of any links or attachments they provide.
2. Enable two-factor authentication (2FA) for your Trezor.io account. This adds an extra layer of security by requiring a second form of verification, such as a unique code generated by a separate device, in addition to your username and password.
3. Use a strong, unique password for your Trezor.io account. Avoid using common passwords that are easy to guess, and consider using a password manager to securely store and generate complex passwords.
4. Regularly update your Trezor.io firmware. Trezor.io releases firmware updates to fix security vulnerabilities and improve the overall security of their devices. By keeping your firmware up-to-date, you can ensure that you have the latest security patches.
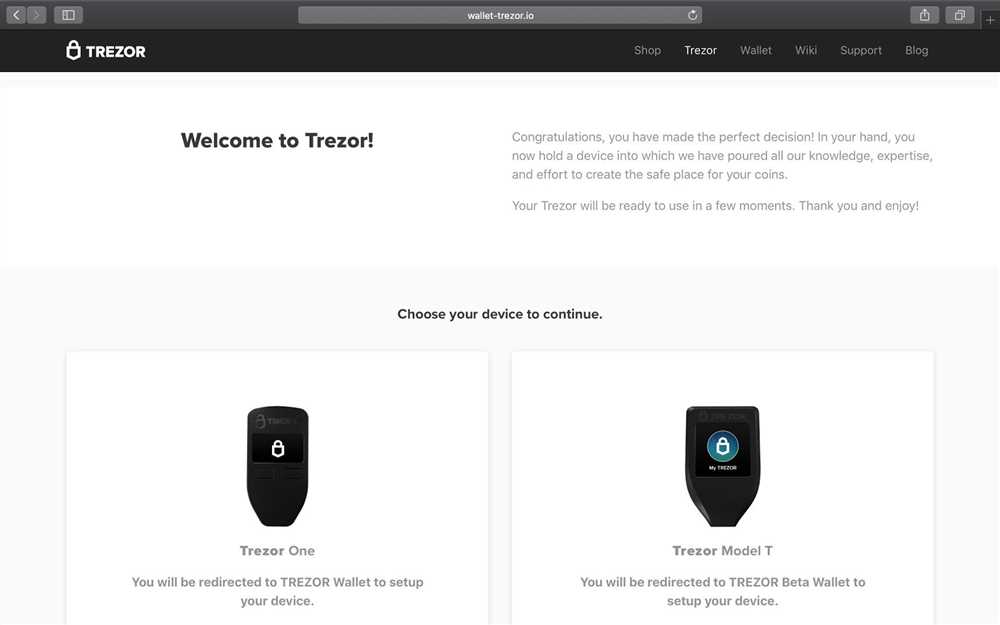
5. Bookmark the official Trezor.io website and only access your account through this bookmark. Avoid clicking on any links or advertisements that claim to take you to Trezor.io, as these could be phishing attempts.
6. Educate yourself about common phishing techniques and be vigilant for any suspicious activity. Watch for signs of phishing, such as misspellings or grammatical errors in emails, requests for personal information, or urgent demands for immediate action.
By following these tips, you can protect your Trezor.io account from phishing attempts and ensure the security of your digital assets.
Strengthen Your Login Security
Protecting your Trezor.io login from phishing attacks is crucial to keeping your funds secure. Here are some tips to strengthen the security of your login:
| 1. Enable Two-Factor Authentication (2FA) | Enable 2FA for your Trezor.io account to add an extra layer of security. This requires you to enter a unique verification code generated by an authentication app on your phone, in addition to your password. |
| 2. Use a Strong, Unique Password | Choose a strong, unique password for your Trezor.io login. Avoid using common words, and include a combination of letters, numbers, and special characters. Also, avoid using the same password for multiple accounts. |
| 3. Double-Check URLs | When logging in to Trezor.io, always double-check the URL to ensure you are on the official website. Phishing attacks often use similar-looking URLs to trick users into entering their login credentials. |
| 4. Be Cautious of Suspicious Emails | Be wary of emails asking for your Trezor.io login credentials or personal information. Legitimate companies will never ask for this information via email. If you receive an email that seems suspicious, contact Trezor.io support directly to verify its legitimacy. |
| 5. Keep Your Device and Software Updated | Regularly update the firmware of your Trezor device, as well as any software or applications associated with your Trezor.io account. Updates often include security patches that protect against potential vulnerabilities. |
| 6. Educate Yourself on Phishing Techniques | Stay informed about the latest phishing techniques used by scammers. Familiarize yourself with common signs of phishing attacks, such as spelling errors, generic greetings, or requests for urgent action. Being able to recognize these signs can help you avoid falling victim to phishing attempts. |
By following these tips, you can significantly enhance the security of your Trezor.io login and reduce the risk of falling victim to phishing attacks. Remember to stay vigilant and prioritize the safety of your funds.
Enable Two-Factor Authentication
One of the most effective ways to secure your Trezor.io login from phishing attacks is to enable two-factor authentication (2FA). Two-factor authentication adds an extra layer of security to your account by requiring a second form of authentication in addition to your password.
When 2FA is enabled, after entering your password, you will be prompted to provide a unique code that is generated by an authenticator app on your smartphone. This code is time-sensitive and changes every few seconds, making it nearly impossible for hackers to guess or capture it.
To enable 2FA on your Trezor.io account, follow these steps:
1. Download an Authenticator App
First, download and install an authenticator app on your smartphone. Popular options include Google Authenticator, Authy, and LastPass Authenticator.
