
Best Practices for Using Trezor One: Avoiding Common Mistakes

When it comes to storing your cryptocurrencies securely, the Trezor One hardware wallet is one of the most popular choices among crypto enthusiasts. With its robust security features and user-friendly interface, it provides an excellent solution for protecting your digital assets.
However, even with such a reliable device, there can still be potential pitfalls if you don’t follow best practices. In this article, we will explore some of the common mistakes that users make when using the Trezor One and provide you with valuable tips to ensure the utmost security and peace of mind.
1. Beware of phishing attacks: One of the most prevalent dangers in the crypto space is phishing attacks. Scammers often try to trick users into revealing their private keys or seed phrases through fake websites or emails. To avoid falling victim to these attacks, always double-check the URL and never enter your private information if anything seems suspicious.
2. Keep your recovery seed offline: Your recovery seed is essentially the key to your wallet. It is crucial to keep it offline and away from any potential security breaches. Many users make the mistake of storing their seed on their computer or in a cloud storage service, which can be vulnerable to hacks. Instead, write it down on a piece of paper and keep it in a secure location, like a safe or a lockbox.
3. Regularly update firmware: The developers behind Trezor One are constantly working on improving its security. To ensure that your device is fortified against the latest threats, it’s essential to regularly update its firmware. This will provide you with the most up-to-date security features and bug fixes, keeping your wallet secure.
4. Enable two-factor authentication (2FA): Adding an extra layer of security to your Trezor One is always a good idea. By enabling two-factor authentication, you will need to provide an additional verification code in addition to your PIN, further protecting your wallet from unauthorized access. Make sure to use a reliable and secure 2FA method, such as Google Authenticator or a hardware token.
5. Be cautious with third-party applications: While the Trezor One is compatible with many third-party applications, it’s important to be cautious when granting these applications access to your wallet. Only use trusted and reputable applications, and thoroughly research their security measures before connecting your Trezor One. It’s better to be safe than sorry when it comes to your precious digital assets.
In conclusion, by following these best practices, you can maximize the security of your Trezor One and reduce the risk of any mishaps. Always stay vigilant and take the necessary precautions to safeguard your cryptocurrencies. With the right knowledge and practices, you can enjoy the convenience and peace of mind that the Trezor One provides.
Proper Setup and Initialization

Setting up and initializing your Trezor One properly is crucial to ensure the security of your cryptocurrencies. By following these best practices, you can minimize the chances of making common mistakes and keep your funds safe.
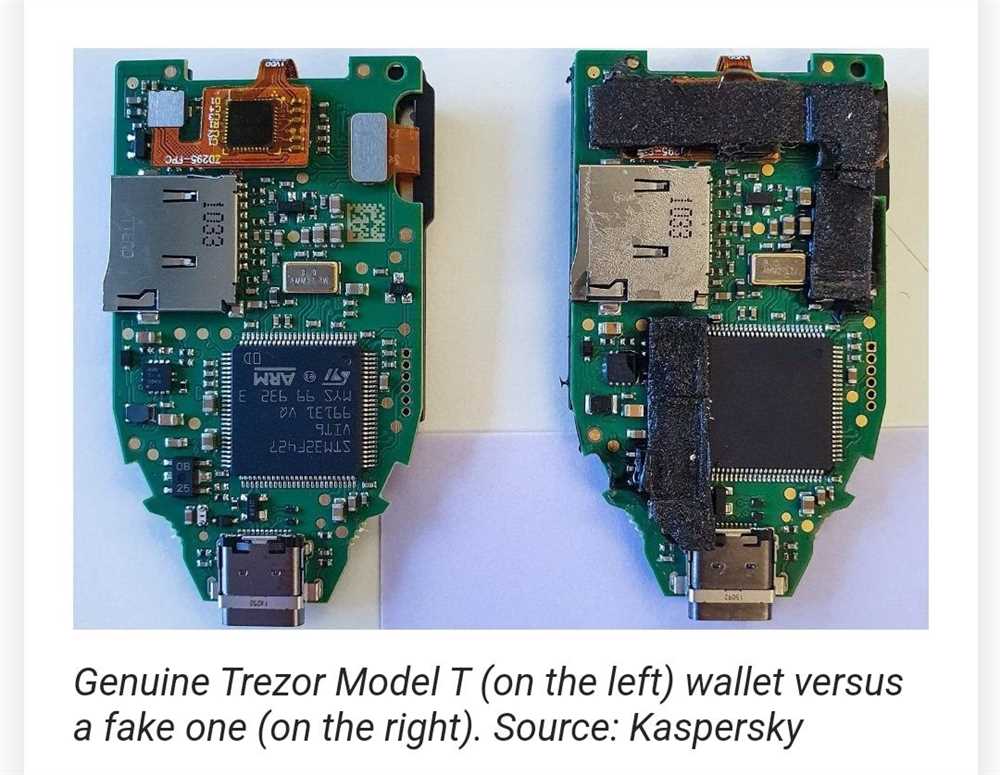
1. Verify the Authenticity of Your Trezor One

Before setting up your Trezor One, it is essential to verify its authenticity. Counterfeit devices could compromise the security of your funds. To ensure the authenticity of your Trezor One:
- Only purchase your device from the official Trezor website or authorized resellers.
- Check the packaging for any signs of tampering or damage.
- Verify the holographic seal on the box; it should be intact and genuine.
- Compare the model number and serial number on your device with the information provided on the Trezor website.
2. Use the Official Trezor Wallet

