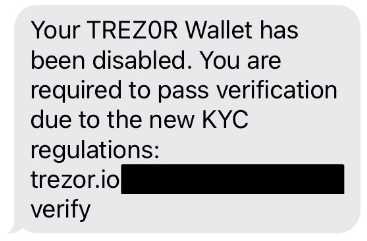
Hacker Breaks into Trezor Implications for Cryptocurrency Security

In a shocking turn of events, a renowned hacker has successfully breached Trezor, one of the most popular hardware wallets for storing cryptocurrencies. This incident highlights the alarming security consequences that cryptocurrency holders might face, further emphasizing the critical need for robust security measures in the digital asset sector.
Trezor, known for its strong security features and user-friendly interface, has been a go-to choice for many cryptocurrency enthusiasts to safeguard their digital wealth. However, this breach has raised serious concerns about the vulnerability of such wallets, and calls into question the overall security infrastructure of the cryptocurrency ecosystem.
The breach itself, which remains shrouded in mystery, has sent shockwaves throughout the cryptocurrency community. Many are now questioning the reliability of hardware wallets and the level of protection they can offer. With the increasing value of cryptocurrencies, hackers are constantly honing their skills and devising new ways to infiltrate security systems, leaving individuals and businesses exposed to potential financial losses.
This incident also serves as a reminder of the importance of taking personal responsibility for securing one’s own assets. While hardware wallets are generally considered safer compared to other forms of storing cryptocurrencies, it is crucial for users to stay vigilant and keep up with the latest security updates. The digital asset landscape is constantly evolving, and the battle between hackers and security experts is an ongoing one.
Hacker Breaches Trezor: Understanding the Implications
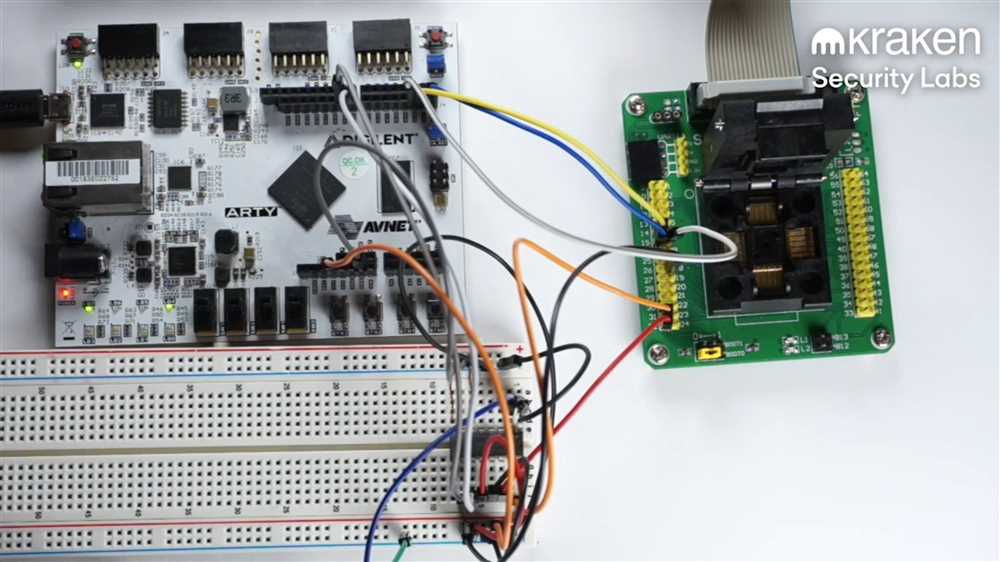
In recent news, a hacker has managed to breach the security measures of the popular cryptocurrency wallet known as Trezor. This significant breach raises serious concerns and has far-reaching implications for the cryptocurrency community.
1. Theft of Funds

The immediate consequence of this breach is the high possibility of theft of funds. Trezor wallets contain user’s private keys, which are essential for accessing and managing their cryptocurrencies. If a hacker gains access to these private keys, they can easily transfer the funds to their own wallets, leaving the victims at a significant financial loss.
2. Compromised Security

The breach of Trezor raises doubts about the overall security of hardware wallets. Trezor is considered one of the most secure options in the market, and if it can be compromised, it raises questions about the security of other similar devices. This breach serves as a reminder that no system is completely immune to attacks.
3. Loss of Trust

