
Understanding the Threat Landscape for Cryptocurrency Holders

In the dynamic world of cryptocurrencies, security is a constant concern for holders and investors. As the popularity of digital currencies continues to rise, so does the threat landscape. One recent incident that highlighted the vulnerabilities of cryptocurrency storage is the Trezor security breach.
Trezor, one of the leading hardware wallet providers in the industry, suffered a security breach that left many of its users at risk of losing their digital assets. This breach not only had financial implications for those affected, but it also raised questions about the overall security of cryptocurrency storage methods.
The threat landscape for cryptocurrency holders is ever-evolving, with hackers constantly finding new ways to exploit vulnerabilities. Understanding the risks and taking necessary precautions is crucial for anyone involved in the world of digital currencies. This article will delve into the Trezor security breach and explore the broader threat landscape that cryptocurrency holders need to be aware of.
By understanding the intricacies of the Trezor security breach and its implications, cryptocurrency holders can better protect their digital assets. It is essential to stay informed and up-to-date with the latest security measures to avoid falling victim to similar incidents. With the right knowledge and proactive approach, individuals can navigate the threat landscape and safeguard their investments in this exciting but risky realm of cryptocurrencies.
Trezor Security Breach
In the world of cryptocurrencies, security is of paramount importance. One of the most widely used hardware wallets for storing cryptocurrencies is Trezor. However, even devices like Trezor can be vulnerable to security breaches.
A security breach refers to an unauthorized access to sensitive information or data. The Trezor security breach was a significant event that put many cryptocurrency holders at risk. In this article, we will explore the Trezor security breach, its impact, and the lessons that can be learned from it.
What Happened?

