
Understanding the Trezor Wallet Hack What Went Wrong

In recent years, the security of cryptocurrency wallets has become a major concern for users and developers alike. One of the most popular hardware wallets on the market, Trezor, recently experienced a security breach that raised questions about the safety of these devices. This article aims to analyze the Trezor wallet hack and shed light on the vulnerabilities that were exploited.
Trezor is renowned for its robust security features, designed to protect users’ digital assets from unauthorized access. However, in this recent incident, hackers were able to exploit a vulnerability in the firmware of the device, gaining unauthorized access to users’ wallets.
The hack involved a technique known as “supply chain attack,” where the hackers tampered with the firmware during the manufacturing process. This allowed them to inject malicious code into the firmware, which provided access to users’ private keys once the wallet was set up.
The consequences of the Trezor wallet hack were significant, with a number of users losing their funds. This incident highlights the importance of understanding the security measures in place for cryptocurrency wallets and staying vigilant against potential threats.
Understanding the Trezor Wallet Hack
The security breach of the Trezor wallet has raised concerns among cryptocurrency users. This article aims to provide an in-depth analysis of the hack and shed light on measures that can be taken to prevent such incidents.
What is Trezor Wallet?
Trezor Wallet is a popular and widely used hardware cryptocurrency wallet. It provides users with a secure way to store their digital assets by keeping the private keys offline and offering protection against various types of attacks.
The Security Breach
The recent hack on the Trezor Wallet raised questions about the overall security of hardware wallets. The breach involved exploiting a vulnerability in the firmware, allowing an attacker to gain unauthorized access and steal sensitive information or even control the funds stored in the wallet.
Attack Vector: The hack involved physical access to the device and tampering with the firmware to inject malicious code.
Impact: The consequences of this breach can be severe, as it can lead to the loss of funds and compromise the privacy of users’ transactions.
Preventing the Hack
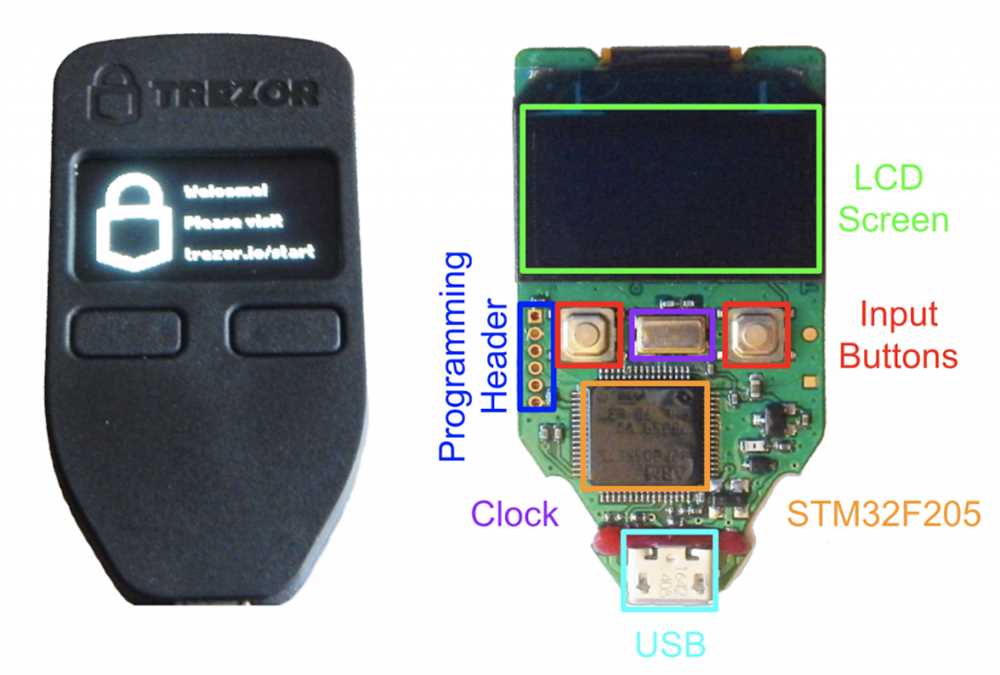
To prevent the Trezor Wallet hack and safeguard your digital assets, consider the following measures:
- Keep Firmware Updated: Regularly update the firmware of your Trezor Wallet to ensure you have the latest security patches and improvements.
- Verify Authenticity: Only purchase Trezor wallets from official sources to avoid counterfeit devices that might have compromised security.
- Enable Password Protection: Set up a strong and unique password for your Trezor Wallet to add an extra layer of security.
- Enable Two-Factor Authentication: Utilize the two-factor authentication feature provided by Trezor to protect against unauthorized access.
- Avoid Physical Attacks: Keep your Trezor Wallet stored in a safe place and avoid exposing it to potential physical attacks.
By implementing these security measures, users can significantly reduce the risk of falling victim to a Trezor Wallet hack.
In conclusion, understanding the Trezor Wallet hack and taking necessary precautions is crucial for safeguarding digital assets. Staying vigilant and informed about the latest security practices is essential in the evolving landscape of cryptocurrency security.
Analyzing the Security Breach
The recent hack of the Trezor wallet has raised concerns about the security of cryptocurrency wallets and the potential vulnerabilities that hackers can exploit. In order to fully understand the breach, it is important to analyze the various aspects of the attack.
One key aspect to analyze is the method used by the hackers to gain unauthorized access to the Trezor wallet. It is crucial to understand how they were able to bypass the security measures implemented by the wallet’s manufacturer. This can help identify potential flaws in the system and provide insights into ways to improve security in the future.
Another aspect to consider is the impact of the security breach on users and their funds. It is important to analyze the extent of the damage caused by the hack and determine if any funds were stolen or compromised. This can help users assess the level of risk associated with using the Trezor wallet and make informed decisions about their cryptocurrency investments.
Additionally, it is important to analyze the response of the wallet manufacturer to the security breach. Did they promptly notify users about the hack? Did they take immediate actions to address the vulnerabilities? Analyzing the response can provide insights into the company’s commitment to security and their ability to handle such incidents effectively.
Furthermore, analyzing the motivations behind the hack can provide valuable insights. Did the hackers have financial motives, or were they targeting specific individuals or groups? Understanding the motives can help develop strategies to prevent future attacks and protect users’ funds.
In conclusion, analyzing the security breach of the Trezor wallet is essential for understanding the vulnerabilities that hackers can exploit and improving the overall security of cryptocurrency wallets. By examining the method used by the hackers, assessing the impact on users and their funds, analyzing the response of the wallet manufacturer, and understanding the motivations behind the attack, valuable insights can be gained to enhance the security measures in place.
Implications of the Trezor Wallet Hack

