
Evaluating the Risks of Malware Infecting Trezor’s Private Keys

In today’s digital age, the security of our cryptocurrencies is of utmost importance. As more and more individuals and businesses turn to hardware wallets like Trezor to store their private keys, the potential risks associated with malware attacks on these devices become a growing concern.
Trezor, one of the leading hardware wallet providers, boasts a strong track record of security. However, no system is completely immune to attacks, and it is crucial to evaluate the risks to understand the potential vulnerabilities.
Malware, a malicious software designed to gain unauthorized access or cause damage to a computer system, can pose a threat to Trezor devices. If a user’s computer becomes infected with malware, it could potentially intercept the communication between the user’s computer and the Trezor wallet, enabling hackers to tamper with or steal the private keys.
While the chance of malware infecting Trezor’s private keys is relatively low, it is essential to take precautions to minimize the risk even further. Regularly updating both the firmware of the Trezor device and the software on the user’s computer is crucial to ensure that any known vulnerabilities are patched.
Evaluating the Risks: Can Malware Infect Trezor’s Private Key?
When it comes to securing your cryptocurrency holdings, a hardware wallet like Trezor is an excellent choice. With its strong encryption and offline storage, it offers a high level of protection against cyber threats. However, no security measure is foolproof, and it’s important to evaluate the potential risks.
One of the main concerns is that malware could infect your Trezor device and compromise your private key. Malware refers to malicious software that can infiltrate your computer or hardware wallet, allowing hackers to gain unauthorized access to your sensitive information.
While the chances of malware infecting a Trezor device are relatively low, it’s not entirely impossible. Cybercriminals are constantly coming up with new ways to bypass security measures and exploit vulnerabilities. Therefore, it’s crucial to stay vigilant and take necessary precautions to minimize the risks.
To evaluate the risks, let’s take a closer look at the potential attack vectors:
| Attack Vector | Description | Risk Level |
|---|---|---|
| Physical Compromise | If someone gains physical access to your Trezor device, they may be able to install malware or tamper with the hardware to intercept your private key. | High |
| Supply Chain Attacks | Malicious actors may compromise the supply chain and inject malware into the device during the manufacturing or distribution process. | Moderate |
| Phishing Attacks | Hackers may trick users into revealing their private key by mimicking legitimate Trezor websites or using social engineering techniques. | Low |
| Software Vulnerabilities | Unpatched software or firmware vulnerabilities in the Trezor device could potentially be exploited by malware. | Low |
To mitigate these risks, it’s crucial to follow these best practices:
- Only purchase Trezor devices from authorized and trusted sources to minimize the risk of supply chain attacks.
- Regularly update the device’s firmware and software to patch any known vulnerabilities.
- Never enter your recovery seed or private key on an insecure website or unfamiliar computer.
- Enable two-factor authentication and use strong, unique passwords for all your accounts.
- Keep your Trezor device in a secure location and avoid using it on public computers or untrusted networks.
By following these guidelines and staying informed about the latest security practices, you can significantly reduce the risk of malware infecting your Trezor device and compromising your private key. Remember, investing in the security of your cryptocurrency is crucial for safeguarding your hard-earned funds.
The Importance of Securing Private Keys
Private keys are a fundamental component of secure cryptocurrency storage, and their protection is of utmost importance. Private keys are used to authenticate transactions and access digital assets, making them a prime target for hackers and malicious actors.
When it comes to storing private keys, it is crucial to adopt best practices to minimize the risk of theft or compromise. One such best practice is using a hardware wallet, like Trezor, which provides an extra layer of security by keeping the private keys offline and away from potential online attacks.
Securing private keys also involves safeguarding them from physical threats, such as loss or damage. Making multiple copies and storing them in secure locations, like a safe deposit box, can help prevent the loss of valuable private keys.
Furthermore, it is essential to keep private keys confidential and avoid sharing them with anyone. Sharing or exposing private keys increases the risk of unauthorized access and potential theft.
To enhance the security of private keys, it is advisable to use strong passwords and enable additional authentication methods, such as two-factor authentication. Implementing these measures adds an extra layer of protection and makes it harder for attackers to gain unauthorized access.
In conclusion, securing private keys is crucial for the safety and integrity of cryptocurrency holdings. By utilizing hardware wallets, practicing physical security measures, keeping keys confidential, and implementing strong passwords with additional authentication, users can significantly reduce the risk of malware infections and unauthorized access to private keys.