Trust is a critical element in the world of cryptocurrencies. The breach of Trezor can lead to a loss of trust in hardware wallets in general. Investors and users may start questioning the safety of their digital assets, and as a result, may choose to avoid using hardware wallets altogether, affecting the adoption and growth of cryptocurrencies.
4. Regulatory Scrutiny
The breach of this magnitude is likely to attract regulatory attention. Governments and regulatory bodies may decide to tighten control and impose stricter regulations on the cryptocurrency industry. This could impact the anonymity and decentralized nature that cryptocurrencies strive to maintain.
5. Increased Phishing and Scams

The exposure of Trezor’s security measures opens the door for phishing attempts and scams. Hackers can use the information gained from this breach to craft convincing phishing emails or messages, tricking users into revealing their private keys or other sensitive information. This could lead to further financial losses and compromise the security of the cryptocurrency community.
- The breach of Trezor highlights the vulnerabilities of hardware wallets and emphasizes the importance of staying vigilant in the face of evolving hacking techniques.
- It is crucial for cryptocurrency enthusiasts to explore alternative security measures and adopt best practices to protect their digital assets.
- Furthermore, hardware wallet manufacturers need to reassess and enhance their security protocols to prevent future breaches.
In conclusion, the breach of Trezor has wide-ranging implications for the cryptocurrency community. It underscores the need for improved security measures, increased awareness regarding potential threats, and the importance of trusting reliable and secure platforms to safeguard digital assets.
Security Vulnerabilities in Cryptocurrency Storage
Storing cryptocurrencies securely is a critical concern for individuals and businesses alike. Unfortunately, there are various security vulnerabilities that can put these digital assets at risk. Understanding these vulnerabilities is essential for developing robust security measures.
One common vulnerability is the use of weak passwords or passphrase protection. Many users tend to choose easy-to-guess passwords or reuse the same password across multiple platforms. This makes it easier for hackers to gain unauthorized access to their cryptocurrency storage.
Another vulnerability is phishing attacks. Hackers often send fake emails or use other social engineering techniques to trick users into revealing their private keys. Once the private keys are compromised, the hackers can easily access and steal the stored cryptocurrencies.
Malware and keyloggers also pose a significant threat to cryptocurrency storage. If a user’s device is infected with malware, it can record keystrokes and steal private keys or other sensitive information related to the cryptocurrency storage. This puts the digital assets at risk of theft.
Physical theft is another security vulnerability that cryptocurrency holders need to be aware of. If a person has physical access to a device containing the private keys, they may be able to extract the keys and gain control over the stored cryptocurrencies. This makes it essential to keep the devices and storage backups in secure locations.
Lastly, there are vulnerabilities specific to hardware wallets, such as the popular Trezor device. Although hardware wallets offer enhanced security, they are still not entirely immune to attacks. In the case of the Trezor breach, the hacker exploited a vulnerability in the wallet’s firmware to gain control over the stored cryptocurrencies.
- Weak passwords
- Phishing attacks
- Malware and keyloggers
- Physical theft
- Hardware wallet vulnerabilities
To mitigate these vulnerabilities, it is crucial to take proactive security measures, such as using strong and unique passwords, enabling two-factor authentication, keeping devices updated with the latest security patches, and using reputable hardware wallets. Additionally, staying informed about the latest security threats and best practices can help cryptocurrency holders stay one step ahead of potential attacks.
In conclusion, the security vulnerabilities in cryptocurrency storage pose significant risks to the digital assets of individuals and businesses. Understanding these vulnerabilities and implementing robust security measures is essential for safeguarding cryptocurrencies against unauthorized access and theft.
Trezor Hack: Impact on Cryptocurrency Owners
The recent breach of Trezor, a popular hardware wallet for cryptocurrencies, has raised serious concerns about the security of digital assets. This incident has left cryptocurrency owners vulnerable to potential risks and has highlighted the need for enhanced security measures.
With the hack, the attacker gained unauthorized access to Trezor’s private keys, which could potentially allow them to steal funds from users’ wallets. This has put the entire cryptocurrency ecosystem at risk, as Trezor is widely used by investors and traders to store their digital assets securely.
As a result of the breach, cryptocurrency owners face significant financial loss. The stolen funds could range from a few to millions of dollars depending on the value and quantity of cryptocurrencies stored in the compromised Trezor wallets. These losses can have a devastating impact on individuals and organizations who rely on cryptocurrencies for their financial activities.
In addition to financial loss, the hack has also raised concerns about privacy and identity theft. Cryptocurrency owners often use pseudonyms and rely on the security of their wallets to protect their identities. With this breach, there is a risk that personal information linked to the compromised wallets could be exposed, potentially leading to blackmail or other forms of targeted attacks.
Furthermore, the Trezor hack has eroded trust in the security of hardware wallets and has prompted cryptocurrency owners to reevaluate their storage options. Many are now considering alternative solutions, such as software wallets or decentralized exchanges, which offer different security features and may be less vulnerable to similar breaches.
Overall, the Trezor hack has had a significant impact on cryptocurrency owners. It has exposed the vulnerability of hardware wallets and has highlighted the necessity for improved security measures in the cryptocurrency industry. As the threat landscape evolves, it is crucial for individuals and organizations to remain vigilant and adopt robust security practices to protect their digital assets.
Steps to Enhance Your Cryptocurrency Security

