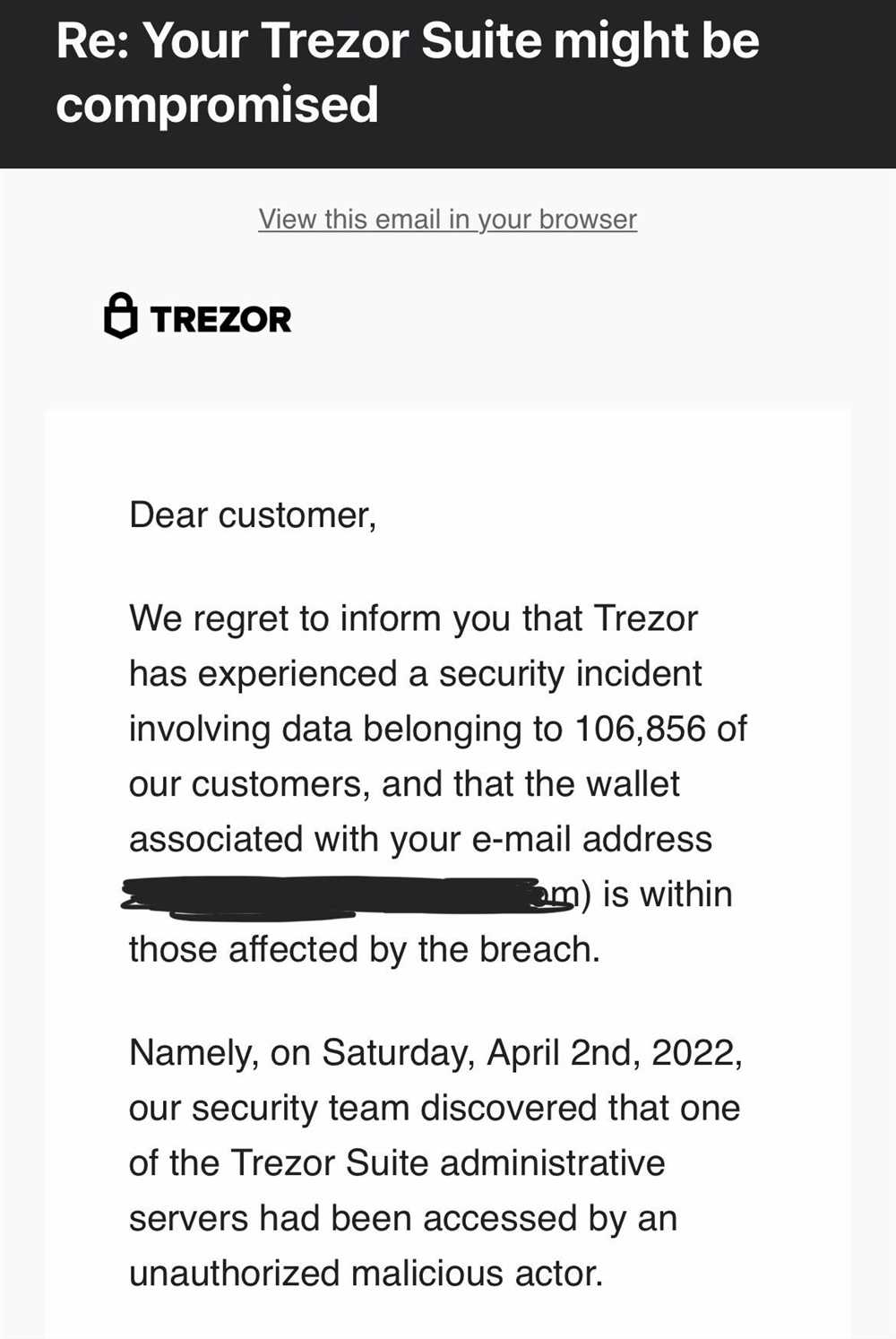
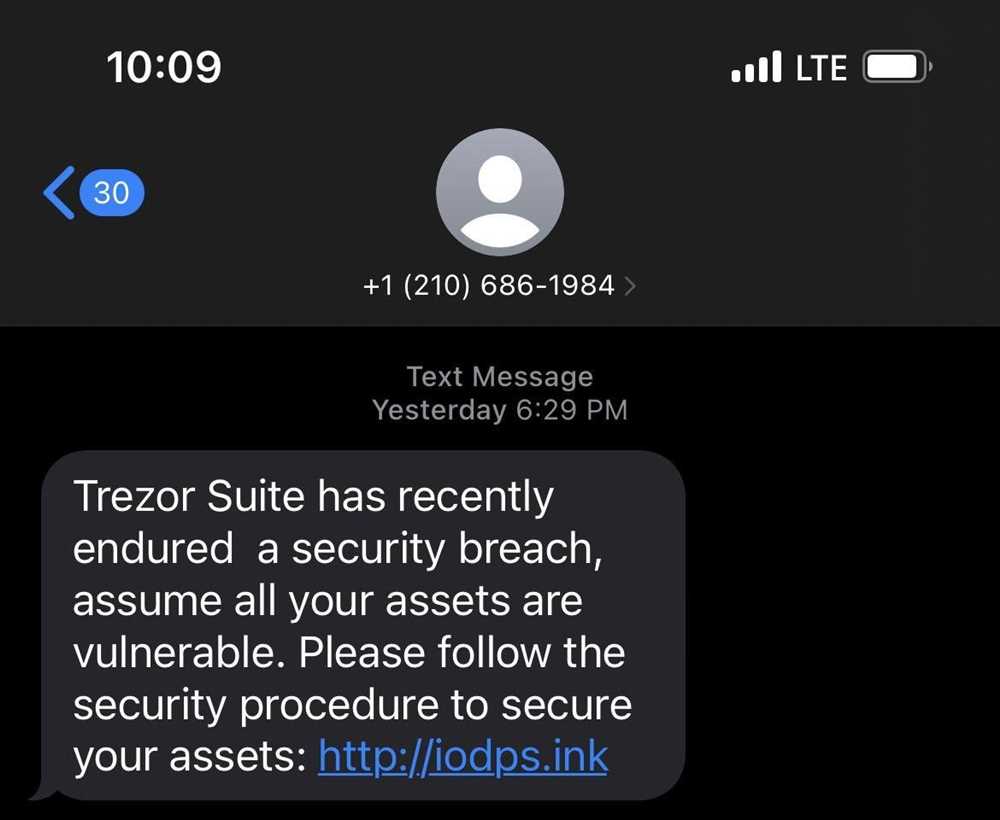
A Closer Look at the Trezor Breach: What Happened and What it Means for Users

In recent years, the importance of securing digital assets has become more evident than ever. Cryptocurrencies, such as Bitcoin, have gained popularity and value, attracting the attention of both investors and hackers. One of the most widely used hardware wallets for storing cryptocurrencies is Trezor, known for its strong security measures. However, no system is completely infallible, as proven by the recent breach of Trezor’s security.
The breach exposed the vulnerabilities of Trezor’s security protocols, leaving thousands of users at risk of losing their digital fortunes. This incident serves as a wake-up call for the entire cryptocurrency community, highlighting the need for constant vigilance and improvement in protecting digital assets.
The impact of the Trezor breach cannot be underestimated. Many users entrusted their private keys and valuable cryptocurrencies to this hardware wallet, believing it to be a safe and secure solution. The breach not only undermined user confidence in Trezor but also raised concerns about the overall security of hardware wallets. As a result, users are left questioning the safety of their investments and wondering if any wallet can truly be trusted.
This breach has significant implications for users, as it highlights the potential risks and threats associated with storing cryptocurrencies. It serves as a reminder that regardless of the security measures in place, hackers are constantly evolving their tactics and finding new ways to exploit vulnerabilities. Users must now reconsider their approach to storage and security, exploring alternative methods and additional layers of protection to safeguard their digital assets.
