
Trezor Security Breach Uncovered: Future of Digital Wallets Threatened

In a shocking turn of events, an alarming security breach has been uncovered in the popular digital wallet Trezor. As one of the most trusted and widely used cryptocurrency hardware wallets, the implications of this breach are far-reaching and raise serious concerns about the security of digital assets.
Trezor has long been praised for its robust security measures, boasting features such as offline storage and encryption. However, recent findings reveal that a vulnerability in the device’s firmware could potentially allow hackers to gain unauthorized access to users’ private keys and steal their cryptocurrencies. This breach not only jeopardizes the funds of Trezor users but also shakes the confidence of the entire cryptocurrency community in the security of digital wallets.
The consequences of this security breach are significant and should not be underestimated. With the rising popularity and value of digital currencies, the need for secure storage solutions has never been more crucial. Users rely on digital wallets like Trezor to keep their assets safe from cyber threats, and this breach calls into question the effectiveness of current security measures in the cryptocurrency industry.
As the news of this breach spreads, it serves as a wake-up call for users to reevaluate their security practices and consider alternative storage options. It is essential for individuals to prioritize the security of their digital assets and stay informed about the latest developments in the field of cryptocurrency security. Only by staying vigilant and taking proactive measures can users protect their investments and maintain trust in the digital wallet industry.
Trezor Security Breach: What It Means for Digital Wallets

In recent news, a security breach has been uncovered in the popular digital wallet Trezor, raising concerns among the user community and highlighting the importance of robust security measures for digital wallets. This breach has significant implications for the wider digital wallet ecosystem and brings to light some important lessons for users and developers.
The Nature of the Breach

The security breach in Trezor involved unauthorized access to user funds and personal information stored within the digital wallet. The exact method used to carry out the breach is still under investigation, but it serves as a stark reminder that even products with a reputation for security can still be vulnerable.
Lessons in Security
One of the key lessons from this breach is the importance of using strong, unique passwords for digital wallets. Many users often reuse passwords across multiple platforms, making it easier for hackers to gain unauthorized access to their funds. Implementing two-factor authentication can also provide an additional layer of security and make it more difficult for attackers to compromise a wallet.
Another crucial lesson is the need to keep digital wallets and associated software up to date. Developers continually release updates to address security vulnerabilities, and failure to install these updates promptly can leave a wallet more susceptible to attacks.
The Implications

