
Can Your Trezor Be Hacked? Unveiling the Truth

In today’s digital age, securing our cryptocurrencies is of utmost importance. With the rise in popularity of cryptocurrencies like Bitcoin and Ethereum, more and more people are turning to hardware wallets like Trezor to keep their digital assets safe. But, just how secure is your Trezor wallet?
Many individuals and companies claim that Trezor wallets are unhackable, boasting about their top-notch security features. However, recent studies and security tests have raised concerns about the vulnerability of these hardware wallets. Hackers are constantly evolving their techniques, and it’s crucial that we stay informed about the potential risks involved in using a Trezor wallet.
One of the main reasons why Trezor wallets have gained such a loyal following is their use of offline storage, also known as cold storage. This means that your private keys are stored on a device disconnected from the internet, making it virtually impossible for hackers to gain access. But, is it really foolproof? Can a determined hacker still find a way to infiltrate your Trezor wallet?
In this article, we will explore the latest research and real-life examples to uncover the truth about the security of Trezor wallets. We will discuss the potential vulnerabilities and examine the best practices to ensure the safety of your cryptocurrencies. Stay tuned as we delve into the fascinating world of digital security and hacking!
Understanding the Security of Trezor Wallets
When it comes to securing your cryptocurrency, the Trezor wallet is often regarded as one of the safest options available. Trezor wallets utilize a combination of hardware and software features to ensure the highest level of security for your digital assets.
Hardware Security

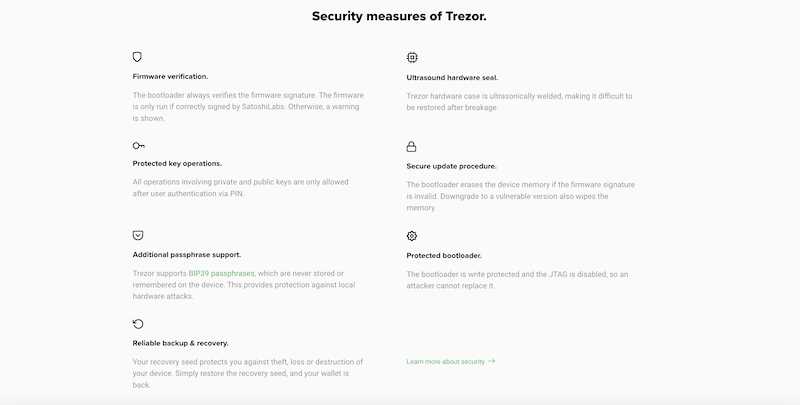
A key aspect of the Trezor wallet’s security is its hardware design. The device itself is tamper-proof and equipped with a secure chip that protects your private keys. This means that even if the device is physically compromised, your private keys remain safe from unauthorized access.
Furthermore, Trezor wallets have a built-in display that allows you to verify transaction details before approving them. This feature ensures that you have full control over your transactions and can prevent any potential mistakes or malicious attempts.
Software Security
In addition to its robust hardware security, the Trezor wallet also employs several software security measures. The wallet’s firmware is open-source, meaning it has been thoroughly reviewed by the community to identify and address any vulnerabilities.
Moreover, Trezor wallets use a unique recovery seed system. When setting up the wallet, you are provided with a 24-word recovery seed. This seed serves as a backup that can be used to restore your wallet in case of loss, damage, or theft.
Additionally, the Trezor wallet is compatible with various software wallets and supports multiple cryptocurrencies. This versatility allows you to securely manage and store a wide range of digital assets in one place.
It is important to note that while the Trezor wallet provides robust security measures, no system is completely immune to hacking or user error. Users should always exercise caution and follow best practices in securing their wallets, such as keeping their recovery seed offline and using strong, unique passwords.
In conclusion, Trezor wallets offer a high level of security through their combination of hardware and software features. By understanding and utilizing these security measures, users can have peace of mind knowing that their cryptocurrencies are protected.
Common Hacking Techniques and Their Impact on Trezor Wallets
In today’s digital world, the security of our cryptocurrencies is of utmost importance. Trezor wallets have gained popularity among crypto enthusiasts due to their strong security features. However, it is essential to understand the common hacking techniques that can potentially compromise the safety of these wallets and the impact they might have.
1. Phishing Attacks

Phishing attacks are one of the most prevalent hacking techniques targeting crypto wallet users. Hackers create fake websites or emails that mimic the official Trezor site or support teams to deceive users into revealing their private keys or recovery seeds. This information can be used by hackers to gain unauthorized access to wallets and steal funds.
2. Malware and Keyloggers

