Key Takeaways from the Trezor Breach: Insights and Recommendations

When it comes to cybersecurity and protecting our valuable digital assets, knowledge is power. That’s why it’s crucial for individuals and businesses alike to understand the recent breach of the popular hardware wallet, Trezor. The breach served as a wake-up call, highlighting the importance of implementing strong security measures and staying up-to-date on the latest best practices.
In this article, we will delve into the details of the Trezor breach, examining how it occurred and the lessons we can learn from it. We will explore the vulnerabilities that were exploited and discuss the implications for users of hardware wallets. By understanding the breach, we can equip ourselves with the knowledge necessary to prevent similar incidents in the future.
One of the key takeaways from the Trezor breach is the importance of password management. Users must adopt robust password practices, such as creating unique and complex passwords for each online account and regularly updating them. Additionally, enabling two-factor authentication can provide an extra layer of security, mitigating the impact of a potential breach.
Furthermore, the breach underscores the crucial need for regular software updates. Manufacturers of hardware wallets, like Trezor, work tirelessly to identify vulnerabilities and release patches to address them. It is essential for users to promptly install these updates to ensure their devices are protected from the latest threats.
While breaches like the one that affected Trezor can be unsettling, they serve as powerful reminders of the importance of cybersecurity. By staying informed and implementing best practices, we can protect our digital assets and prevent unauthorized access. It’s a constant battle, but one that we must be prepared to fight in order to safeguard our financial and personal information.
Armed with the knowledge acquired from understanding the Trezor breach, we can take proactive steps to secure our digital wallets and ensure the safety of our cryptocurrencies. Let’s learn from this incident, share the lessons with others, and together, strengthen our defenses against future breaches.
Understanding the Trezor Breach: Key Takeaways
The Trezor breach demonstrated the importance of implementing strong security measures for cryptocurrency storage and emphasized the need for users to exercise caution when using hardware wallets. Here are the key takeaways from the incident:
1. Choose a reputable hardware wallet manufacturer
It is crucial to research and select a hardware wallet manufacturer that is trusted and has a proven track record in the industry. This helps to reduce the risk of vulnerabilities and security breaches.
2. Keep software and firmware up to date
Regularly updating the software and firmware of your hardware wallet is essential to ensure that you have the latest security patches and bug fixes. This helps to protect against known vulnerabilities and enhances the overall security of your cryptocurrency holdings.
3. Enable multi-factor authentication

Using multi-factor authentication adds an extra layer of security to your hardware wallet. Enable this feature whenever possible to further protect your funds from unauthorized access.
4. Implement a strong PIN