Protecting your cryptocurrency assets is of utmost importance in an increasingly digital world. With the rise in cyberattacks and hacker breaches, it is imperative to take proactive steps to enhance your cryptocurrency security. Here are some essential measures to consider:
1. Use a Hardware Wallet: A hardware wallet, such as Trezor, provides an added layer of security by storing your private keys offline. This greatly reduces the risk of online attacks and unauthorized access to your cryptocurrency funds.
2. Enable Two-Factor Authentication: Implementing two-factor authentication adds an extra security step to the login process. By requiring a second form of authentication, such as a verification code sent to your mobile device, you can significantly reduce the risk of unauthorized access.
3. Regularly Update Your Wallet Software: Wallet providers often release updates that patch vulnerabilities and improve security. It is crucial to regularly update your wallet software to ensure you have the latest security enhancements.
4. Use Strong, Unique Passwords: Creating strong and unique passwords for your cryptocurrency accounts is essential. Avoid using common phrases or easily guessable information. Utilize a combination of uppercase and lowercase letters, numbers, and special characters for maximum security.
5. Be Mindful of Phishing Attempts: Phishing is a common method used by hackers to trick individuals into revealing their login credentials. Always be cautious of unsolicited emails or messages asking for personal information. Verify the authenticity of the source before providing any sensitive data.
6. Secure Your Digital Footprint: Be mindful of your online activities and take steps to secure your digital footprint. Avoid using public Wi-Fi networks when accessing your cryptocurrency accounts and be cautious of the websites you visit. Install and regularly update reputable antivirus software to detect and prevent any potential threats.
7. Keep Backup Copies of Your Wallet: In case of hardware failure, loss, or theft, it is crucial to keep backup copies of your wallet and store them securely. Consider using offline storage options, such as encrypted USB drives or paper wallets, to safeguard your cryptocurrency assets.
8. Educate Yourself: Stay informed about the latest security practices and trends in the cryptocurrency industry. By educating yourself on potential risks and best practices, you can make informed decisions to enhance your cryptocurrency security.
Conclusion: Taking proactive steps to enhance your cryptocurrency security is essential in protecting your digital assets from potential threats. By implementing these measures, you can significantly reduce the risk of hacker breaches and ensure the safety of your cryptocurrency holdings.
Q&A:
Are my cryptocurrencies safe if I use a Trezor wallet?
Using a Trezor wallet is generally considered to be safe, as it provides a high level of security for storing cryptocurrencies. However, it is important to stay vigilant and keep your wallet firmware updated to protect against potential vulnerabilities.
What are the consequences of the hacker breaching Trezor?
The consequences of a hacker breaching Trezor could potentially be severe. If the hacker gains access to a user’s private keys, they could steal their cryptocurrencies, leading to financial loss. Additionally, it could damage the reputation of Trezor and shake the confidence of users in the security of hardware wallets.
How can I protect my cryptocurrencies from a potential breach?
To protect your cryptocurrencies from a potential breach, it is important to take several precautions. Firstly, make sure to always purchase hardware wallets directly from reputable sources. Additionally, regularly update your wallet’s firmware to ensure it has the latest security patches. Finally, be cautious of phishing attempts and never share your private keys with anyone.


