
Best practices for storing and securing your cryptocurrency following the Trezor breach

The recent breach of Trezor, a popular hardware wallet for cryptocurrencies, has highlighted the importance of storing and securing digital assets. As the value of cryptocurrencies continues to rise, so does the interest of hackers and cybercriminals. It is crucial for cryptocurrency holders to take necessary precautions to protect their investments from potential threats.
When it comes to storing and securing cryptocurrencies, there are certain dos and don’ts that every investor should be aware of. First and foremost, it is highly recommended to use a hardware wallet like Trezor. Hardware wallets provide an extra layer of security by storing private keys offline, away from potential online threats. They are designed to protect against malware and phishing attacks, making them a reliable choice for storing cryptocurrencies.
However, even with a hardware wallet, there are certain dos and don’ts that every cryptocurrency holder should follow. One of the dos is to always use strong and unique passwords for your wallets and exchange accounts. Strong passwords should be a combination of letters, numbers, and special characters, and they should not be related to any personal information. Using a password manager can also help in generating and keeping track of strong passwords.
Another important do is to enable two-factor authentication (2FA) whenever possible. 2FA adds an additional layer of security by requiring a second form of verification, such as a text message or a biometric scan, before accessing the cryptocurrency wallet or account. This ensures that even if someone gains access to your password, they would still need the second factor to log in.
On the other hand, there are certain don’ts that should be avoided when storing and securing cryptocurrencies. One of the major don’ts is to never store large amounts of cryptocurrency on an exchange. Although exchanges provide convenience for trading, they are frequent targets for hackers. It is advisable to move the cryptocurrency to a secure hardware wallet or cold storage after completing the trading process.
Additionally, it is important not to share private keys or recovery phrases with anyone. Private keys are essential for accessing and transferring cryptocurrencies, and sharing them can give unauthorized individuals full access to your funds. Similarly, recovery phrases should be kept secure and confidential, as they can be used to restore access to a wallet in case of loss or theft.
In conclusion, the recent Trezor breach serves as a wake-up call for cryptocurrency holders to prioritize the security of their digital assets. By following the dos and don’ts mentioned above, investors can significantly reduce the risk of their cryptocurrencies being compromised. Storing and securing cryptocurrencies is not something to be taken lightly, and it requires constant vigilance and adherence to best practices.
Best Practices for Cryptocurrency Storage
Storing and securing your cryptocurrency investments is of utmost importance to safeguard them from potential threats and breaches. By following these best practices, you can significantly reduce the risk of losing your valuable digital assets.
1. Use Hardware Wallets
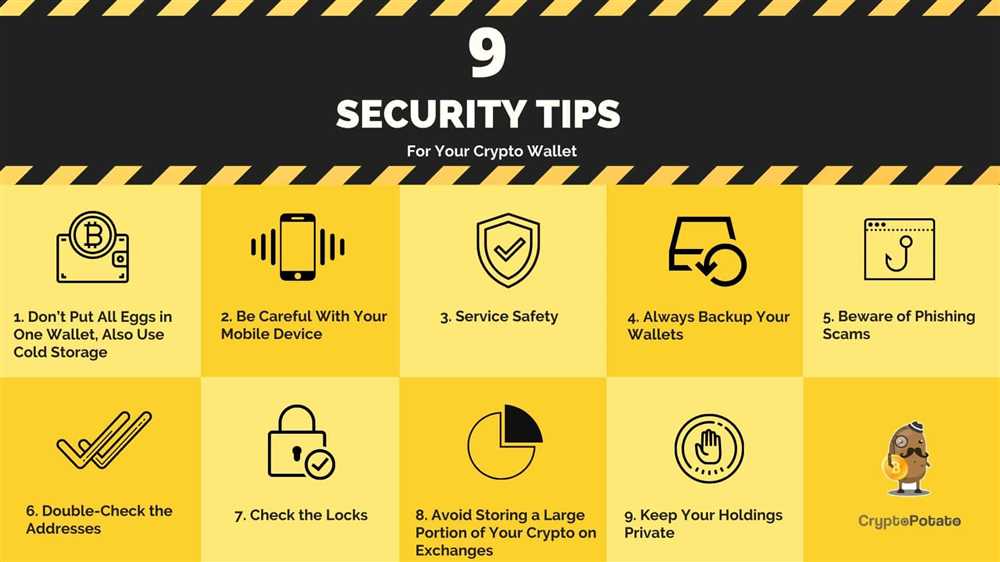
Hardware wallets, such as Trezor and Ledger, are considered one of the most secure options for storing cryptocurrencies. These devices store your private keys offline, making them inaccessible to hackers. Ensure that you purchase hardware wallets only from trusted sources and never share your recovery seed phrase with anyone.
2. Enable Two-Factor Authentication (2FA)