Choosing a strong PIN is crucial to safeguard your hardware wallet. Avoid using easily guessable or common PINs and opt for a unique combination of numbers and characters that is difficult for others to guess.
5. Be cautious of phishing attempts
Always be vigilant and cautious of phishing attempts. Exercise caution when entering your wallet’s seed phrase, sensitive information, or providing personal details online. Be sure to verify the authenticity of the websites or applications you interact with before entering any personal information.
6. Backup and secure your seed phrase
It is essential to back up and securely store your hardware wallet’s seed phrase. This ensures that you can recover your funds in the event of loss, damage, or theft of your hardware wallet.
7. Test recovery process and backup
Regularly test the recovery process by restoring your hardware wallet using your backup seed phrase. This helps ensure that you have correctly backed up your wallet and can confidently recover your funds if needed.
8. Stay informed about security updates
Stay updated on the latest security measures and best practices for cryptocurrency storage. Following reliable sources, such as official hardware wallet manufacturer websites and industry news outlets, can help you stay informed about any potential security vulnerabilities or updates.
| Disclaimer: |
| The information provided in this article is for educational and informational purposes only. It is not intended as financial or investment advice. Please do your own research and exercise caution when dealing with cryptocurrencies. |
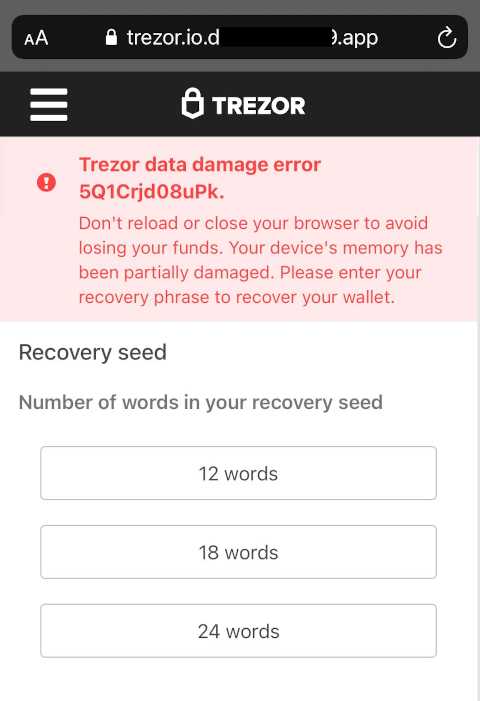
Breach Overview: What Happened?
In this section, we will provide a detailed overview of the Trezor breach and what exactly happened. On March 1st, 2020, Trezor, a popular hardware wallet provider, announced that they had experienced a security breach. The breach involved unauthorized access to Trezor’s infrastructure and resulted in the compromise of customer data.
According to Trezor, the breach occurred due to a sophisticated phishing attack. The attacker sent fraudulent emails to Trezor customers, pretending to be from the company, and tricked them into revealing their login credentials. With these credentials, the attacker gained access to the internal systems of Trezor.
Once inside, the attacker had access to sensitive customer data, including email addresses, ordered products, and some shipping addresses. It is important to note that no funds or private keys were compromised in the breach since the attacker did not have access to Trezor wallets directly.
Trezor responded promptly to the breach by immediately notifying all affected customers via email and posting a public announcement on their website. They assured their customers that they had taken steps to address the issue, including resetting all user passwords and enhancing their security measures.
As a result of the breach, Trezor also advised their customers to be cautious of any suspicious emails and to always verify the legitimacy of any communication before sharing personal information. They emphasized the importance of using strong and unique passwords for their accounts and enabling two-factor authentication whenever possible.
In conclusion, the Trezor breach was a result of a phishing attack, which allowed an attacker to gain unauthorized access to customer data. Trezor promptly responded to the breach by taking necessary measures to secure their systems and notify affected customers.
Lessons Learned: Security Measures and Precautions
Following the Trezor breach incident, it is important for individuals and organizations to learn from the incident and implement appropriate security measures and precautions to prevent similar breaches from occurring in the future. Here are some key lessons that can be taken away from the incident:
Educate Employees and Users:
One crucial lesson is the importance of educating employees and users about security best practices. It is essential to provide comprehensive training and awareness programs to ensure that individuals are aware of the potential risks and understand how to protect their devices and data.
Implement Multi-Factor Authentication:
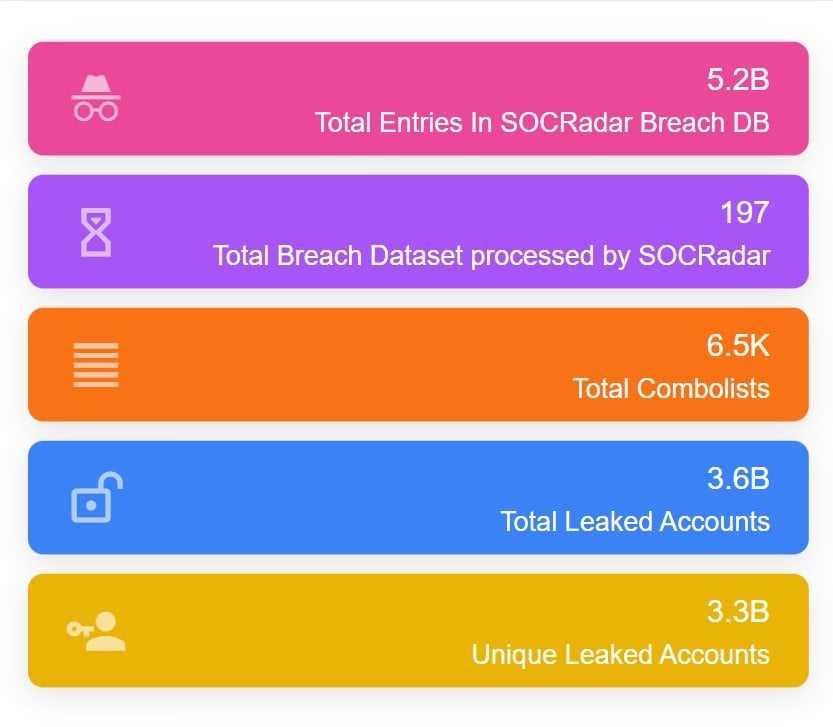
Another lesson learned is the significance of implementing multi-factor authentication (MFA) for accessing sensitive information and systems. This additional layer of security can greatly reduce the risk of unauthorized access, even if passwords are compromised.
Regularly Update Software and Firmware:
Maintaining up-to-date software and firmware is critical for ensuring the security of devices and systems. Regularly checking for updates and promptly applying patches and security fixes can help protect against known vulnerabilities and exploits.
Use Strong Passwords:
Using strong and unique passwords for different accounts is a fundamental security practice. It is important to encourage the use of complex passwords, comprised of a combination of letters, numbers, and special characters, and to avoid common password patterns that are easy to guess.
Implement Access Controls:
Implementing access controls and limiting user privileges can help prevent unauthorized access and reduce the impact of a potential breach. Only providing necessary access permissions to individuals based on their roles and responsibilities can significantly reduce the attack surface.
Regularly Backup Data:
Creating regular backups of important data is an essential precaution that can minimize the impact of a breach or data loss incident. Backups should be stored in secure locations and tested periodically to ensure data integrity.
Conduct Regular Security Assessments:
Regularly conducting security assessments and penetration testing can help identify vulnerabilities and weaknesses in systems and infrastructure. By proactively identifying and addressing these issues, organizations can strengthen their security posture and reduce the risk of breaches.
By implementing these security measures and precautions, individuals and organizations can enhance their overall security posture and better protect their sensitive information and assets from potential breaches and attacks.
Best Practices: Protecting Your Digital Assets
In today’s digital age, it is crucial to take the necessary steps to protect your digital assets. Whether you have cryptocurrencies, important documents, or personal information stored online, implementing best practices can help safeguard your valuable data from unauthorized access.
1. Use a Strong and Unique Password
Creating a strong and unique password is the first line of defense in protecting your digital assets. Avoid using common passwords or easily guessable combinations. Instead, use a combination of uppercase and lowercase letters, numbers, and special characters. Furthermore, it is essential to use a unique password for each online account to prevent a domino effect in case one account gets compromised.
2. Enable Two-Factor Authentication (2FA)
Enable two-factor authentication whenever possible. Two-factor authentication adds an extra layer of security to your accounts by requiring an additional piece of information, such as a verification code sent to your phone, in addition to your password. This makes it significantly harder for hackers to gain unauthorized access to your accounts.
3. Keep Software and Firmware Up to Date
Regularly update the software and firmware on all your devices, including your computer, smartphone, and any hardware wallets. These updates often include security patches that address known vulnerabilities. By keeping your software and firmware up to date, you ensure that you have the latest protection against emerging threats.
4. Use a Hardware Wallet
If you have cryptocurrencies or other digital assets, consider using a hardware wallet for added security. A hardware wallet is a physical device that stores your private keys offline, making it much more difficult for hackers to access your funds. Look for hardware wallets from reputable manufacturers and always verify the authenticity of the device before using it.
5. Be Wary of Phishing Attempts

