
Pitfalls of Utilizing Trezor as Cold Storage

Trezor is one of the most popular hardware wallets used for storing cryptocurrencies. With its offline storage capability, it provides a secure solution for safeguarding digital assets. However, like any technology, there are potential drawbacks to consider when using Trezor as a cold storage option.
Firstly, relying solely on Trezor as a cold storage option means putting all your eggs in one basket. If something were to happen to your Trezor device, such as loss or damage, you may lose access to your cryptocurrencies permanently. It is important to have backup measures in place to ensure the safety of your digital assets.
Another potential drawback is the learning curve associated with using Trezor. While the device itself is user-friendly, understanding the ins and outs of cold storage and the security protocols can be challenging for beginners. It requires a certain level of technical knowledge and diligence to ensure proper usage and protection of your cryptocurrencies.
Furthermore, Trezor is a physical device that can be subject to theft. Although the device is designed to be resistant to tampering, it is still vulnerable to physical attacks. If someone gains access to your Trezor and manages to extract the seed phrase or PIN, they can potentially access your funds. It is essential to keep your Trezor device in a secure location and implement additional security measures to minimize this risk.
In conclusion, while Trezor offers a secure means of cold storage for cryptocurrencies, it is important to be aware of its potential drawbacks. It is crucial to have backup measures, be knowledgeable about cold storage protocols, and implement additional security measures to mitigate the risks associated with using Trezor as a cold storage option.
Security Risks

While Trezor is generally considered a secure option for cold storage of cryptocurrencies, it is not without its potential security risks. One of the main concerns is the possibility of physical theft. If someone gains access to your Trezor device, they can potentially steal your cryptocurrency by bypassing the device’s security measures.
Another security risk is the possibility of keyloggers or other malware compromising your computer or smartphone. If a malicious program is able to record your keystrokes or capture your screen while you are using the Trezor web interface, it could potentially obtain your private key and gain access to your funds.
There is also the risk of phishing attacks, where scammers create fake websites or emails that mimic the official Trezor interface in order to trick users into entering their sensitive information. If users are not vigilant and fail to verify the authenticity of the website or email, they could inadvertently provide their private key to attackers.
Furthermore, there have been reports of vulnerabilities in the Trezor hardware and firmware, although these are relatively rare. If hackers discover a weakness in the device’s security system, they may be able to exploit it and gain unauthorized access to your funds.
Lastly, there is the risk of user error. If you forget your PIN or lose your recovery seed, you may permanently lose access to your funds. It is essential to securely store your recovery seed and take appropriate measures to ensure it does not fall into the wrong hands.
Overall, while Trezor is a reputable and secure option for cold storage, users should be aware of the potential security risks and take appropriate precautions to protect their funds.
Vulnerability to Physical Damage
While Trezor offers secure offline storage for cryptocurrencies, it is important to consider that it is not immune to physical damage. Physical damage can occur through various means such as dropping the device, exposing it to extreme temperatures, or even accidentally spilling liquids on it.
One of the main vulnerabilities of Trezor to physical damage is its hardware component. The device consists of a small and delicate circuit board that houses the private keys. Any physical damage to this board can potentially result in the loss of the stored cryptocurrencies.
Another potential vulnerability is the device’s USB connector. Since Trezor requires connection to a computer or other device to access and manage the stored cryptocurrencies, the USB connector can be prone to wear and tear over time. Excessive use or accidental damage to the connector can render the device unusable or cause issues with connectivity.
To minimize the risk of physical damage to Trezor, it is recommended to handle the device with care and store it in a secure location when not in use. Additionally, users should avoid exposing the device to extreme temperatures or liquids that could potentially damage the hardware.
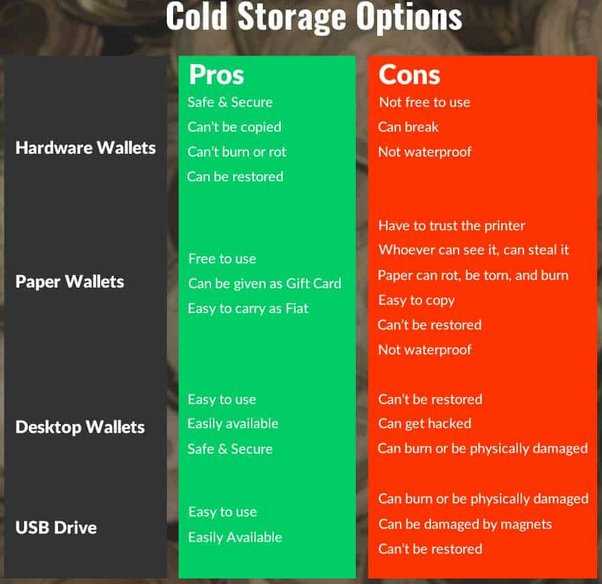
| Pros | Cons |
|---|---|
| Secure offline storage | Vulnerable to physical damage |
| Easy to use and set up | Reliance on hardware and USB connector |
| Protection against malware and phishing attacks | Cost of purchasing the device |
| Support for multiple cryptocurrencies | Potential compatibility issues with certain devices |
Limited Accessibility

