
Defending Against Malware: Can Trezor’s Security Features Protect You?

Protect your digital assets with Trezor’s advanced security features
With the rising popularity of cryptocurrencies, the threat of malware and hacking attempts has become an ever-present danger. As a cryptocurrency owner, it is crucial to safeguard your funds from potential attackers.
Trezor is the ultimate solution for securing your cryptocurrency holdings. With its cutting-edge security features, it ensures that your digital assets are safe from the prying eyes of cybercriminals.
Key features of Trezor:
- Hardware Encryption: Trezor’s hardware encryption guarantees the highest level of security for your private keys. With an offline storage approach, it eliminates the risk of online attacks and unauthorized access to your funds.
- Two-Factor Authentication: By enabling two-factor authentication, Trezor adds an extra layer of protection to your account. It requires both something you know (your password) and something you have (your physical device) to access your funds.
- Secure PIN Protection: Trezor’s PIN protection ensures that only you can access your device. With the option to set a unique PIN, you can prevent unauthorized individuals from tampering with your device or accessing your cryptocurrency.
- Expanded Cryptocurrency Support: Trezor supports a wide range of cryptocurrencies, including Bitcoin, Ethereum, Litecoin, and many more. With Trezor, you can securely store all of your digital assets in one place.
Don’t let hackers compromise your crypto holdings. Invest in Trezor today and rest easy knowing that your digital assets are protected by state-of-the-art security features.
Order your Trezor now and take control of your cryptocurrency security!
Defending Against Malware

Malware, or malicious software, poses a significant threat to the security of your cryptocurrency. It is designed to infiltrate your devices, steal sensitive information, and gain unauthorized access to your digital assets. Without adequate protection, you risk losing everything.
Understanding the Threat
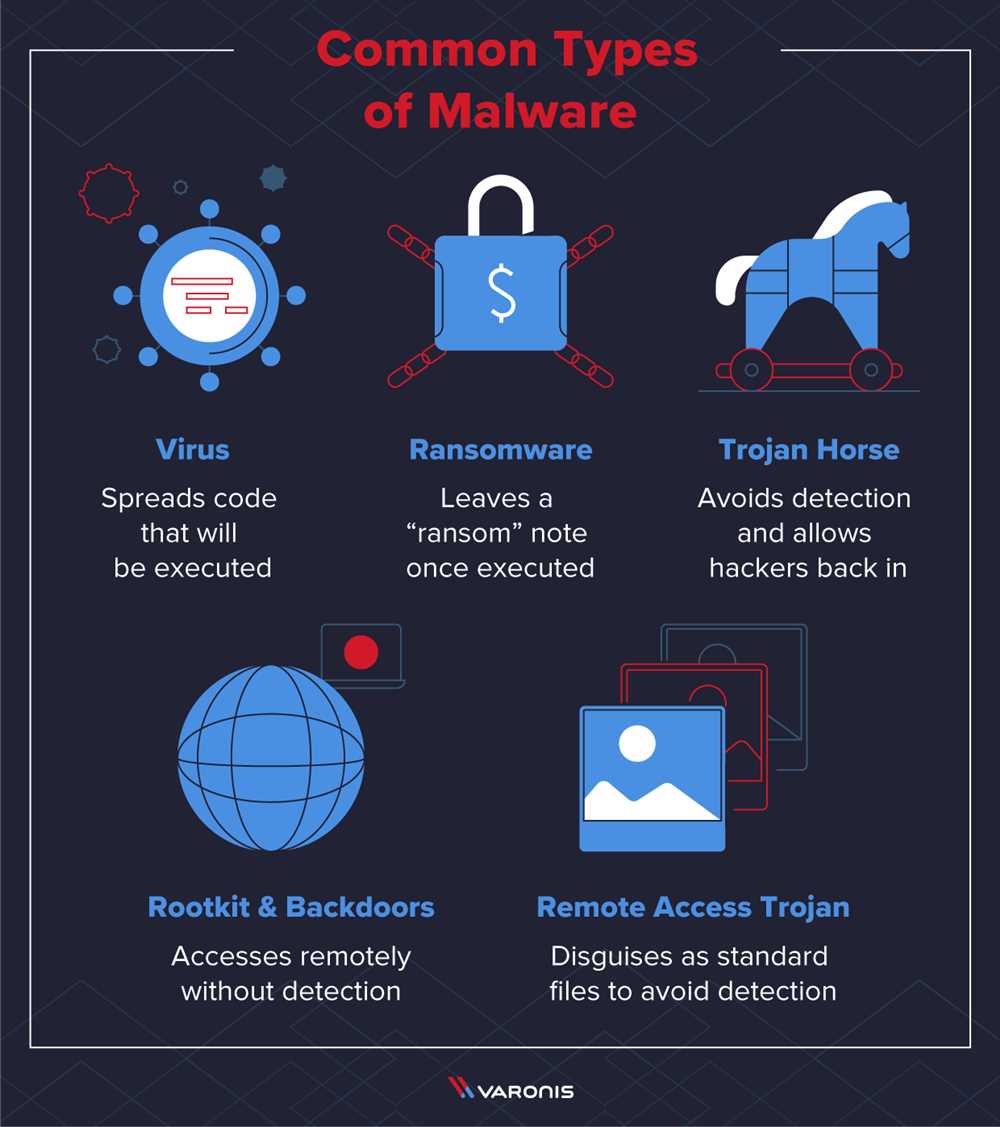
Malware comes in many forms, including viruses, worms, Trojans, ransomware, and spyware. These malicious programs can be downloaded unknowingly through suspicious emails, websites, or software downloads. Once installed on your device, they can silently monitor your activities, record keystrokes, and even alter or delete your files.
Malware specifically targets cryptocurrency wallets because of the potential financial gain. By gaining access to your private keys or seed phrases, hackers can empty your wallet and make off with your funds. This can have devastating consequences for your financial security and personal well-being.
The Importance of Hardware Wallets