When setting up your Trezor One for the first time, make sure to use the official Trezor Wallet. The official wallet provides the highest level of security and compatibility with your device. Avoid using third-party wallets or software unless they are officially recommended by Trezor.
3. Create a Strong Recovery Seed
During the initialization process, you will be prompted to create a recovery seed. This seed is essential for recovering your wallet in case your device gets lost or damaged. Follow these guidelines when creating your recovery seed:
- Choose a strong password to encrypt your recovery seed. Include a mix of uppercase and lowercase letters, numbers, and special characters.
- Write down your recovery seed on a piece of paper and store it in a secure location. Avoid digital storage or cloud-based solutions, as they can be vulnerable to hacking.
- Never take a picture or screenshot of your recovery seed, as it can be easily compromised.
- Consider creating multiple copies of your recovery seed and storing them in different secure locations.
By following these best practices for proper setup and initialization, you can minimize the risk of common mistakes and ensure the overall security of your Trezor One.
Secure Storage and Backup

Securing your Trezor One device and backup is essential to protect your cryptocurrencies. Here are some best practices for secure storage and backup:
1. Store your Trezor One device in a secure location, such as a safe or a lockbox. It is important to keep it away from potential threats, such as theft or physical damage.
2. Do not store your recovery seed phrase electronically, as it can be vulnerable to hacking or data breaches. Instead, write down the seed phrase on a piece of paper and store it in a secure place.
3. Consider using a metal backup plate or cryptosteel to back up your recovery seed phrase. These tools provide an additional layer of protection against fire, water damage, and physical degradation.
4. Create multiple copies of your recovery seed phrase and store them in different secure locations. This will ensure redundancy and protect against loss or damage to your backup.
5. Regularly check the condition of your Trezor One device and backup. Look for any signs of physical damage or tampering. If you notice anything suspicious, contact the manufacturer immediately.
6. Keep your backup and recovery seed phrase separate from your Trezor One device, preferably in different physical locations. This will protect you from losing both in case of theft or natural disaster.
7. Test your backup and recovery process to ensure that you can restore your wallet in case of loss or theft. This will help you identify any issues or mistakes in your backup strategy.
By following these best practices, you can enhance the security of your Trezor One device and backup, reducing the risk of losing your cryptocurrencies.
Strong Password and PIN

Creating a strong password and PIN is crucial for ensuring the security of your Trezor One device and the funds it protects. Here are some best practices to follow:
1. Use a long and complex password: When creating a password for your Trezor One, make sure to use a combination of uppercase and lowercase letters, numbers, and special characters. The longer and more complex your password is, the harder it is for anyone to guess or crack it.
2. Avoid common passwords: Stay away from using common passwords, such as “123456” or “password,” as these can be easily guessed or found in password databases. Choose a unique password that is not easily associated with you or any personal information.
3. Change your password regularly: It is important to change your Trezor One password periodically to ensure its security. Aim to change it at least once every few months, and avoid reusing old passwords. This practice helps decrease the chances of someone gaining unauthorized access to your device.
4. Set a strong PIN: In addition to a strong password, it is recommended to set a strong PIN for your Trezor One. A PIN is a numeric code that you enter on the device itself. Choose a unique and hard-to-guess PIN, and avoid using easily guessable combinations like “1234”.
5. Memorize your password and PIN: It is crucial to memorize your Trezor One password and PIN instead of writing them down. Avoid storing them in digital or physical formats, as this can increase the risk of someone finding and using them. If you find it difficult to remember, consider using a password manager to securely store and manage your credentials.
Remember: Your password and PIN are the keys to access your Trezor One device and the funds it protects. By following these best practices, you can significantly enhance the security of your Trezor One and minimize the risk of unauthorized access.
Regular Firmware Updates

Regular firmware updates are crucial for ensuring the security and functionality of your Trezor One device. Trezor regularly releases firmware updates to address any vulnerabilities or bugs that may have been discovered. It is important to keep your device’s firmware up to date to protect yourself from potential threats.
Benefits of Regular Firmware Updates
- Enhanced Security: Firmware updates often include security patches that address any vulnerabilities found in the previous versions. By updating your device’s firmware, you ensure that you are using the latest and most secure version available.
- Improved Functionality: Firmware updates can also introduce new features and improvements to the Trezor One device. These updates can enhance your overall user experience and provide you with additional functionalities.
- Bug Fixes: Firmware updates may also include fixes for any bugs or glitches that have been identified in previous versions. Updating your device’s firmware helps to ensure that you have a smooth and error-free experience when using your Trezor One.
How to Perform a Firmware Update
Performing a firmware update for your Trezor One is a straightforward process. Here are the steps to follow:
- Connect your Trezor One device to your computer using the provided USB cable.
- Access the Trezor Bridge or Trezor Wallet interface on your computer.
- Check if there is a firmware update available for your device. If an update is available, you will be prompted to install it.
- Follow the on-screen instructions to initiate the firmware update process.
- During the update process, make sure not to disconnect your device or close the update window. Wait for the update to complete.
- Once the update is finished, you will be notified that your device’s firmware has been successfully updated.
It is recommended to regularly check for firmware updates for your Trezor One and install them as soon as they are available. This ensures that you are always using the latest and most secure firmware version, providing optimal security for your cryptocurrencies.
Question-answer:
What are some common mistakes people make when using Trezor One?
Some common mistakes people make when using Trezor One include not properly backing up recovery seeds, using weak PIN codes, not verifying the device’s authenticity, and failing to update the firmware regularly.
Why is it important to back up recovery seeds for Trezor One?
Backing up recovery seeds for Trezor One is crucial because it allows users to recover their funds in case of theft, loss, or damage to the device. Without a backup, access to the funds may be permanently lost.


