
Flaws in popular hardware wallet models exposed by Trezor hack reveal major vulnerabilities

Hardware wallets have long been touted as the most secure way to store cryptocurrencies. These physical devices, like the popular Trezor and Ledger wallets, use offline storage and encryption to protect users’ private keys. However, a recent hack has exposed vulnerabilities in these supposedly ironclad security measures.
The hack, which targeted Trezor devices, was carried out by a group of security researchers who were able to bypass the wallet’s encryption and gain access to users’ private keys. This type of attack is known as a “cold boot” attack, and it involves freezing the device’s memory chip to extract sensitive information.
While the hack required physical access to the device, it highlights the fact that even the most advanced hardware wallets are not immune to security vulnerabilities. As cryptocurrencies continue to gain popularity and value, hackers are becoming more motivated to find ways to exploit these wallets’ weaknesses.
As a result of this hack, it is crucial for hardware wallet manufacturers to continuously improve their products’ security measures. Users should also take precautions, such as keeping their wallets up to date with the latest firmware and avoiding purchasing used devices, which may have been compromised.
Trezor hack: a wake-up call for hardware wallet security
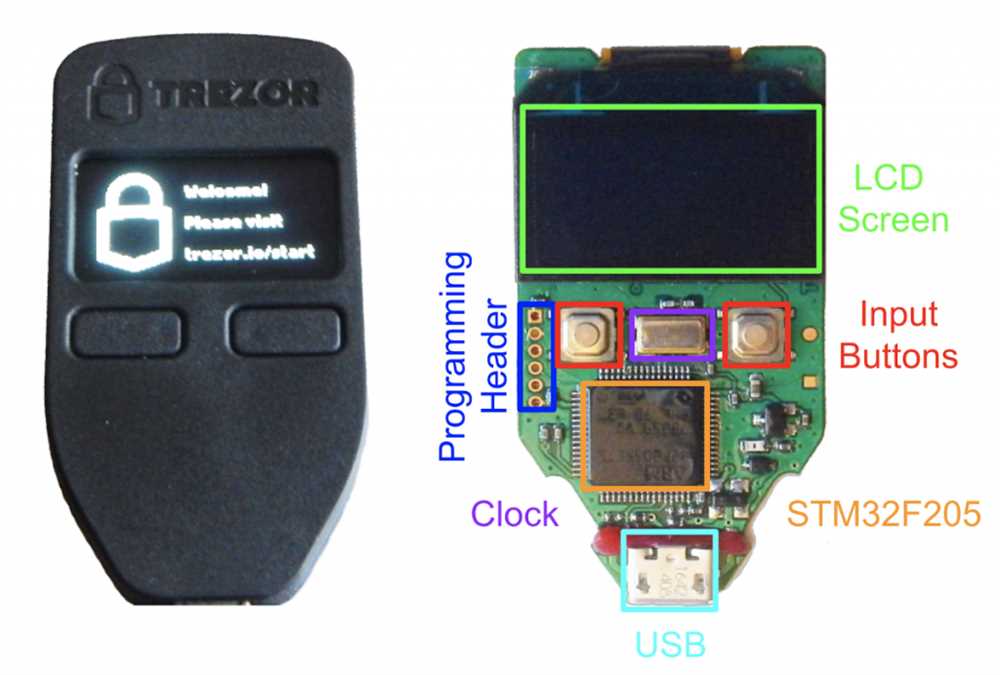
The recent hack of Trezor, one of the most popular hardware wallet models on the market, has exposed serious flaws in the security of these devices, leading to concerns among cryptocurrency investors and experts.
Hardware wallets, like Trezor, are physical devices used to store and secure cryptocurrencies offline, providing an extra layer of protection against hacking and cybercriminals. However, the recent hack has highlighted the potential vulnerabilities of these devices and raised questions about their overall security.
The hack, which was carried out by a group of security researchers, demonstrated how an attacker could exploit the firmware of the Trezor wallet to gain unauthorized access to the private keys and steal the stored cryptocurrencies. This has major implications for users who rely on hardware wallets to safeguard their digital assets.
Although Trezor has taken immediate steps to address the vulnerabilities exposed by the hack and release a fix, this incident serves as a wake-up call for the entire hardware wallet industry. It underscores the need for constant vigilance and ongoing investment in security measures to protect user’s funds.
With the popularity of cryptocurrencies continuing to rise, it is essential that hardware wallet manufacturers prioritize security and regularly update their devices to ensure they are resistant to potential attacks. Wallet users must also stay informed about any new vulnerabilities or potential risks to their funds.
Investors and users of hardware wallets should strongly consider diversifying their storage options and implementing additional security measures, such as using multi-signature wallets or cold storage. It is also crucial to research and choose wallet models that have been thoroughly audited and have a proven track record of security.