Potential Vulnerabilities in Trezor’s Security
While Trezor is generally considered one of the most secure hardware wallets in the market, there are a few potential vulnerabilities that users should be aware of:
1. Physical Tampering
One potential vulnerability in Trezor’s security lies in the physical tampering of the device. If an attacker gains physical access to the device, they may attempt to extract the private keys stored within it. Users should be cautious about leaving their Trezor device unattended or in the hands of unauthorized individuals.
2. Supply Chain Attacks
Another possible vulnerability is the risk of supply chain attacks. In this scenario, an attacker may compromise the security of a Trezor device during the manufacturing or distribution process. This could involve injecting malware or tampering with the device’s components, allowing the attacker to gain unauthorized access to the private keys. Users should only purchase Trezor devices from trusted and reputable sources to mitigate this risk.
It is important to note that while these vulnerabilities exist, they are not easily exploitable in practice. Trezor has implemented various security measures to protect against these threats, including secure chip technology, encryption, and firmware updates.
However, it is crucial for users to stay vigilant and take necessary precautions to ensure the security of their private keys and funds stored on Trezor wallets. This includes regularly updating firmware, enabling additional security features such as passphrase protection, and following best practices for handling and storing the device.
Protecting Against Malware Attacks
In order to protect against malware attacks and keep your Trezor private keys secure, it is important to follow certain best practices:
1. Keep Your Devices Up to Date

Regularly update the firmware and software on your devices, including your computer, smartphone, and Trezor hardware wallet. Updates often include security patches that can protect against known vulnerabilities and exploits.
2. Only Install Trusted Software

Be cautious when downloading and installing software onto your devices. Stick to reputable sources such as official app stores and the Trezor website. Avoid downloading software from unknown websites or clicking on suspicious links.
3. Use Reliable Antivirus and Antimalware Software
Install and regularly update antivirus and antimalware software on your devices. These programs can help detect and remove malicious software before it has a chance to infect your device.