One potential drawback of using Trezor as a cold storage option is the limited accessibility it offers. Since Trezor is a hardware device, it requires physical access in order to manage and access your cryptocurrency funds. This can be inconvenient for users who need quick and easy access to their funds, especially in emergency situations.
Unlike online wallets or software wallets, which can be accessed from any device with an internet connection, Trezor can only be used with the specific device it is connected to. This means that if you lose or forget your Trezor device, or if it gets damaged or stolen, you may lose access to your funds permanently.
Additionally, if you travel frequently or often find yourself in situations where you need to access your cryptocurrency funds while on the go, Trezor may not be the most practical option. You would need to carry the Trezor device with you at all times, which can be cumbersome and increase the risk of losing or damaging it.
Furthermore, if the Trezor company were to go out of business or discontinue support for their device, it could potentially render your Trezor device useless. Without continued updates and support, your funds stored on the device may become inaccessible.
While the limited accessibility of Trezor is intended to provide enhanced security for your cryptocurrency funds, it can also be a downside for users who require more flexibility and convenience in managing their assets.
Dependence on Third-Party Software
One potential drawback of using Trezor as a cold storage option is the dependence on third-party software. While Trezor provides secure storage for your private keys and allows you to sign transactions offline, you still need to use third-party software to interact with your Trezor device.
Most users rely on software wallets or web interfaces to manage and transact with their cryptocurrencies. These software wallets often require you to connect your Trezor device to your computer or mobile device and use their interface to access your funds.
While many software wallets are reputable and have built-in security measures, there is still a level of trust involved when using third-party software. If the software wallet you are using is compromised or contains a vulnerability, it can potentially put your funds at risk.
Additionally, using third-party software means that you are reliant on the availability and compatibility of that software. If the software wallet you are using becomes incompatible with your Trezor device or is no longer supported, it could limit your ability to access or manage your funds.
Table: Potential Risks of Depending on Third-Party Software with Trezor
| Risks | Explanation |
|---|---|
| Compromised software | If the software wallet you are using is compromised, it can potentially expose your private keys and funds to malicious actors. |
| Vulnerabilities | Third-party software may contain vulnerabilities that could be exploited to gain unauthorized access to your Trezor device or funds. |
| Availability and compatibility | If the software wallet you rely on becomes unavailable or incompatible with your Trezor device, it could hinder your ability to access or manage your funds. |
It is important to carefully research and select reputable and trusted software wallets when using Trezor as a cold storage option. Regularly updating both your Trezor firmware and the software wallet you are using can help mitigate potential risks.
Q&A:
What are some potential drawbacks of using Trezor as a cold storage option?
There are a few potential drawbacks of using Trezor as a cold storage option. One drawback is that it requires a physical device, which means if you lose the device, you could potentially lose access to your cryptocurrencies. Another drawback is that Trezor can be susceptible to malware or hacking attempts if not used correctly. Additionally, Trezor may not support all cryptocurrencies, so you should check if your specific coins are supported before using it as a cold storage option.
Can using Trezor as a cold storage option be risky?
While using Trezor as a cold storage option can be a secure option, there are still some risks involved. One risk is the potential loss of the physical device, which could result in the loss of access to your cryptocurrencies. Another risk is the possibility of malware or hacking attempts if the device is not used securely. It’s important to take precautions and always backup your device and store it in a safe location.
Are there any limitations to using Trezor as a cold storage option?
Yes, there are a few limitations to using Trezor as a cold storage option. Firstly, Trezor may not support all cryptocurrencies, so you should check if your specific coins are supported before using it. Secondly, using Trezor as a cold storage option requires a physical device, so if you prefer a more convenient solution, it may not be the best option for you. Finally, there is a small learning curve associated with using Trezor, so you will need to familiarize yourself with the device and its features.
Is it possible to lose access to my cryptocurrencies if I use Trezor as a cold storage option?
Yes, it is possible to lose access to your cryptocurrencies if you use Trezor as a cold storage option. If you lose the physical device, you will not be able to access your funds unless you have a backup or recovery seed. It’s important to keep your device safe and secure, and to have a backup plan in case of loss or damage to the device.
How can I ensure the security of my cryptocurrencies when using Trezor as a cold storage option?
To ensure the security of your cryptocurrencies when using Trezor as a cold storage option, there are a few key steps you should take. Firstly, always buy your Trezor device from an authorized and reputable source to avoid counterfeits. Secondly, set up a strong PIN code and enable two-factor authentication to protect your device from unauthorized access. Finally, regularly update the firmware on your Trezor device and double-check the official Trezor website for any security updates or alerts.