This incident has shed light on the importance of robust security practices in the cryptocurrency space. As the industry evolves, it is paramount that users, developers, and manufacturers collaborate to strengthen the security of hardware wallets and ensure the protection of digital assets.
While the Trezor hack has undoubtedly raised concerns about the security of hardware wallets, it also presents an opportunity for the industry to learn and improve. By taking this incident seriously and working towards enhanced security measures, hardware wallet manufacturers can regain trust and continue to provide secure solutions for cryptocurrency users.
Overall, the Trezor hack serves as a stark reminder that no security system is invulnerable. It is a wake-up call for both users and manufacturers to prioritize security and stay at the forefront of developments in the ever-evolving landscape of cryptocurrency.
Popular hardware wallet models were found to have serious flaws

Recently, a Trezor hack has exposed significant flaws in popular hardware wallet models, raising concerns among cryptocurrency users. Trezor is one of the leading manufacturers of hardware wallets, which are considered to be one of the safest ways to store cryptocurrencies.
However, the hack revealed vulnerabilities in the firmware of Trezor devices and raised questions about the security of other popular hardware wallet models.
The flaw allowed attackers to exploit the devices’ weaknesses and gain unauthorized access to users’ private keys, potentially compromising their cryptocurrency holdings. This has led to concerns among users who had placed their trust in these hardware wallets for secure storage.
Hardware wallets are designed to provide an added layer of security by storing private keys offline, away from potential online threats. They are often praised for their tamper-resistant design and strong encryption algorithms.
Despite these qualities, the recent hack has shown that even the most reputable hardware wallet manufacturers are not immune to vulnerabilities. It serves as a reminder that no system is entirely foolproof and that users should remain vigilant in protecting their digital assets.
The Trezor hack has prompted both the manufacturer and the wider cryptocurrency community to reassess the security measures employed in hardware wallet models. It is expected that firmware updates and enhanced security features will be implemented to address the vulnerabilities highlighted by the hack.
Overall, this incident highlights the importance of staying informed about the latest security developments in the cryptocurrency industry and taking necessary precautions to safeguard investments. Cryptocurrency users are advised to regularly update their firmware and follow best practices for securing their private keys to minimize the risk of unauthorized access.
As the popularity of cryptocurrencies continues to grow, it is crucial that hardware wallet manufacturers strive to improve the security of their products and ensure that users’ assets are adequately protected against potential threats.
In conclusion, the recent Trezor hack has shed light on the vulnerabilities present in popular hardware wallet models. While hardware wallets are generally considered secure, this incident serves as a reminder that no system is completely immune to flaws. It emphasizes the need for continuous improvement and vigilance in the realm of cryptocurrency security.
The risks of using vulnerable hardware wallets
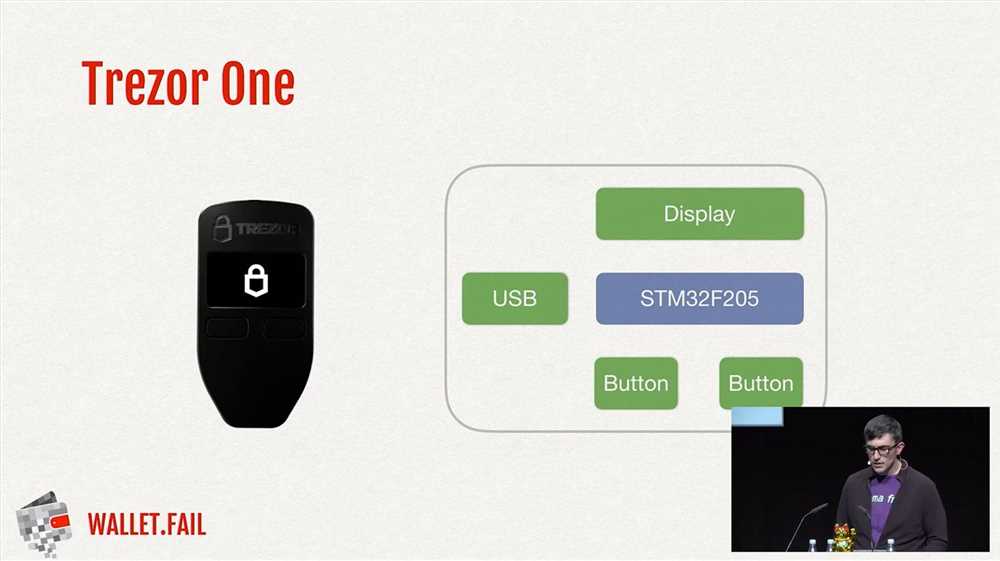
Hardware wallets are often considered to be one of the most secure ways of storing cryptocurrencies. However, recent incidents such as the Trezor hack have highlighted the inherent risks associated with using vulnerable hardware wallets. These risks can have significant consequences for cryptocurrency owners and warrant careful consideration.