4. Enable Two-Factor Authentication

Two-factor authentication adds an extra layer of security to your accounts by requiring a second form of verification. Enable this feature on all platforms and services that support it, including your Trezor wallet.
5. Be Mindful of Phishing Attempts
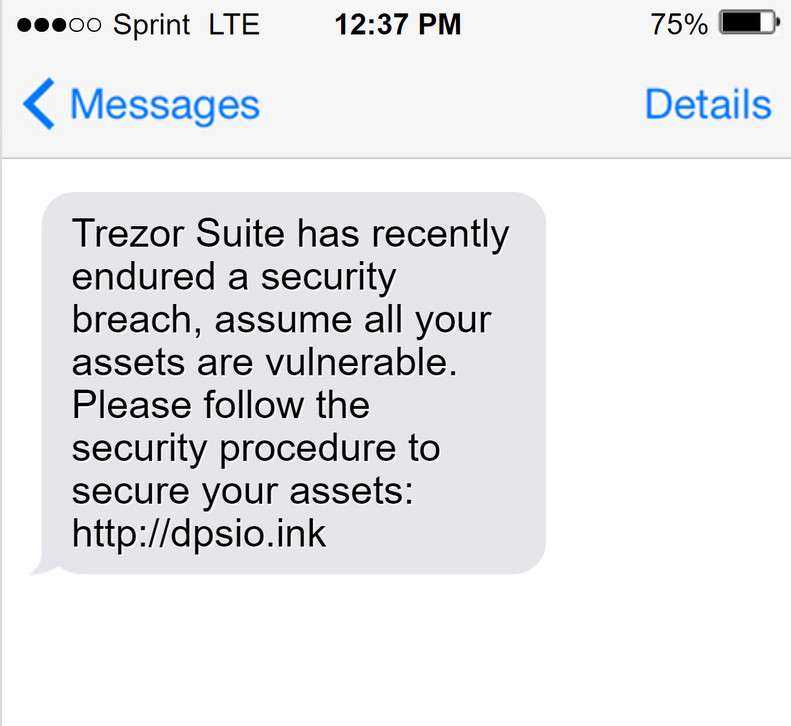
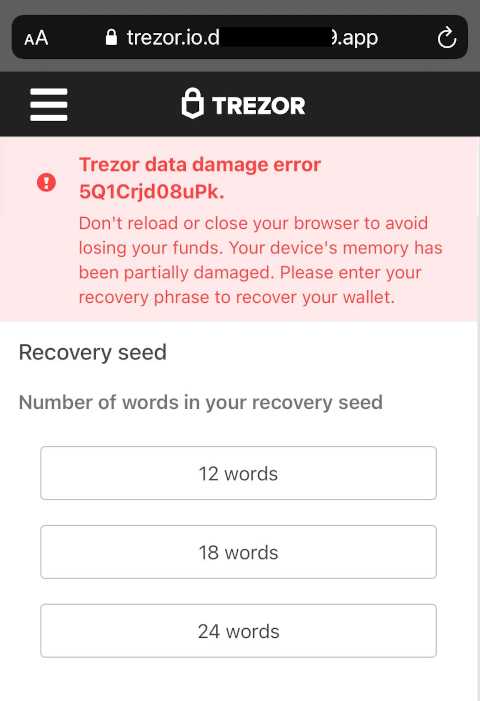
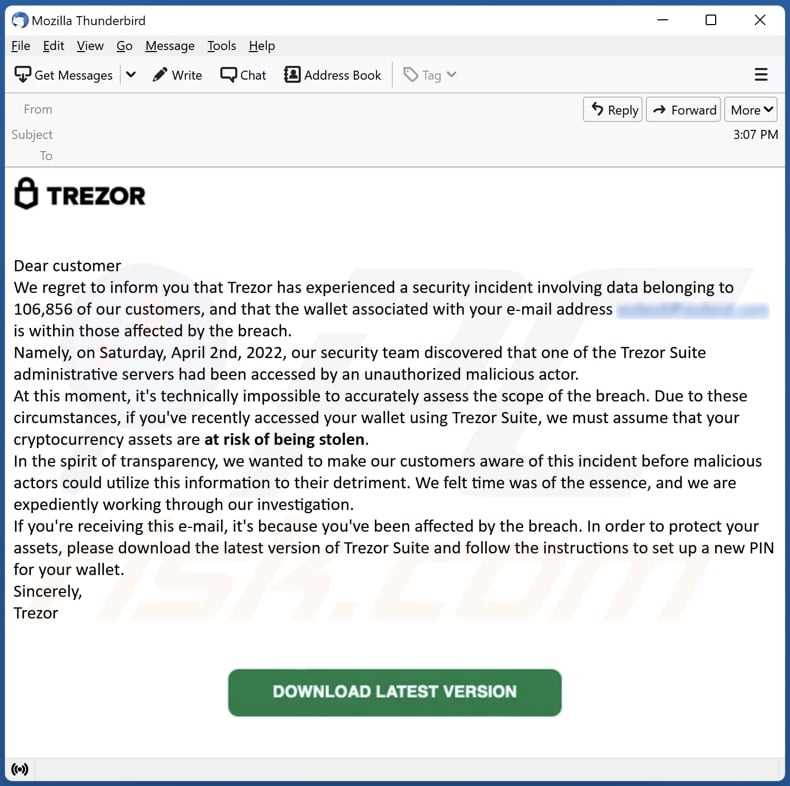
Be wary of emails, messages, or websites that ask for personal information, including your Trezor private keys. Legitimate organizations will never ask for this information. Always double-check the legitimacy of any requests before providing any sensitive data.
By following these best practices, you can significantly reduce the risk of malware infecting your Trezor private keys and ensure the security of your cryptocurrency investments.
Q&A:
What is Trezor?
Trezor is a popular hardware wallet that is used for storing private keys to cryptocurrencies. It provides an extra layer of security by keeping the private keys offline, away from potential malware attacks.
How does Trezor protect against malware attacks?
Trezor protects against malware attacks by keeping the private keys offline. The private keys are stored and encrypted on the device itself, which means they are not exposed to the internet or vulnerable to malware infections. However, it is important to note that malware can still infect the computer used to interact with Trezor, so it is important to ensure that the computer is secure and free from malware infections.
Can malware infect Trezor’s private keys?
No, malware cannot infect Trezor’s private keys. Trezor uses advanced encryption techniques to store the private keys securely on the device itself. Even if malware infects the computer used to interact with Trezor, it will not be able to access or steal the private keys stored on the device.
What are the risks of malware infecting Trezor?
The risks of malware infecting Trezor primarily lie in the computer used to interact with the device. If the computer is infected with malware, it could potentially capture the data entered on the device, such as the PIN or passphrase, and use that information to gain unauthorized access to the private keys stored on the device. It is therefore important to ensure that the computer used with Trezor is secure and free from malware infections.