In 2020, a security researcher discovered a vulnerability in the firmware of certain Trezor hardware wallets. This vulnerability allowed an attacker with physical access to the device to extract the private keys stored on it, potentially compromising the user’s funds.
The vulnerability was related to the manufacturing process of the devices, where an attacker could manipulate the hardware to extract the encrypted seed phrase from the device. With the seed phrase in hand, the attacker could then access the user’s cryptocurrency funds.
Impact on Cryptocurrency Holders
The Trezor security breach had a significant impact on cryptocurrency holders who relied on the device to store their funds securely. Those who were affected by the breach faced the risk of losing their cryptocurrency investments if the attacker successfully accessed their funds.
However, it is important to note that Trezor acted swiftly to address the issue and issued a security update to fix the vulnerability. Users were urged to update their firmware and follow the instructions provided by Trezor to strengthen their security measures.
| Lessons Learned |
|---|
| 1. Regular firmware updates are crucial to address security vulnerabilities
2. Physical security is just as important as digital security for cryptocurrency holders 3. Backup your seed phrase and store it securely in multiple locations 4. Stay informed about the latest security threats and best practices |
In conclusion, the Trezor security breach served as a reminder of the importance of strong security measures in the cryptocurrency world. By staying vigilant and taking appropriate precautions, cryptocurrency holders can better protect their investments from potential threats.
Understanding the Threat Landscape for Cryptocurrency Holders
Cryptocurrency has become an increasingly popular investment option, offering potential for significant returns. However, along with its soaring popularity, the threat landscape for cryptocurrency holders has also been expanding rapidly.
One of the major threats in the cryptocurrency world is hacking. Hackers are constantly looking for vulnerabilities in cryptocurrency platforms, wallets, and exchanges. They are highly skilled at exploiting these vulnerabilities to gain unauthorized access and steal cryptocurrencies.
Phishing attacks are another common threat faced by cryptocurrency holders. Scammers create fake websites or send fraudulent emails pretending to be legitimate cryptocurrency platforms or exchanges. They trick users into revealing their private keys or login credentials, giving the scammers access to their cryptocurrency funds.
Malware is also a significant threat to cryptocurrency holders. Malicious software can infect a user’s device and steal their private keys or login information. This allows hackers to gain access to their cryptocurrency wallets and transfer the funds to their own accounts.
Social engineering is yet another tactic used by hackers to target cryptocurrency holders. They manipulate individuals into revealing sensitive information or performing actions that compromise their cryptocurrency security. This can include impersonating customer support representatives or sending fraudulent messages designed to deceive the user into providing their private keys or passwords.
To protect themselves from these threats, cryptocurrency holders must take proactive measures. They should use hardware wallets, such as Trezor, that offer enhanced security features. It is also important to keep software and antivirus programs up to date, and to be cautious of phishing attempts and suspicious links.
In conclusion, understanding the threat landscape for cryptocurrency holders is crucial for ensuring the security of their investments. By being aware of the risks and implementing necessary security measures, cryptocurrency holders can better protect their valuable assets and minimize the chances of falling victim to malicious actors in the digital world.
Implications of the Trezor Security Breach
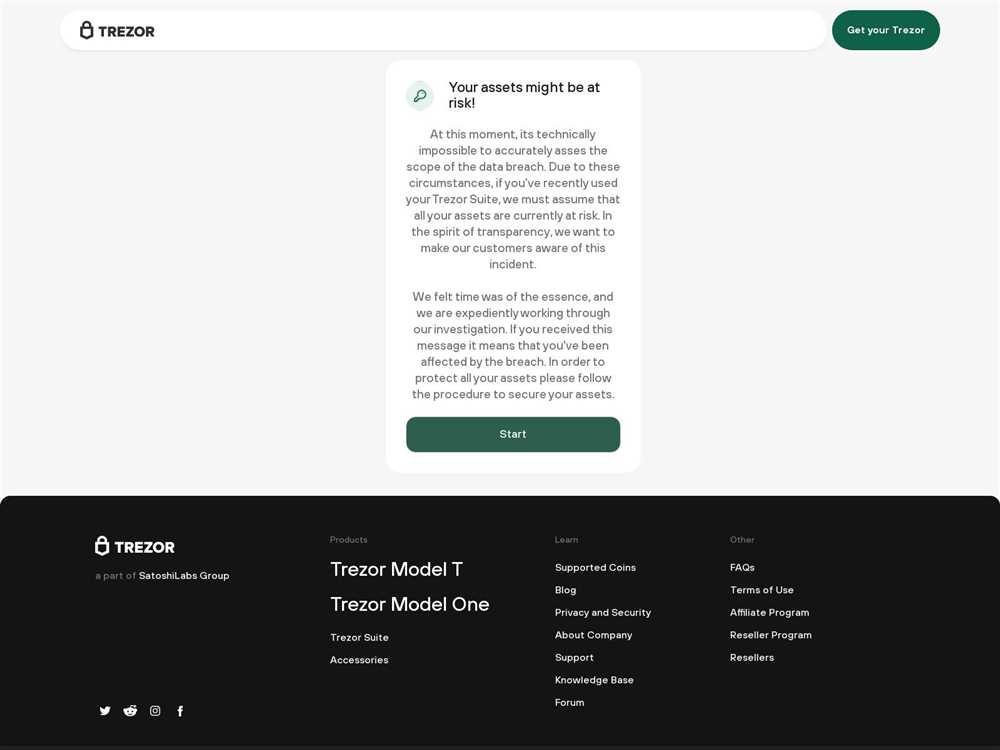
The recent security breach of the Trezor hardware wallet has raised significant concerns and implications for cryptocurrency holders. This breach highlighted the vulnerabilities that exist in the cryptocurrency ecosystem and the need for enhanced security measures.
User Funds at Risk
One of the major implications of the Trezor security breach is the potential risk to user funds. With access to the private keys, hackers can gain control over the user’s cryptocurrencies, leading to the loss of funds. This breach serves as a reminder that even hardware wallets, considered to be one of the most secure ways to store cryptocurrencies, are not immune to attacks.
Trust in Hardware Wallets Shaken

The security breach of Trezor has also shaken the trust of cryptocurrency holders in hardware wallets. Many relied on these wallets to keep their digital assets secure, but this incident has shown that they are not infallible. This breach may lead to a decrease in the adoption of hardware wallets and a shift towards alternative storage methods or increased skepticism towards the security of such devices.
Limited Recourse for Users
One of the significant concerns arising from the Trezor security breach is the limited recourse available for affected users. Due to the decentralized nature of cryptocurrencies, recovering stolen funds can be challenging, if not impossible. This lack of recourse adds to the consequences faced by users who have fallen victim to such breaches.
Call for Enhanced Security Measures
The Trezor security breach serves as a wake-up call for the cryptocurrency industry to prioritize enhanced security measures. Both hardware wallet manufacturers and cryptocurrency exchanges need to invest in strengthening their security protocols to safeguard user assets effectively. Industry-wide collaboration in sharing information, implementing best practices, and developing robust security systems is crucial to preventing similar incidents in the future.
Increased Regulatory Scrutiny
Finally, the Trezor security breach may lead to increased regulatory scrutiny on the cryptocurrency ecosystem. Regulators may view this breach as evidence of the need for stricter regulations on cryptocurrency exchanges and custodial services, aiming to enhance user protections and mitigate the risks associated with holding digital assets.
- Overall, the implications of the Trezor security breach highlight the need for constant vigilance and continuous improvement in the security measures employed by cryptocurrency holders and service providers.
Protecting Your Cryptocurrency: Best Practices and Recommendations