The Trezor security breach serves as a wake-up call for the digital wallet industry, reminding both users and developers about the importance of implementing robust security measures. Users should be vigilant in protecting their own security by following best practices, while developers must prioritize security in their wallet designs and continually update their software to address emerging threats.
In conclusion, the Trezor security breach has significant implications for the digital wallet industry and highlights the need for users and developers to prioritize security. By learning from this breach and implementing necessary precautions, we can ensure safer digital wallet experiences for all.
Exposing the Trezor Security Vulnerability
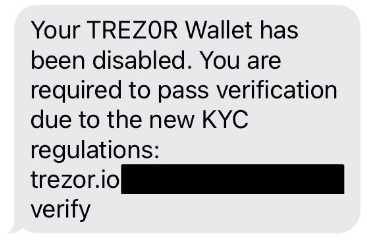
While Trezor is widely regarded as one of the most secure digital wallets on the market, a recent security breach has uncovered a significant vulnerability in its system. This breach has far-reaching implications for the security of digital wallets and highlights the importance of continuous vigilance when it comes to protecting sensitive financial information.
The Vulnerability
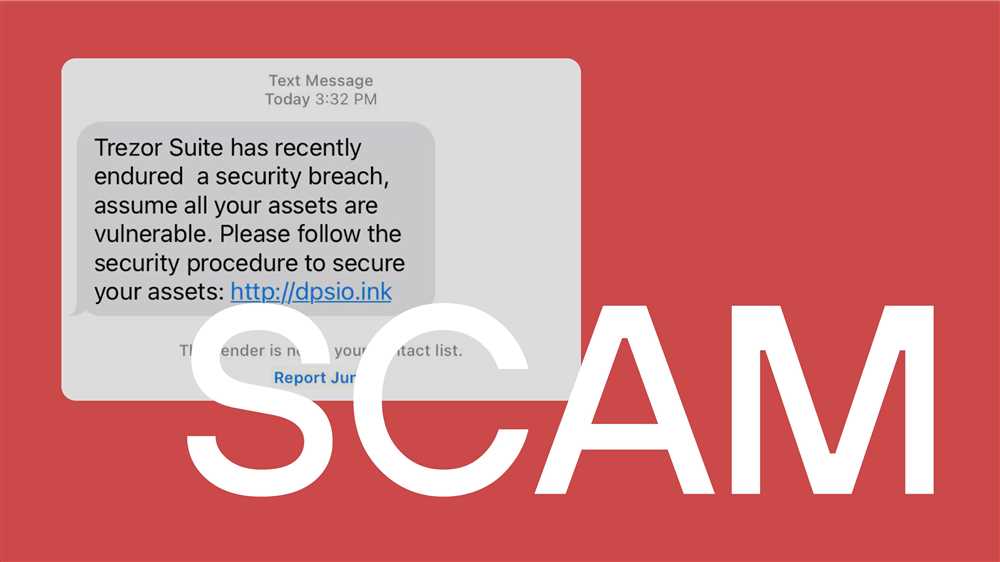
The vulnerability in Trezor’s security system lies in the physical device itself. Although the device’s security measures are robust, hackers have discovered a way to exploit a weakness in its design, allowing them to gain unauthorized access to users’ private keys. By gaining control of these private keys, hackers can gain full access to the stored cryptocurrencies, putting users’ funds at risk.
This vulnerability is particularly concerning because Trezor is known for its emphasis on security. Many users rely on Trezor as their go-to option for storing cryptocurrencies, assuming that their funds are safe from potential threats. However, this breach serves as a wake-up call for users to re-evaluate their security measures and potentially consider alternative methods for safeguarding their digital assets.
The Implications
As a result of this security breach, the implications for digital wallets, in general, are significant. Users must now question the overall security of their chosen digital wallet and reassess the level of protection offered. Additionally, this breach raises concerns about the broader security standards within the cryptocurrency industry and highlights the need for increased regulation and oversight.
Furthermore, this vulnerability exposes the potential flaws in relying solely on hardware wallets for storing cryptocurrencies. While hardware wallets are generally considered more secure than software wallets, they are not foolproof, as demonstrated by the Trezor breach. Users must now consider adopting additional security measures, such as multi-signature wallets or cold storage, to enhance the security of their digital assets.
In conclusion, the discovery of the Trezor security vulnerability serves as a critical reminder of the constant need for vigilance and improvement in the realm of digital wallet security. Users should take this opportunity to reassess their security measures and explore alternative options to protect their cryptocurrencies effectively.
Potential Risks for Digital Wallet Users

As the Trezor security breach has recently demonstrated, there are several potential risks that digital wallet users should be aware of:
1. Phishing Attacks
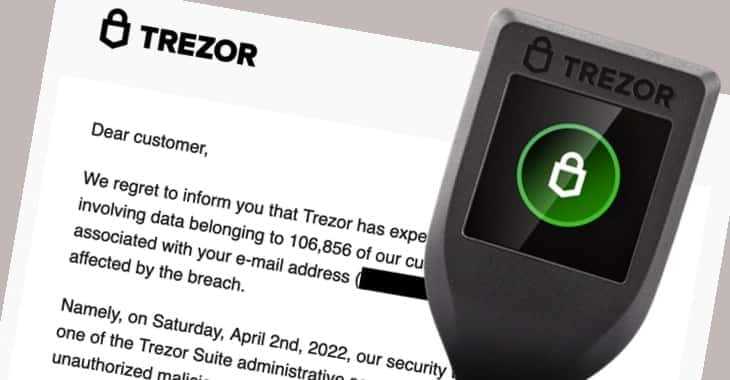
Phishing attacks are a common tactic employed by cybercriminals to trick users into revealing their sensitive information, such as login credentials or private keys. Digital wallet users should be cautious when receiving unsolicited emails or messages asking for their wallet information and should always verify the authenticity of the request before providing any information.
2. Malware and Keyloggers

Malware and keyloggers are malicious software that can be installed on a user’s device without their knowledge. These programs are specifically designed to capture sensitive information, including digital wallet passwords or private keys. Users should ensure that they have up-to-date antivirus software installed and regularly scan their devices for any potential threats.
Additionally, users should exercise caution when downloading software or applications related to their digital wallets, as these can sometimes be disguised as legitimate but are in fact malware.
3. Lost or Stolen Devices