Malware and keyloggers are another significant threat to Trezor wallets. These malicious software or scripts can be unknowingly installed on a user’s computer or mobile device. They can track keystrokes, capture screen contents, and even modify or replace addresses during transactions. This allows hackers to intercept sensitive information, such as private keys or passwords, compromising the security of the wallet.
3. Man-in-the-Middle Attacks
Man-in-the-middle attacks occur when hackers intercept communication between a user’s device and the Trezor wallet. Through various techniques like Wi-Fi spoofing or DNS hijacking, attackers can redirect the user’s connection to a fake wallet interface controlled by them. This enables them to manipulate transactions and gain unauthorized access to the wallet.
4. Seed Phrase Vulnerabilities

The seed phrase (recovery seed) is a crucial aspect of Trezor wallet security. However, if not handled properly, seed phrases can become vulnerable to hacking. This includes storing the seed phrase in digital or cloud-based platforms, sharing it with others, or even taking screenshots. If a hacker gains access to the seed phrase, they can easily restore the wallet and gain control over the funds.
5. Physical Attacks

Although Trezor wallets provide robust security against digital threats, physical attacks can still pose a risk. If an attacker gains physical access to the device, they may try various methods, such as tampering with the wallet or extracting the memory chip, to retrieve sensitive information. It is crucial to keep the physical wallet secure and never leave it unattended.
It is important for Trezor wallet users to remain vigilant and take necessary precautions to protect their digital assets. Understanding these common hacking techniques and their potential impacts can help users implement additional security measures and minimize the risks involved.
Protecting Your Trezor Wallet from Hacking Attempts
As the security of your cryptocurrency assets is of utmost importance, taking measures to protect your Trezor wallet from potential hacking attempts is crucial. Here are some steps you can take to enhance the security of your Trezor wallet:
1. Set Up a Strong Password: When setting up your Trezor wallet, ensure that you choose a strong and unique password. Avoid using common words or combinations and instead opt for a combination of uppercase and lowercase letters, numbers, and special characters.
2. Enable Two-Factor Authentication (2FA): Adding an extra layer of security through 2FA can significantly reduce the risk of unauthorized access to your Trezor wallet. Enable 2FA on your Trezor device and make sure to use a reliable and secure 2FA authentication app.
3. Keep Your Firmware Up to Date: Regularly updating the firmware of your Trezor wallet is essential, as it helps fix any identified vulnerabilities and ensures the highest level of security. Keep an eye out for firmware updates and promptly install them.
4. Verify Addresses on the Device Display: Always verify the addresses displayed on your Trezor device before confirming transactions. This is important to prevent any Man-in-the-Middle attacks or tampering with the addresses by hackers. Confirm the addresses visually and double-check them with the recipient before proceeding.
5. Beware of Phishing Attempts: Be cautious when opening email attachments or clicking on suspicious links related to your Trezor wallet. Hackers often use phishing techniques to trick users into revealing their wallet information. Always double-check the sender’s email address and verify the authenticity of the communication before taking any action.
6. Store Your Recovery Seed Securely: The recovery seed of your Trezor wallet is crucial for restoring access to your funds in case of loss or theft. Make sure to store it safely in a secure location, preferably offline, and avoid sharing it with anyone.
7. Consider a Passphrase: Adding a passphrase to your Trezor wallet offers an additional layer of security. It acts as a second password, making it harder for hackers to gain unauthorized access to your funds. Choose a strong and unique passphrase and remember to store it in a safe place.
By following these security measures, you can significantly reduce the risk of your Trezor wallet being hacked. Remember, being vigilant and proactive in safeguarding your cryptocurrency assets is key to maintaining their security.
Question-Answer:
Can a Trezor wallet be hacked?
While Trezor wallets are generally considered to be very secure, no system is completely immune to hacking. However, the chances of a Trezor wallet being hacked are extremely low and require a significant amount of effort and knowledge on the part of the hacker.
What security measures does Trezor take to protect its wallets?
Trezor implements various security measures to protect its wallets, including a PIN code, passphrase encryption, two-factor authentication, and a recovery seed. These measures are designed to keep your private keys safe and make it extremely difficult for hackers to gain access to your funds.
Is it safe to use a Trezor wallet for storing cryptocurrencies?
Yes, using a Trezor wallet is generally considered to be safe for storing cryptocurrencies. Trezor wallets are designed with a strong focus on security and have a solid reputation in the crypto community. However, it’s always important to follow best practices and ensure that you’re using the latest firmware version to minimize any potential risks.
Can a hacker remotely access my Trezor wallet?
No, it’s highly unlikely for a hacker to remotely access your Trezor wallet. Trezor wallets are designed to be offline hardware wallets, meaning they are not continuously connected to the internet. This greatly reduces the risk of remote hacking attempts.
What should I do if I suspect my Trezor wallet has been compromised?
If you suspect that your Trezor wallet has been compromised, the first step is to disconnect it from your computer immediately. Then, you should contact Trezor support for assistance in securing your funds and investigating the potential breach. It’s also important to monitor your account for any unauthorized transactions and take appropriate action to protect your assets.


