
Are Trezors Really Hack-Proof? Weighing the Pros and Cons of this Popular Crypto Wallet

In today’s digital world, securing your cryptocurrency investments is crucial. With the rise of cyber threats and hacking incidents, finding a safe and reliable storage solution is becoming more important than ever. One popular option that many investors turn to is the Trezor.
The Trezor is a hardware wallet that offers a high level of security for storing your digital assets. It is known for its robust security features, including offline storage and encryption. Many users claim that it is virtually hack-proof and provides peace of mind when it comes to protecting your funds. But is this really the case?
While the Trezor offers a range of benefits, it is not without its risks. Like any technology, it is not completely immune to vulnerabilities. Hackers are constantly evolving, constantly finding new ways to breach security measures. While the Trezor may be one of the most secure storage solutions available, there is still a small possibility that it could be compromised.
It is important for users to understand that the security of their digital assets ultimately depends on their own actions. Even with a reliable hardware wallet like the Trezor, taking precautions such as using strong passwords, enabling two-factor authentication, and regularly updating firmware is essential. Additionally, users should always be vigilant and stay informed about the latest security practices to ensure their cryptocurrency investments remain safe.
The Vulnerabilities of Trezor Wallets
Trezor wallets are often touted as one of the most secure options for storing cryptocurrencies. However, it is important to understand that they are not completely immune to vulnerabilities. While the probability of an attack is relatively low, it is still crucial to be aware of potential risks.
1. Phishing Attacks

Phishing attacks remain a major concern when it comes to Trezor wallets. Scammers may try to trick users into visiting a fake website that mimics the official Trezor site, prompting them to enter their recovery seed or private keys. By doing so, hackers can gain access to funds stored in the wallet.
To avoid falling victim to such attacks, it is essential to always verify the authenticity of the website or app. Double-check the URL, use a secure connection, and never enter your recovery seed or private keys on any website other than the official Trezor website.
2. Supply Chain Attacks

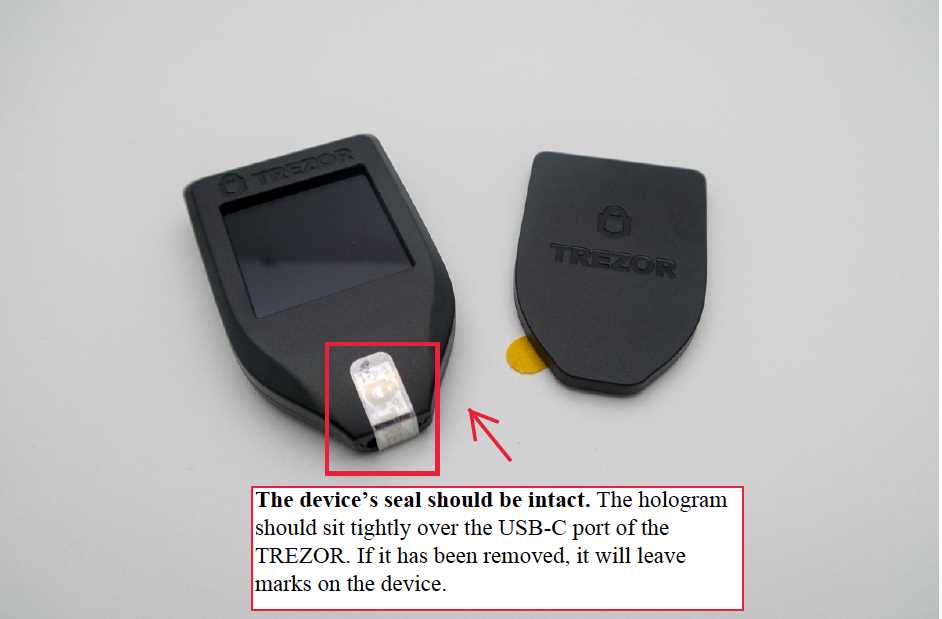
Supply chain attacks involve compromising the device during the manufacturing or distribution process. This means that the wallet may be tampered with before it even reaches the hands of the user. Hackers may install malicious firmware or components that can compromise the security of the device.
To mitigate the risk of supply chain attacks, it is recommended to only purchase Trezor wallets from trusted sources. Avoid buying second-hand wallets or those from unknown sellers. Additionally, always update the firmware of your device to ensure you have the latest security features installed.
Remember: While Trezor wallets have vulnerabilities, they are still considered one of the most secure options available. By staying vigilant, practicing good security habits, and regularly updating your firmware, you can minimize the risks and enjoy the benefits of using a Trezor wallet.
The Benefits of Using a Trezor Wallet
When it comes to securely storing your cryptocurrencies, the Trezor Wallet stands out as one of the best options available. Here are some of the key benefits that come with using a Trezor Wallet:
1. Enhanced Security