1. Unauthorized access to funds

One of the primary risks of using a vulnerable hardware wallet is the potential for unauthorized access to funds. If a wallet’s security measures are compromised, attackers can gain control of the private keys used to access and transfer cryptocurrencies. This can result in the loss of funds and complete ownership over a user’s digital assets.
While hardware wallet manufacturers implement various security measures, vulnerabilities in their design or software can provide opportunities for attackers to exploit. Therefore, it is crucial to choose a hardware wallet from a reputable manufacturer that regularly updates and patches security vulnerabilities.
2. Physical tampering
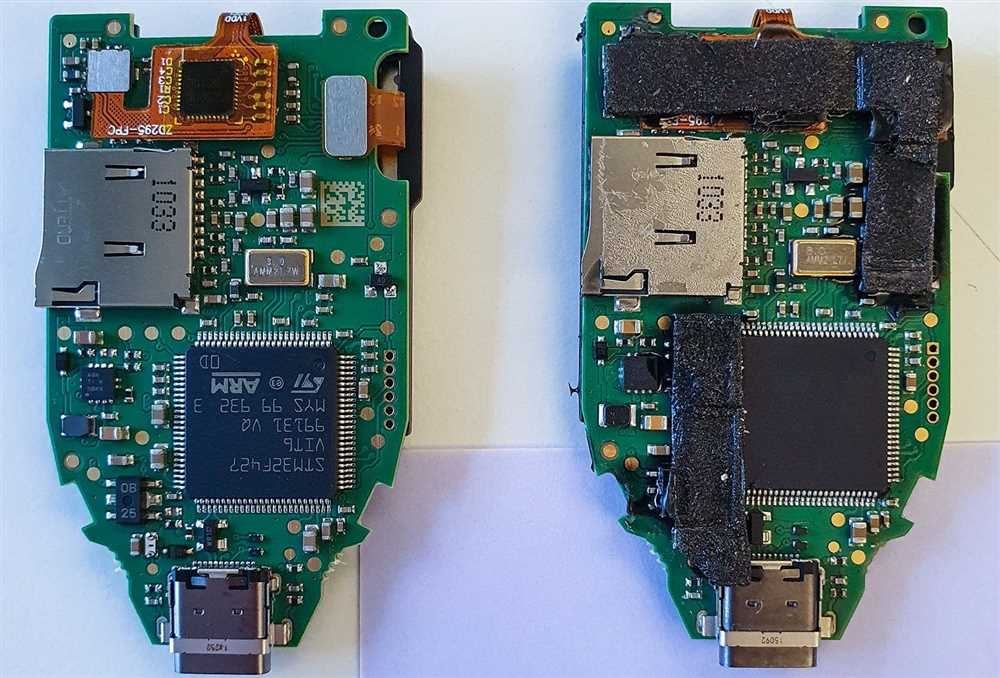
Physical tampering is another risk associated with using vulnerable hardware wallets. If an attacker gains physical access to a wallet, they may attempt to tamper with its components to gain unauthorized access to the private keys. This can be done by modifying the wallet’s hardware or installing malicious software onto it.
Preventing physical tampering requires keeping the hardware wallet in a secure location and regularly checking for any signs of tampering. In addition, it is important to purchase hardware wallets from trusted sources to minimize the risk of receiving a compromised device.
In conclusion, while hardware wallets provide an extra layer of security for cryptocurrency owners, they are not immune to vulnerabilities. Users should be aware of the risks associated with using vulnerable hardware wallets and take the necessary precautions to protect their funds.
Users’ cryptocurrencies could be compromised
In light of the recent Trezor hack, it has become evident that users’ cryptocurrencies could be compromised if they are not taking the necessary precautions. Hardware wallets have long been hailed as a secure option for storing cryptocurrencies, but this incident raises concerns about their reliability.
The hack exposed flaws in popular hardware wallet models, such as the Trezor One and Trezor Model T, which are widely used by cryptocurrency enthusiasts. These vulnerabilities allowed attackers to gain unauthorized access to users’ funds, potentially resulting in significant financial losses.
One of the main issues uncovered during the hack was the lack of robust security measures implemented in these hardware wallets. While they are designed to protect private keys from being exposed to the internet, they still rely on a user interface to initiate transactions, which opens up the possibility for attackers to intercept sensitive information.
Furthermore, the Trezor hack highlighted the importance of regularly updating firmware and security patches. The exploited vulnerabilities in the hardware wallets had already been patched in newer firmware versions, but many users had not updated their devices, leaving them vulnerable to attack.
It is imperative for cryptocurrency users to stay vigilant and keep up with the latest security recommendations. This includes using additional layers of security, such as multi-factor authentication, and regularly reviewing and updating firmware on hardware wallets. Moreover, it is crucial to only purchase hardware wallets from reputable sources to minimize the risk of counterfeit devices.