The Trezor wallet hack has significant implications for both individual cryptocurrency users and the overall security of the cryptocurrency industry. This breach highlights the vulnerabilities that even hardware wallets can have, and it raises concerns about the safety of storing digital assets.
First and foremost, this hack compromises the security and trust that users had in the Trezor wallet. The breach of a supposedly secure hardware wallet raises questions about the effectiveness of the security measures implemented and the level of encryption employed.
Furthermore, the hack serves as a wake-up call for cryptocurrency users to reevaluate their security practices. It emphasizes the importance of using strong and unique passwords, enabling two-factor authentication, and keeping software and firmware up to date. It also underscores the need for diversified storage solutions, such as using multiple wallets or offline cold storage.
The implications of this hack extend beyond the individual level and have broader implications for the cryptocurrency industry as a whole. The incident highlights the need for continuous research and development in the field of cybersecurity, as hackers constantly evolve their techniques. It underscores the importance of conducting regular security audits and implementing robust protocols to ensure the safety of digital assets.
Impact on Industry Reputation
The security breach also has implications for the reputation of hardware wallet manufacturers. The Trezor wallet hack may lead to a loss of trust and credibility for Trezor and other similar devices. Users may be hesitant to trust their digital assets to these wallets, potentially dampening the adoption and growth of the hardware wallet market.
Regulatory Concerns
The incident may also have regulatory implications. Regulators may view the hack as evidence of the inherent risks associated with cryptocurrency and take steps to tighten regulations on digital asset storage and security. This could have a significant impact on the cryptocurrency industry, potentially restricting the freedom and flexibility that users currently enjoy.
In conclusion, the Trezor wallet hack has far-reaching implications for both individual users and the broader cryptocurrency industry. It highlights the importance of cybersecurity, the need for continuous improvement in security measures, and the necessity of diversifying storage solutions. It also serves as a reminder of the risks associated with cryptocurrency and the importance of staying vigilant and proactive in safeguarding digital assets.
Protecting Your Crypto Assets: Best Practices
Keeping your crypto assets safe is crucial in the ever-evolving world of digital finance. With the rise of hacking incidents, it is imperative to follow best practices to ensure the security of your funds. Here are some recommended measures you can take to protect your crypto assets:
1. Use a Hardware Wallet

Investing in a hardware wallet, like Trezor, is one of the safest ways to store your cryptocurrencies. These devices are designed to keep your private keys offline, making it difficult for hackers to gain access to them. By using a hardware wallet, you can have peace of mind knowing that your assets are well-protected.
2. Enable Two-Factor Authentication
Enabling two-factor authentication (2FA) adds an extra layer of security to your crypto accounts. By requiring a second form of verification, such as a unique code generated by an authentication app or sent via SMS, you can prevent unauthorized access to your funds. Be sure to enable 2FA on all of your crypto exchange accounts and wallets.
3. Be Mindful of Phishing Attempts

Phishing attacks are one of the most common methods used by hackers to steal crypto assets. Be cautious of suspicious emails, links, or messages that request your login credentials or private keys. Always double-check the URL of the website you are visiting and ensure it is legitimate. Don’t click on any unexpected or unsolicited links.
4. Keep Software Updated
Regularly updating the software on your devices is essential for maintaining the security of your crypto assets. Software updates often include patches for known vulnerabilities and security weaknesses. Make sure to keep your operating system, wallets, and any other crypto-related software up to date to minimize the risk of exploitation.
5. Use Strong Passwords and Secure Storage

Create strong, unique passwords for all of your crypto accounts and wallets. Avoid using easily guessable information or reusing passwords across multiple platforms. Consider using a password manager to securely store your passwords. Additionally, consider encrypting your wallets and backups with strong passwords or using encryption software.
By following these best practices, you can increase the security of your crypto assets and reduce the risk of theft. Stay vigilant, stay informed, and prioritize the protection of your digital wealth.
Q&A:
What is Trezor Wallet Hack?
The Trezor Wallet Hack refers to a security breach that occurred on the Trezor hardware wallet in 2017. Hackers were able to exploit a vulnerability in the wallet’s firmware and gain access to users’ private keys and cryptocurrency funds.
How did the hackers manage to hack the Trezor Wallet?
The hackers were able to hack the Trezor Wallet by exploiting a vulnerability in the wallet’s firmware. They used a technique known as “glitching” to manipulate the firmware and gain access to users’ private keys. Once they had access to the private keys, they could transfer the users’ cryptocurrency funds to their own wallets.
What measures did Trezor take to fix the security breach?
Trezor took several measures to fix the security breach and protect its users. They released a firmware update that addressed the vulnerability exploited by the hackers. In addition, they implemented additional security measures, such as introducing a passphrase feature and requiring physical confirmation for transactions.