In conclusion, the Trezor breach has exposed the vulnerabilities of hardware wallets and has shaken the faith of many cryptocurrency users. It serves as a stark reminder that no system is impervious to attack, and vigilance is crucial in protecting digital assets. As the cryptocurrency landscape continues to evolve, it is imperative for users to stay informed, adapt their security practices, and remain cautious in order to mitigate the risks and prevent future breaches.
Understanding the Trezor Breach
The Trezor breach, which occurred on [date], has raised concerns and questions about the security of cryptocurrency wallets. This article aims to provide a closer look at the Trezor breach, analyzing its impact and implications for users.
Background
Trezor is a popular hardware wallet used by cryptocurrency enthusiasts to securely store their digital assets. It uses advanced encryption techniques and offline storage to protect users’ private keys.
The Breach
The Trezor breach involved the exploitation of a vulnerability that allowed attackers to gain unauthorized access to users’ private keys. This breach potentially exposed users’ cryptocurrency holdings to theft or unauthorized transactions.
Upon discovering the breach, the Trezor team took immediate action to address the vulnerability and notify affected users. They released an update to fix the issue and provided guidance on how to secure their accounts.
Impact on Users
The breach has had significant implications for Trezor users. It has eroded trust in the security of hardware wallets and has raised concerns about the overall safety of storing cryptocurrency assets.
Users affected by the breach may have lost funds or had unauthorized transactions made on their behalf. They may also face the risk of future attacks targeting their compromised private keys.
