
Preventing Future Breaches: Evaluating the Trezor Hack

The recent hack of the Trezor hardware wallet has sent shockwaves through the cryptocurrency community. As more and more people turn to hardware wallets for added security, this incident has raised important questions about the vulnerabilities that exist in these devices. In order to ensure the safety of our digital assets, it is crucial that we thoroughly analyze this hack and learn from it to prevent similar incidents in the future.
First and foremost, it is important to understand the nature of the Trezor hack. The hackers were able to exploit a vulnerability in the device’s firmware, allowing them to gain unauthorized access to users’ private keys. This breach highlights the need for rigorous security measures when it comes to hardware wallets, as even the most reputable brands can have vulnerabilities that can be exploited.
One of the key lessons from this hack is the importance of keeping firmware up to date. By regularly updating the firmware of our hardware wallets, we can ensure that any known vulnerabilities are patched and our devices remain secure. Additionally, it is crucial to only purchase hardware wallets from trusted sources, as counterfeit devices may come with pre-installed malware that can compromise the security of our digital assets.
Furthermore, this incident serves as a reminder that the security of our digital assets is not solely dependent on the hardware wallet itself. It is equally important to practice good security hygiene, such as using strong and unique passwords, enabling two-factor authentication, and regularly backing up our wallets. By implementing these best practices, we can mitigate the risks associated with potential vulnerabilities in hardware wallets.
In conclusion, the Trezor hack has highlighted the need for constant vigilance and proactive security measures in the world of cryptocurrency. By analyzing this incident and learning from it, we can take the necessary steps to secure our future transactions and protect our digital assets from potential threats.
Analyzing the Trezor Hack: What Went Wrong
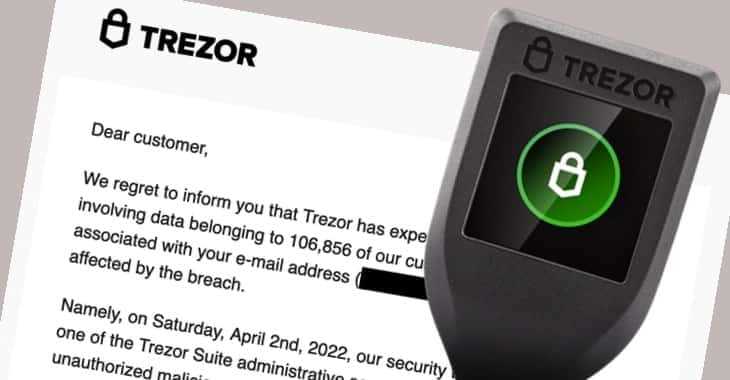
The Trezor hack that occurred highlighted some critical security vulnerabilities that need to be addressed to ensure the safety of future transactions. By examining the hack in detail, we can gain valuable insights into what went wrong and how to prevent similar incidents in the future.
One of the key issues that led to the Trezor hack was a phishing attack. Hackers were able to create a convincing website that mirrored the official Trezor site and tricked users into entering their login credentials. This highlights the importance of educating users about phishing attacks and implementing robust authentication measures to prevent unauthorized access.
Another factor that contributed to the hack was a vulnerability in the firmware of the Trezor device. Hackers were able to exploit this vulnerability and gain access to the private keys stored on the device. This emphasizes the need for regular firmware updates and rigorous security testing to identify and patch any potential vulnerabilities.
Furthermore, the hack revealed the risks associated with storing large amounts of cryptocurrency in a single device. The Trezor hack resulted in significant financial losses for some users who had all their funds stored in one place. It is crucial to diversify storage methods and employ backup strategies to mitigate the impact of potential security breaches.
Additionally, the Trezor hack emphasized the importance of user awareness and proper security practices. Many users fell victim to the phishing attack because they did not verify the authenticity of the website they were accessing. It is essential to educate users about the risks, provide clear instructions on how to verify the legitimacy of websites and transactions, and promote the use of additional security measures such as two-factor authentication.
In conclusion, the Trezor hack serves as a wake-up call for the cryptocurrency industry. It highlights the urgent need for improved security measures, regular firmware updates, user education, and diversification of storage methods. By learning from this incident and implementing necessary safeguards, we can better secure future transactions and protect users’ funds.
Vulnerabilities Exploited in the Trezor Hack

The Trezor hack raised significant concerns over the security of cryptocurrency wallets and the vulnerabilities that attackers can exploit to gain unauthorized access. In this section, we will analyze the specific vulnerabilities that were exploited in the Trezor hack.
1. Physical Access

One of the main vulnerabilities in the Trezor hack was the requirement for physical access to the device. Attackers obtained physical control over the Trezor wallet, allowing them to perform the necessary steps to exploit other vulnerabilities.
2. Firmware Vulnerabilities
The hackers discovered a critical vulnerability within the firmware of the Trezor wallet. By exploiting this vulnerability, they were able to manipulate the firmware and inject malicious code, allowing them to bypass authentication measures and gain unauthorized access to the device.
3. Weak PIN Protection