Enabling 2FA adds an additional layer of security to your cryptocurrency storage. By linking your accounts to an authenticator app or a physical security key, you ensure that unauthorized access to your funds becomes much more difficult. Always choose a reputable and widely supported 2FA method.
3. Keep Software Updated

Regularly updating the software on your devices is crucial for maintaining the security of your cryptocurrency wallets. Developers continuously release updates to address potential vulnerabilities. By keeping your software up to date, you minimize the risk of exploitation from known security loopholes.
4. Use Strong and Unique Passwords

Using strong and unique passwords for your cryptocurrency wallets is essential. Avoid using common combinations or easily guessable information. Instead, create complex passwords that include a combination of uppercase and lowercase letters, numbers, and special characters. Use a password manager to securely store and manage your passwords.
5. Practice Cold Storage
Cold storage refers to storing your cryptocurrency offline, away from any internet-connected device. This includes using hardware wallets or physical storage mediums, such as paper wallets or encrypted USB drives. By keeping your assets offline, you eliminate the risk of being targeted by online hackers.
6. Regularly Backup Your Wallets

Creating regular backups of your cryptocurrency wallets is essential in case of unexpected hardware failures or accidents. Store these backups in multiple secure locations, such as encrypted external hard drives or offline storage mediums. Test your backups to ensure they can be successfully restored.
7. Be Cautious of Public Wi-Fi
Avoid accessing your cryptocurrency wallets or making transactions while connected to public Wi-Fi networks. These networks are often unsecured and vulnerable to malicious activities. Use a trusted and secure internet connection to reduce the risk of exposing your private keys and sensitive information.
8. Be Skeptical of Phishing Attempts
Phishing attempts are common in the cryptocurrency space. Be cautious of unsolicited emails, messages, or websites that ask for your private keys or sensitive information. Always verify the legitimacy of the source before providing any personal details.
By following these best practices, you can enhance the security of your cryptocurrency storage and minimize the risk of unauthorized access or loss of funds. Stay vigilant and stay informed about the latest security measures to ensure the safety of your valuable digital assets.
Common Mistakes to Avoid
When it comes to storing and securing your cryptocurrency, there are several common mistakes that you should avoid making. By being aware of these mistakes, you can ensure that your funds are protected and secure.
1. Using Weak Passwords

One of the most common mistakes that people make is using weak passwords to protect their cryptocurrency wallets. A strong password should be long, complex, and include a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable passwords such as your birthdate or the word “password”.
2. Not Using Two-Factor Authentication
Another mistake to avoid is not using two-factor authentication (2FA) for your cryptocurrency wallets. 2FA adds an extra layer of security by requiring you to provide an additional piece of information, such as a code generated by an app on your smartphone, in addition to your password. This makes it much harder for hackers to gain access to your funds.
Tip: Use a reputable authenticator app such as Google Authenticator or Authy for generating the 2FA codes.
3. Falling for Phishing Scams

Phishing scams are a common method used by hackers to trick people into revealing their login credentials or private keys. These scams often involve sending emails or creating fake websites that look like legitimate cryptocurrency platforms. Always double-check the URL of the website before entering any sensitive information and be cautious of any unsolicited emails.
Tip: Enable browser extensions like MetaMask that can help detect and block phishing attempts.
4. Neglecting Software and Firmware Updates

Another mistake to avoid is neglecting to update the software and firmware of your hardware wallet. These updates often include important security patches that fix vulnerabilities and enhance the overall security of your wallet. Always keep your wallet’s firmware and software up to date.
5. Not Having a Backup
Failure to have a backup of your wallet’s recovery phrase is a mistake that can lead to permanent loss of funds. If you lose access to your wallet or if it gets stolen, having a backup recovery phrase allows you to regain access to your funds. Be sure to store your backup phrase in a safe and secure location, such as a hardware wallet or a piece of paper stored in a safe.
By avoiding these common mistakes, you can significantly reduce the risk of losing your cryptocurrency funds. Remember to always prioritize security and take the necessary precautions to protect your digital assets.
Q&A:
What is the Trezor breach?
The Trezor breach refers to a security breach where hackers gained unauthorized access to some Trezor wallets and stole the stored cryptocurrency.
How did the Trezor breach happen?
The details of the Trezor breach are not known yet. Trezor is currently conducting an investigation to determine how the breach occurred.
What are the dos for storing and securing cryptocurrency?
Some of the dos for storing and securing cryptocurrency include using hardware wallets like Trezor, creating strong and unique passwords, enabling two-factor authentication, and regularly updating software and firmware.
What are the don’ts for storing and securing cryptocurrency?
Some of the don’ts for storing and securing cryptocurrency include storing cryptocurrency on exchanges, using weak passwords, downloading and installing software from untrusted sources, and sharing sensitive information with others.
What should I do if I have been affected by the Trezor breach?
If you have been affected by the Trezor breach, it is recommended to contact Trezor’s customer support immediately and follow their instructions on securing your account and recovering any lost funds.