Implications for the Industry
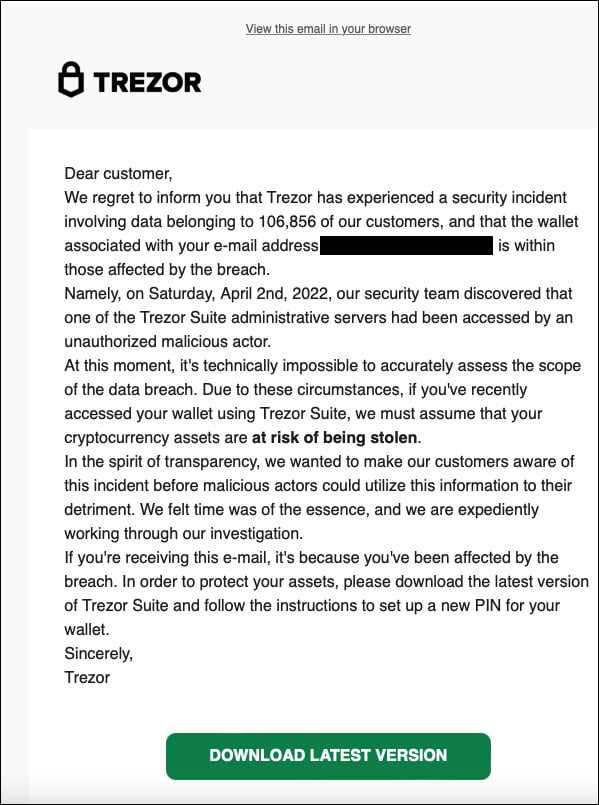
The Trezor breach serves as a wake-up call for the cryptocurrency industry as a whole. It highlights the importance of robust security measures in protecting users’ digital assets.
Wallet manufacturers and developers need to invest in constant security testing and updates to stay ahead of evolving threats. Additionally, users should stay vigilant and follow best practices in securing their cryptocurrency holdings.
As the industry matures, it is likely that regulators will impose stricter security standards on cryptocurrency wallet providers to protect consumers and promote trust in the ecosystem.
Conclusion
The Trezor breach has underscored the need for constant vigilance and robust security measures in the cryptocurrency industry. Users should remain cautious and take necessary precautions to protect their digital assets. Wallet providers should prioritize security and invest in regular security audits to ensure the safety of their users’ funds.
Evaluating the Impact on User Security
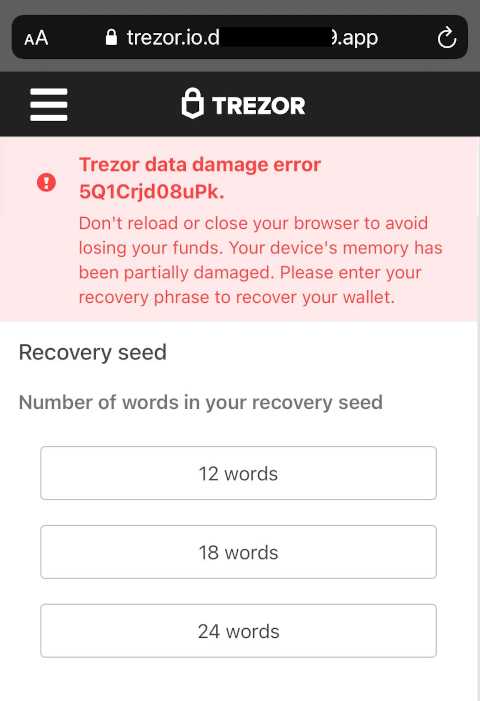
The recent Trezor breach has raised significant concerns regarding the security of user information and assets. This incident serves as a stark reminder of the ever-present threat of hacking and the importance of maintaining strong security measures.
One of the key aspects to evaluate is the extent of the breach and the potential impact on user security. It is critical to understand the scope of the attack in order to assess the effectiveness of Trezor’s security systems and the level of vulnerability users may face.
Firstly, it is essential to determine the specifics of the data compromised during the breach. Were user account credentials, sensitive personal information, or wallet access keys exposed? Understanding this information will help users grasp the potential risks they may face, such as identity theft or unauthorized access to their digital assets.
Additionally, it is crucial to examine the actions taken by Trezor following the breach. How quickly did the company detect the intrusion and respond? Were immediate steps taken to contain the attack and mitigate the potential damage? Evaluating the company’s response will provide users with insight into their commitment to protecting user security and their ability to effectively address such incidents.
The impact on user security also extends to the measures Trezor has taken to prevent similar breaches in the future. Have they identified the vulnerability exploited in this attack? Have they implemented additional security measures to fortify their systems and protect user information? Understanding the steps taken by the company to address the breach will help users assess the reliability and trustworthiness of the Trezor platform.