To defend against malware, it’s essential to use a secure cryptocurrency wallet. Hardware wallets, like the Trezor, offer a higher level of protection compared to software wallets or keeping your funds on an exchange.
Trezor’s security features include a built-in OLED display for verifying transactions, a secure chip that isolates your private keys from your computer or smartphone, and a PIN code to prevent unauthorized access. These measures ensure that even if your device is infected with malware, your cryptocurrency remains safe and secure.
Additionally, Trezor’s open-source firmware allows for regular security updates, keeping up with the latest threats and vulnerabilities in the ever-evolving landscape of malware. With Trezor, you can have peace of mind knowing that your cryptocurrency is protected against potential attacks.
Don’t let malware compromise your cryptocurrency. Invest in a hardware wallet like Trezor and take control of your financial security.
Trezor’s Security Features
Trezor is a leading provider of hardware wallets for securely storing cryptocurrencies. With its advanced security features, Trezor ensures that your digital assets are protected against malware and other potential threats. Here are some of the key security features that make Trezor stand out:
Offline Storage

Trezor wallets store your private keys offline, away from any potential cyber attacks. By keeping your private keys offline, Trezor ensures that they are shielded from malware that could potentially compromise your digital assets.
Two-Factor Authentication

Trezor supports two-factor authentication (2FA) to further enhance the security of your cryptocurrency holdings. With 2FA enabled, accessing your wallet requires both a physical device (Trezor) and a unique code generated by the device. This adds an extra layer of protection against unauthorized access.
Additionally, Trezor’s 2FA feature provides protection against phishing attacks by ensuring that the user is interacting with the legitimate Trezor device, rather than a malicious replica.
Secure PIN Protection

Trezor wallets come with a secure PIN protection feature, which prevents unauthorized users from accessing your funds even if they have physical access to your device. The PIN is entered directly on the Trezor device, ensuring that it remains secure from any potential keyloggers or other malware that may be installed on your computer.
Furthermore, Trezor’s secure PIN protection feature includes an incremental lockout mechanism. After a certain number of unsuccessful PIN attempts, the device is temporarily locked, preventing any further unauthorized access.
With these robust security features, Trezor provides users with peace of mind, knowing that their cryptocurrency investments are protected against malware and other potential risks.
Keeping Your Cryptocurrency Safe

Protecting your cryptocurrency is of utmost importance, and Trezor is committed to keeping your digital assets secure. Here are some key features that make Trezor a reliable choice for safeguarding your cryptocurrency:
Offline Storage: Trezor stores your private keys offline, which means they are not vulnerable to online attacks or malware. By keeping your keys offline, Trezor ensures that your cryptocurrency remains safe even if your computer or smartphone is compromised.
Multi-factor Authentication: Trezor employs multi-factor authentication to provide an extra layer of security. In addition to entering your PIN, you also need to physically confirm transactions on your Trezor device. This prevents unauthorized access and protects against potential hacking attempts.
Advanced Encryption: Trezor uses advanced encryption protocols to secure your private keys. This ensures that your cryptocurrency remains encrypted and protected from potential threats.
Secure Recovery: In the event of a lost or stolen device, Trezor provides a secure recovery process. By using a unique recovery seed, you can easily restore your cryptocurrency to a new device, ensuring that your funds are never lost.
Regular Firmware Updates: Trezor is dedicated to constantly improving the security of their devices. They regularly release firmware updates that address any vulnerabilities and introduce new security measures to protect your cryptocurrency.
Third-Party Integration: Trezor works seamlessly with popular cryptocurrency wallets and platforms, allowing you to securely manage and transact with your digital assets. This integration ensures that your cryptocurrency is always accessible and protected.
With Trezor’s robust security features, you can have peace of mind knowing that your cryptocurrency is safe and secure from the ever-evolving threats of malware and hacking. Don’t take chances with your digital assets – choose Trezor for the ultimate protection.
Q&A:
What makes Trezor’s security features effective against malware?
Trezor’s security features include a combination of hardware and software protections. The device uses a secure chip that ensures the private keys are stored safely and cannot be accessed by malware. Additionally, Trezor utilizes encrypted communication, multi-factor authentication, and a secure bootloader to prevent malware from tampering with the device’s firmware.
Is Trezor compatible with different types of cryptocurrencies?
Yes, Trezor is compatible with a wide range of cryptocurrencies. You can store popular cryptocurrencies such as Bitcoin, Ethereum, and Litecoin on your Trezor device. Additionally, Trezor supports many other altcoins and is constantly adding support for new cryptocurrencies.
Can I use Trezor with my mobile device?
Yes, you can use Trezor with your mobile device. Trezor has a mobile app called “Trezor Wallet” that is available for both iOS and Android devices. The app allows you to manage your cryptocurrency securely on the go, making it convenient for mobile users.
What happens if I lose my Trezor device?
If you lose your Trezor device, you don’t have to worry about losing your cryptocurrencies. When you first set up your Trezor, you’ll be given a recovery seed. With this seed, you can restore your wallet and access your funds on a new Trezor device or any other compatible wallet. It’s important to keep your recovery seed in a safe place and never share it with anyone.