If a user’s digital wallet is stored on a device that gets lost or stolen, there is a risk that unauthorized individuals may gain access to their funds. To mitigate this risk, users should consider enabling two-factor authentication and regularly backing up their wallet data to an offline storage device. It is also advisable to use strong passwords and PINs to protect the wallet on the device itself.
Furthermore, when choosing a digital wallet provider, users should research their security measures and reputation to ensure they are selecting a trusted and reliable service.
In conclusion, while digital wallets offer convenience and ease of use, they also come with potential risks. Users should be cautious and take proactive measures to protect their wallets and funds from falling into the wrong hands.
Steps to Protect Your Digital Wallet
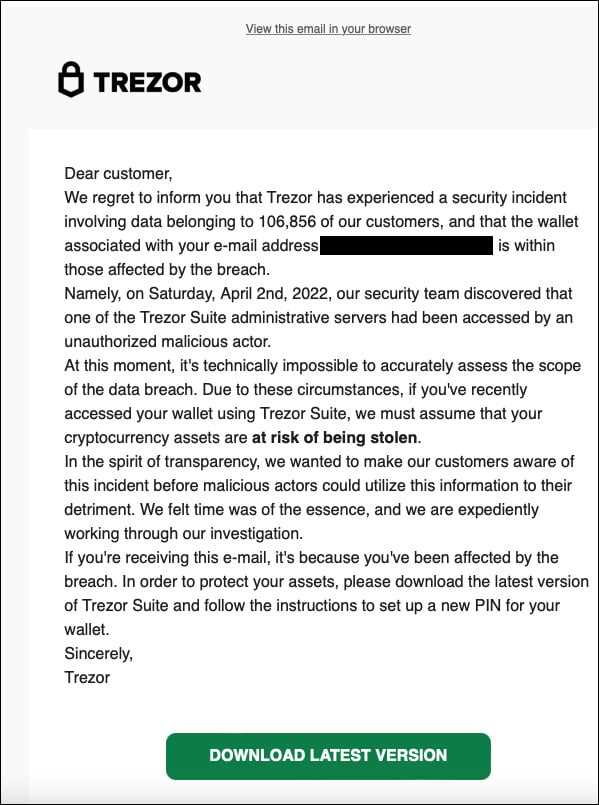
With the increasing popularity of digital wallets, it’s essential to take steps to protect your money and personal information. Here are some measures you can take to ensure the security of your digital wallet:
- Choose a reputable digital wallet provider: Research different providers and select one with a proven track record of security and reliability.
- Enable two-factor authentication: Utilize the added layer of security provided by two-factor authentication, requiring not only a password but also a unique code sent to your mobile device.
- Create a strong, unique password: Avoid using common or easily guessable passwords. Instead, create a complex password with a combination of uppercase and lowercase letters, numbers, and special characters.
- Regularly update your wallet software: Keep your digital wallet up to date with the latest security patches and software updates provided by the wallet provider.
- Be cautious with public Wi-Fi: When accessing your digital wallet on public Wi-Fi networks, be aware that your connection may not be secure. Avoid making any financial transactions or accessing sensitive information while connected to public networks.
- Backup your wallet: Regularly backup your digital wallet and store the backup in a secure location. This way, if your wallet is compromised, you can restore it without losing your funds.
- Keep your wallet offline: Consider using a hardware wallet, like a Trezor, which stores your private keys offline and provides an extra layer of security against hacking attempts.
- Be vigilant against phishing attempts: Be cautious of suspicious emails, messages, or websites that may be attempting to steal your wallet information. Always verify the authenticity of any communication before providing sensitive information.
- Monitor your wallet activity: Regularly review your wallet activity to identify any unauthorized transactions or suspicious activity. If you notice anything unusual, take immediate action to secure your wallet.
- Keep your device secure: Ensure that your device is protected with a strong password, PIN, or biometric authentication. Keep your device’s operating system and antivirus software up to date.
By following these steps and staying informed about the latest security practices, you can help protect your digital wallet from potential breaches and keep your funds and personal information safe.
Q&A:
What is the Trezor Security Breach?
The Trezor Security Breach refers to a recent incident where a vulnerability in the Trezor hardware wallets was discovered. This vulnerability could potentially allow attackers to steal the private keys of users and gain access to their digital assets.
How was the Trezor Security Breach uncovered?
The Trezor Security Breach was uncovered by a group of researchers who were conducting a security audit of the hardware wallets. They discovered a flaw in the way the wallets generate random numbers, which could be exploited by attackers to compromise the security of the devices.
What are the implications of the Trezor Security Breach for digital wallets?
The Trezor Security Breach highlights the importance of robust security measures for digital wallets. It serves as a reminder that even hardware wallets, which are considered to be more secure than software wallets, are not immune to security vulnerabilities. Users need to be cautious and take appropriate steps to secure their digital assets.