Lastly, it is vital to consider the broader implications of the breach on the cryptocurrency community as a whole. Such incidents can erode trust in digital wallets and other crypto-related platforms. Users may become hesitant to store their assets digitally, which can have long-lasting consequences for the adoption and advancement of cryptocurrencies.
In conclusion, evaluating the impact on user security in the wake of the Trezor breach is essential for users to comprehend the potential risks they may face and make informed decisions regarding their digital asset management. Analyzing the specifics of the breach, Trezor’s response, and their steps towards prevention will enable users to gauge the level of trustworthiness and reliability of the platform, as well as understand the broader implications for the cryptocurrency community.
Assessing the Implications for the Cryptocurrency Community
The recent Trezor breach has raised serious concerns within the cryptocurrency community. The breach not only compromised the security of user funds, but it also highlighted potential vulnerabilities in the overall infrastructure of cryptocurrency platforms. As a result, it is imperative for the cryptocurrency community to assess the implications of this breach and take proactive measures to prevent similar incidents in the future.
One of the main implications of the Trezor breach is the loss of trust and confidence among cryptocurrency users. With the security of their funds compromised, users may become hesitant to store their digital assets in wallets, fearing that their funds could be vulnerable to hackers. This lack of trust could have a detrimental effect on the adoption and growth of cryptocurrencies, hindering the mainstream acceptance of digital currencies.
Furthermore, the breach serves as a wakeup call for the cryptocurrency community to strengthen security measures. It is clear that existing security protocols and practices are not sufficient to protect user funds from determined hackers. Therefore, it is crucial for developers and exchanges to invest in robust security systems, conduct frequent audits, and implement multi-factor authentication to ensure the safety of user accounts and funds.
The Trezor breach also underscores the need for increased education and awareness within the cryptocurrency community. Many users may not fully understand the intricacies of securing their digital assets and may be unaware of the potential risks associated with storing their funds in wallets. Providing educational materials and resources to users can empower them to make informed decisions and take necessary precautions to safeguard their cryptocurrencies.
Another implication of the breach is the potential for regulatory scrutiny and intervention. The unauthorized access of user funds raises questions about the adequacy of existing regulations and oversight in the cryptocurrency space. Regulators may see the need to tighten regulations to protect consumers and prevent similar breaches from occurring in the future. While increased regulation can provide a level of protection, it is important to strike a balance that allows for innovation and growth within the cryptocurrency industry.
In conclusion, the Trezor breach has significant implications for the cryptocurrency community. It highlights the importance of trust, security, education, and regulation within the industry. By addressing these implications head-on and implementing necessary changes, the cryptocurrency community can work towards enhancing security, fostering trust, and promoting the widespread adoption of cryptocurrencies.
Protecting Your Assets: Best Practices for Trezor Users
In light of the recent Trezor breach, it is crucial for users to take every precaution to protect their assets. Below, we outline a set of best practices that all Trezor users should follow to ensure the security of their funds:
1. Keep Your Firmware Up to Date
Regularly updating your Trezor firmware is essential for staying protected against potential vulnerabilities. Check for firmware updates frequently and install them as soon as they become available.
2. Enable Two-Factor Authentication
Enabling two-factor authentication (2FA) adds an extra layer of security to your Trezor device. By requiring a second verification method, such as a code sent to your mobile device, you can significantly reduce the risk of unauthorized access to your funds.
3. Use a Strong, Unique PIN

Choose a strong PIN for your Trezor that is not easily guessable. Avoid using common numbers or patterns and opt for a combination of letters, numbers, and special characters. Keep your PIN confidential and do not share it with anyone.
4. Backup Your Recovery Seed
It is crucial to create and securely store a backup of your Trezor recovery seed. This seed is essential for recovering your funds in case of a device loss or failure. Use a reliable offline method, such as writing it down on paper, and store it in a secure location.
5. Be Wary of Phishing Attempts
Always double-check the URL of any website you visit to ensure it is the legitimate Trezor website. Beware of phishing attempts that try to trick you into revealing your recovery seed or other sensitive information. Trezor will never ask you for this information directly.
6. Secure Your Physical Device
Store your Trezor device in a secure location when not in use. Keep it protected from physical damage, theft, and unauthorized access. Avoid leaving it unattended in public places or easily accessible areas.
By following these best practices, Trezor users can enhance the security of their assets and reduce the risk of falling victim to hacks or breaches.
Q&A:
What is the Trezor Breach?
The Trezor Breach refers to a security incident where a hacker claimed to have successfully compromised the Trezor hardware wallet, potentially gaining access to users’ cryptocurrency funds.
How did the hacker breach the Trezor?
The exact details of how the hacker breached the Trezor are not yet known. However, it is believed that the hacker either exploited a vulnerability in the device’s firmware or gained physical access to the device and extracted the private keys.