With the increasing popularity and value of cryptocurrencies, it is more important than ever to take the necessary precautions to protect your digital assets. Here are some best practices and recommendations to help you keep your cryptocurrency safe:
1. Use a Hardware Wallet:
A hardware wallet, such as the Trezor, is one of the most secure ways to store your cryptocurrency. It provides an offline storage solution that keeps your private keys away from potential hackers.
2. Enable Two-Factor Authentication:
Add an extra layer of protection to your cryptocurrency accounts by enabling two-factor authentication. This will require you to enter a verification code, usually sent to your mobile device, in addition to your password.
3. Keep Software and Devices Updated:
Regularly update both your software and devices to ensure you have the latest security patches. Hackers often exploit vulnerabilities in outdated software, so staying up to date is crucial.
4. Use Strong and Unique Passwords:
Create strong and unique passwords for all your cryptocurrency accounts. Avoid using common phrases or easily guessable information, and consider using a password manager to securely store your passwords.
5. Be Cautious of Phishing Attempts:
Be wary of phishing attempts, where attackers try to trick you into revealing your private keys or other sensitive information. Always double-check the URLs of websites and be cautious of unsolicited emails or messages.
6. Secure Your Internet Connection:

Ensure that your internet connection is secure when accessing your cryptocurrency accounts, especially when using public Wi-Fi. Consider using a virtual private network (VPN) for an added layer of protection.
7. Backup Your Wallet:

Regularly backup your cryptocurrency wallet and store the backup in a safe and secure location. This will allow you to recover your funds in case of loss, theft, or damage to your primary wallet.
8. Be Careful with Third-Party Services:
Exercise caution when using third-party services, such as cryptocurrency exchanges or online wallets. Research and choose reputable and trusted platforms with a proven track record of security.
By following these best practices and recommendations, you can significantly reduce the risk of a security breach and protect your cryptocurrency holdings.
Q&A:
Why is it important for cryptocurrency holders to understand the threat landscape?
Understanding the threat landscape is crucial for cryptocurrency holders because it allows them to be aware of potential risks and take necessary precautions to protect their assets. By understanding the threats that exist, holders can make informed decisions about their security measures and reduce the likelihood of falling victim to a security breach.
What is Trezor?
Trezor is a hardware wallet designed to securely store cryptocurrency. It provides an offline storage solution, keeping the private keys that control the user’s cryptocurrency holdings offline and away from potential hacking attempts. This provides an additional layer of security compared to online wallets.
How did the security breach impact Trezor users?
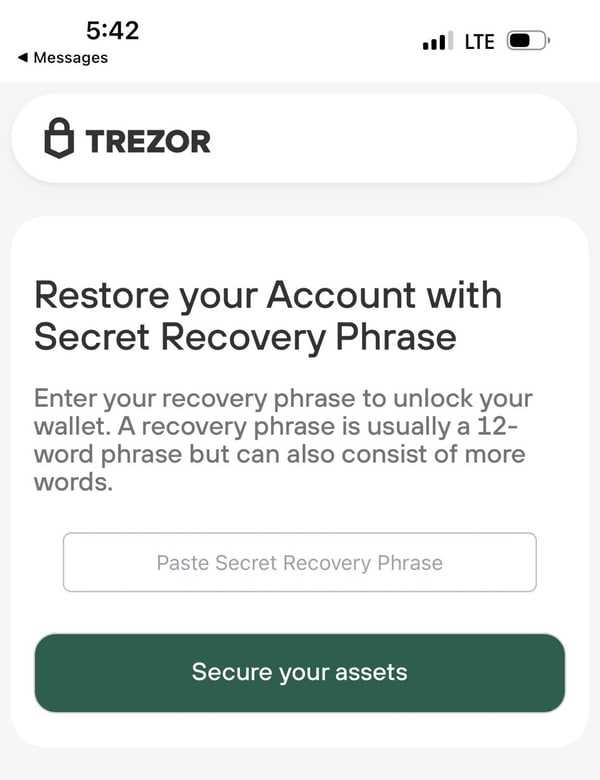
The security breach potentially exposed sensitive user data, such as email addresses and purchase history, to hackers. While user funds were not directly compromised, the breach could enable phishing attacks or other social engineering attempts targeting Trezor users. It highlights the importance of staying vigilant and being cautious when interacting with any communications related to their Trezor account or cryptocurrency holdings.
What can cryptocurrency holders do to protect themselves from security breaches?
Cryptocurrency holders can take several steps to protect themselves from security breaches. These include using hardware wallets like Trezor, enabling two-factor authentication for all their accounts, using unique and strong passwords, keeping software and firmware up to date, and being cautious of phishing attempts. Regularly monitoring account activity and employing best practices for online security can greatly reduce the risk of falling victim to a security breach.


