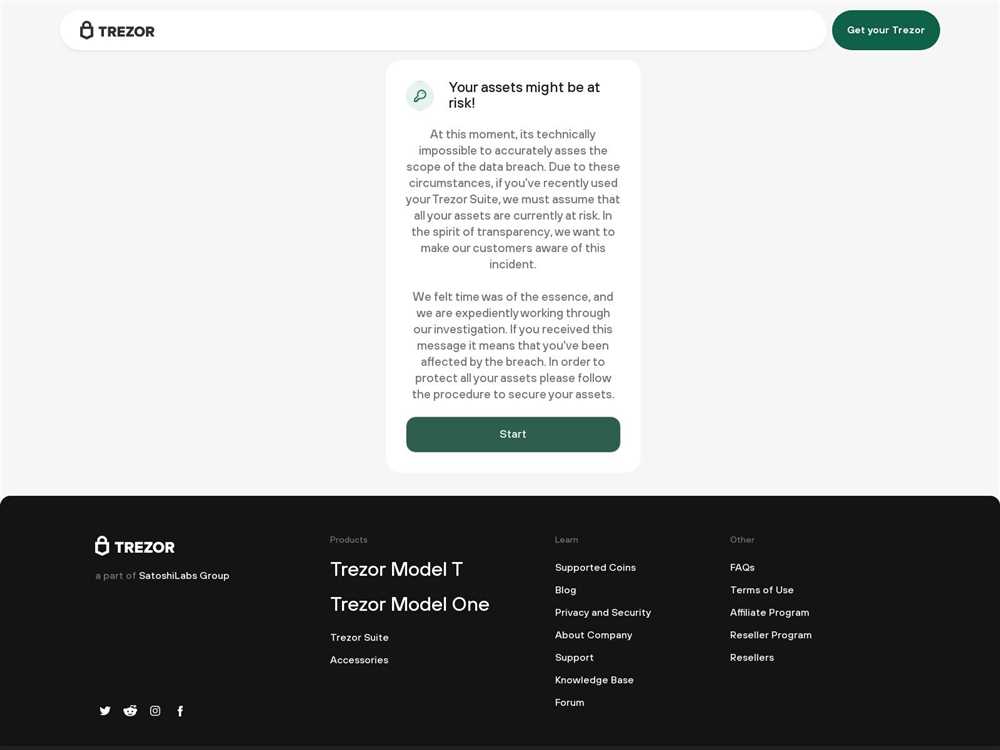
Can Trezor Crypto Wallet Be Compromised by Malicious Software?

In the fast-paced world of cryptocurrency, security is of the utmost importance. One small vulnerability can lead to devastating consequences for crypto holders. Trezor, a popular hardware wallet, has been regarded as one of the safest options for storing digital assets. However, recent research has uncovered potential vulnerabilities that could put users at risk of malware attacks.
Malware attacks have become increasingly sophisticated, targeting both individuals and organizations. These attacks involve the use of malicious software to gain unauthorized access to sensitive information, such as private keys or passwords. With the rise of cryptocurrency, hackers are now turning their attention towards targeting crypto users.
Trezor’s vulnerability to malware attacks lies in its firmware update process. Researchers have discovered that attackers can exploit this process to inject malicious code into the device, compromising the security of the wallet. Once the malware is injected, hackers can gain access to the user’s private keys and steal their crypto assets.
As a Trezor user, it is crucial to stay proactive in defending your crypto. One way to mitigate the risk of malware attacks is to always verify the authenticity of firmware updates. Trezor recommends using their official website or their desktop app, rather than relying on third-party sources. Additionally, keep an eye out for any unusual behavior or prompts during the update process, as these could be indicators of a potential malware attack.
Furthermore, it is essential to only download apps and extensions from trusted sources. Malware attacks often disguise themselves as legitimate software, so it is crucial to research and verify the source before installing anything related to your Trezor device. Remember to keep your computer and antivirus software up to date to ensure you are protected against the latest malware threats.
While Trezor remains a secure option for storing cryptocurrencies, it is important to be aware of the potential vulnerabilities and take the necessary precautions to safeguard your assets. By staying vigilant and implementing the recommended security measures, you can defend your crypto against malware attacks and enjoy the peace of mind that comes with knowing your digital assets are safe.
Understanding Trezor’s Vulnerability

In the world of cryptocurrency, security is paramount. Investors and traders rely on secure hardware wallets to store their digital assets. One such hardware wallet is Trezor, known for its robust security measures and ease of use. However, even the most secure devices can have vulnerabilities that hackers can exploit.
Trezor’s vulnerability lies in its susceptibility to malware attacks. Malware, or malicious software, can infect a user’s computer and compromise the security of their Trezor wallet. This can lead to theft of cryptocurrency funds and other malicious activities.
The main reason Trezor is vulnerable to malware attacks is its reliance on a computer or mobile device for transactions. When a user connects their Trezor wallet to a compromised computer, the malware can intercept and manipulate the data exchanged between the wallet and the computer. This can allow hackers to steal private keys or tamper with transaction details.
To mitigate this vulnerability, Trezor recommends several best practices. First, users should always verify the integrity of their Trezor device by checking for tampering signs before every use. Additionally, users should enable the passphrase feature, which adds an extra layer of security by requiring a unique passphrase to access the wallet.
Another important step in protecting against malware attacks is to ensure that the computer or mobile device used for transactions is secure. This includes regularly updating software and using antivirus programs to detect and remove malware. It is also crucial to be cautious about downloading and installing software from untrusted sources.
While Trezor’s vulnerability to malware attacks poses a risk, it is important to note that the company is actively working to improve the security of its devices. Regular firmware updates and bug bounty programs are part of their ongoing efforts to stay one step ahead of hackers.
Overall, understanding Trezor’s vulnerability to malware attacks is essential for anyone who uses a Trezor wallet to store their cryptocurrency. By following best practices and staying vigilant, users can greatly reduce the risk of falling victim to these types of attacks and ensure the safety of their digital assets.
How Malware Attacks Can Compromise Your Crypto

Malware attacks are a serious threat to the security of your cryptocurrency. These malicious programs can find their way onto your devices through various channels, such as phishing emails, fake websites, or compromised downloads.
Once malware infects your device, it can perform a range of damaging actions that put your crypto funds at risk. Here are some common ways malware can compromise your crypto:
Keyloggers

Keyloggers are a type of malware that secretly records every keystroke you make, including your cryptocurrency wallet passwords or private keys. By capturing this sensitive information, keyloggers enable attackers to gain unauthorized access to your crypto wallets and steal your funds.
Screen Recorders

Malware can also include screen recording capabilities, allowing hackers to capture your actions on the screen, such as entering your wallet credentials or making transactions. By monitoring your activities, attackers can obtain the information they need to hijack your crypto accounts.
Clipboard Hijackers

Clipboard hijackers are malware that can replace the content of your clipboard with their own malicious code. If you copy and paste your crypto wallet address, the malware can alter it to a different address owned by the attackers. As a result, when you initiate a transaction, your funds may end up in the wrong hands.
In addition to these specific tactics, malware can also compromise the security of your crypto by monitoring your online activities, stealing sensitive information from your computer or mobile device, or even launching ransomware attacks.
To protect yourself from malware attacks and safeguard your crypto, it is crucial to follow best security practices:
- Be cautious of suspicious emails and avoid clicking on unknown links or downloading attachments.
- Always verify the authenticity of websites before entering sensitive information.
- Keep your operating system, antivirus software, and crypto wallets up to date with the latest security patches.
- Use strong, unique passwords for your crypto wallets and enable two-factor authentication whenever possible.
- Regularly scan your devices for malware using reputable antivirus software.
By staying vigilant and taking proactive measures, you can reduce the risk of malware compromising your crypto and ensure the security of your digital assets.
Recognizing the Signs of Malware on Your Trezor

When it comes to securing your cryptocurrencies, it is crucial to be aware of the signs of malware on your Trezor. Malware, short for malicious software, can pose a serious threat to the security of your crypto assets. By recognizing the signs of malware, you can take the necessary steps to protect your funds and prevent unauthorized access to your Trezor.
One of the key indicators of malware on your Trezor is unexpected behavior. If you notice any unusual activity, such as sudden crashes, slow performance, or unresponsive buttons, it may indicate that your device has been compromised. Additionally, if you encounter any unexpected pop-ups or messages requesting you to enter sensitive information, it is essential to exercise caution.
Another sign to watch out for is the presence of unfamiliar apps or files on your device. Malware can disguise itself as legitimate software, so it is crucial to double-check the apps and files installed on your Trezor. If you come across any unfamiliar or suspicious applications, it is best to remove them immediately.
Furthermore, be wary of phishing attempts targeting your Trezor. Phishing is a common tactic used by hackers to trick individuals into revealing their sensitive information. If you receive any suspicious emails, messages, or links claiming to be from Trezor or requesting personal data, do not click on them. Instead, reach out to Trezor’s official support channels to verify the authenticity of the communication.
Regularly updating your Trezor’s firmware is also crucial in detecting and mitigating malware attacks. Manufacturers often release firmware updates to address security vulnerabilities and enhance device performance. By keeping your Trezor up to date, you can ensure that your device is equipped with the latest security features.
Lastly, the use of strong and unique passwords can help protect your Trezor from malware attacks. A strong password should be complex and difficult to guess, and it should never be shared with anyone. Additionally, consider enabling two-factor authentication to add an extra layer of security to your Trezor.
In conclusion, being aware of the signs of malware on your Trezor is essential in safeguarding your cryptocurrency assets. By staying vigilant and taking preventive measures, you can minimize the risk of falling victim to malware attacks and protect your funds. Remember, investing in the security of your Trezor is investing in the security of your crypto assets.
Protecting Your Crypto Against Malware Attacks
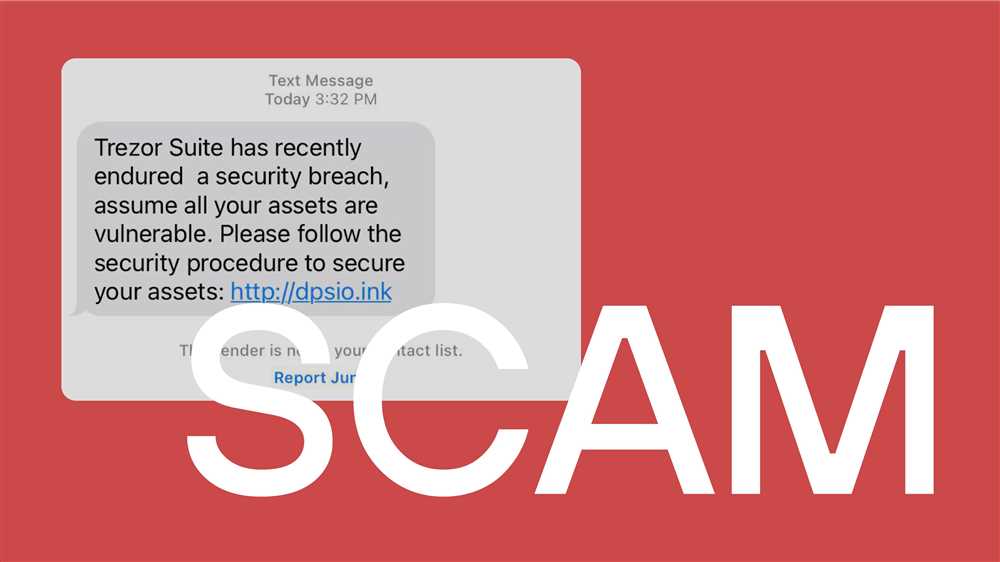
As the popularity of cryptocurrencies continues to grow, so does the risk of malware attacks targeting digital assets. It is crucial to take proactive steps to protect your crypto from these malicious threats. Here are some effective measures you can implement:
1. Use a Hardware Wallet: Hardware wallets like Trezor provide an extra layer of security by storing your private keys offline. This makes it more difficult for malware to access and steal your crypto assets.
2. Keep Your Software Up to Date: Regularly update your operating system, antivirus software, and cryptocurrency wallet applications. These updates often include patches and fixes for vulnerabilities that can be exploited by malware.
3. Exercise Caution When Downloading and Installing Software: Be wary of downloading and installing software from untrusted sources. Stick to reputable websites and double-check the integrity of the files before running them.
4. Enable Two-Factor Authentication (2FA): Implementing 2FA adds an extra layer of protection to your accounts. Even if malware manages to get access to your device, they will need a second factor, such as a unique code sent to your phone, to gain control.
5. Be Mindful of Phishing Attempts: Do not click on suspicious links or provide personal information in response to unsolicited emails or messages. Malware can be spread through phishing attempts that trick users into revealing their private keys or login credentials.
6. Keep Your Crypto Wallet Offline: If you are not actively trading or transacting with your cryptocurrencies, consider keeping them in an offline wallet, also known as a cold wallet. This offline storage protects your crypto from online malware attacks.
By implementing these measures, you can significantly reduce the risk of falling victim to malware attacks and safeguard your valuable cryptocurrencies. Remember, staying vigilant and proactive is key to protecting your digital assets.
Choosing a Secure Storage Solution for Your Crypto

With the increasing popularity and value of cryptocurrencies, it is important to prioritize the security of your digital assets. One crucial step in safeguarding your crypto is to select a secure storage solution. Here are some factors to consider when choosing the right storage option:
1. Hardware Wallets:
An excellent choice for secure cryptocurrency storage is a hardware wallet. These devices store your private keys offline, minimizing the risk of hacking or malware attacks. Examples of popular hardware wallets include Trezor, Ledger, and KeepKey. Make sure to choose a reputable and well-reviewed brand.
2. Multi-Signature Wallets:
Multi-signature wallets require multiple signatures to authorize a transaction, adding an extra layer of security. With this type of wallet, you can involve multiple parties, such as family members or business partners, in the management of your crypto funds. It significantly reduces the risk of unauthorized access.
3. Cold Storage:
Cold storage refers to keeping your cryptocurrency offline, disconnected from the internet. This method provides a high level of security against hacking and online threats. Offline hardware wallets and paper wallets are considered cold storage options.
4. Backups:
Always create regular backups of your wallet’s seed phrase or private key. Store these backups securely in multiple locations, such as a safe deposit box or fireproof safe. Having backups ensures that you can easily recover your crypto assets in case of loss or damage to your primary storage.
5. Security Features:
When evaluating a storage solution, look for additional security features like PIN/password protection, encryption, and two-factor authentication. These features provide an extra layer of protection against unauthorized access and ensure the safety of your crypto.
6. Reputation and Reviews:
Before choosing a storage solution, thoroughly research and read reviews about the product or service. Pay attention to the reputation and track record of the company behind the solution. Look for unbiased opinions and feedback from other crypto users to make an informed decision.
Remember, the security of your cryptocurrency is in your hands. By choosing a secure storage solution and following best practices, you can minimize the risk of theft or loss of your valuable digital assets.
Q&A:
What is Trezor and how does it work?
Trezor is a hardware wallet designed to securely store cryptocurrencies. It works by generating and storing private keys offline, which ensures that they are not exposed to potential online threats.
What are some of the vulnerabilities that Trezor has?
Trezor has been found to be vulnerable to malware attacks. A hacker can use malware to steal the user’s private keys and gain access to their cryptocurrency. Additionally, there have been reports of fake firmware updates being used to trick users into revealing their private keys.