The weak PIN protection used by the Trezor wallet was also exploited in the hack. The PIN that users set to protect their wallets was vulnerable to brute-force attacks, as the device did not have any mechanism in place to prevent multiple incorrect attempts.
4. Social Engineering
Additionally, the hackers employed social engineering techniques to trick users into revealing their PINs or secret recovery phrases. By impersonating Trezor support staff or creating convincing phishing websites, they were able to deceive users and gain access to their wallets.
In conclusion, the Trezor hack exposed several vulnerabilities that allowed attackers to gain unauthorized access to users’ wallets. It highlights the importance of implementing robust security measures and educating users about potential threats to ensure the safety of their cryptocurrency holdings.
Lessons Learned: Strengthening Future Transactions

The Trezor hack served as a valuable lesson in the importance of securing future transactions. Several key takeaways can be drawn from this incident, providing insights on how to enhance the security of cryptocurrency transactions going forward.
One of the primary lessons learned from the Trezor hack is the criticality of using strong and unique passwords. Many users reuse passwords across multiple accounts, making them vulnerable to attacks. It is crucial to create complex and unique passwords for each cryptocurrency wallet to minimize the risk of unauthorized access.
Another lesson is the significance of regularly updating firmware and software. Trezor developers released an update that addressed the vulnerabilities exploited in the hack. Keeping the firmware and software up to date ensures that any known security issues are patched, reducing the likelihood of successful attacks.
Furthermore, enabling two-factor authentication (2FA) plays a crucial role in strengthening account security. By requiring an additional verification step, such as entering a unique code sent to a trusted device, 2FA adds an extra layer of protection against unauthorized access.
Additionally, storing cryptocurrency offline in hardware wallets can provide enhanced security. Hardware wallets like Trezor keep the private keys offline, minimizing the risk of them being compromised by malware or hackers. Storing funds offline reduces the attack surface and increases the overall security of transactions.
Lastly, promoting user education and awareness is key to preventing future attacks. By educating users about the risks associated with storing and transacting with cryptocurrencies, they can make more informed decisions and take necessary precautions to protect their assets.
In conclusion, the Trezor hack serves as a reminder of the importance of strengthening future transactions. By adopting strong passwords, regularly updating firmware, enabling 2FA, using hardware wallets, and promoting user education, individuals can significantly enhance the security of their cryptocurrency transactions.
Importance of Regular Security Audits and Updates
Regular security audits and updates are essential to maintaining the integrity and security of any system, especially when it comes to protecting financial transactions. The Trezor hack serves as a reminder of the constant threats faced by users of cryptocurrency wallets and the need for proactive security measures.
One of the primary benefits of regular security audits is the identification of vulnerabilities and weaknesses in the system. By conducting thorough assessments, developers can pinpoint potential entry points for hackers and take the necessary steps to fortify those areas. This proactive approach can prevent future attacks and protect the sensitive information stored within the wallet.
Additionally, regular security audits allow developers to stay up to date with the latest security practices and industry standards. As technology advances and hackers become more sophisticated, it is crucial to evolve and adapt security measures accordingly. By regularly reviewing and updating security protocols, wallet providers can ensure that their systems remain resilient to emerging threats and safeguard user funds.
Benefits of Regular Security Audits and Updates:
- Identify vulnerabilities and weaknesses
- Prevent future attacks
- Protect sensitive information
- Stay up to date with security practices
- Adapt to emerging threats
- Safeguard user funds
In conclusion, regular security audits and updates play a crucial role in the protection of financial transactions, especially in the context of cryptocurrency wallets. By conducting thorough assessments, staying informed about the latest security practices, and implementing necessary updates, wallet providers can enhance the security of their systems and ensure the safety of user funds.
Exploring Alternative Hardware Wallet Options

In light of the recent Trezor hack, it is important for cryptocurrency investors to consider alternative hardware wallet options to secure their future transactions. While Trezor remains a popular choice for many, it is always wise to explore and diversify one’s options.
One alternative hardware wallet option is Ledger Nano S. This hardware wallet is highly regarded for its robust security features. With a combination of encryption and tamper-proof hardware, the Ledger Nano S ensures that private keys and transactions remain secure.
Another option worth exploring is KeepKey. Like Trezor and Ledger, KeepKey is a hardware wallet that offers a high level of security. It uses a large display and a confirmation button to verify transactions, providing an extra layer of protection against malicious attacks.
Treasury, by Coinkite, is another hardware wallet that is gaining popularity. It is designed for convenience and security, allowing users to easily send and receive transactions through its touchscreen interface. It also supports multi-signature transactions for added security.
While these are just a few examples, it is crucial for cryptocurrency investors to research and evaluate different hardware wallet options. Each wallet has its own unique features and security measures, catering to different user preferences and needs. By diversifying one’s hardware wallet options, investors can mitigate the risk of potential hacks and ensure the security of their digital assets.
It is important to note that while hardware wallets provide an added layer of security, users must still practice proper security measures such as keeping their wallets and recovery phrases in secure locations, enabling two-factor authentication, and staying vigilant against phishing attempts.
In summary, exploring alternative hardware wallet options is a crucial step in securing future transactions. By researching and evaluating different wallets, investors can find a solution that best fits their needs and provides the highest level of security for their digital assets.
Q&A:
What is the Trezor Hack?
The Trezor Hack refers to a recent cyber attack in which hackers managed to access a significant amount of cryptocurrency from Trezor wallets.
How did the hackers manage to hack the Trezor wallets?
The exact details of how the hackers hacked the Trezor wallets are not known, but it is believed that they exploited a vulnerability in the device’s firmware.