2. Enable 2FA on Trezor.io

Next, log in to your Trezor.io account and navigate to the security settings. Look for the option to enable two-factor authentication and follow the instructions provided. You will typically need to scan a QR code with your authenticator app to link it to your account.
Once 2FA is enabled, you should see a small, time-sensitive code on your authenticator app whenever you log in to Trezor.io. Simply enter this code in addition to your password, and you will have successfully logged in with two-factor authentication.
By enabling two-factor authentication, you significantly increase the security of your Trezor.io account and protect yourself from phishing attacks. It is an easy and highly recommended step that all users should take to safeguard their funds and personal information.
Be Vigilant of Suspicious Emails
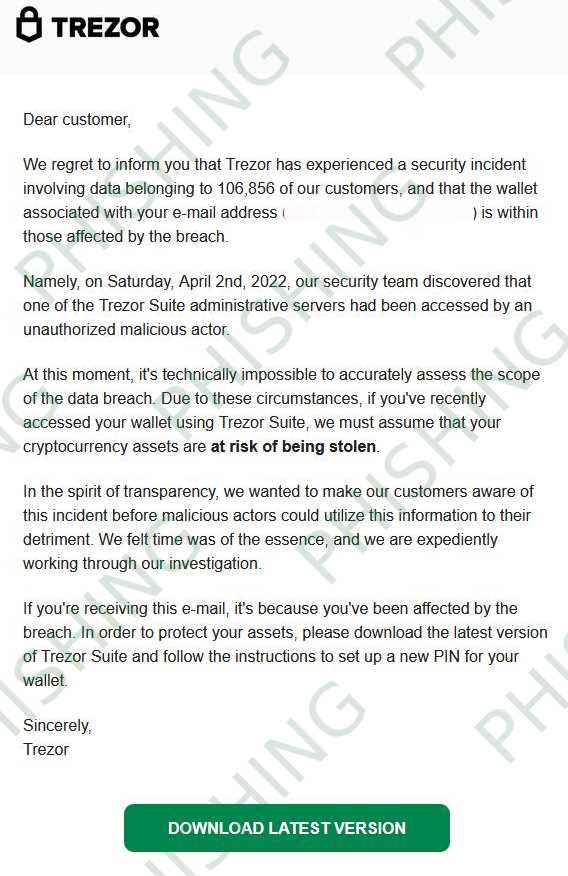
When it comes to securing your Trezor.io login, it’s crucial to be wary of suspicious emails. Phishing attacks often start with an email that looks like it’s from a legitimate source, such as Trezor.io, but is actually designed to steal your account information.
To avoid falling victim to phishing emails, here are some tips to keep in mind:
- Check the sender’s email address carefully. Phishers often use email addresses that mimic the legitimate source, but there may be slight variations or misspellings.
- Pay attention to the email content. Phishing emails often use urgent or threatening language to scare you into taking immediate action.
- Never click on suspicious links or download attachments from unknown senders. These can contain malware or lead you to a fake website designed to steal your login credentials.
- Verify the email with the official source. If you receive an email that seems suspicious, contact the legitimate company directly through their official website to confirm its authenticity.
- Keep your email account secure by using a unique, strong password and enabling two-factor authentication.
By staying vigilant and being cautious of suspicious emails, you can help protect your Trezor.io login from phishing attacks and keep your account secure.
Keep Your Devices Secure
Securing your devices is crucial to protecting your personal information and preventing unauthorized access to your accounts. Follow these tips to keep your devices secure:
1. Enable strong passcodes or biometric authentication
Use a unique and strong passcode or enable biometric authentication, such as fingerprint or facial recognition, to prevent unauthorized access to your device.
2. Keep your software up to date
Regularly update your device’s operating system and applications to ensure that you have the latest security patches and bug fixes. This helps protect against known vulnerabilities that can be exploited by hackers.
3. Install reputable security software
Install reputable antivirus and anti-malware software on your device. This software can help detect and remove any malicious programs or files that may compromise your device’s security.
4. Be cautious when downloading apps or files
Only download apps and files from trusted sources, such as official app stores or reputable websites. Be wary of downloading anything from unverified sources, as they could contain malware or other harmful software.
5. Use a virtual private network (VPN)
When connecting to the internet, especially on public Wi-Fi networks, use a VPN to encrypt your internet traffic. This adds an extra layer of security and prevents others from intercepting your data.
6. Enable two-factor authentication (2FA)
Enable two-factor authentication for your accounts whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password.
7. Regularly back up your data
Regularly back up your important files, photos, and data to external hard drives or cloud storage. This ensures that you can easily recover your data in case of device loss, theft, or damage.
8. Be cautious of phishing attempts
Avoid clicking on suspicious links or providing sensitive information to unknown sources. Phishing attempts can trick you into revealing your login credentials or other personal information, so always verify the source before sharing any sensitive data.
By following these tips and practicing good device security habits, you can better protect your personal information and minimize the risk of unauthorized access to your accounts.
Question-answer:
What is Trezor.io?
Trezor.io is a website that provides a hardware wallet for securely storing cryptocurrency. It is a popular choice for individuals who want to keep their digital assets safe from online threats.
What are phishing attacks?
Phishing attacks are fraudulent attempts to trick individuals into revealing sensitive information, such as passwords, credit card numbers, or private keys. They often come in the form of fake websites or emails that mimic legitimate ones in order to deceive users.
How can I secure my Trezor.io login?
There are several tips to secure your Trezor.io login from phishing attacks:


