
Can Hackers Compromise Trezor Hardware Wallet Security?

In today’s world where online threats and cyber attacks are on the rise, the security of our digital assets has become a critical concern. As more people turn to cryptocurrencies as a form of investment and storage of wealth, the need for secure storage solutions has also increased. One such solution is the Trezor hardware wallet, which is widely regarded as one of the most secure options in the market.
However, no system is completely immune to potential security vulnerabilities. Even though Trezor has implemented strong security measures, some experts argue that hackers could potentially compromise the security of the hardware wallet.
One possible attack vector is the physical tampering of the device. Hackers who can gain physical access to the Trezor wallet may attempt to extract sensitive information or even inject malicious code into the hardware. However, Trezor has taken measures to mitigate this risk by implementing tamper-evident seals and secure microcontrollers to detect any unauthorized access.
Another potential vulnerability lies in the software that interacts with the hardware wallet. Hackers could try to exploit software vulnerabilities to gain unauthorized access to the wallet or its contents. To combat this, Trezor regularly releases firmware updates to address any potential security flaws and encourages its users to keep their devices up to date.
Despite these concerns, it’s important to note that no successful compromise of Trezor’s security has been reported so far. The company has built a strong reputation for its commitment to security and has a team of experts constantly working to enhance the system’s defenses. Nevertheless, it is always advisable to stay vigilant and keep abreast of any potential security risks in order to safeguard your digital assets effectively.
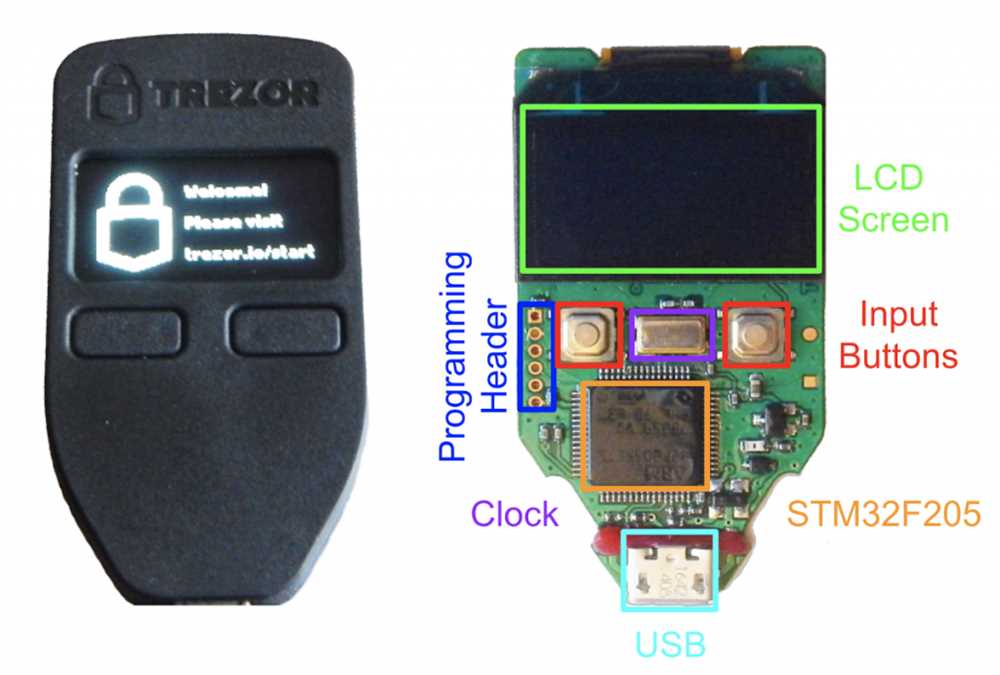
Trezor Hardware Wallet Overview
Trezor is a popular hardware wallet that provides secure storage for cryptocurrencies such as Bitcoin, Ethereum, and more. It is a small device that connects to your computer via USB and is designed to keep your private keys safe.
One of the key features of the Trezor hardware wallet is its ability to generate and store private keys offline, away from the vulnerable environment of your computer or smartphone. This significantly reduces the risk of your private keys being compromised by hackers or malware.
The Trezor hardware wallet uses a combination of advanced cryptography and secure chip technology to protect your private keys. It incorporates a microcontroller that is designed to resist physical tampering and has a built-in screen for securely displaying transaction details.
To access your cryptocurrencies, you need to enter a PIN code on the Trezor device. This adds an extra layer of security, as even if your computer is infected with malware, the hacker would still need physical access to your Trezor and knowledge of your PIN code to steal your funds.
Furthermore, Trezor also supports a feature called “seed recovery,” which allows you to recover your wallet and funds in case your device gets lost or stolen. It provides you with a recovery seed, which is a randomly generated list of words that you can use to restore your wallet on a new device.
Overall, the Trezor hardware wallet is considered a highly secure solution for storing and managing your cryptocurrencies. Its offline private key generation and storage, combined with its advanced security features, make it a trusted choice among cryptocurrency enthusiasts and investors.
Security Features and Encryption Technology
Trezor hardware wallets are equipped with a variety of security features and advanced encryption technology to ensure the safety and integrity of your digital assets.
One of the key security features of Trezor wallets is the implementation of a secure element chip. This chip is responsible for securely storing your private keys and executing cryptographic operations. The secure element is tamper-resistant and provides protection against physical attacks, such as attempts to extract the private keys from the device.
In addition to the secure element, Trezor devices incorporate strong encryption algorithms. The private keys stored on the device are encrypted using AES-256 encryption, which is considered highly secure and widely used in the financial industry.
Trezor wallets also utilize a hierarchical deterministic (HD) wallet structure. This means that each transaction made with the wallet generates a new address, ensuring that your funds are not linked to a single address and providing an additional layer of privacy. The HD wallet structure also allows for easy backup and recovery of your wallet by using a mnemonic seed.
Furthermore, Trezor devices have a built-in display that allows users to verify and confirm transaction details directly on the device. This prevents attackers from manipulating transaction information on a compromised computer or mobile device.
When it comes to firmware updates, Trezor follows a rigorous process to ensure the authenticity and integrity of the updates. The updates are cryptographically signed by the Trezor team, and the device verifies the signature before applying any updates.
In conclusion, Trezor hardware wallets employ multiple layers of security, including a secure element chip, strong encryption algorithms, HD wallet structure, and display verification. Together, these features make it extremely difficult for hackers to compromise the security of a Trezor device and access your digital assets.
Potential Vulnerabilities: Myth vs. Reality
As the popularity of Trezor hardware wallets continues to grow, concerns about their security have also emerged. However, it is important to distinguish between potential vulnerabilities that are often just myths and actual realities. In this section, we will explore some common misconceptions and provide a clear understanding of the true security capabilities of Trezor hardware wallets.
Myth: Physical Compromise of Trezor Wallets is Easy
One of the most common myths surrounding Trezor hardware wallets is that they can be easily compromised physically. While it is true that physical access to the device opens up the possibility of an attack, it is important to note that Trezor’s security measures are designed to protect against physical tampering. The hardware wallets are equipped with specialized security chips that make it extremely difficult for malicious actors to gain access to the private keys stored on the device.
To further enhance security, Trezor wallets also come with a feature called “passphrase protection.” This additional layer of security requires users to enter a unique passphrase that serves as an encryption key. Even if an attacker physically gains access to the device, the passphrase serves as an extra barrier to prevent unauthorized access to the funds.
Myth: Trezor Wallets Are Susceptible to Remote Attacks
Another myth surrounding Trezor hardware wallets is that they are vulnerable to remote attacks. This misconception arises from a misunderstanding of how the wallets operate. Trezor wallets do not connect directly to the internet; instead, they rely on a computer or smartphone as an intermediary for transactions. This reduces the risk of remote attacks as the wallets are not exposed to the internet directly.
Furthermore, Trezor wallets utilize open-source software, allowing security researchers to scrutinize the code for any potential vulnerabilities. Any identified weaknesses are promptly addressed through software updates, ensuring that the wallets remain resilient to evolving threats.
Reality: User-Enabled Vulnerabilities
While Trezor hardware wallets offer robust security against physical and remote attacks, it is important to understand that users can create vulnerabilities unintentionally. For example, if users do not properly store or backup their recovery phrases or fail to enable the passphrase protection feature, their wallet’s security may be compromised. It is crucial for users to follow Trezor’s guidelines and best practices to ensure optimal security.
In conclusion, Trezor hardware wallets have proven to be highly secure, providing users with peace of mind when it comes to safeguarding their cryptocurrencies. By dispelling the myths surrounding potential vulnerabilities, it becomes clear that Trezor wallets offer robust security measures to protect users’ digital assets.
Best Practices to Strengthen Trezor Hardware Wallet Security
Securing your cryptocurrency is of utmost importance, and using a hardware wallet like Trezor can provide an extra layer of protection. However, it is crucial to follow best practices to ensure the highest level of security for your hardware wallet. Here are some recommendations to strengthen the security of your Trezor hardware wallet:
1. Purchase from a Trusted Source
Always buy your Trezor hardware wallet from an authorized and reputable source. Avoid purchasing from third-party sellers or unknown sources, as they might sell counterfeit or tampered devices.
2. Verify the Authenticity

After receiving your Trezor hardware wallet, verify its authenticity by ensuring that the packaging is sealed and unaltered. Use the official Trezor website to verify the serial number and compare it with the one on your device.
3. Set a Strong Password

During the initial setup process, create a strong and unique password for your Trezor device. Include a mix of upper and lowercase letters, numbers, and special characters. Avoid using easily guessable passwords.
4. Enable Two-Factor Authentication
Activate two-factor authentication (2FA) on your Trezor hardware wallet. This will add an extra layer of security by requiring a second verification step, often through your mobile device, for any sensitive transactions.
5. Keep Your Firmware Updated

Regularly check for firmware updates from the Trezor website and install them as soon as they become available. Firmware updates often include security patches and enhancements that help protect your hardware wallet from potential vulnerabilities.
6. Enable the Passphrase Feature

Consider using the passphrase feature provided by Trezor. This allows you to add an additional layer of security by using a unique phrase in addition to your standard password. Make sure to choose a strong passphrase and keep it secure.
7. Backup Your Recovery Seed
During the initial setup, Trezor generates a recovery seed that can be used to restore your wallet in case of loss or damage. It is essential to write down this seed and store it in a secure location that is separate from your hardware wallet.
| Best Practice | Description |
|---|---|
| Use a Trusted Source | Purchase your Trezor hardware wallet from an authorized source. |
| Verify Authenticity | Ensure that your Trezor device is genuine after receiving it. |
| Set a Strong Password | Create a strong and unique password for your Trezor device. |
| Enable Two-Factor Authentication | Activate 2FA for added security during transactions. |
| Keep Firmware Updated | Regularly update your Trezor firmware to protect against vulnerabilities. |
| Enable the Passphrase Feature | Use a passphrase for additional security. |
| Backup Your Recovery Seed | Write down and securely store your recovery seed. |
Following these best practices will significantly enhance the security of your Trezor hardware wallet and help protect your valuable cryptocurrency investments.
Q&A:
Can hackers gain access to my cryptocurrency if I use a Trezor hardware wallet?
No, it is highly unlikely that hackers will be able to compromise the security of a Trezor hardware wallet. Trezor uses advanced encryption and security features to protect your private keys and ensure the safety of your cryptocurrency.
Is it possible for a hacker to steal my private keys from my Trezor hardware wallet?
No, it is extremely difficult for a hacker to steal your private keys from a Trezor hardware wallet. The private keys are stored securely in the device and are never exposed, making it highly unlikely for them to be compromised.
What measures does Trezor take to protect against hacking attempts?
Trezor takes several measures to protect against hacking attempts. These include strong encryption algorithms, secure firmware updates, and a secure bootloader. In addition, Trezor employs a randomized PIN entry system and a built-in display to prevent keyloggers and phishing attacks.