Phishing is a common tactic used by hackers to trick individuals into revealing their sensitive information. Be cautious of emails, messages, or websites that ask for your login credentials or personal data. Always double-check the sender’s email address, be wary of unsolicited communications, and verify the legitimacy of any websites before entering any sensitive information.
By following these best practices, you can significantly reduce the risk of unauthorized access to your digital assets. Taking proactive steps to protect your valuable data not only ensures your financial security but also provides peace of mind in an increasingly digital world.
Moving Forward: Improving Security in the Crypto Industry

The Trezor breach serves as a stark reminder of the importance of strengthening security measures within the crypto industry. As the value and popularity of cryptocurrencies rise, so does the risk of cyberattacks and breaches. It is imperative that the industry takes proactive steps to enhance the security of their systems and protect user funds.
Here are some key strategies that can be implemented to improve security in the crypto industry:
- Hardware Wallet Innovation: Hardware wallets like Trezor have long been considered one of the most secure ways to store cryptocurrencies. Continuous research and innovation in this area will lead to the development of even more advanced and robust hardware wallets with enhanced security features.
- Multi-Factor Authentication: Implementing multi-factor authentication (MFA) adds an extra layer of security to user accounts. By requiring users to provide two or more factors of authentication, such as a password and a unique code sent to their mobile device, it becomes much harder for attackers to gain unauthorized access.
- Bug Bounty Programs: Encouraging ethical hackers to report vulnerabilities through bug bounty programs can help identify and fix security flaws before they can be exploited. By rewarding individuals who responsibly disclose vulnerabilities, crypto companies can improve their security posture.
- Security Audits: Regular security audits conducted by third-party experts can help identify potential vulnerabilities and weaknesses in crypto systems. Identifying and addressing these issues promptly can prevent future breaches.
- User Education: Educating users about security best practices is crucial for protecting their funds. Crypto companies should provide clear and easy-to-understand guides on topics such as choosing strong passwords, enabling MFA, and being wary of phishing attempts.
- Regulatory Compliance: The crypto industry should work closely with regulators to establish and adhere to robust security standards. This will help create a more secure ecosystem and build trust among users and investors.
As cryptocurrencies continue to gain mainstream adoption, the importance of security in the industry cannot be overstated. By implementing these strategies and continuously striving to improve security measures, the crypto industry can protect user funds and ensure the long-term success of cryptocurrencies.
Q&A:
What is the Trezor Breach?
The Trezor Breach refers to a security incident that occurred with the Trezor hardware wallet, which is a popular device used for storing cryptocurrency. During the breach, hackers were able to gain access to some of the wallet’s sensitive information, potentially putting user’s funds at risk.
How did the Trezor Breach happen?
The exact details of the Trezor Breach have not been publicly disclosed, but it is believed that the breach was a result of a vulnerability in the device’s firmware or software. Hackers may have exploited this vulnerability to gain unauthorized access to the wallet’s data.
What are the lessons learned from the Trezor Breach?
The Trezor Breach serves as a reminder of the importance of strong security practices when it comes to cryptocurrency storage. Some of the key lessons learned from this incident include the need to regularly update firmware and software, use strong and unique passwords, enable two-factor authentication, and store backups of wallet data in secure locations.