The Trezor Wallet offers state-of-the-art security features that help protect your digital assets from hackers and unauthorized access. With its offline storage and multi-factor authentication, you can ensure that your private keys and cryptocurrencies remain safe and secure.
2. User-Friendly Interface

Using a Trezor Wallet is incredibly easy, even for beginners. The wallet’s user-friendly interface makes it simple to navigate and manage your crypto holdings. Whether you want to send or receive funds, check your transaction history, or monitor your portfolio, the Trezor Wallet makes it intuitive and convenient.
3. Wide Compatibility
Trezor Wallet supports a wide variety of cryptocurrencies, including Bitcoin, Ethereum, Litecoin, and many others. This compatibility allows you to store and manage all your different coins in one secure place without the need for separate wallets.
4. Advanced Privacy Features
Trezor Wallet prioritizes your privacy and provides you with advanced features to protect your identity and transaction details. Through features like CoinJoin, you can improve the anonymity of your transactions, making it harder for anyone to link your wallet address to your personal information.
5. Regular Firmware Updates
Trezor regularly releases firmware updates to address any security vulnerabilities and improve the overall functionality of the wallet. By keeping your device up to date, you can ensure that you have the latest security patches and features.
In conclusion, the Trezor Wallet offers a range of benefits that make it an excellent choice for securely managing your cryptocurrencies. Its enhanced security, user-friendly interface, wide compatibility, advanced privacy features, and regular firmware updates set it apart from other wallets on the market. Whether you’re new to crypto or a seasoned investor, the Trezor Wallet provides the peace of mind and convenience you need.
Is a Trezor Wallet Truly Hack-Proof?

When it comes to storing your cryptocurrency, security is of utmost importance. Many people turn to hardware wallets like the Trezor, attracted by its reputation for being hack-proof. But is it really as secure as it claims to be?
The Trezor wallet utilizes a number of advanced security measures to protect your digital assets. One of the key features is its offline storage, which means that your private keys never leave the device and are always protected from online threats. This makes it incredibly difficult for hackers to gain access to your funds.
End-to-End Encryption

Trezor also employs end-to-end encryption, ensuring that your transactions and wallet information are securely encrypted from start to finish. This adds an extra layer of protection against any potential vulnerabilities or data breaches.
Pin Code and Recovery Seed
Another security feature of the Trezor wallet is the use of a PIN code, which needs to be entered every time you want to access your funds. This prevents anyone without the PIN from gaining unauthorized access to your wallet. Additionally, the wallet generates a recovery seed during the setup process, which consists of a series of words. This allows you to recover your wallet and funds in the event that your device is lost or stolen.
While the Trezor wallet is designed with strong security measures, it is important to note that no system is completely hack-proof. There have been reported instances of advanced techniques such as phishing attacks and physical tampering that have successfully compromised some Trezor wallets. However, these instances are rare and require significant effort and expertise on the part of the attacker.
Ultimately, using a Trezor wallet significantly reduces the risk of your cryptocurrency being hacked compared to storing it on an online exchange or a software wallet. However, it is important to stay vigilant and follow best practices to further enhance the security of your digital assets.
Q&A:
What is a Trezor and how does it work?
Trezor is a hardware wallet used for storing cryptocurrencies. It works by securely storing the private keys that are needed to access and manage your cryptocurrency funds.
Is using a Trezor completely hack-proof?
While Trezor is designed to be highly secure, it is not entirely hack-proof. There have been instances in the past where hackers were able to exploit vulnerabilities in the device and steal funds. However, the risk of such an attack is relatively low compared to other forms of storing cryptocurrencies.
What are the risks of using a Trezor?
One of the main risks of using a Trezor is the possibility of losing or damaging the device. If you lose your Trezor or it gets damaged and you don’t have a backup of the recovery seed, you could lose access to your cryptocurrency funds. Additionally, there is always a risk of hackers finding new vulnerabilities in the device and exploiting them to steal funds.