While hardware wallets still offer a higher level of security compared to other storage options, this incident serves as a reminder that they are not infallible. Users must be proactive in implementing security measures to protect their cryptocurrencies and stay informed about potential vulnerabilities in their chosen wallet models.
In conclusion, the recent Trezor hack has exposed the potential risks associated with using hardware wallets. Users’ cryptocurrencies could be compromised if they do not take the necessary precautions and regularly update their devices’ firmware. It is essential for cryptocurrency enthusiasts to remain vigilant and prioritize security to mitigate the risk of financial losses.
Lessons learned from the Trezor hack

The recent Trezor hack, which exposed flaws in popular hardware wallet models, highlights several important lessons that both cryptocurrency investors and wallet manufacturers should keep in mind.
First and foremost, this incident serves as a reminder that no hardware wallet is completely immune to hacking. While hardware wallets are generally considered to be one of the most secure ways to store cryptocurrencies, this hack shows that vulnerabilities can exist even in the most trusted models.
Additionally, the Trezor hack highlights the importance of regularly updating firmware and software. In this case, the hack was made possible due to a security vulnerability that had already been patched in a newer version of the firmware. By not updating their devices to the latest firmware, users left themselves vulnerable to attacks.
Furthermore, the hack emphasizes the need for multi-factor authentication. While hardware wallets provide an extra layer of security, combining them with other authentication methods, such as strong passwords or biometric identification, can further protect against unauthorized access.
Another lesson to be learned is the importance of conducting thorough security audits. The Trezor hack revealed a vulnerability that could have been identified and fixed earlier through a comprehensive security review. Wallet manufacturers should regularly assess and improve their security measures to stay ahead of potential hackers.
Lastly, users must be vigilant and exercise caution when using their hardware wallets. The Trezor hack involved a sophisticated phishing attack, where hackers created a convincing replica of the official Trezor website to trick users into entering their wallet information. By always double-checking website URLs and being wary of suspicious links or emails, users can help protect themselves from such attacks.
In conclusion, the Trezor hack serves as a powerful reminder that even the most secure hardware wallets can have vulnerabilities. By staying informed, regularly updating firmware, implementing multi-factor authentication, conducting security audits, and practicing caution, users and manufacturers can enhance the security of their cryptocurrency wallets.
Importance of thorough security audits for hardware wallet manufacturers

Security audits play a crucial role in ensuring the integrity and trustworthiness of hardware wallets. With the recent Trezor hack exposing flaws in popular hardware wallet models, it is imperative for manufacturers to conduct thorough security audits to identify and address vulnerabilities.
Hardware wallets are designed to securely store cryptocurrencies by keeping the private keys offline and away from potential hackers. However, as the Trezor hack demonstrated, even the most trusted and widely used hardware wallets can have vulnerabilities.
Thorough security audits help manufacturers identify any potential weaknesses in their hardware wallets and enable them to implement necessary measures to enhance their security. These audits involve comprehensive assessments of the hardware, firmware, and software components of the wallet, as well as the overall system architecture.
During security audits, manufacturers can evaluate the effectiveness of the cryptographic algorithms used in the hardware wallet and ensure they are resistant to attacks. They can also assess the physical security measures implemented in the design, such as tamper-evident seals or secure elements, to prevent unauthorized access to the private keys.
Furthermore, security audits can help identify any flaws in the firmware and software components of the hardware wallet. Manufacturers can test the wallet’s resistance to malware and hacking attempts and identify any potential vulnerabilities that could compromise the security of the private keys.
By conducting thorough security audits, manufacturers can assure their customers that their hardware wallets have undergone rigorous testing and meet high-security standards. This can help build trust in the product and attract more users to adopt hardware wallets as a secure means of storing their cryptocurrencies.
In addition to conducting initial security audits, manufacturers should also regularly update and audit their hardware wallets as new vulnerabilities and attack vectors emerge. This proactive approach is essential for maintaining the security of the wallets and protecting the funds of the users.
In conclusion, the recent Trezor hack highlights the importance of thorough security audits for hardware wallet manufacturers. By conducting regular audits and addressing vulnerabilities, manufacturers can enhance the security and integrity of their products, instill trust in their customers, and contribute to the widespread adoption of hardware wallets as a safe storage solution for cryptocurrencies.
Q&A:
What is Trezor hack?
Trezor hack refers to the breach of security in popular hardware wallets known as Trezor, resulting in the exposure of vulnerabilities within these models.
How did the Trezor hack occur?
The Trezor hack occurred due to the discovery of a vulnerability in the Trezor hardware wallet models, which allowed hackers to exploit weaknesses in the device’s security system.


